
SCADA system security requires rigorous management of processes operating with elevated privileges. A recent technical analysis has examined the CVE-2025-0921 vulnerability in the ICONICS Suite, a supervisory system used in critical industrial sectors. With a CVSS score of 6.5, this flaw lies in the improper handling of file system operations by some of the suite’s services, which can be manipulated to compromise the integrity of the host system.
The core of the issue was identified in the Pager Agent, part of the AlarmWorX64 MMX feature set. This component handles sending notifications and alarms through the PagerCfg.exe utility.
During configuration, the system allows you to define a path for the SMSLogFile file. Each messaging operation generates a write to this log file, performed with the service’s privileges, a detail that proves crucial to the dynamics of the attack.
The full extent of CVE-2025-0921 becomes apparent when combined with the vulnerability CVE-2024-7587. The latter vulnerability, related to the GenBroker32 installer, grants full control permissions to every local user on the C:ProgramDataICONICS directory.
This incorrect configuration makes the IcoSetup64.ini file, which contains the path to the SMS log, freely editable even by accounts without administrative permissions, creating the basis for abuse.
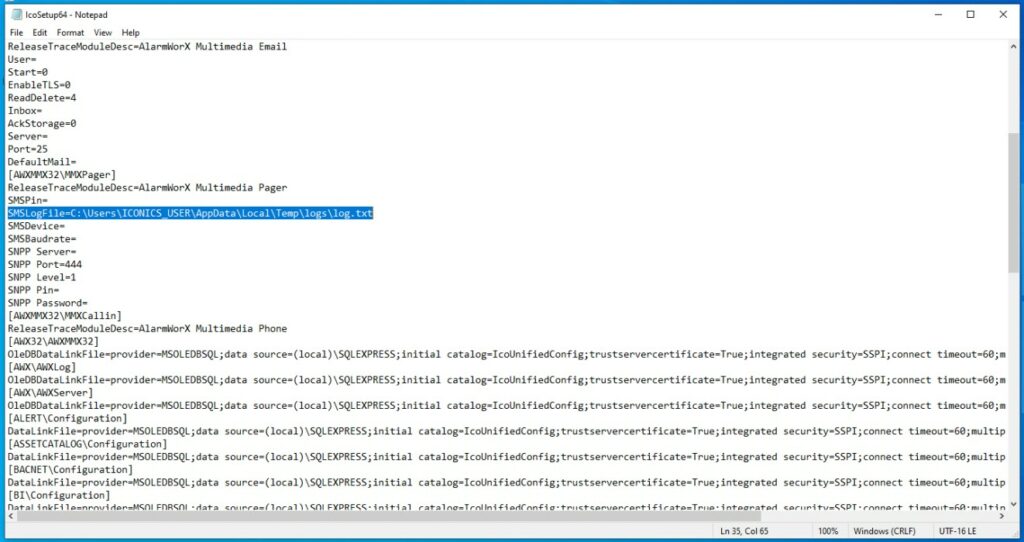
An attacker can then alter the log path specified in the configuration file. By replacing the legitimate path with a symbolic link (symlink) to a critical system file, the attacker indirectly “instructs” the privileged service to attack the operating system. It’s not the user who elevates their privileges, but the legitimate service that is tricked into performing malicious actions on the attacker’s behalf.
During security testing, this mechanism has been shown to cause a persistent denial-of-service (DoS) . By creating a symlink pointing to the cng.sys driver (essential for Windows encryption), the Pager Agent overwrites the driver binary with text log data as soon as an alert or SMS test is triggered. The original file is thus corrupted with readable text strings, losing its executable functionality.
When the computer restarts, Windows attempts to load cng.sys, but fails due to file corruption. This causes the operating system to enter an infinite self-healing loop , rendering the workstation or SCADA server inoperable. The attack demonstrates how a seemingly innocuous operation, such as writing a log, can become a vector for instability if not properly isolated.
The discovery highlights the need to protect configuration directories from unauthorized modification. Coordination between researchers and the ICONICS team led to the definition of corrective measures that eliminate the reported vulnerabilities through specific workarounds. These actions are essential to prevent the creation of malicious symbolic links that exploit the privileges of industrial monitoring services to damage the underlying infrastructure.
A detailed analysis of this vulnerability chain and related technical demonstrations were provided by Unit 42 experts, whose original report forms the basis for understanding these risks in Mitsubishi Electric Iconics Digital Solutions systems. Correctly configuring file system permissions remains the first line of defense against this type of symlink-based and indirect escalation attacks.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
