
For a few days now, news has been circulating, which I don’t think has been confirmed by official sources, of a ransomware attack carried out through Samsung’s “corporate fleet” management function ( E-FOTA ).
According to a post by a user on the FibraClick forum , published a few days ago, this attack is also spreading in Italy. Essentially, cybercriminals trick users browsing the web on their Samsung smartphone into opening a specially crafted link like this:
intent://signin.samsung.com/key/yphxkjlx?modelName=SAMSUNG#intent;scheme=https;package=com.osp.app.signin;end.
which opens a pop-up on the victim’s smartphone requesting access through their Samsung account. If the victim approves the login, the smartphone becomes part of the cybercriminal’s ” corporate fleet ,” which then gives the attacker full control of the device (MDM).
Obviously, the opportunity is not missed: the cybercriminal disconnects the victim from their Samsung account and assigns the smartphone to another account , setting the related protection PIN and reporting it as lost/stolen: the victim is effectively cut off from their device. As per the original article that technically describes this attack, published on the XDA-Developers forum (and then removed), ” This security state effectively prevents flashing via Odin, and causes the “KG Status: LOCKED (01)” message to appear in Download Mode. “
At this point the victim is contacted to request a ransom , which must be paid in cryptocurrency, in exchange for the unlock PIN.
Technically, it’s a ransomware attack , although it uses a different method than usual. The attackers take control of the device remotely, holding not only the user’s data hostage, but also the phone itself. According to this article, currently available on archive.org , the attackers use a
Telegram group and an automated bot to facilitate extortion by leaving a ransom note on the device’s lock screen with instructions on how to contact them.
If you’ve been a victim of this attack, it’s extremely important not to pay these scammers. The reason is simple: even if you pay and they unlock your device, all they’ve done is change the status from “lost” to “found.” This means the device is still associated with the cybercriminal’s E-FOTA license and there’s no intention of removing it. The risk is that the attacker could re-lock your smartphone, demanding a ransom again to unlock it. I therefore recommend going to the Postal Police to file a formal complaint, attaching the device’s technical data (IMEI) and requesting Samsung Italy , preferably via certified email, to release the smartphone from the fraudulent MDM.
At the moment the fastest technical solution to prevent attacks of this type on Samsung smartphones is to disable the ” Open supported links ” function from enabled to disabled: Settings -> Applications -> Samsung account -> Set as default -> Open supported links
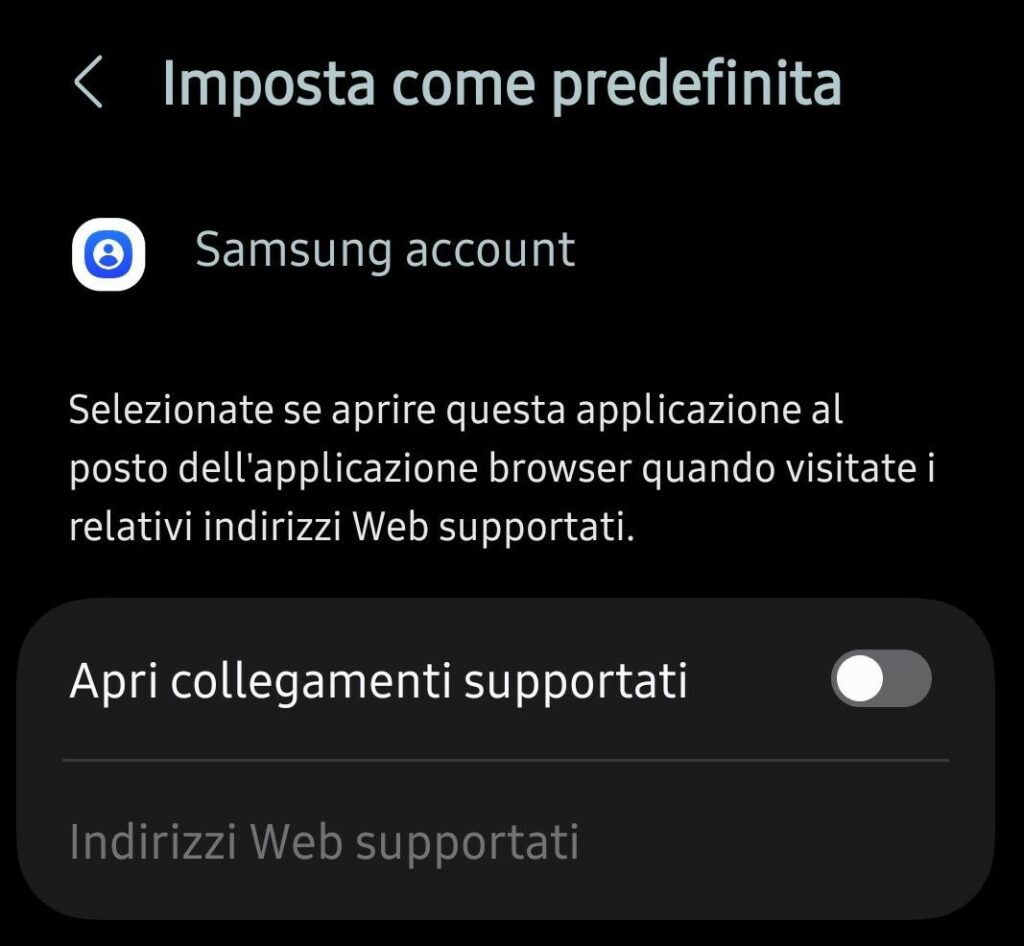
In any case, the same precautionary rules always apply: don’t use your smartphone for websites of dubious security and never click on links without carefully checking them first. Furthermore, when asked to log in using your Samsung account, stop and carefully check what you’re being asked to do.
Technically speaking, Samsung’s E-FOTA feature is perfectly legitimate and used by thousands of businesses without issue. However, the ease with which an attacker can purchase such a license, costing a few dozen dollars, makes this attack quite simple to implement.
Samsung could, if necessary, deactivate the E-FOTA licenses issued to these malicious actors, following a complaint from the victims, releasing the relevant IMEIs and consequently unlocking the smartphones of the unfortunate victims. However, as the aforementioned article emphasizes, ” Samsung has made it extremely difficult for me and others to reach out, with their support team sending generic email responses without escalating the issue to their Knox department.”
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
