
Autore: Gianluca Tiepolo
APT29 è un gruppo APT (Advanced Persistent Threat) altamente sofisticato che è stato attribuito al Foreign Intelligence Service (SVR) della Russia . Il gruppo è attivo almeno dal 2008 ed è stato coinvolto in un’ampia gamma di campagne di spionaggio e attacchi informatici contro governi, organizzazioni militari, appaltatori della difesa e varie industrie negli Stati Uniti, in Europa e in Asia.
APT29 è anche noto come NOBELIUM (Microsoft), Cozy Bear (Crowdstrike), The Dukes (Kaspersky), JACKMACKEREL (iDefense), BlueBravo (Recorded Future) e UNC2452 (FireEye).
Il gruppo è noto per il suo mestiere sottile e sofisticato nel rubare informazioni geopolitiche: a differenza di altri gruppi sponsorizzati dallo stato russo come APT28 o Sandworm, APT29 non è stato collegato a operazioni dirompenti e opera con molta più discrezione.
Il gruppo è stato attribuito a una serie di attacchi informatici di alto profilo, tra cui:
Nel maggio 2021, è stato rivelato che APT29 era responsabile di un attacco informatico su larga scala a più agenzie governative statunitensi e società private, inclusa Microsoft. Il gruppo ha utilizzato un sistema di email marketing compromesso per inviare e-mail di spear phishing a oltre 3.000 account individuali, con l’installazione di una backdoor che ha consentito agli aggressori di accedere alle reti delle vittime. Il gruppo è stato anche collegato ad altri attacchi informatici significativi, incluso il furto della ricerca COVID-19 da parte di aziende farmaceutiche con sede negli Stati Uniti.
Nel complesso, APT29 è uno dei gruppi APT più sofisticati e dotati di risorse al mondo e le sue TTP sono in continua evoluzione e cambiamento.
APT29 è noto per il suo targeting paziente e persistente delle sue vittime, spesso utilizzando attacchi in più fasi che richiedono settimane o addirittura mesi per essere completati. Di seguito è riportato un elenco dei TTP più importanti del gruppo:
In questa particolare ricerca, mi sono concentrato sull’analisi delle capacità di comando e controllo di APT29.
Questo gruppo di minacce ha una storia di utilizzo di servizi cloud affidabili e legittimi ( come servizi di social media e Google Drive ) per i propri attacchi informatici nel tentativo di integrarsi nel normale traffico di rete ed eludere il rilevamento . Il malware distribuito da APT29 contiene anche la capacità di esfiltrazione dei dati su quegli stessi canali C2. Per esempio:
APT29 ha anche utilizzato metodi di crittografia personalizzati , come quelli trovati nel malware SeaDuke del gruppo in cui è stata generata un’impronta digitale univoca per l’host infetto e la codifica Base64 e la crittografia RC4/AES sono state utilizzate per stratificare i dati durante le comunicazioni con il proprio server C2. Il gruppo ha anche utilizzato tecniche come il ” fronting del dominio ” e i plug-in di offuscamento TOR per creare tunnel di rete crittografati.
L’utilizzo dei social network per le comunicazioni C2 non è una tecnica del tutto nuova: altri gruppi russi come Turla (Orso velenoso) hanno sfruttato i commenti postati su Instagram per ottenere l’indirizzo dei propri server di comando e controllo.
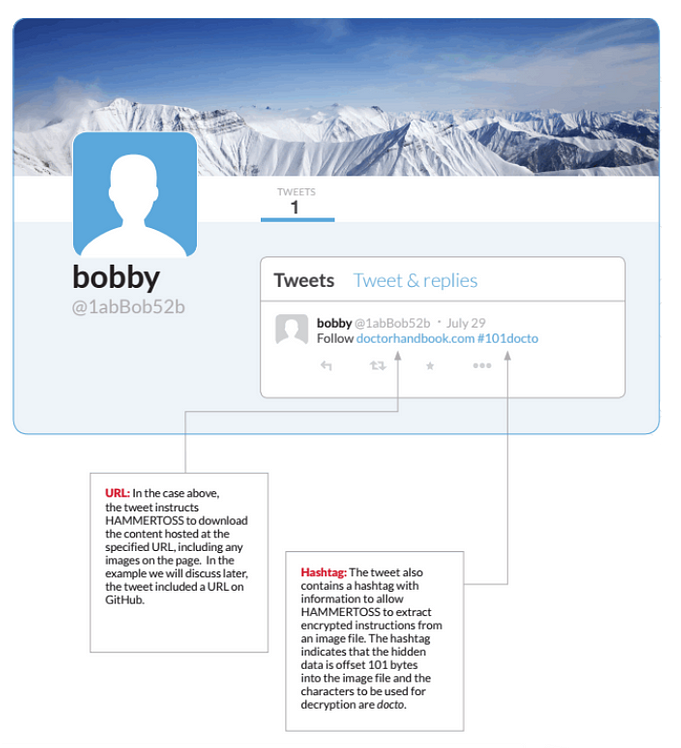
APT29 è stato individuato utilizzando Twitter per controllare le macchine infette già nel 2015: nella campagna HAMMERTOSS , il gruppo è stato in grado di ricevere comandi e inviare dati rubati attraverso il popolare social network, che ha permesso loro di eludere il rilevamento da parte di soluzioni di sicurezza che non monitoravano i social traffico mediatico.
In una campagna più recente risalente a giugno 2021, APT29 ha preso di mira le organizzazioni diplomatiche italiane con una campagna di spear phishing che ha distribuito la backdoor EnvyScout .
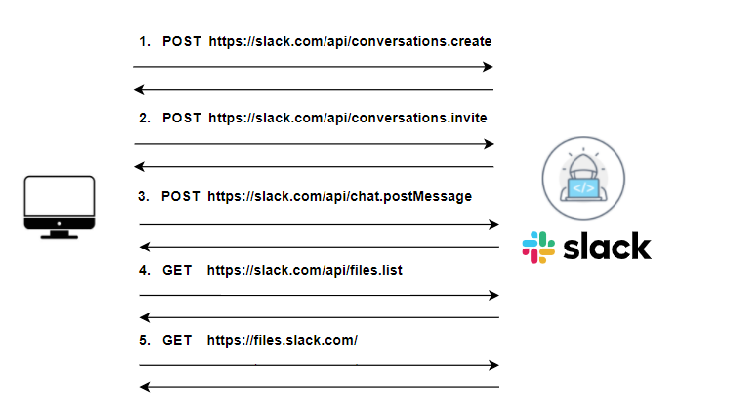
La backdoor chiama prima una funzione per creare un canale Slack personalizzato , aggiungendo l’ID utente dell’attaccante al canale appena creato. La backdoor ottiene il nome utente e il nome host dell’host vittima, aggiunge 4 numeri casuali per formare il nome del canale e invia una richiesta HTTP con un token di autorizzazione all’API Slack.
Dopo che il canale è stato stabilito, la backdoor entra in un ciclo infinito: utilizza la richiesta API “chat.postMessage” per inviare un messaggio beacon al canale appena creato e riceve una risposta con un elenco di file e payload aggiuntivi che vengono scaricati e eseguito sulla macchina di destinazione.
A metà gennaio 2022, APT29 ha lanciato un’altra campagna di spear phishing contro un’entità diplomatica, che è stata rilevata e risolta da Mandiant. Durante le indagini, Mandiant ha scoperto che le e-mail dannose sono state utilizzate per distribuire i downloader BEATDROP e BOOMMIC .
BEATDROP è un downloader scritto in C che sfrutta Trello per la comunicazione Command-and-Control (C2) . Trello è un’applicazione di gestione dei progetti basata sul Web che consente agli utenti di organizzare attività e progetti utilizzando schede, elenchi e schede personalizzabili.
Quando viene eseguito, BEATDROP mappa la propria copia ntdll.dllin memoria per eseguire lo shellcode nel proprio processo. Crea un thread sospeso, quindi enumera il sistema per il nome utente, il nome del computer e l’indirizzo IP per creare un ID vittima. Questo ID vittima viene utilizzato da BEATDROP per archiviare e recuperare i payload delle vittime dal suo C2. Una volta creato l’ID della vittima, BEATDROP invia una richiesta iniziale a Trello per determinare se l’attuale vittima è già stata compromessa. Il payload shellcode viene quindi recuperato da Trello ed è preso di mira per ogni vittima. Una volta che il payload è stato recuperato, viene eliminato da Trello.
Nell’ottobre 2022, ESET Research ha scoperto un campione caricato su VirusTotal che somigliava molto a quello che APT29 aveva utilizzato alcuni mesi fa, con la differenza fondamentale che utilizzava Notion , una piattaforma software per prendere appunti basata su cloud, per Command-and-Control (C&C) comunicazioni.
È possibile abusare dell’API Notion per le comunicazioni C2 incorporando i comandi nell’area di lavoro Notion, a cui accede il malware come se fosse un utente legittimo. Questo uso improprio di Notion consente agli attori delle minacce di eludere il rilevamento e aggirare i controlli di sicurezza , poiché è probabile che il traffico tra il malware e il server Notion venga percepito come traffico legittimo.
I ricercatori ESET sospettano che il downloader distribuito in questa particolare campagna sia stato progettato per raccogliere ed eseguire ulteriori payload dannosi, come Cobalt Strike . La campagna è stata analizzata in modo più dettagliato dai ricercatori di Hive Pro e Recorded Future , che identificano il campione come il malware GraphicalNeutrino .
Secondo Recorded Future, APT29 ha utilizzato un sito Web compromesso con un testo esca di ” Programma dell’ambasciatore novembre 2022 ” per distribuire il file ZIP “programma.zip”, suggerendo che gli obiettivi della campagna sono legati al personale dell’ambasciata o a un ambasciatore . GraphicalNeutrino, il malware utilizzato nell’operazione, funge da caricatore con funzionalità C2 di base e impiega varie tecniche anti-analisi per evitare il rilevamento, tra cui l’unhooking delle API e l’evasione della sandbox.
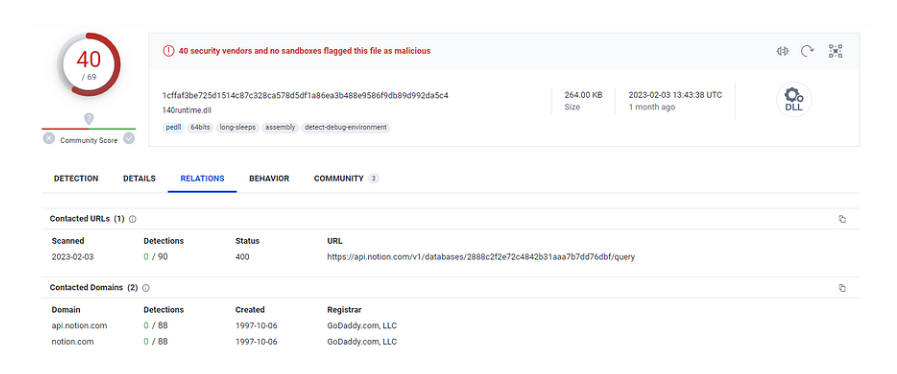
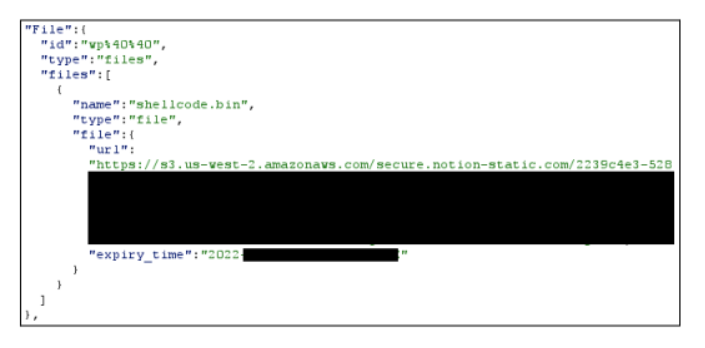
Dopo aver stabilito la persistenza, il malware decrittografa diverse stringhe, tra cui una chiave API Notion e un identificatore di database, e calcola un ID univoco per la vittima in base al nome utente e al nome host. Quindi utilizza l’API di Notion per la comunicazione C2 e per fornire payload aggiuntivi alla macchina della vittima.
Per ogni richiesta al C2, GraphicalNeutrino analizza la risposta in formato JSON e cerca un array ” file “; se l’array non è vuoto, il malware analizzerà il campo dell’URL, scaricherà il file e lo decrittograferà utilizzando una cifratura personalizzata. Una volta decifrato, lo shellcode viene generato indirettamente in un nuovo thread.
L’uso di esche diplomatiche durante periodi di accresciute tensioni geopolitiche, come la guerra in corso in Ucraina, è probabile che sia efficace per i gruppi APT russi, dato il potenziale impatto delle informazioni raccolte da entità o individui compromessi sulla politica estera russa e sulle decisioni strategiche. processi di realizzazione. È forse per questo motivo che APT29 ha adottato le stesse tattiche – in particolare la comunicazione furtiva C2 tramite Notion – per la sua prossima grande campagna, questa volta rivolta alla Commissione europea .
In questa sezione finale del post del blog, sto analizzando una campagna precedentemente sconosciuta attribuita ad APT29 che ha preso di mira la Commissione Europea . Si spera che la precedente introduzione ai TTP e alle campagne del gruppo sia vantaggiosa per il lettore, poiché questo attacco condivide alcune somiglianze con la campagna GraphicalNeutrino che è stata esposta da Recorded Future .
A partire da metà febbraio 2023, una campagna di spear phishing ha preso di mira una serie di indirizzi e-mail relativi a membri della Commissione europea. L’attacco ha comportato la distribuzione di un’immagine .iso dannosa che conteneva un nuovo campione del downloader VaporRage . Una volta eseguito, il malware è stato osservato sfruttare l’ API Notion per distribuire i beacon Cobalt Strike.
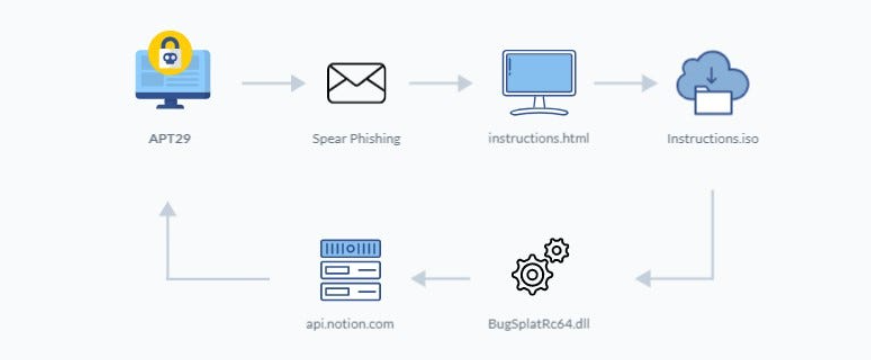
La prima e-mail di phishing, inviata il 13 febbraio 2023, mascherata da avviso amministrativo relativo a documenti disponibili per il download da eTrustEx, una piattaforma di scambio basata sul Web che garantisce la trasmissione sicura di documenti tra i membri della Commissione. Le e-mail esca sono scritte in inglese e sono state consegnate a un numero estremamente mirato di persone chiave che utilizzano la piattaforma eTrustEx.
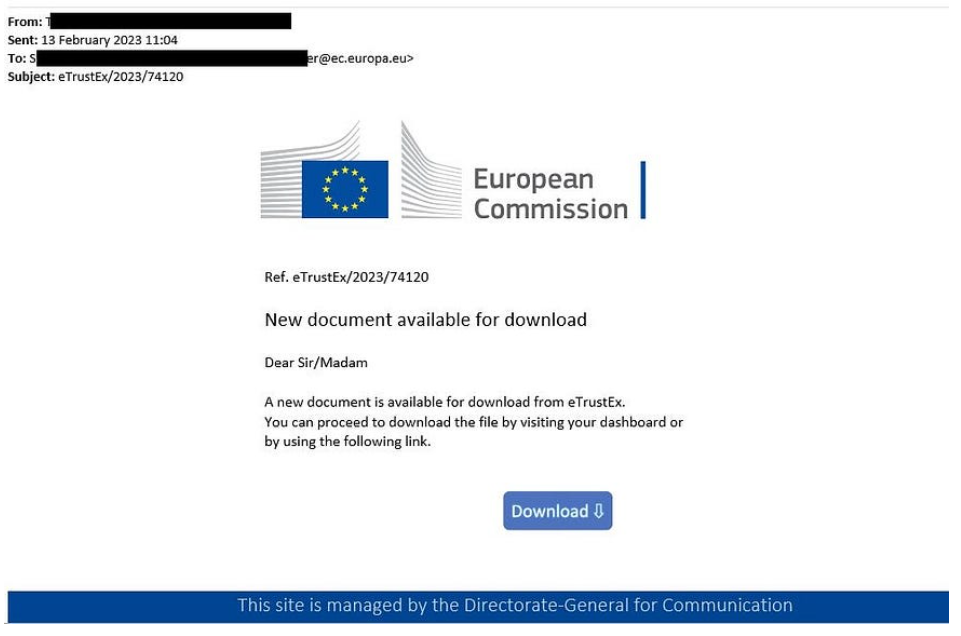
Inoltre, ho notato che in diversi campioni di posta elettronica, i mittenti sono probabilmente account di posta elettronica compromessi appartenenti a organizzazioni governative legittime. Ciò potrebbe indurre le vittime a credere che le e-mail provenissero da partner affidabili, rendendo più probabile che i destinatari facciano clic sui collegamenti.
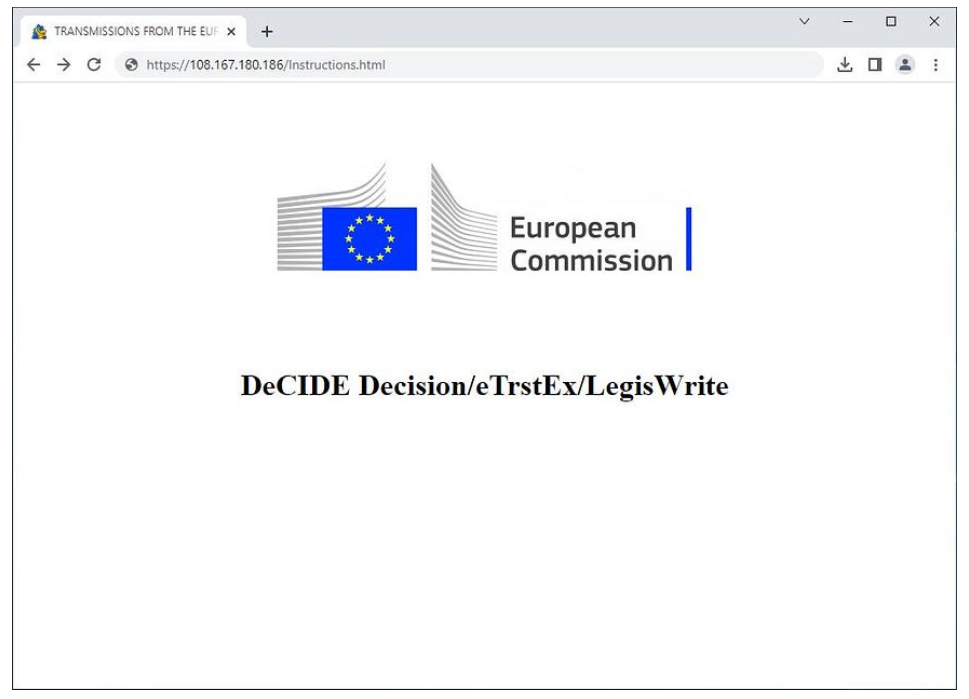
Quando il collegamento viene aperto, la vittima viene reindirizzata a una pagina HTML dannosa ospitata in hxxps://literaturaelsalvador[.]com/Instructions.htmlcui utilizza una tecnica nota come contrabbando HTML per scaricare un’immagine ISO sul sistema di destinazione. Credo che questo dominio non sia di proprietà dell’attore ma sia stato compromesso, il che è in linea con la precedente attività APT29.
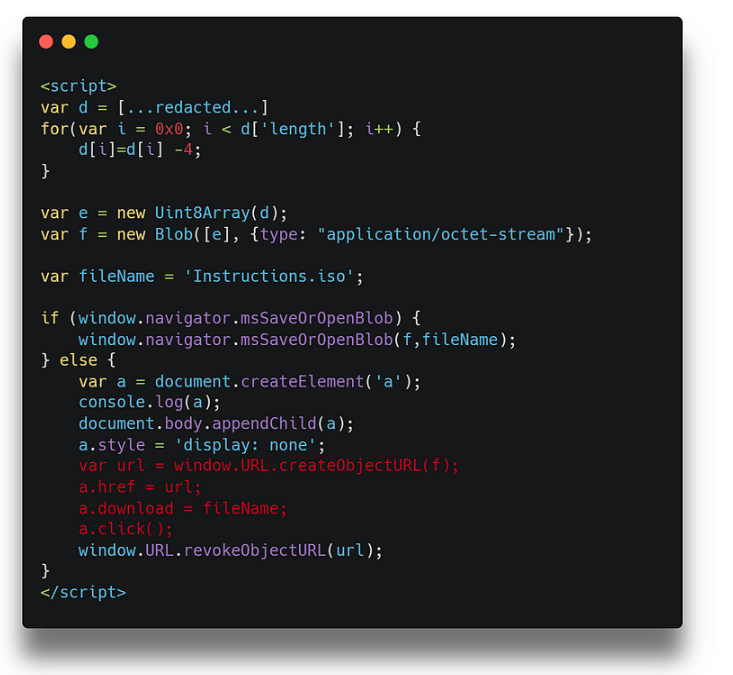
Il file ISO è impostato per il download automatico quando il sito Web viene visitato dalla vittima; questo si ottiene attraverso il seguente codice JavaScript. Il contenuto di Instructions.isoè memorizzato nella dvariabile.
Una volta che il file è stato scritto su disco, quando un utente fa doppio clic su di esso in Windows 10 o versioni successive, l’immagine viene montata e il contenuto della cartella viene visualizzato in Esplora risorse. L’ISO contiene due file: un file di scelta rapida di Windows ( Instructions.lnl) e una DLL dannosa ( BugSplatRc64.dll).
Se l’utente fa clic sul file LNK, viene eseguito il seguente comando, attivando involontariamente l’esecuzione della DLL dannosa.
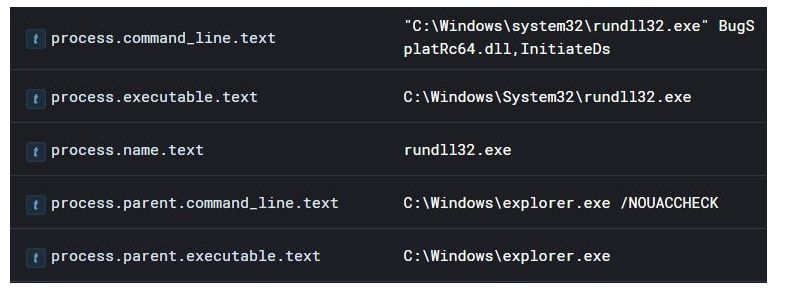
L’utilizzo di scorciatoie LNK per eseguire DLL dannose è una tecnica che è stata associata ad APT29 in numerose campagne. In questo particolare scenario, ho riconosciuto il campione come VaporRage , un downloader utilizzato da APT29 dal 2021 .
Quando viene eseguito con l’ InitiateDsesportazione, VaporRage esegue prima alcuni comandi di ricognizione e genera un host-id codificando in esadecimale il dominio DNS e il nome utente. Quindi, crea una copia di se stesso in:
C:\Users\%USERNAME%\AppData\Local\DsDiBacks\BugSplatRc64.dll
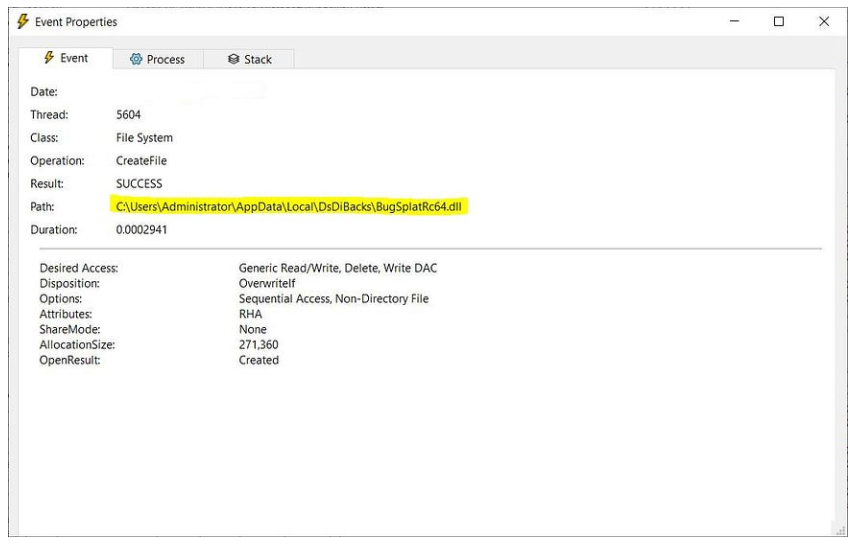
VaporRage stabilisce quindi la persistenza sul sistema compromesso creando una chiave di esecuzione del registro situata in: \Software\Microsoft\Windows\CurrentVersion\Run\DsDiBacks.
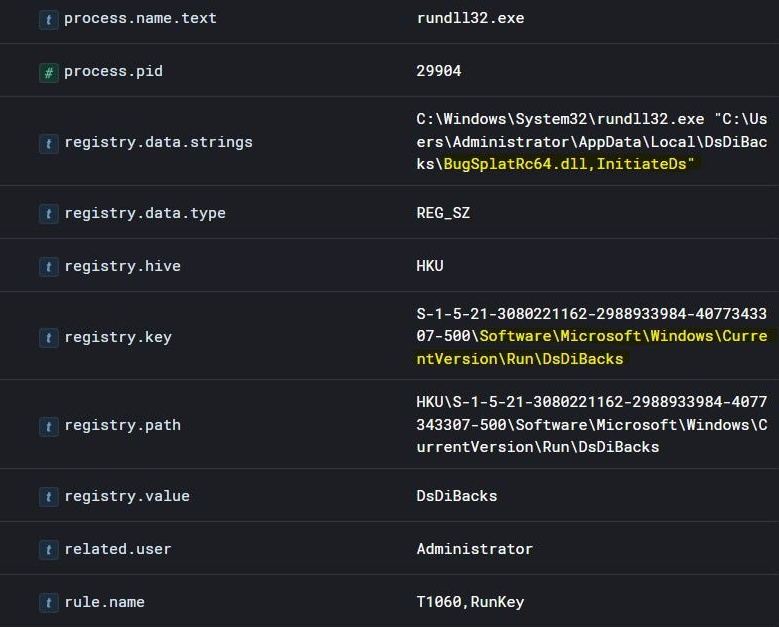
Come ho anticipato all’inizio di questo post, l’esempio VaporRage fornito nella catena di esecuzione sfrutta il suo comando e controllo comunicando su HTTPS utilizzando Notion APIs . La funzione di database di Notion viene utilizzata anche per archiviare le informazioni sulle vittime e mettere in scena ulteriori payload per il download.
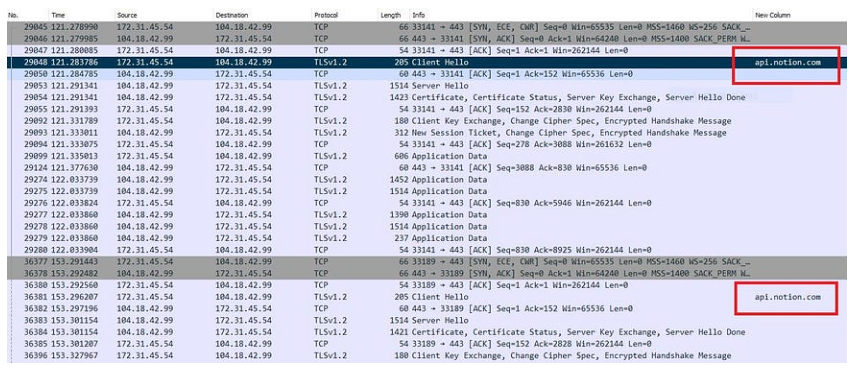
Sulla base delle mie osservazioni, questo campione di VaporRage esegue periodicamente una richiesta POST all’API Notion per verificare la disponibilità di un payload malware di seconda fase , che viene quindi recuperato ed eseguito in memoria. In questa particolare campagna, APT29 ha utilizzato VaporRage per distribuire i beacon Cobalt Strike per stabilire ulteriormente un punto d’appoggio all’interno dell’ambiente.
Il seguente endpoint è stato utilizzato per le comunicazioni C2:
Questa tecnica esemplifica i continui tentativi di APT29 di oscurare le sue azioni e mantenere un accesso continuo ai sistemi bersaglio. Ciò è stato ampiamente documentato da Mandiant , che ha descritto APT29 utilizzando una varietà di tecniche, tra cui attività pianificate , chiavi di esecuzione, certificati dannosi e backdoor in memoria , a volte utilizzando più metodi per ciascun obiettivo.
Nel complesso, l’uso di servizi cloud come Trello e Notion per le comunicazioni C2 non solo fornisce a un attore di minacce maggiori capacità di eludere i controlli di sicurezza della rete, ma aumenta anche la resilienza alle operazioni di rimozione da parte delle forze dell’ordine: i social media e i servizi cloud sono spesso ospitati su più server e posizioni, rendendo più difficile per le autorità rimuovere l’intera piattaforma. Ciò significa che l’autore della minaccia può continuare a utilizzare la piattaforma per le comunicazioni C2 anche se alcuni server vengono disattivati. Questi vantaggi lo rendono un’opzione interessante per i gruppi di minacce come APT29 per condurre le loro attività dannose.
La gamma di tattiche, tecniche e procedure (TTP) utilizzate da APT29 in questa campagna supporta la conclusione che il loro obiettivo è stabilire numerosi mezzi di accesso a lungo termine per facilitare la raccolta di informazioni relative allo spionaggio all’interno delle reti di vittime delle entità governative prese di mira. Le nazioni che hanno un legame con la crisi ucraina, in particolare quelle con significativi legami geopolitici, economici o militari con la Russia o l’Ucraina, affrontano un rischio maggiore di essere prese di mira dall’APT29.
Questo gruppo di minacce ha mostrato un’impressionante capacità di adattarsi rapidamente durante le loro operazioni. Usano metodi innovativi e unici per aggirare i requisiti di rilevamento e autenticazione nei loro ambienti di destinazione. Nelle loro recenti operazioni, il gruppo ha dimostrato una profonda conoscenza della sicurezza operativa, consentendo loro di spostarsi senza problemi tra risorse on-premise e cloud con un uso minimo di malware. Questi fattori, combinati con le loro capacità avanzate di sviluppo di malware, la lunga storia delle operazioni e il tempo prolungato sugli obiettivi, indicano che APT29 è un attore ben finanziato ed eccezionalmente sofisticato e continuerà sicuramente a rappresentare una minaccia durante il 2023.
Di seguito è riportato un elenco di indicatori associati a questa campagna.
Domini
hxxps://literaturaelsalvador[.]com/instructions.html
hxxps://api[.]notion[.]com/v1/databases/37089abc0926463182bb5343bce252cc/query
PI
108[.]167.180.186
104[.]18.42.99
File — SHA256
21a0b617431850a9ea2698515c277cbd95de4e59c493d0d8f194f3808eb16354 (Instructions.iso)
e957326b2167fa7ccd508cbf531779a28bfce75eb2635ab822927B9augRplat.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…