
Specialists at Solar 4RAYS of Solar Group have discovered a new hacker group, Proxy Trickster, dedicated to cryptocurrency mining and proxyjacking (interception of server control for conversion and sale). Over the course of a year, attackers targeted nearly 900 servers in 58 countries. In March 2025, specialists investigated a cybersecurity incident at an IT company and discovered the activity of a previously unknown group called Proxy Trickster.
Hackers earn their main income from cryptocurrency mining and proxyjacking, which involves taking control of legitimate servers by exploiting known vulnerabilities, converting them into proxy servers, and then selling them on the darknet to other criminals so they can hide their activities and IP addresses. The first traces of Proxy Trickster attacks date back to May 2024, and the hackers have continued their activities since then.
In the attack studied by the experts, the entry point was not restored, but analysts at Cado Security wrote that the group is using previously discovered vulnerabilities in Selenium Grid. In the case studied by Solar 4RAYS, this software was not used, so the hypothesis arose that the group attacked several public services that already had known vulnerabilities.
Over the course of more than a year of activity, at least 874 devices in 58 countries were infected. The largest number of attacked servers were detected in the United States (16% of the total number of infected servers), Germany (6%), Russia (4%), Ukraine (4%), France (4%), and other countries. From this, the researchers conclude that the geography of the targets doesn’t matter to the hackers: they attack any available server to make money.
The researchers believe the group is more of a group of amateurs, using tools and techniques from professional hackers who attack for espionage and destructive purposes. Proxy Trickster replaces system utilities (ps, pstree, pkill) with custom scripts that mask malicious processes (e.g., [kworker/u8:1-events_unbound]) from system administrators and also uses multi-level attack automation.
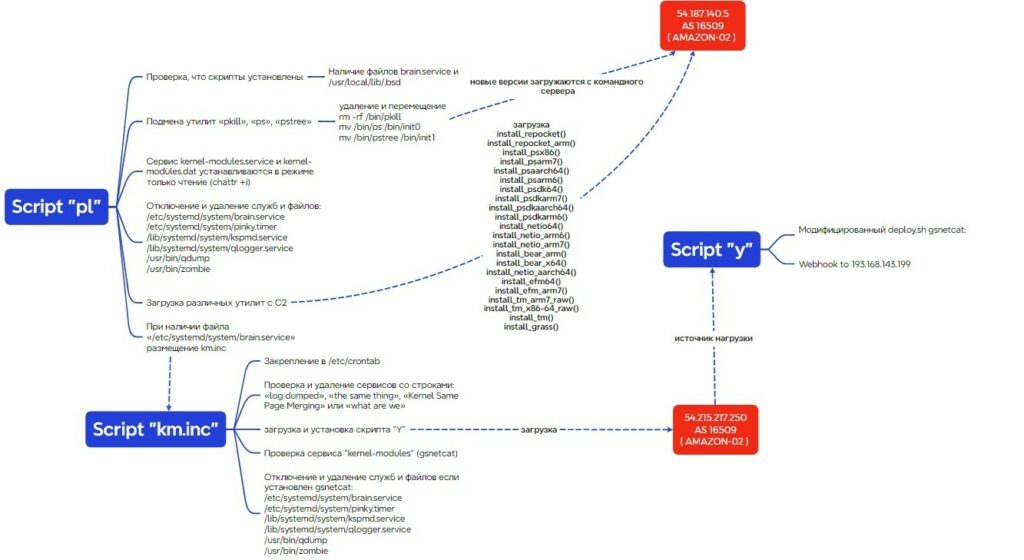
General diagram of how the script works
Furthermore, the group retains access to the attacked servers, which, in theory, allows for more complex attacks. In other words, the group could pose a threat to hundreds, if not thousands, of companies.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
