Shannon acts as a penetration tester who doesn’t just report vulnerabilities, but launches actual exploits. Shannon’s goal is to breach your web application’s security before anyone with malicious intent can.
Using its built-in browser, Shannon automatically searches your code for vulnerabilities to exploit and, to demonstrate the actual existence of these vulnerabilities, performs concrete attacks, such as injection attacks and those aimed at bypassing authentication systems.
Security auditing through penetration testing is generally limited to only once a year. If performed manually, this results in a significant security breach. For the remaining 364 days, you could be at risk without knowing it.
Shannon fills this gap by acting as an on-demand pentester. In addition to identifying potential vulnerabilities, she actually runs exploits, providing proof of concept for the vulnerabilities found.
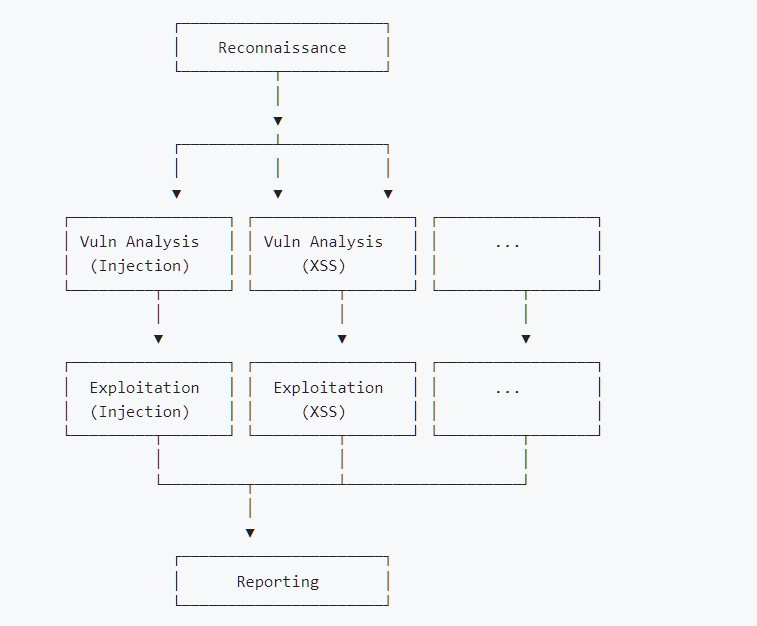
This tool outperformed human penetration testers and proprietary systems in the XBOW benchmark, marking a shift toward continuous security testing. Shannon simulates red team tactics, covering the entire process of reconnaissance, vulnerability analysis, exploitation, and reporting. Its operating principle includes:
Shannon software offers a range of features that allow you to automate various tasks that were previously performed manually. These can be summarized as follows:
In vulnerability benchmark tests, Shannon demonstrated practical capabilities that surpass static scanning : These results demonstrate that Shannon has the autonomous ability to fully compromise applications. Built on Anthropic’s Claude Agent SDK , Shannon support can perform:
Two versions are available:
A typical test lasts 1 to 1.5 hours and costs about $50, providing results that include a run summary and a proof of concept (PoC). By using AI-based programming tools like Claude to accelerate testing, Shannon enables daily security testing in non-production environments, closing coverage gaps in annual penetration tests.
The developers emphasize that it should only be used compliantly after obtaining authorization and warn against running potentially harmful attack tests in production environments.
The tool is open source on GitHub and community contributions are welcome to expand its detection capabilities.
The Shannon software is licensed under the GNU Affero General Public License v3.0 (AGPLv3) , one of the most restrictive copyleft licenses. This license permits commercial use, modification, distribution, and private use of the software, including an explicit grant of patent rights. However, it requires that any modified versions or derivative works be released under the same license , preserving the original copyright and license notices.
A key feature of the AGPLv3 is the requirement to make the complete source code available even when the software is used to provide a service over a network (e.g., a web service or SaaS). In this case, network use is effectively considered a form of distribution. The license excludes any warranty and limits the authors’ liability, making the software available “as is,” with no assurances regarding its functionality or suitability for a specific purpose.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
