
Kaspersky Lab experts have detected a new wave of attacks by the RevengeHotels group. A distinctive feature of this campaign is that many of the new malware samples were created using artificial intelligence.
RevengeHotels (also known as TA558) has been active since 2015 and specializes in stealing credit card data from hotel guests and travelers. Criminal hackers typically send emails with phishing links that redirect visitors to websites disguised as document storage sites. These websites download malicious scripts that infect the targeted computers.
The final payloads are various remote access trojans (RATs) that allow attackers to control compromised systems, steal sensitive data, gain a foothold in the infrastructure, and so on.
In the summer of 2025, specialists detected new attacks by the group against hotels, using increasingly sophisticated systems and tools. The group’s primary targets were hotels in Brazil, but targets were also identified in several Spanish-speaking countries: Argentina, Bolivia, Chile, Costa Rica, Mexico, and Spain.
In previous campaigns, the RevengeHotels group targeted users in Russia, Belarus, Turkey, Malaysia, Italy, and Egypt.
This time, the attackers continued to send phishing emails (disguised as invoices, hotel booking requests, or hospitality job applications) to distribute VenomRAT using JavaScript and PowerShell-based loaders.
The analysis demonstrated that a significant portion of the initial infection and implant loading code in these campaigns may have been generated using LLM agents. Researchers believe attackers are actively using artificial intelligence technologies to improve their capabilities.
“Although the RevengeHotels signature remains recognizable, attackers are refining their methods. In particular, a significant portion of the malicious code was presumably written using large-scale language models (LLM). This indicates the active use of artificial intelligence technologies to improve the effectiveness of cyberattacks. It is important to understand that banking and other sensitive data may be at risk. Even on the websites of large and well-known hotels, so caution is always essential,” comments Dmitry Galov, head of Kaspersky GReAT in Russia.
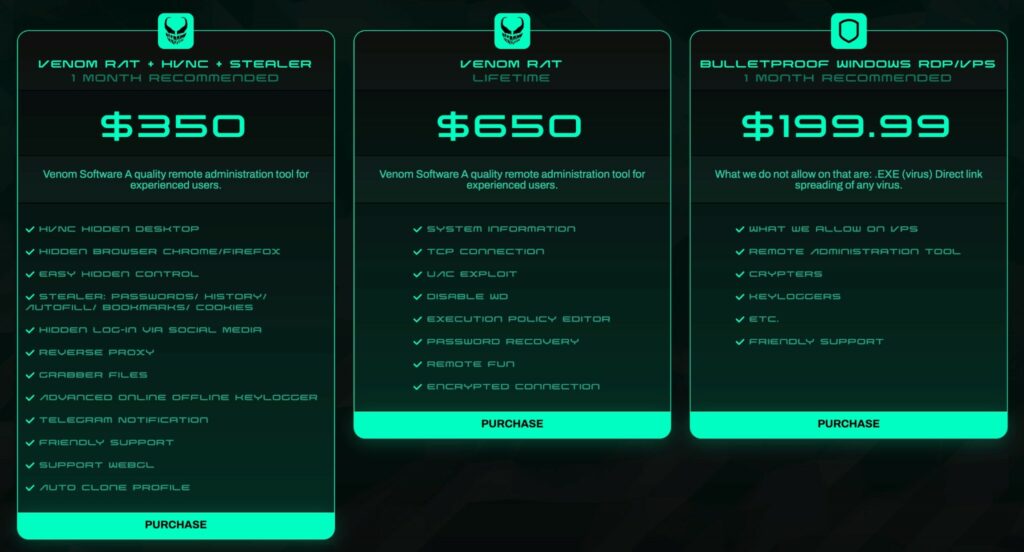
VenomRAT is an updated version of the open-source QuasarRAT trojan, first discovered in mid-2020. VenomRAT is distributed on the darknet, with a price of up to $650 for a lifetime license. Despite the VenomRAT source code leak, the malware continues to be sold and used by attackers.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
