
È stato scoperto che i collegamenti di comunicazione satellitare utilizzati da agenzie governative, militari, aziende e operatori di telefonia mobile sono la fonte di un’enorme fuga di dati.
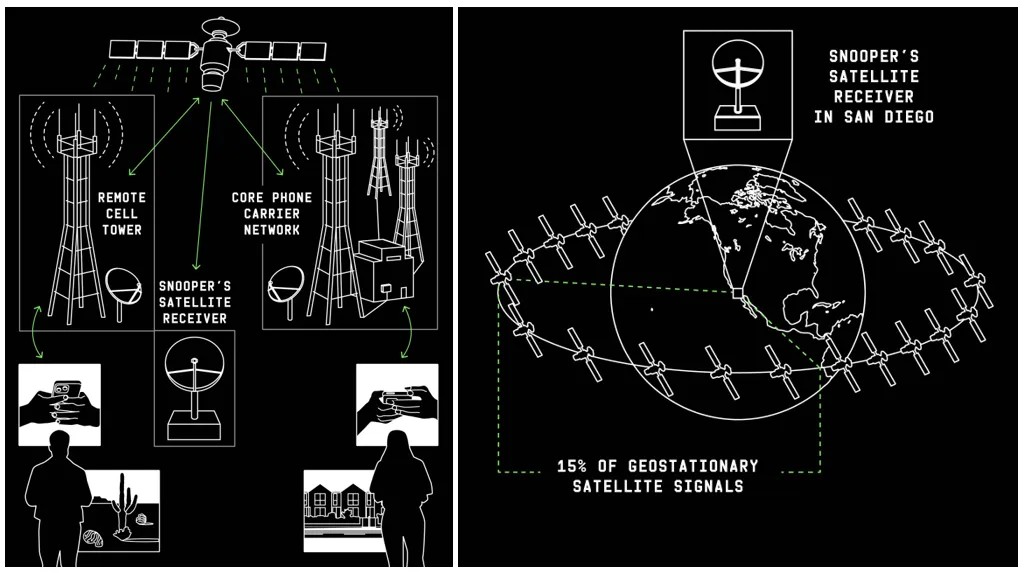
I ricercatori dell’Università della California, San Diego, e dell’Università del Maryland hanno scoperto che circa la metà di tutti i satelliti geostazionari trasmette informazioni senza alcuna protezione.
Nel corso di tre anni, hanno intercettato segnali utilizzando apparecchiature dal costo non superiore a 800 dollari e hanno scoperto migliaia di conversazioni telefoniche e messaggi di utenti T-Mobile, dati dell’esercito statunitense e messicano e comunicazioni interne di aziende energetiche e industriali.
Utilizzando una parabola satellitare standard sul tetto di un’università a La Jolla, il team ha puntato un ricevitore verso vari satelliti in orbita e ha decodificato i segnali provenienti dall’interno del raggio d’azione accessibile dalla California meridionale.
Hanno scoperto che conversazioni tra abbonati, dati Wi-Fi in volo, telemetria di strutture militari , corrispondenza dei dipendenti di importanti catene di vendita al dettaglio e transazioni bancarie venivano trasmessi via etere.
Tra le scoperte svolte dai ricercatori, come riportato nell’articolo di Wired, messaggi provenienti dai sistemi di comunicazione delle forze di sicurezza messicane, le coordinate di aerei ed elicotteri UH-60 Black Hawk e informazioni su piattaforme di rifornimento e reti elettriche.
I ricercatori hanno prestato particolare attenzione alle linee non protette degli operatori di telecomunicazioni. Hanno intercettato il traffico di backhauling (flussi di servizio tra stazioni base remote e la rete centrale) di tre aziende: T-Mobile, AT&T Mexico e Telmex. Durante nove ore di registrazione del traffico, T-Mobile è riuscita a raccogliere i numeri di oltre 2.700 utenti e il contenuto delle loro chiamate e messaggi in arrivo.
Dopo aver informato gli operatori, l’azienda americana ha rapidamente attivato la crittografia, ma molte linee in Messico sono rimaste aperte. AT&T ha confermato che la fuga di dati si è verificata a causa di una configurazione errata dei collegamenti satellitari in diverse aree remote del Paese.
I ricercatori hanno anche scoperto un’enorme quantità di dati militari e industriali. Da parte statunitense, sono state registrate comunicazioni navali non criptate, incluso il traffico internet con i nomi delle navi.
Le unità messicane, invece, hanno trasmesso comunicazioni radio non criptate con i centri di comando e informazioni di manutenzione per aerei e veicoli blindati. Il flusso di dati includeva anche documenti interni della rete elettrica statale, la CFE, contenenti informazioni su guasti, indirizzi dei clienti e rapporti sulla sicurezza.
Oltre alle strutture militari e agli operatori di telecomunicazioni, anche i sistemi aziendali erano a rischio. I ricercatori hanno registrato pacchetti non crittografati dalle reti di bordo delle compagnie aeree utilizzando apparecchiature Intelsat e Panasonic, che trasmettevano dati di navigazione dei passeggeri, metadati di servizio e persino flussi audio da trasmissioni di bordo. In alcuni casi, sono state scoperte e-mail interne di dipendenti Walmart in Messico, registri interni di sportelli bancomat Santander e traffico delle banche Banjercito e Banorte. Dopo essere state informate, la maggior parte delle organizzazioni ha crittografato i propri canali di trasmissione.
Gli esperti stimano che i dati ottenuti coprano solo circa il 15% di tutti i transponder satellitari operativi, ovvero il settore di cielo visibile dalla California. Ciò significa che una sorveglianza simile potrebbe essere facilmente implementata in qualsiasi parte del mondo utilizzando la stessa attrezzatura: un’antenna da 185 dollari, una staffa motorizzata da 140 dollari e un sintonizzatore TV da 230 dollari. Un’operazione del genere non richiede competenze professionali o attrezzature costose: richiede solo componenti domestici e tempo per l’installazione.
I ricercatori hanno riconosciuto che pubblicare apertamente su GitHub i loro strumenti, denominati “Don’t Look Up”, potrebbe facilitare la raccolta di tali dati da parte degli aggressori, ma consentirebbe anche agli operatori di telecomunicazioni e ai proprietari di infrastrutture di riconoscere la portata della minaccia e di implementare con urgenza la crittografia.
Secondo gli esperti, una parte significativa delle comunicazioni satellitari è ancora protetta dal principio “Don’t Look Up”, che consente già la sorveglianza di flussi di dati riservati provenienti dallo spazio, coprendo quasi l’intero pianeta.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…