
The Russian cybercrime ecosystem has entered a phase of profound transformation, triggered by a combination of factors: unprecedented international pressure from law enforcement agencies, a shift in domestic priorities, and the persistent, yet evolving, links between organized crime and the Russian state.
A key event was Operation Endgame , launched in May 2024, a multinational initiative aimed at targeting ransomware groups, money laundering services, and related infrastructure, including within Russian jurisdictions. In response, Russian authorities conducted a series of high-profile arrests and seizures.
These actions mark a departure from Russia’s historical stance of near-total non-interference with domestic cybercriminals. The traditional concept of Russia as a ” safe haven ” for these actors is becoming more complex, increasingly conditional and selective. This analysis is based on a recent report by experts at Recorded Future, a US organization with which Red Hot Cyber actively collaborates on intelligence activities .
Leaked chats and investigative reports have confirmed that prominent cybercrime figures have long maintained relationships with Russian intelligence services . These contacts include providing data, performing specific tasks, or exploiting political connections and corruption to ensure impunity.
Recorded Future , through analyses by its Insikt Group , found that the Russian government’s relationship with cybercriminals has evolved from passive tolerance to active management . Since 2023, a clear shift has been observed: selective law enforcement, orchestrated arrests, and public ” examples ” used to strengthen state authority. Intercepted communications even reveal direct operational coordination between criminal leaders and intelligence intermediaries.
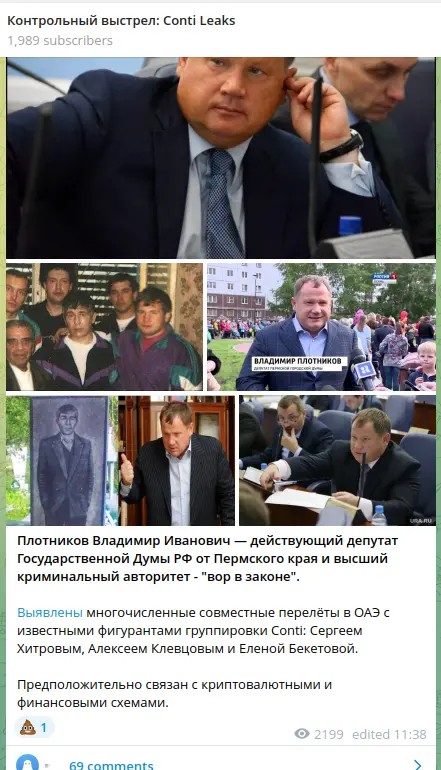
This dynamic falls within the “Dark Covenant” framework , which describes a network of relationships (direct, indirect, and tacit) linking the Russian cybercrime world to state forces. In this context, cybercrime is not just a commercial business, but also a tool for influence, a means of acquiring information , and accountable only when it threatens internal stability or harms Russian interests.
Within the underground community, growing state interference and international operations have undermined trust . Data collected by Recorded Future on the dark web indicates that Russian cybercrime is fracturing under the dual pressure of state control and domestic distrust.
This double pressure accelerated operational adaptations:
At the same time, Western governments have toughened their policies, considering ransom bans , introducing mandatory incident reporting, and even offensive cyber operations.
This more aggressive stance coincides with negotiations and prisoner exchanges. Insikt Group believes Russia is strategically using cybercriminals as geopolitical tools , linking arrests and releases to broader diplomatic cycles.
While Operation Endgame did not dismantle the ransomware-as-a-service (RaaS) model, it did trigger an immediate operational self-discipline within the criminal ecosystem. RaaS operators did not change the basic structure of their business model, but they dramatically increased the threshold for entry to mitigate the risk of detection. Recruitment became more selective: managers now prioritize known networks, intensify screening , and, effectively, outsource the risk of potential infiltration operations to their affiliates.
To maintain the integrity and liquidity of their networks, RaaS operators have introduced more stringent activity and financial collateral requirements. Affiliates who are inactive for a short period ( sometimes as little as 10 or 14 days, depending on the group, such as Mamona or PlayBoy RaaS ) are banned to eliminate potential “dormant” infiltrators. Additionally, for new members, membership capital has been replaced with financial collateral: deposits (for example, $5,000) are required on other reputable forums. This entry fee raises the barriers for scammers and makes infiltration much more costly.
At the same time, groups have refined their targeting rules to avoid attracting political and law enforcement attention. Many operators, including Anubis and PlayBoy RaaS, have formally banned attacks against government entities, healthcare organizations, and non-profits . These restrictions serve both as reputational protection and as an implicit alignment with the “lines not to be crossed” of the Russian Dark Covenant. Minimum ransoms (often $50,000 or more ) have also been imposed to prioritize high-yield victims, and repeated attacks have been prohibited to protect the credibility of negotiations.
In essence, growing external pressure and the increasingly precarious state of state tolerance have pushed the criminal community toward strict self-regulation. As members on dark web forums have complained, the rise of fraud and the influx of unqualified agents have led to a deterioration of reputation-based control. Consequently, criminal markets have shifted toward closed channels and rely on financial guarantees, sacrificing openness for greater resilience and survival.
The Conti Ransomware group and its associated Trickbot network (considered a hotbed of talent and a link to Russian intelligence) have been heavily targeted by European authorities. Despite this pressure, Russia’s response to high-level figures associated with Conti and Trickbot has been modest or ambiguous . Sporadic arrests, such as that of Fyodor Aleksandrovich Andreev (“Angel”) or other Conti members, have been followed by swift releases or scant official coverage.
The lack of enforcement action against other individuals wanted by the EU, such as Iskander Rifkatovich Sharafetdinov (“alik”) or Vitalii Nikolaevich Kovalev (“stern”, “Bentley”), indicates a continued internal protection. Kovalev, the alleged leader of Trickbot/Conti, is believed to have ties to the Russian Federal Security Service ( FSB ).
This protection is multi-level:
Conversely, financial services have been found expendable. In September 2024, US and European authorities seized cryptocurrency infrastructure and funds related to money laundering services Cryptex, PM2BTC, and UAPS . These services, run by Sergey Ivanov , allegedly laundered over a billion dollars in illicit proceeds.
Russia’s reaction was swift and visible: in October 2024, the Russian Investigative Committee ( SKR ) announced the opening of an investigation, the arrest of nearly 100 associated individuals, and the seizure of $16 million in rubles and several properties. The choice to target financial facilitators, rather than the main ransomware operators, demonstrates that Russia acts when international pressure is high and the intelligence value of these services is low. The signal is clear: the Russian “safe haven” is driven by state interests , not the law.
The ecosystem’s evolution will depend on the Russian authorities’ ability to balance external pressures, internal political sensitivities, and the long-term strategic value provided by cybercriminal proxies . Russia presents itself less as a uniform “haven” and more as a controlled market , where state interests determine who enjoys protection and who is repressed.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
