
Push Security specialists have noticed that the Sneaky2FA phishing platform now supports browser-in-the-browser attacks, which allow the creation of fake login windows and the theft of credentials and sessions.
Sneaky2FA is one of the most popular Phishing-as-a-Service (PhaseaS) services among cybercriminals. Along with Tycoon2FA and Mamba2FA , Sneaky2FA primarily targets Microsoft 365 account theft.
This phishing kit is known for attacks using SVG and the “attacker-in-the-middle” tactic: the authentication process is forwarded via a phishing page to the real service, allowing attackers to intercept session tokens.
As a result, even with two-factor authentication (2FA) enabled, attackers gain access to the victim’s account.
The browser-in-the-browser (BitB) attack technique was first described in 2022 by a security researcher known under the pseudonym mr.d0x. He demonstrated that browser-in-the-browser attacks enable the creation of phishing login forms using fake browser windows.
The attack relies on the fact that when you access a website, a message often appears prompting you to sign in using a Google, Microsoft, Apple, Twitter, Facebook, Steam , or other account. Clicking such a button (for example, “Sign in with Google “) opens a Single Sign-On (SSO) window in the browser, prompting you to enter your credentials and log in with that account.
These windows are truncated, displaying only the login form and an address bar displaying the URL. This URL verifies that the site is being accessed through a real domain (e.g., google.com), further strengthening the user’s trust in the process.
Essentially, attackers create fake browser windows within real browser windows and present victims with login pages or other forms to steal credentials or one-time passcodes (OTPs).
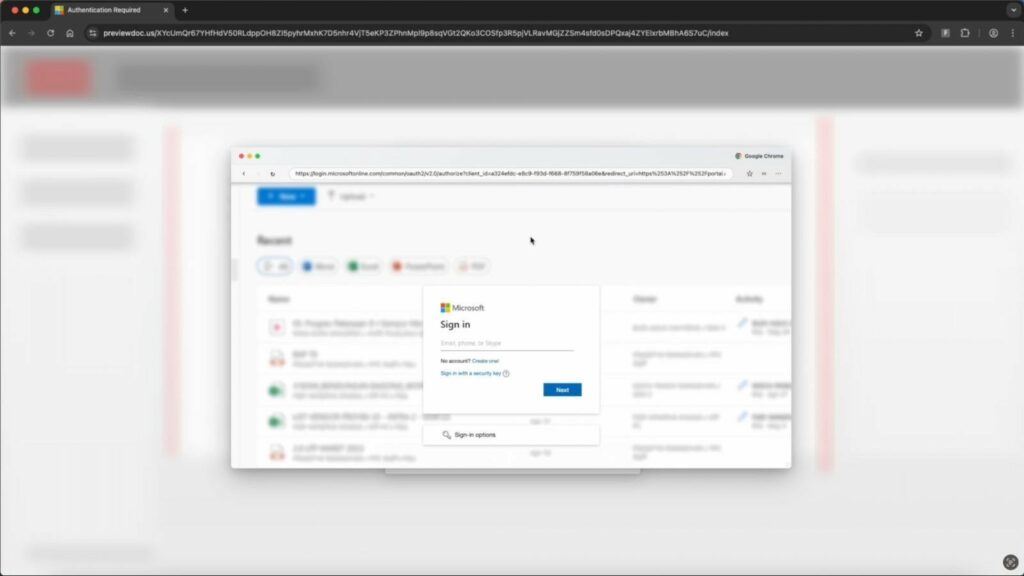
BitB is now actively used in Sneaky2F: the fake page dynamically adapts to the victim’s operating system and browser (for example, imitating Edge on Windows or Safari on macOS).
The attack works as follows:
Essentially, using BitB’s technique adds an additional layer of deception to Sneaky2FA’s existing capabilities.
Researchers note that the phishing kit uses advanced HTML and JavaScript obfuscation to evade static detection (the text is interspersed with invisible tags, and the interface elements are encoded images). While everything appears normal to the user, this hinders the functioning of security tools. Additionally, Sneaky2FA redirects bots and researchers to a separate, harmless page.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
