The group behind RansomHouse, one of the most notorious ransomware distribution services, has strengthened the technical capabilities of its attacks. According to experts, the cybercriminals have added an updated encryption tool to their arsenal , featuring a more complex architecture and expanded functionality.
The changes affected both the file processing algorithm and the methods that complicate subsequent analysis. RansomHouse has been active since late 2021, initially with data leaks and then with the active use of ransomware in attacks.
The service has developed rapidly, including the release of the MrAgent utility for mass blocking VMware ESXi hypervisors. One of the most recent known incidents involved the use of several ransomware variants against the Japanese e-commerce company Askul.
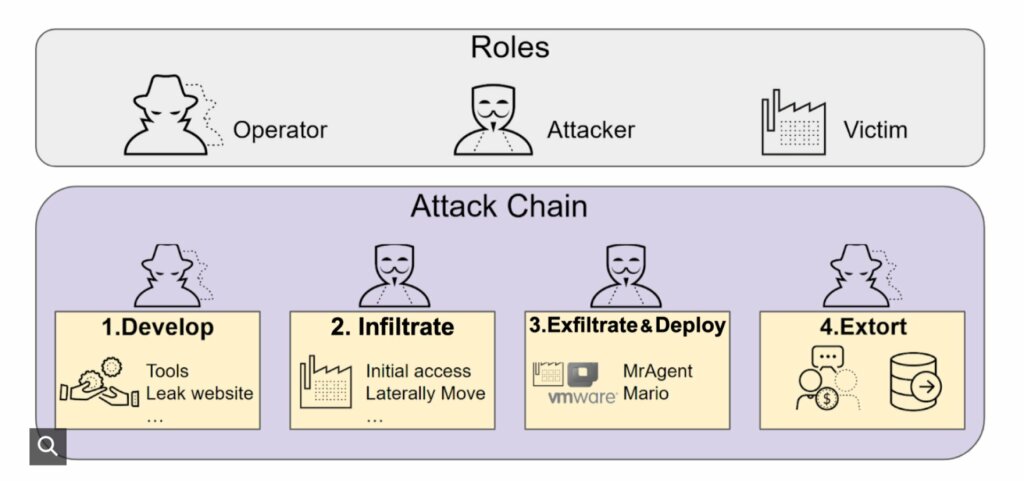
A recent report from Palo Alto Networks Unit 42 describes a new variant of the ransomware called ” Mario .” Unlike the previous version, which used single-stage processing , the updated modification uses a two-stage approach with two keys: a 32-byte primary key and an 8-byte secondary key.
This significantly increases the strength of the encryption and complicates data recovery attempts.
Additional protection is provided by a redesigned file processing mechanism . Instead of a linear scheme, dynamic block splitting is used, with an 8 GB threshold and partial encryption.
The size and processing method of each file depend on its size and are calculated using complex mathematical operations. This approach complicates static analysis and makes the cryptographic system’s behavior less predictable.
The RAM management structure has also been changed: separate buffers are now used for each encryption stage . This increases the complexity of the code and reduces the likelihood of detection during analysis. Furthermore, the new version provides more detailed information during file processing, whereas previously it was limited to a message about task completion.
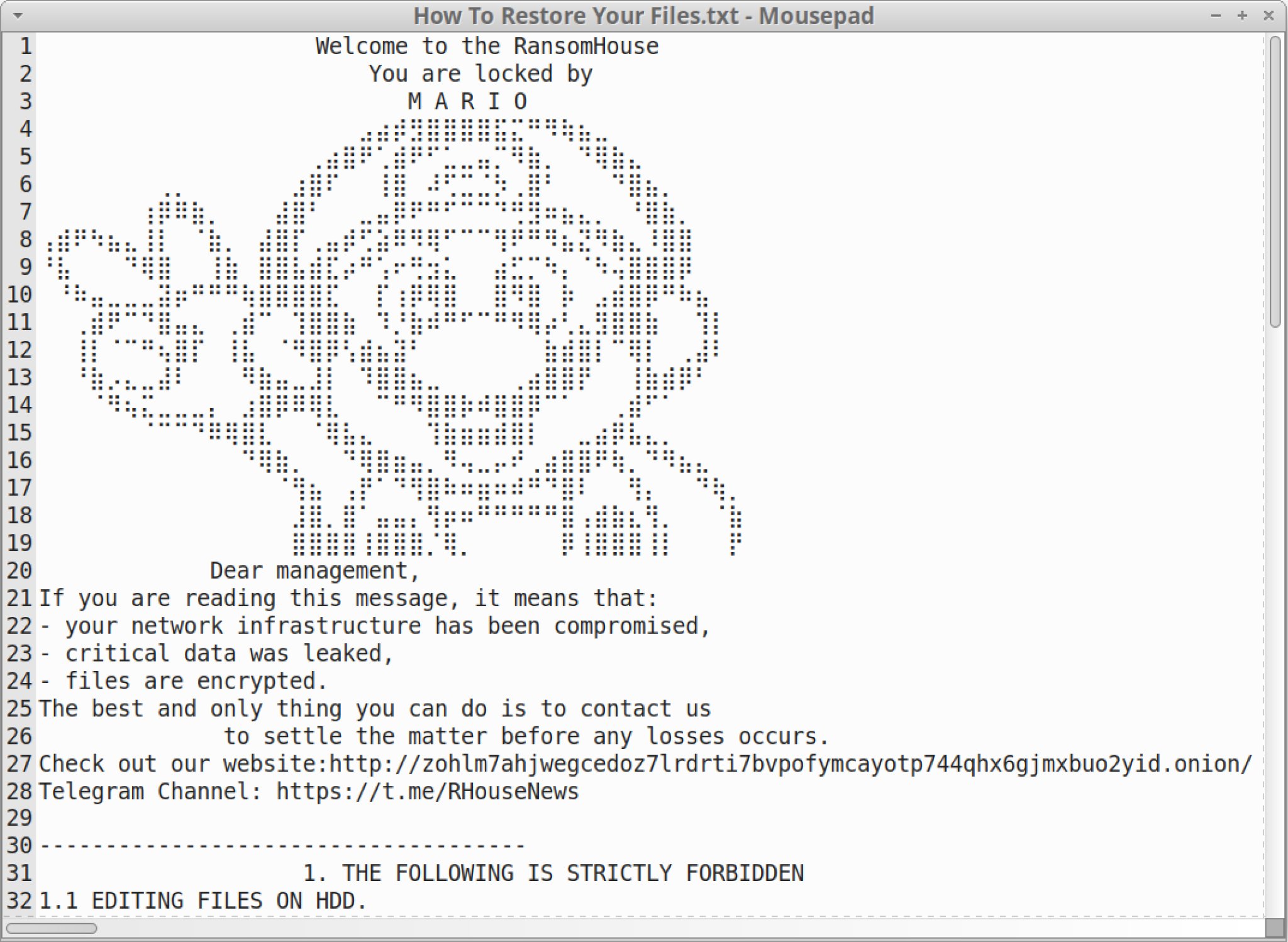
Virtual machine files, which receive the “.emario” extension after encryption, remain the target of attacks. A message with instructions on how to restore access to the data (a ransom note) is left in each affected directory.
Unit 42 specialists emphasize that this evolution of the RansomHouse ransomware is a warning sign. The increased complexity hinders decryption and significantly complicates sample analysis, suggesting a carefully considered strategy focused not on scale, but on efficiency and secrecy.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
