
Author: Dott. Luca Mella, Cyber Security Expert (founder doubleextortion.com)
Translate: Vincenzo Marcovecchio
Pubblication Date: 5/02/2022
In recent years, the ransomware phenomenon has been so disruptive that it heavily influences the security agendas of many companies, organizations, and beyond.
The disruptive brutality of the cyber-criminal practices of double extortion has even influenced the political decisions of the United States and the European Union: these attacks have increasingly revealed themselves as instruments of geopolitical pressure in the dialectics between the nations of the Atlantic Pact and the states under Russian influence.
Monitoring modern ransomware attacks, double extortion, one of the “game-changers” that is most affecting the world and national cyber security landscape, is the underlying reason for the Ransomware Data Room, an observatory, a virtual place where to monitor the phenomenon of ransomware through the factuality of data and news.
Information and data on cyber extortion attempts and ransomware attacks are acquired through OSINT data, public news, open data, and through the doubleextortion.com portal.
Data Room: January 2022 The Ransomware Data Room found evidence of at least 153 cyber extortion attempts and criminal attacks by 24 active threat actors during the reporting period.
The attacks observed were distributed constantly in the first part of the month, at the end of the Italian Christmas holidays and close to the Orthodox holidays. At this juncture, activity peaks were recorded on 12 January 2022 and 17 January 2022, the date of publication of the data leak of the Italian luxury giant Moncler by the new cyber criminal group Alphvm / BlackCat.
Subsequently, a marked increase in activity was recorded between 25 and 27 January 2022 due to an intense operation of the LockBit and Snatch groups, where the potential involvement of the French Ministry of Justice among the victims of extortion attempts was found.
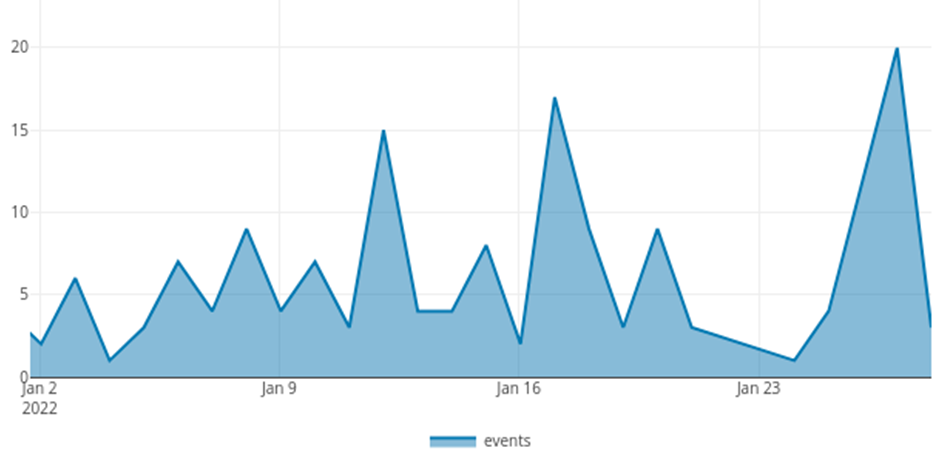
Figura. Profilo dei tentativi di estorsione registrati nel Gennaio 2022.
Organizations from 33 nations were subjected to ransomware double extortion attempts in January 2022, cumulatively, the West is confirmed as the prime target of this disruptive phenomenon.
However, among these, five stand out for the volume of attacks: the United States, the first country on which cyber criminal organizations insist, but also France, United Kingdom, Germany and Italy to represent the European economic area as another cornerstone of extortion interests for cyber criminal gangs.
Of particular interest in this situation is a fierce intensification recorded in the second half of the period, towards the French realities which even involved central government bodies such as the French Ministry of Justice, with timing and circumstances that widen to great question marks on the possible correlations with the international tensions for Ukrainian demand
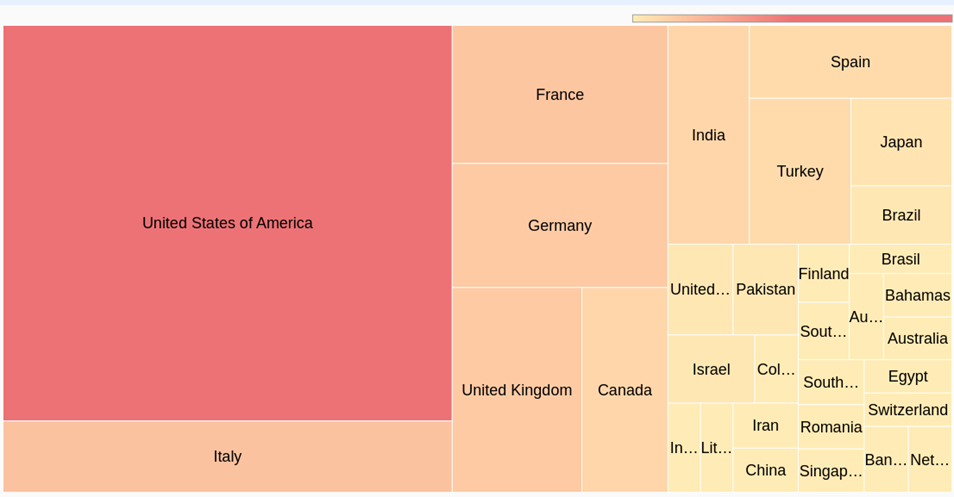
Figura. Nazioni più impattate da estorsioni cyber a Gennaio 2022
The verticals impacted by the extortion were over 60, but among these some with more insistence. The construction and infrastructure supply chain has been among the most affected by cyber-criminal operations, together with manufacturing, the backbone of Western economies.
There are also a series of attacks on companies that deal with providing services to support the business, such as accounting, management consulting, management support and recruiting, but this is not the only surprise: companies operating in financial services are also heavily involved in criminal extortion attempts. This data is of great concern, especially due to the strong regulation that has always characterized this vertical and the sensitivity of the information processed.
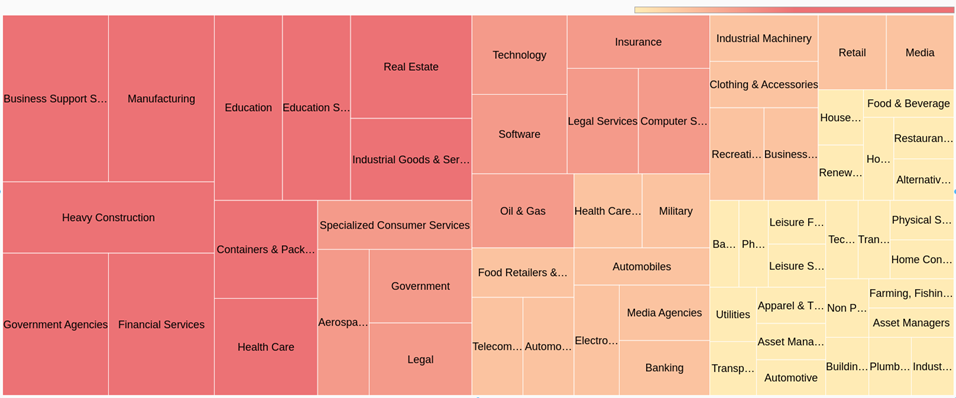
Figura. Settori produttivi più impattati da estorsioni a Gennaio 2022
Among the numerous cases of attacks recorded in January 2022, the observatory assessed the following cases of attempted double extortion as having a particularly significant scope and implication for the respective sectors and contexts of reference:
In January 2022, the observatory records the following ransomware extortion as most relevant in the Italian context:
Globally, the observatory reports the following cases and events impacting the world of ransomware of international importance:
In this month, a new extortion method was detected, related to the DeadBolt ransomware, which hit through a zeroday, the NAS of the famous vendor QNAP. Specifically, the cyber gang, in addition to targeting NAS owners, asking for the encryption key 0.03 bitcoin (about 1,100 dollars), turned to QNAP itself saying that if it is willing to pay 5 Bitcoins of the value of 184,000 dollars, would have provided the exploit of the zeroday used. Furthermore, in the message, they always asked QNAP for the figure of 50 bitcoins worth about 1.9 million dollars, to release the main decryption key to unlock all the victims of the infection.
We are also witnessing an increase in the RaaS offer related to Linux ransomware, in fact as well as in HelloKitty, BlackMatter, Revil, AvosLocker and Hive, recently LOCKBIT has focused part of its efforts to compromise virtual machines hosted on Linux servers And then activate the encryption payload. This denotes an interest that we are moving from physical servers to virtual machines that today are used by all companies to save computer resources, consolidate servers and simplify backup operations.
Furthermore, confidential sources have reported the use of secondary extortion practices by sending threatening communications to customers of companies victim of ransomware attack as seen in the Italian scene.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.