
In February 2025 we had already observed the functioning of DDoSIA, the crowd-hacking system promoted by NoName057(16): a client distributed via Telegram, DDoS attacks against European targets, rewards in cryptocurrencies.
A simple, brutal, but effective machine.
Its strong point is not its technical sophistication, but its ability to rapidly mobilize thousands of users, even those with no experience, turning them into occasional cyber-mercenaries. All you need is a smartphone, a Telegram channel, and a download link to enter the “patriotic war.” No training, no skills, just automated clicks and a dashboard with assigned targets.
Then came Operation Eastwood, led in recent days by Europol, which led to the dismantling of over 100 servers in five European countries, with arrests in France and Spain.
But what emerges goes beyond the image of patriotic activism: an ecosystem is taking shape where propaganda, digital infrastructures and tools of cultural control are intertwined. A system that hits cyber targets, but which — in parallel — intercepts and directs identities, young people and narratives.
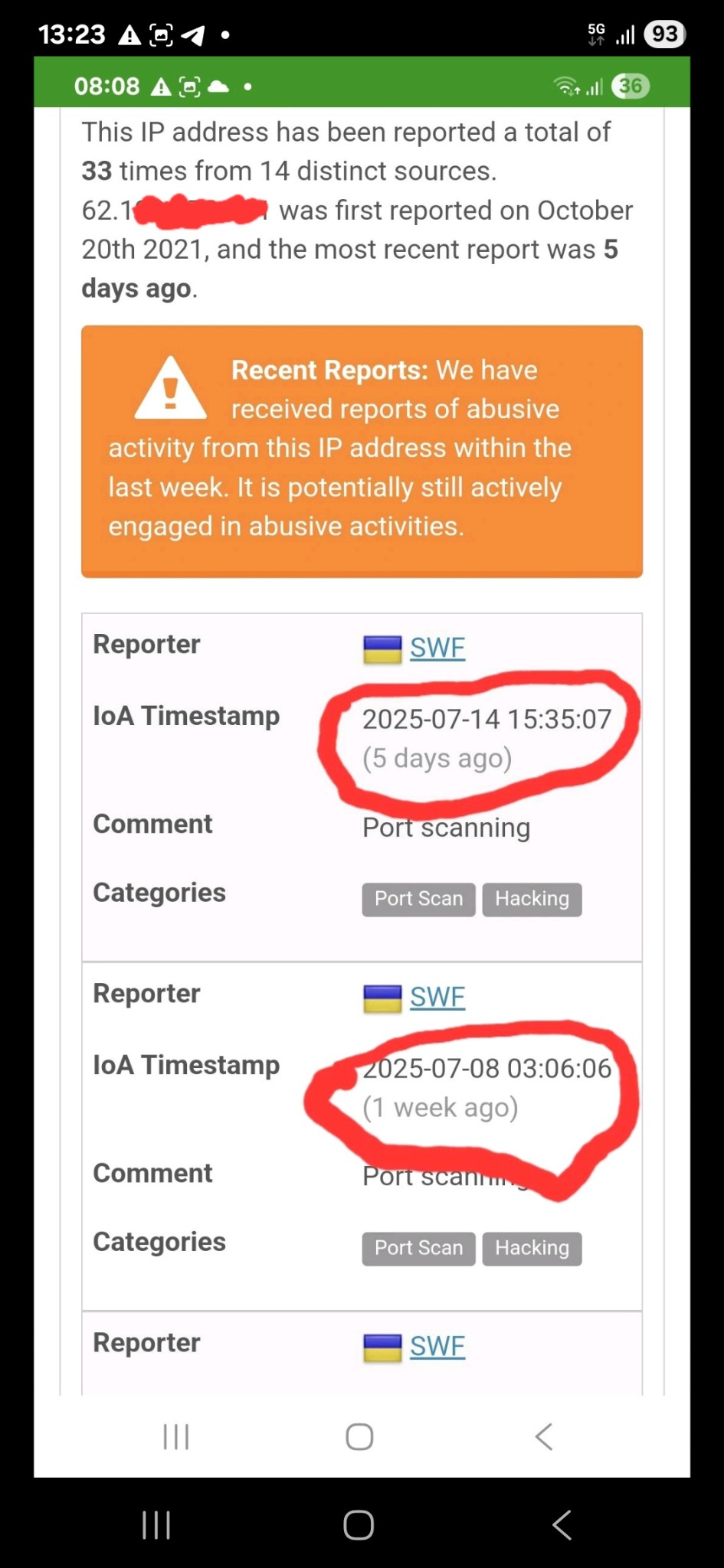
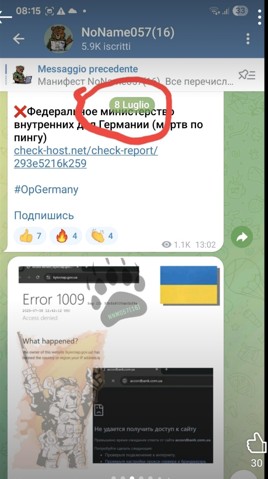
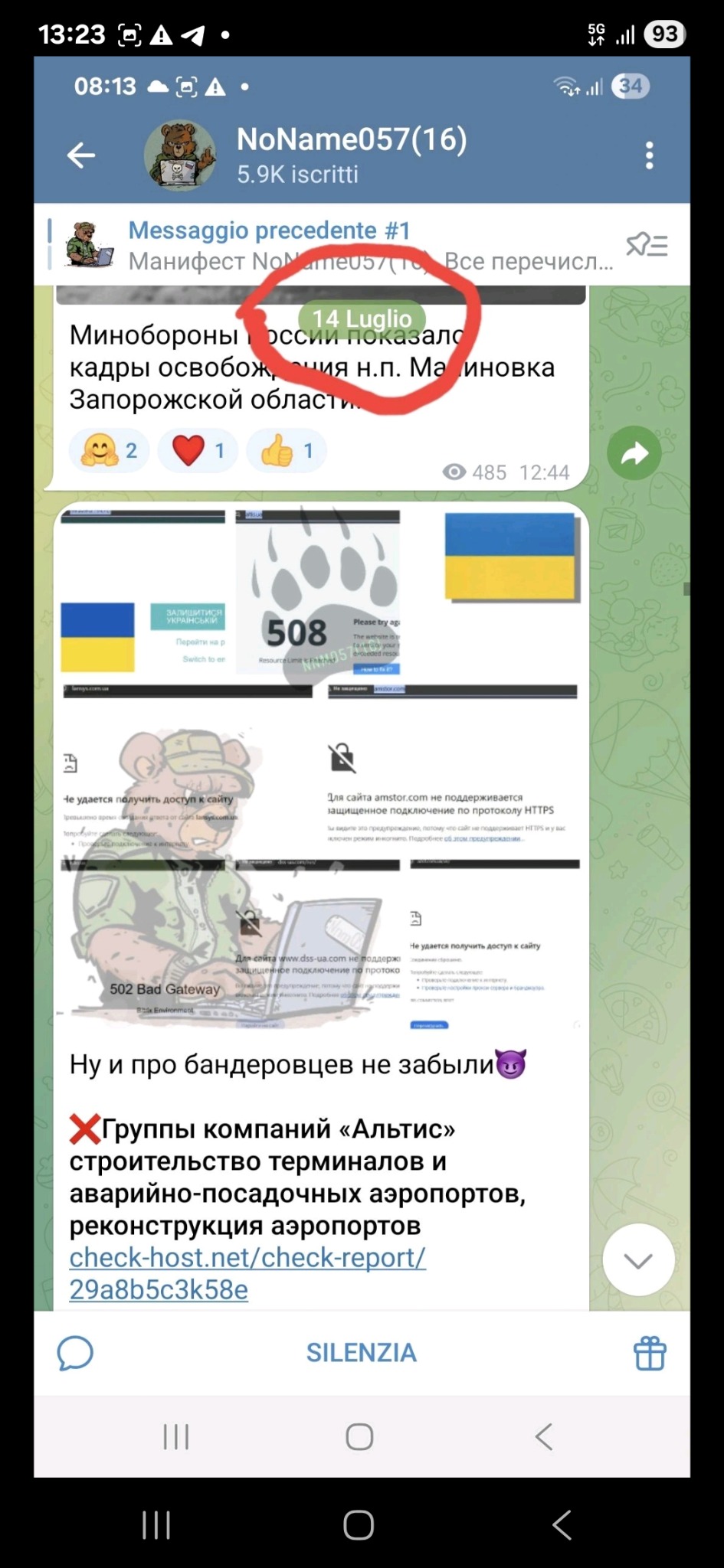
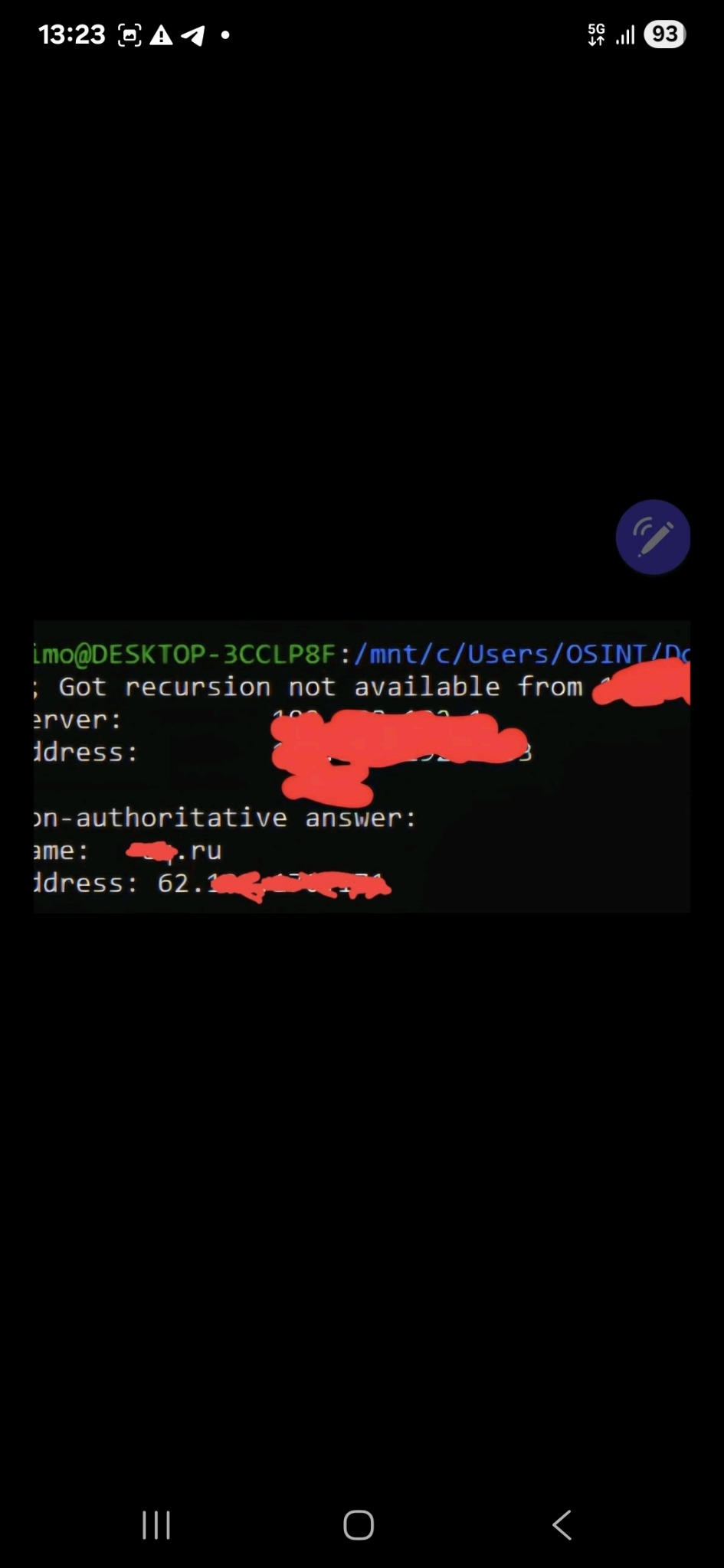
In recent months, a recurring pattern has raised suspicions. Several times, the same machine has appeared in a public database for aggressive port scanning activities, precisely at the same times in which NoName057(16) claimed DDoS attacks on Telegram. A emblematic example: July 8th and then July 14th. Same behavior, same machine, new claim. Analyzing the DDoS client, distributed to volunteers, a crucial detail emerges: a remote endpoint not declared in the code. This C2 (Command and Control) server acts as a hidden ‘brain, sending encrypted commands to coordinate simultaneous attacks.
No public announcements, no Telegram messages. Just a task. This is not a spontaneous attack. It is a distributed order.
This confirms, if ever it were needed, that the client is not just a distributed tool for “patriotic volunteers”, but reflects a centralized and functional logic, which raises doubts about the effective autonomy of the collective.
NoName057(16) is thus configured not only as a community, but as a possible technical interface of a more extensive system, in which names, roles and infrastructures appear that can be traced back — directly or indirectly —to institutional contexts
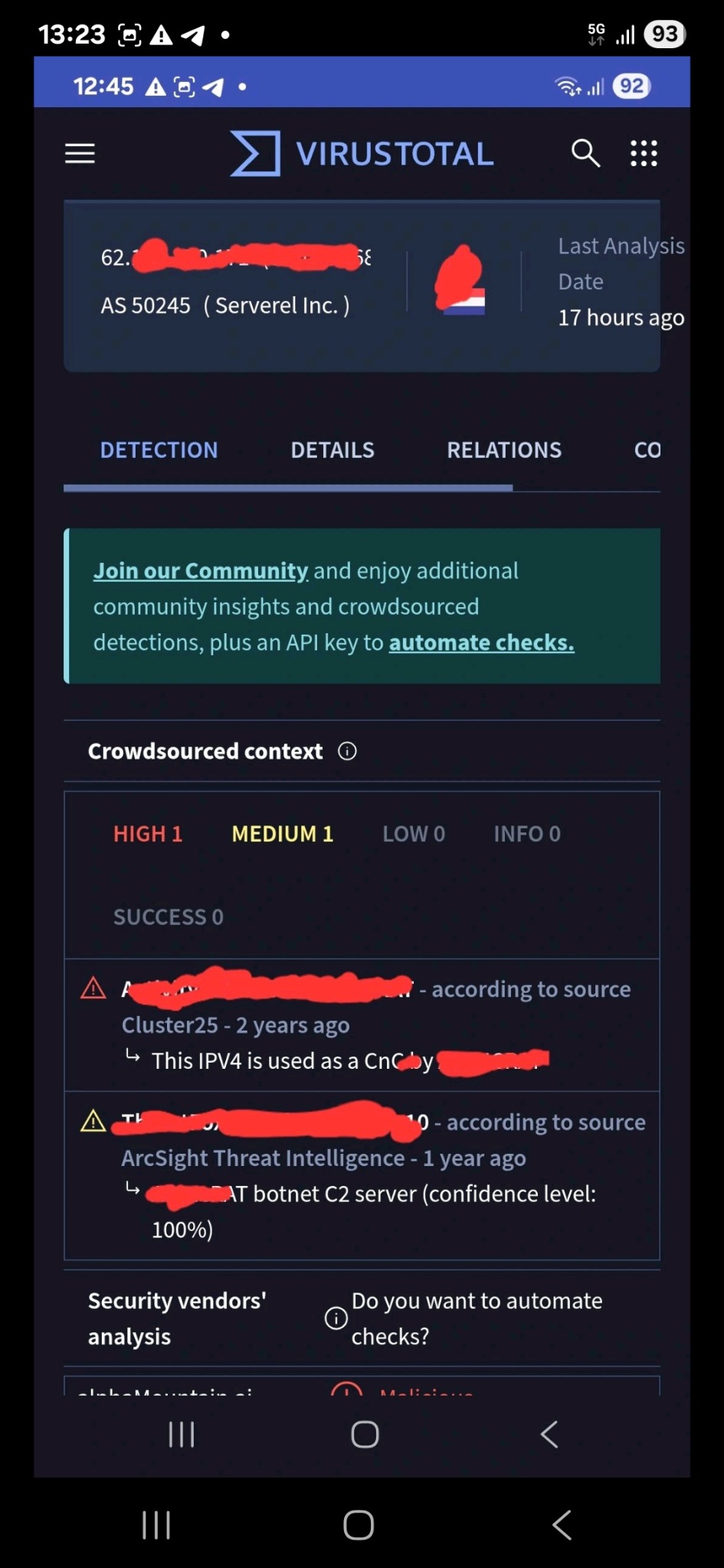
The system works. The client attacks. The message circulates.
But who built it? Who really controls it?
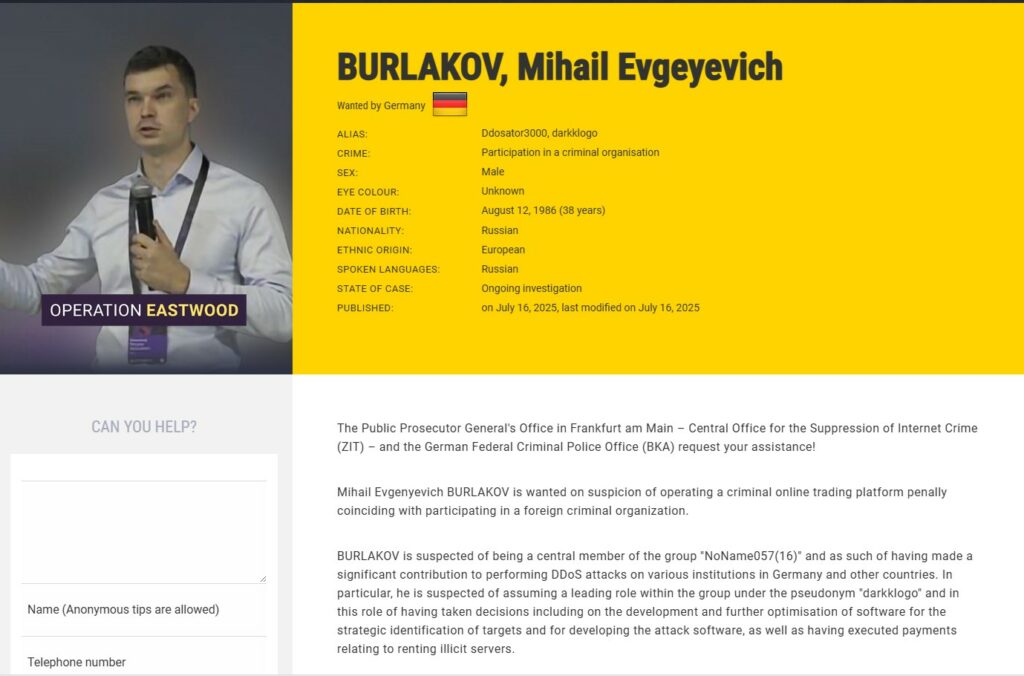
Two names are beginning to emerge: Maxim Lupin and Mihail Burlakov.
Thanks to Operation Eastwood, international warrants and OSINT evidence, two key figures emerge:
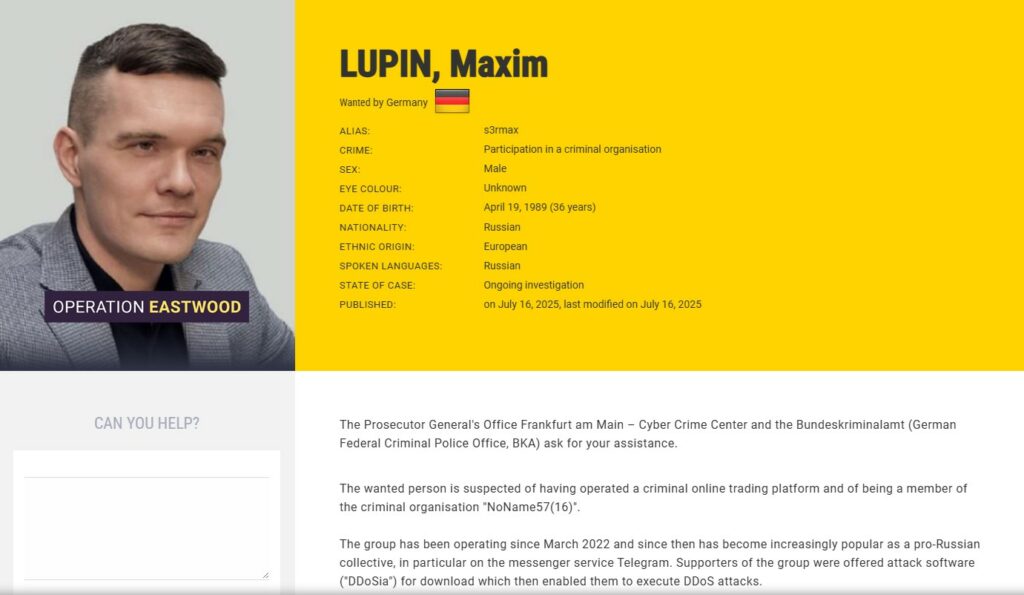

Burlakov is known in the group’s Telegram channels as ddosator3000 or @darkklogo. He is recognized in internal DDoS malware rankings. According to Europol, he designed the client code, rented illegal servers to manage the attacks, and actively participated in the distribution of the software.
His phone number, published in the university’s official contacts, is associated with a Telegram profile registered with the alias @darkklogo. The IP addresses linked to that user are not anonymized and can be traced back to an area with a high institutional density: the Kremlin.
No precautions. No anonymity. Only the certainty of impunity.

Less exposed in technical channels, but central to the structure, is Maxim Nikolaevich Lupin, general director of the CISM and an institutional figure linked to educational projects, information security and “ideological prevention”.
Lupin is accredited to the Presidency of the Russian Federation. He worked as a cybersecurity specialist for the pro-government veterans organization Combat Brotherhood and as a project manager for ZephyrLab, a company that develops websites for federal ministries. He is also suspected of running an illegal online trading platform.
If Burlakov writes the code, Lupine decides its use

The Center for the Study and Monitoring of Youth (CISM) is not a think tank.
Founded at the direct instigation of the Kremlin, it receives over 2 billion rubles for projects that aim, officially, to “protect young people from destructive content”.
In reality, it is an infrastructure that merges:
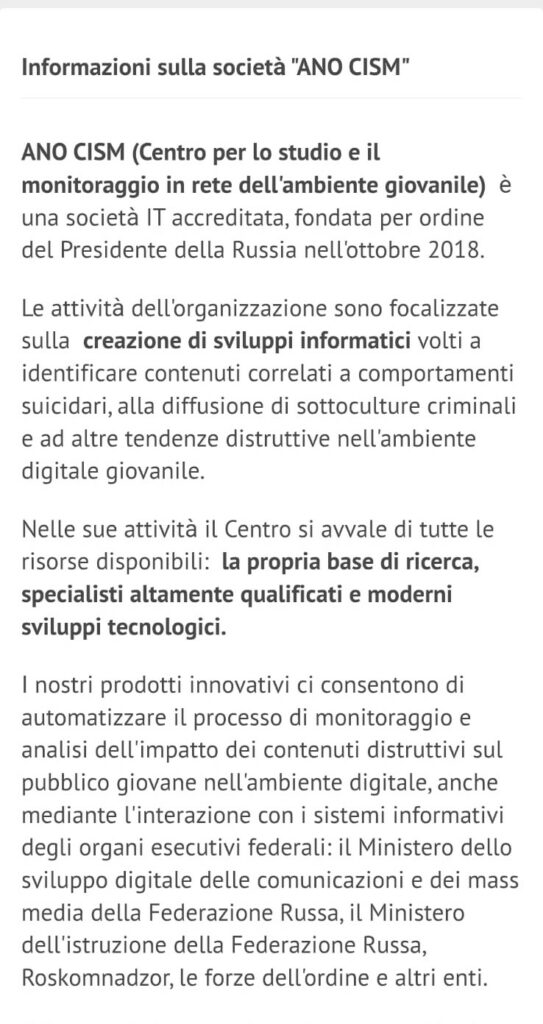
The technological heart of the CISM is the AIS “Prevention” system, which probes further 540 million social profiles analyzing posts, likes, emojis, comments, hashtags, silences.
Every teenager receives two indices:
The data is de-anonymized, profiled and reported.
According to documents leaked by the Kremlin and analyzed in the investigative project Kremlin Leaks — edited by Der Spiegel, iStories, VSquare and Frontstory.pl — the system is currently active in at least 44 Russian regions and is being integrated with the Interior Ministry’s databases.
It’s artificial intelligence at the service of ideology.
The CISM works closely with the Ministry of Education and the Federal RPSP Center to handle minors deported from the occupied Ukrainian territories.
The model is clear:
According to internal documents obtained by Meduza, the Ministry of Education has initiated systematic monitoring of adopted minors from occupied regions. In the first half of 2023, at least five children died. In one documented case, it was suicide. The causes were not disclosed.
In response, “preventive work” has been activated, including the direct involvement of the CISM: behind the rhetoric of protection lies an algorithmic surveillance system. The Center develops psychosocial risk profiles, but not to offer support: the goal is to classify minors based on their “deviance,” “opposition,” or ideological fragility.
Each registered teenager receives a personal file with identifying data, online tracking, and predictive indicators generated by neural networks, used to report to the authorities. The result is an automated filing based on digital behavior and political opinions, which eliminates any anonymity.
There is no evidence that the CISM, as an institution, is directly involved in the attacks. But when both the director and the deputy director are linked to the same infrastructure used by NoName057(16), the line between “youth protection” and cyber operations becomes increasingly thin. And less and less credible.
NoName057(16), DDoSIA, CISM, AIS Prevenzione, @darkklogo, Maxim Lupin.
These names appear in different contexts, but sometimes they touch, overlap, speak to each other.
There is no proof that directly links them.
But there are patterns, temporal coincidences, double roles, shared infrastructures.
And above all: strategic absences of anonymity, as if there were no need to hide anything.
Maybe it’s not a centralized operation. Maybe it is.
What is certain is that not everything that appears spontaneous really is.
The risk today is not just technical, but cultural.
And understanding where digital noise ends and a structured design begins is the first step to defending not only servers, but also our ability to read the present.
Because when ideological algorithms classify children as “oppositional,” and when digital architects themselves design both re-education tools and attack platforms, the line between cybersecurity and social control becomes too thin to be ignored.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
