
Un esperto di sicurezza ha scoperto che sei dei gestori di password più diffusi, utilizzati da decine di milioni di persone, sono vulnerabili al clickjacking, un fenomeno che consente agli aggressori di rubare credenziali di accesso, codici di autenticazione a due fattori e dati delle carte di credito.
Il problema è stato segnalato per la prima volta dal ricercatore indipendente Marek Tóth, che ha presentato un rapporto sulle vulnerabilità alla recente conferenza di hacker DEF CON 33. Le sue scoperte sono state successivamente confermate dagli esperti di Socket, che hanno contribuito a informare i fornitori interessati e a coordinare la divulgazione pubblica delle vulnerabilità.
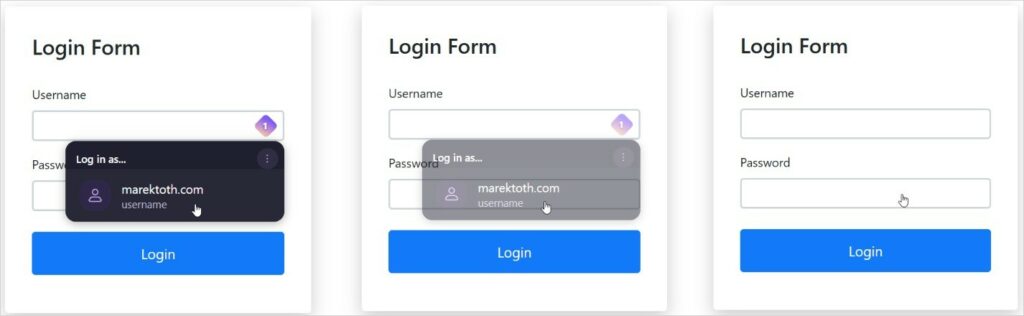
Ha testato il suo attacco su varianti specifiche di 1Password, Bitwarden, Enpass, iCloud Passwords, LastPass e LogMeOnce e ha scoperto che tutte le versioni del browser potevano far trapelare dati sensibili in determinati scenari.
Gli aggressori possono sfruttare le vulnerabilità quando le vittime visitano pagine dannose o siti vulnerabili ad attacchi XSS o al cache poisoning. Di conseguenza, gli aggressori sono in grado di sovrapporre elementi HTML invisibili all’interfaccia del gestore delle password. L’utente penserà di interagire con innocui elementi cliccabili sulla pagina, ma in realtà attiverà il riempimento automatico, che “trapelerà” le sue informazioni riservate agli hacker.
L’attacco si basa sull’esecuzione di uno script su un sito web dannoso o compromesso. Questo script utilizza impostazioni di trasparenza, sovrapposizioni o eventi puntatore per nascondere il menu a discesa di compilazione automatica del gestore password del browser. Allo stesso tempo, l’aggressore sovrappone elementi falsi e fastidiosi alla pagina (come banner di cookie, pop-up o CAPTCHA). Tuttavia, i clic su questi elementi conducono a controlli nascosti del gestore delle password, che portano alla compilazione di moduli con informazioni riservate.
Ha dimostrato diversi sottotipi DOM e exploit dello stesso bug: manipolazione diretta dell’opacità dell’elemento DOM, manipolazione dell’opacità dell’elemento radice, manipolazione dell’opacità dell’elemento padre e sovrapposizione parziale o completa.
Il ricercatore ha anche dimostrato l’utilizzo di un metodo in cui l’interfaccia utente segue il cursore del mouse e, di conseguenza, qualsiasi clic dell’utente, ovunque si trovi, attiva il riempimento automatico dei dati. Allo stesso tempo, Toth ha sottolineato che lo script dannoso può rilevare automaticamente il gestore di password attivo nel browser della vittima e quindi adattare l’attacco a un obiettivo specifico in tempo reale.
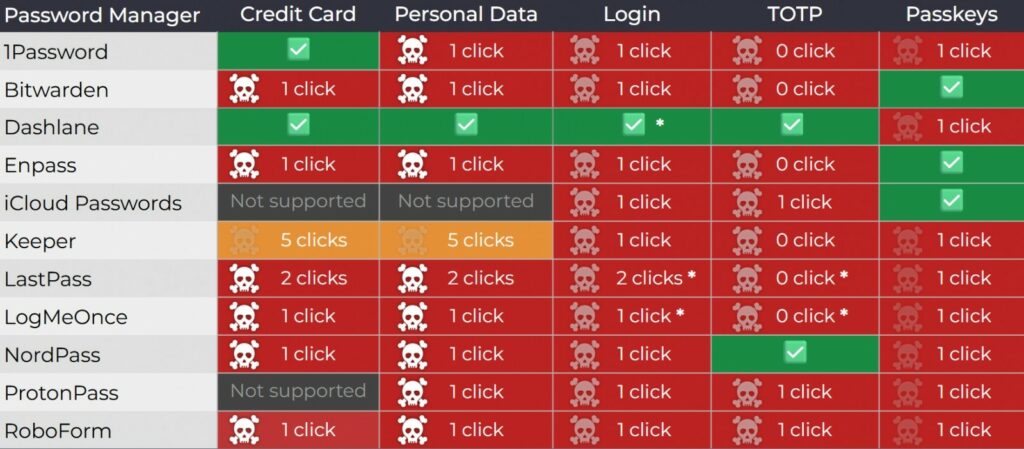
Di conseguenza, il ricercatore ha testato 11 gestori di password per individuare la vulnerabilità al clickjacking e ha scoperto che tutti erano vulnerabili ad almeno uno dei metodi di attacco. Sebbene Toth avesse informato tutti i produttori dei problemi già nell’aprile 2025 e li avesse anche avvisati che la divulgazione pubblica delle vulnerabilità era prevista per DEF CON 33, non ci fu alcuna risposta immediata. La scorsa settimana, Socket ha contattato nuovamente gli sviluppatori per ribadire la necessità di assegnare CVE ai problemi nei prodotti interessati.
I rappresentanti di 1Password hanno definito il rapporto del ricercatore “informativo”, sostenendo che il clickjacking è una minaccia comune da cui gli utenti dovrebbero essenzialmente proteggersi. Anche gli sviluppatori di LastPass hanno trovato il rapporto “informativo” e Bitwarden ha riconosciuto i problemi e, sebbene l’azienda non li abbia considerati gravi, le correzioni sono state implementate nella versione 2025.8.0, rilasciata la scorsa settimana. I seguenti gestori di password, che complessivamente contano circa 40 milioni di utenti, sono attualmente vulnerabili agli attacchi di clickjacking:
Le patch sono già state implementate nei loro prodotti: Dashlane (v6.2531.1 rilasciata il 1° agosto), NordPass, ProtonPass, RoboForm e Keeper (17.2.0 rilasciata a luglio). Ora si consiglia agli utenti di assicurarsi di aver installato le versioni più recenti disponibili dei prodotti.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…