
We know that criminal hackers always manage to surprise us, and this time too they surprise us with the innovation and ways they invent to overcome obstacles, such as anti-spam filters.
Cybercriminals have found an unexpected way to bypass email services’ protection against malicious QR codes, and they did it quite elegantly.
Instead of the usual images , they started sending QR codes composed entirely of HTML code. As a result, the emails appear harmless, and security systems often simply don’t recognize them as a hidden phishing attack .
The new campaign was brought to the attention of specialists at the SANS Technology Institute ‘s Internet Storm Center. Between December 22 and 26, a series of phishing emails arrived in their inboxes. The QR codes were “designed” using HTML tables , rather than image attachments, as is usual.
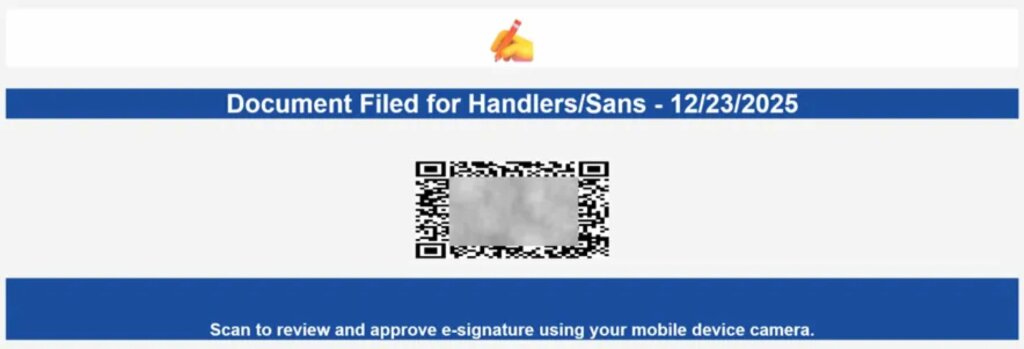
QR code composed of HTML tables (Internet Storm Center)
The trick has proven surprisingly effective. Most existing protection mechanisms look for QR codes in images, but in this case, there’s nothing to analyze . Experts point out that this technique bypasses the automatic detection and analysis of QR codes in emails.
The messages themselves were as simple as possible. A few lines of text and a QR code, without unnecessary details. Recipients were encouraged to scan the code to view and sign the document. Visually, everything seemed plausible and did not arouse suspicion.
Technically, each pixel of the QR code was a separate cell in a 35 x 35 pixel HTML table . The cell’s background was colored black or white, forming a familiar pattern. To the user, this code appeared almost normal, except for its slightly compressed vertically.
After scanning the QR code, the victim was redirected to a phishing site designed to steal their credentials. While the technique itself is not new , its use in real-world attacks once again demonstrates the dangers of relying on established assumptions about how malicious content is distributed.
The study’s authors emphasize that technical measures alone cannot stop all threats, especially when attacks employ a combination of technology and social engineering. In this cat-and-mouse game, attackers constantly seek and find new loopholes, and the story of HTML QR codes is yet another example, undoubtedly aided by a healthy dose of artificial intelligence.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
