
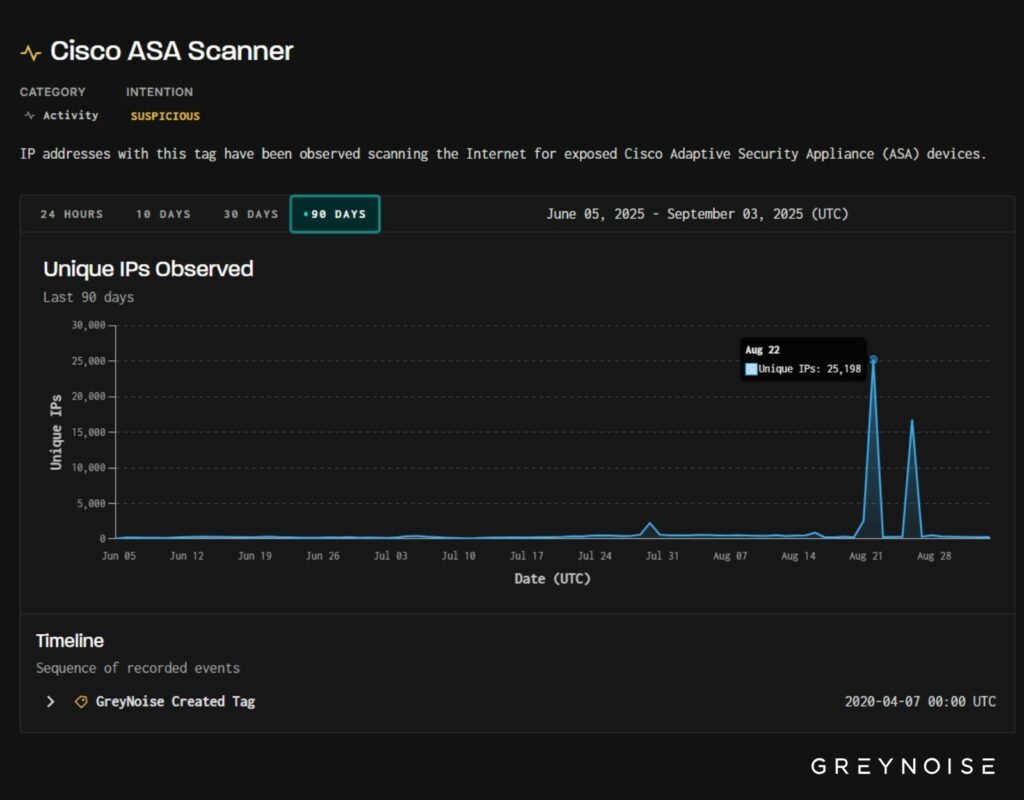
A fine agosto, GreyNoise ha registrato un forte aumento dell’attività di scansione mirata ai dispositivi Cisco ASA. Gli esperti avvertono che tali ondate spesso precedono la scoperta di nuove vulnerabilità nei prodotti. Questa volta, si tratta di due picchi: in entrambi i casi, gli aggressori hanno controllato massicciamente le pagine di autorizzazione ASA e l’accesso Telnet/SSH in Cisco IOS.
Il 26 agosto è stato osservato un attacco particolarmente esteso, avviato da una botnet brasiliana, che ha utilizzato circa 17.000 indirizzi univoci e ha gestito fino all’80% del traffico. In totale, sono state osservate fino a 25.000 sorgenti IP. È interessante notare che entrambe le ondate hanno utilizzato intestazioni di browser simili, mascherate da Chrome, a indicare un’infrastruttura comune.
Gli Stati Uniti erano l’obiettivo principale, ma anche Regno Unito e Germania sono stati monitorati.
Secondo GreyNoise, circa l’80% di tali ricognizioni si traduce nella successiva scoperta di nuove problematiche di sicurezza, sebbene la correlazione statistica sia notevolmente più debole per Cisco rispetto ad altri produttori. Ciononostante, tali indicatori consentono agli amministratori di rafforzare in anticipo le proprie difese.
In alcuni casi, questi potrebbero essere tentativi falliti di sfruttare bug già chiusi, ma una campagna su larga scala potrebbe anche essere mirata a mappare i servizi disponibili per un ulteriore sfruttamento di vulnerabilità non ancora divulgate.
Un amministratore di sistema indipendente con il nickname NadSec – Rat5ak, ha segnalato un’attività simile iniziata a fine luglio e che ha preso slancio fino al 28 agosto. Ha registrato oltre 200.000 richieste ad ASA in 20 ore con un carico uniforme di 10.000 richieste da ciascun indirizzo, il che indica una profonda automazione. Le fonti erano tre sistemi autonomi: Nybula, Cheapy-Host e Global Connectivity Solutions LLP.
Si consiglia agli amministratori di installare gli ultimi aggiornamenti di Cisco ASA il prima possibile per chiudere le falle note, abilitare l’autenticazione a più fattori per tutti gli accessi remoti e non pubblicare direttamente pagine /+CSCOE+/logon.html, Web VPN , Telnet o SSH.
In casi estremi, si consiglia di esternalizzare l’accesso tramite un concentratore VPN, un reverse proxy o un gateway con verifica aggiuntiva.
È inoltre possibile utilizzare gli indicatori di attacco pubblicati da GreyNoise e Rat5ak per bloccare le richieste sospette sul perimetro e, se necessario, abilitare il geo-blocking e la limitazione della velocità. Cisco non ha ancora rilasciato dichiarazioni in merito.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…