
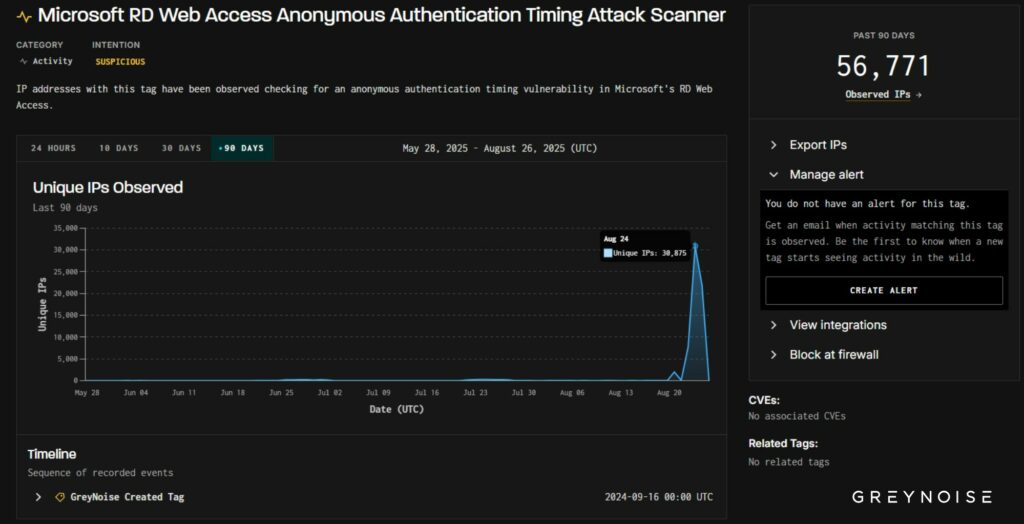
Security researchers at greyNoise have detected a large, coordinated scanning operation against Microsoft Remote Desktop Protocol (RDP) services, in which attackers scanned over 30,000 unique IP addresses to assess vulnerabilities in the Microsoft RD Web Access and RDP Web Client authentication portals.
The attack methodology focuses on time-based authentication enumeration, a technique that exploits subtle differences in server response times to identify valid usernames without triggering traditional brute-force detection mechanisms.
This approach allows attackers to create comprehensive lists of targets for subsequent credential stuffing and password spraying, while maintaining maximum operational discretion.
The campaign, reports researchers at GrayNoise, represents one of the largest coordinated RDP reconnaissance operations observed in recent years,signaling potential preparedness for large-scale credential-based attacks. The scanning operation began with a first wave on August 21, 2025, targeting nearly 2,000 IP addresses simultaneously.
The timing of the campaign coincides with the back-to-school season in the United States, when educational institutions typically deploy RDP-enabled lab environments and remote access systems for incoming students. This targeting window is strategically significant, as educational networks often implement predictable username patterns (student IDs, firstname.lastname formats) that facilitate enumeration attacks.
Network telemetry analysis reveals that 92% of the scanning infrastructure consists of previously classified malicious IP addresses, with The traffic was heavily concentrated in Brazil (73% of observed origins) and targeted exclusively at US-based RDP endpoints.
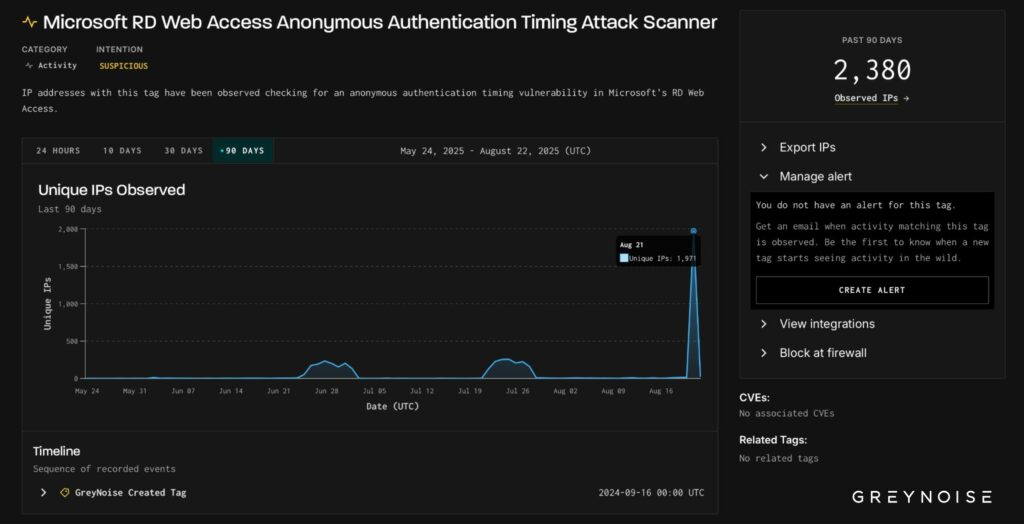
However, the campaign escalated dramatically on August 24, when security researchers detected over 30,000 unique IP addresses conducting Coordinated investigations using identical client signatures, indicating a sophisticated botnet infrastructure or coordinated toolset deployment. Consistent client signature patterns across 1,851 of the initial 1,971 scanning hosts suggest a centralized command and control infrastructure typical of advanced persistent threat (APT) operations.
The threat actors are conducting multi-stage reconnaissance operations, first identifying exposed RD Web Access and RDP Web Client endpoints, then testing authentication workflows for information disclosure vulnerabilities. This systematic approach enables the creation of comprehensive target databases containing valid usernames and accessible endpoints for future exploitation campaigns.
Security researchers observed that the same IP infrastructure was observed performing parallel scans for open proxy services and web crawling operations, indicating a multipurpose threat toolkit designed for comprehensive network reconnaissance.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
