
Online scams known as “pig butchering” are undergoing a profound transformation. From artisanal and disorganized operations , based on makeshift call centers, they have become a structured, scalable, and highly automated system. This is according to a recent report published by Infoblox , which describes the evolution of this phenomenon towards a model called “Pig Butchering-as-a-Service” (PBaaS).
According to the analysis, criminal groups can now launch large-scale fraud campaigns as easily as activating a digital subscription service. The key to this shift is the emergence of specialized providers that provide, for a fee, every component needed to carry out a complete scam.
In the new illegal ecosystem, these operators market ready-made packages that include databases of potential victims, contact tools, fake investment platforms, and automated interaction management systems. This dramatically reduces the technical skills required of scammers, lowering the barriers to entry globally.
One of the key players identified in the report is a vendor known as ” Penguin ,” also known as Heavenly Alliance or the Overseas Alliance. The group acts as a true hub, offering comprehensive fraud kits, operational models, and ready-to-use solutions.
The catalog attributed to Penguin is particularly complex. It includes the “Shè gōng kù,” a vast archive of personal data relating to Chinese citizens, including years of bank statements and travel information, used to select targets considered financially significant. This is complemented by the sale of compromised Western accounts, such as verified developer profiles on Tinder, WhatsApp, and Apple, sold at extremely low prices.
Another key element is the so-called “character sets” (Ren She Tao Tu) : collections of images and videos stolen from social media influencers, used to construct credible and consistent digital identities, useful for luring victims. The system is complemented by SCRM AI, an automated social media relationship management tool that allows for maintaining and intensifying contact with targeted individuals.
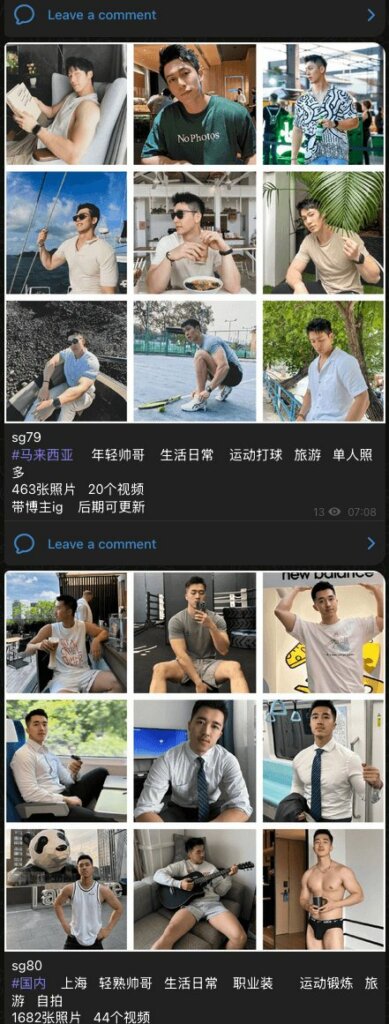
While Penguin provides the resources to identify and engage victims, other operators handle the final stage of the fraud. Among these, Infoblox highlights UWORK , a provider that offers an advanced Customer Relationship Management platform designed to simultaneously coordinate hundreds of victims and operators.
The effectiveness of this infrastructure is documented by a court case brought to trial in the United States in early 2025, in which Chinese criminals used the UWORK system to steal over $13 million.
The platform also allows the creation of fraudulent trading sites that closely mimic the appearance of legitimate software like MetaTrader . Some of these portals even include ” Know Your Customer” (KYC) procedures, used to obtain victims’ identity documents, thus extending the damage beyond financial loss.
The shift to a model based on industrialized services represents a significant risk factor. As the report highlights, this structure allows criminal networks to expand rapidly without having to develop advanced technological expertise, replicating dynamics already observed in the illegal malware and phishing-as-a-service markets.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
