
Android has never been so exploited, at least according to the latest developments reported by a recent investigation. Google announced that it has dismantled what may be the largest network of “home” proxies ever seen , an infrastructure that for years used Android devices as exit points for third-party internet traffic, without users’ knowledge.
The mechanism was as simple as it was insidious. Smartphones, computers, and consumer smart devices ended up on a network where other people’s traffic was routed through the unsuspecting user’s IP address. It was like turning your phone into an unauthorized public gateway—a veritable Airbnb for internet traffic , but without the owner’s knowledge.
It all worked through a software package called the Ipidea SDK , which developers integrated into free apps or games. Once the app was installed, the smartphone automatically began acting as a proxy node, while still displaying the app’s normal interface.
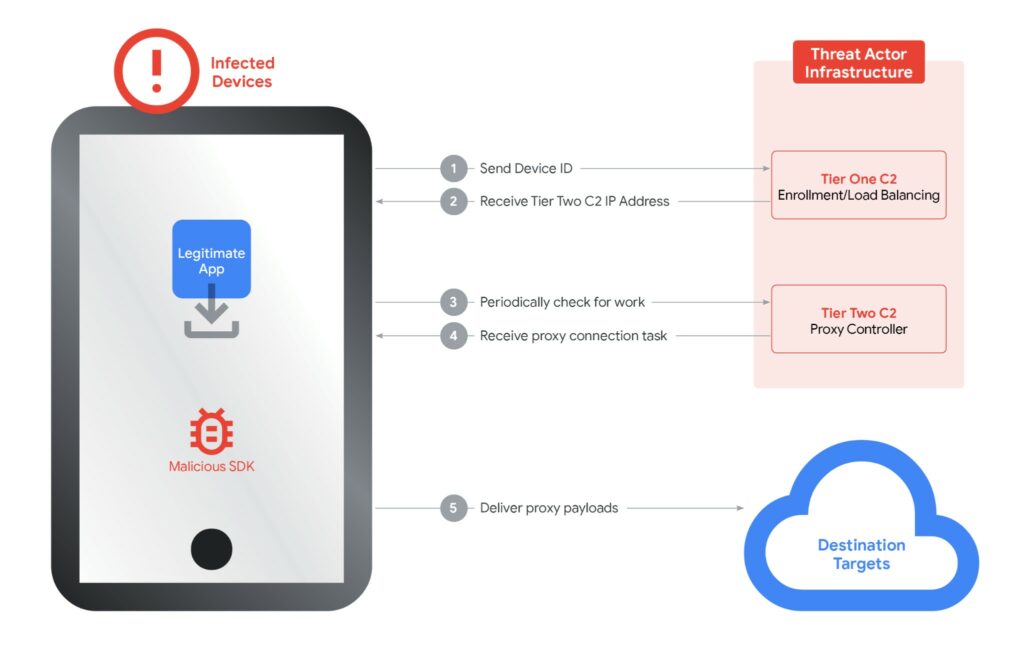
The problem wasn’t just theoretical. Google clarified that its Play Protect protection service now recognizes and removes these apps, even blocking new installations. However, the fact that developers were paid for each SDK installation kept the risk of stumbling upon compromised apps high.
Once inside this network, traffic passed from your device to third-party servers. Essentially, anyone exploiting that node could act as if they were connecting from your IP address, with all the associated privacy and digital liability implications.
This is not an abstract risk: last year, a vulnerability allowed attackers to aggregate over two million devices into a botnet called Kimwolf , used for large-scale DDoS attacks.
According to estimates by The Wall Street Journal , Google’s actions have disabled nearly nine million Android devices connected to this malicious infrastructure, as well as removing hundreds of apps from the Play platform.
The company behind the SDK, Ipidea , denied the accusations, saying it offers legitimate services and has abandoned aggressive practices, though it admitted to advertising on cybercrime forums.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
