
Recently, a user on the Breachforums known as “cisc0” posted an announcement regarding the sale of a 0Day exploit for GLPI HelpDesk. According to the user, this exploit works on all versions of the software without exception. The news has raised concerns among cybersecurity professionals and organizations that use this IT service management system.
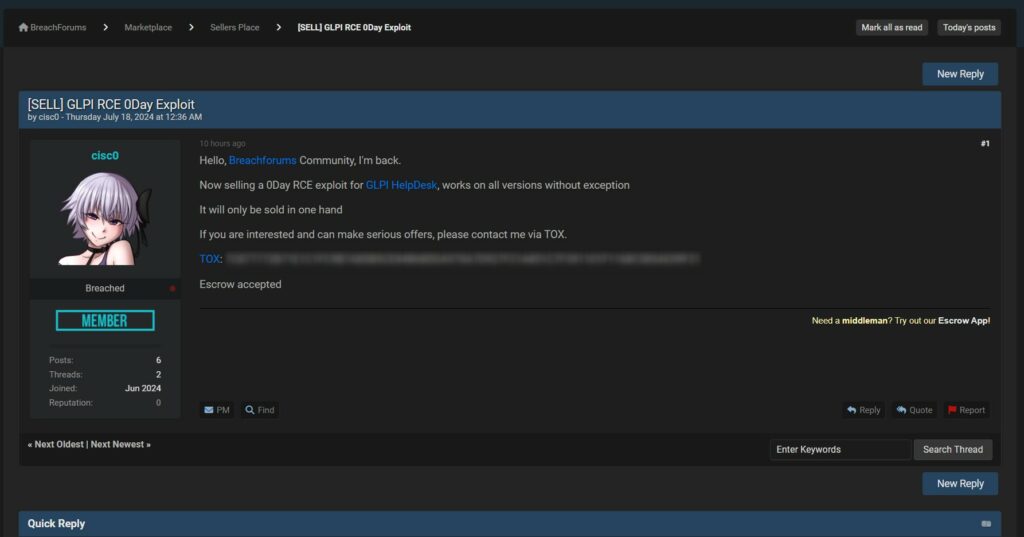
The user “cisc0” claims that the exploit allows remote code execution (RCE) on all versions of GLPI HelpDesk. This type of vulnerability is particularly dangerous as it enables attackers to execute arbitrary commands on the vulnerable server, potentially gaining full control of the system.
At the moment, we cannot accurately confirm the veracity of the breach, as the GLPI organization has not yet released any official press statement on their website regarding the incident. Therefore, this article should be considered an ‘intelligence source’ rather than a definitive confirmation of the data breach.
If confirmed, such an exploit could have serious consequences for organizations using GLPI HelpDesk. System administrators should consider taking preventive measures, such as monitoring systems for suspicious activity, applying security patches as soon as they become available, and, if possible, limiting access to GLPI instances to trusted networks only.
The announcement of the sale of a 0Day exploit for GLPI HelpDesk on Breachforums represents a serious threat to the cybersecurity of organizations using this software. Although the veracity of the vulnerability has not yet been officially confirmed, it is prudent for organizations to adopt preventive measures to protect their systems. Staying updated on official communications and maintaining active vigilance can help mitigate the risks associated with this potential threat.
As is our practice, we always leave room for a statement from the company should they wish to provide updates on the matter. We will be happy to publish such information with a specific article highlighting the issue.
RHC will monitor the evolution of the situation to publish further news on the blog, should there be substantial developments. If there are individuals informed about the facts who wish to provide information anonymously, they can use the encrypted whistleblower email.
Note: This article is based on unconfirmed information and should be considered as a potential intelligence source rather than a definitive verification of the incident.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
