
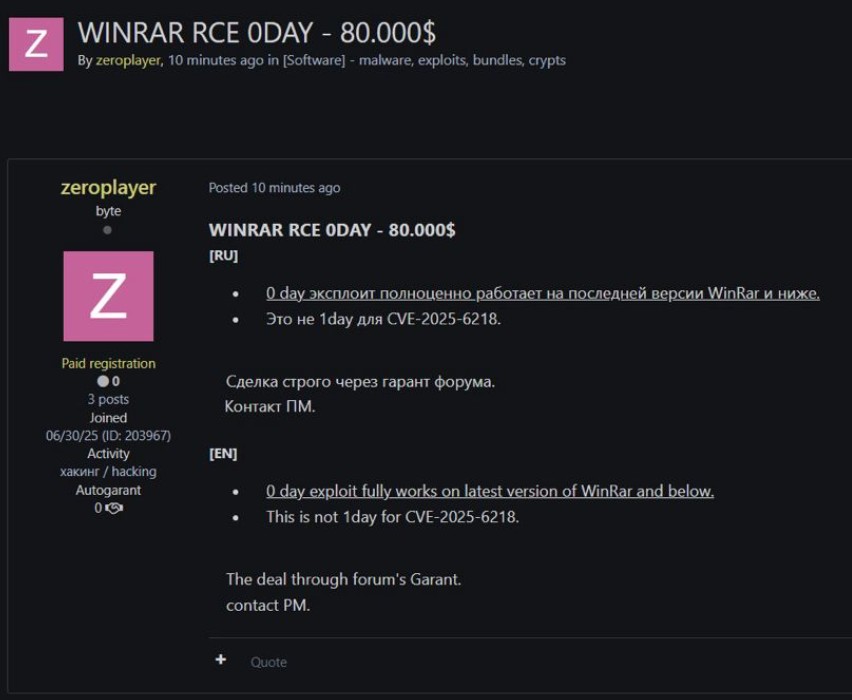
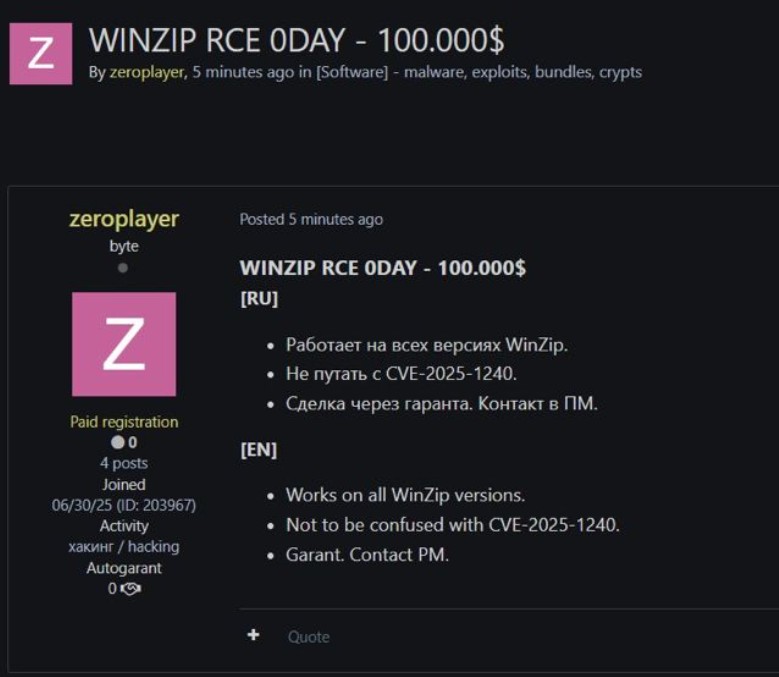
In questi giorni, sul noto forum underground exploit.in, attualmente chiuso e accessibile solo su invito – sono stati messi in vendita degli exploit per una vulnerabilità di tipo 0day che colpiscono i noti software WinRAR e WinZIP. L’annuncio, pubblicato dall’utente zeroplayer, propone tali exploit tra 80.000 e 100.000 dollari.
Specifica che non si tratta di un semplice 1day (cioè un exploit per una vulnerabilità già nota come CVE-2025-6218), ma di un bug sconosciuto e non ancora patchato.
Gli exploit sono strumenti o porzioni di codice che permettono di sfruttare vulnerabilità software per ottenere comportamenti non previsti dal programma, come l’esecuzione di codice malevolo, il furto di dati o il controllo completo di un sistema.
Quando parliamo di 0day, intendiamo vulnerabilità che non sono ancora conosciute dal produttore del software e per le quali non esistono patch: proprio per questo motivo sono particolarmente preziose nel mercato nero e incredibilmente pericolose.
WinZIP e WinRAR sono i software più utilizzati al mondo per la gestione di archivi compressi come file ZIP e RAR. Una vulnerabilità RCE (Remote Code Execution) su questo tipo di programma permette a un attaccante di far eseguire codice malevolo semplicemente inducendo la vittima ad aprire o visualizzare un archivio compromesso.
Un possibile scenario d’attacco prevede l’uso di email di phishing, in cui l’utente riceve un allegato ZIP o RAR apparentemente innocuo. Basta un clic per attivare l’exploit e compromettere completamente il sistema, installando malware, ransomware o backdoor per il controllo remoto.
Forum chiusi come exploit.in fungono da veri e propri marketplace per la compravendita di vulnerabilità, malware, dati rubati e altri strumenti usati nel cybercrime. Gli utenti che vendono exploit, come nel caso di zeroplayer, spesso offrono garanzie di affidabilità attraverso servizi interni chiamati Garant, che fanno da intermediari per evitare truffe tra criminali.
L’utente zeroplayer, che ha pubblicato gli annunci, appare come un profilo nuovo e ancora privo di una reputazione consolidata. Registrato sul forum exploit.in solo il 30 giugno 2025, conta appena 3 post e non ha ancora concluso transazioni certificate tramite il sistema di Garant interno alla piattaforma, che solitamente serve a ridurre il rischio di truffe tra venditori e acquirenti.
Sebbene abbia effettuato una registrazione a pagamento, pratica comune nei forum underground più chiusi per filtrare account fake e inattivi, questo elemento da solo non basta a definirlo affidabile agli occhi della community. Un account così recente potrebbe indicare due scenari contrapposti: da un lato, un vendor realmente in possesso di un exploit molto prezioso che sceglie di aprire un nuovo profilo per motivi di anonimato; dall’altro, un tentativo di frode per monetizzare la paura attorno a una vulnerabilità critica e ancora sconosciuta. La mancanza di feedback e attività passata rende difficile distinguere tra le due possibilità, ma sottolinea quanto sia complesso — perfino nei circuiti del cybercrime — fidarsi senza prove concrete dell’esistenza e dell’efficacia dell’exploit offerto.
La vendita di un exploit 0day per WinRAR rappresenta una seria minaccia, vista la diffusione globale del software. È un ulteriore richiamo all’importanza di mantenere i programmi sempre aggiornati, usare strumenti di sicurezza affidabili e prestare la massima attenzione alle email sospette, soprattutto se contengono allegati compressi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…