
Stuxnet is widely recognized as the malware par excellence, the one that introduced cyber warfare to the world, where pages and pages have been written and will continue to be written about this marvel of technology, intelligence, and cyber warfare.
In this article, we want to take a slide and try to reconstruct a story, starting from public sources, to understand how the malware itself works, as well as describing the motivations and events that occurred in the summer of 2010.
The Stuxnet worm first appeared in the summer of 2010. It is a computer worm weighing only 500 kilobytes that infiltrated numerous computer systems. This worm operated in three phases. First, it scanned and targeted Windows networks and computer systems, and then spread throughout the computer network to attack the systems for which it was designed. Uranium enrichment centrifuges, managed by Programmable logic controllers (PLCs).
The worm, once infiltrated into these machines, began to replicate by infiltrating the Windows-based Siemens Step7 software. This Siemens software system was and continues to be a widespread software within industrial computer networks, such as uranium enrichment plants.
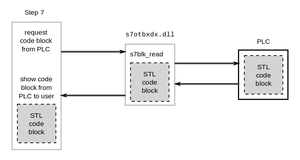
Logic diagram of Siemens’ Step7 software
By compromising the Step7 software, the worm gained access to the Programmable logic controllers (PLCs), and this final step allowed the worm to manipulate crucial industrial information, as well as gain the ability to operate different machinery at individual industrial sites.
The replication process is what made the worm so widespread. It was so invasive that if a USB stick was plugged into a computer system where it was present inside, the worm would move from the USB device and begin spreading to all subsequent computer systems to which the USB was connected, such as within Air Gap networks, i.e. isolated networks that cannot be reached from the internet.
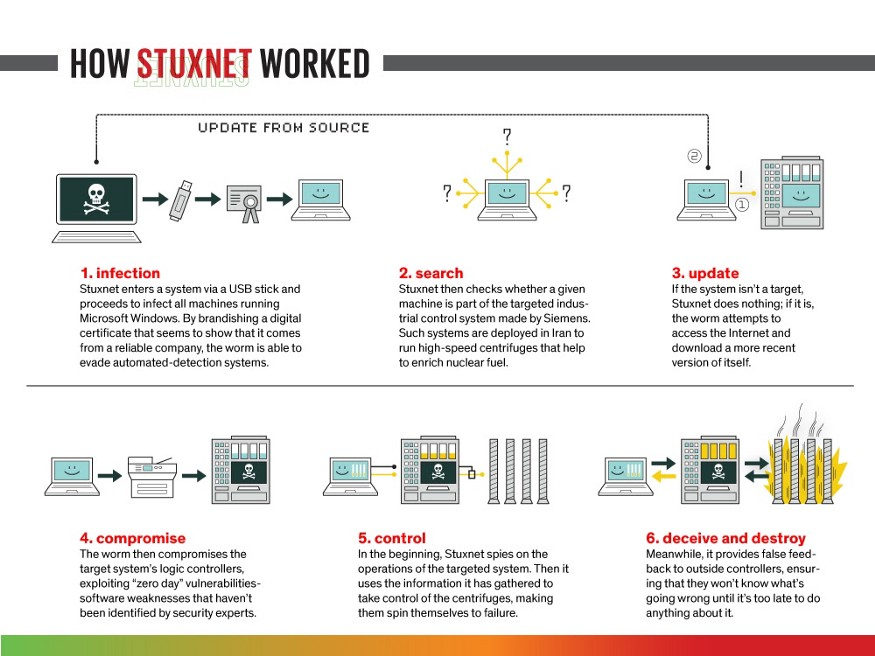
Once the malware was launched, more than fifteen Iranian facilities were attacked and infected by the Stuxnet worm. This attack is believed to have been initiated from a worker’s USB drive inside the plant.
One of the affected industrial facilities was the Natanz nuclear power plant. Inspectors from the International Atomic Energy Agency visited the Natanz plant and observed that a strange number of uranium enrichment centrifuges were breaking down. The cause of these failures was unknown at the time.
Later in 2010, Iranian technicians commissioned cybersecurity specialists in Belarus to examine their computer systems. This security firm eventually discovered multiple malicious files on Iranian computer systems. It later revealed that these malicious files were the Stuxnet worm.

Site of Iran’s Natanz nuclear power plant
Although Iran has not released specific details about the effects of the attack, it is currently estimated that the Stuxnet worm destroyed 984 uranium enrichment centrifuges. According to current estimates, this represented a 30% decrease in nuclear enrichment efficiency and therefore a severe blow to the Iranian nuclear program.
The Stuxnet virus had two main technological components: one was the computer worm that distributed the malware on Microsoft Windows networks and another was the payload that penetrated Windows hosts and then operated Siemens PLCs. The worm component used 4 0-day exploits to propagate the virus within networks:
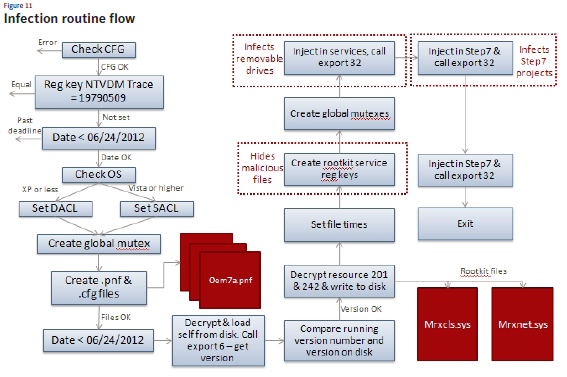
Once Stuxnet was inside a machine, it would escalate its privileges from a local administrator to SYSTEM using two other 0-day exploits in the Windows Task Scheduler (CVE-2010–3888) or another in the Windows Win32 keyboard layout (CVE-2010–2743) and then install a hardware driver-level rootkit (mrxnet.sys, mrxcls.sys) hidden behind a digital certificate stolen (initially from Realtek, then JMicro) to masquerade as legitimate software and evade detection by traditional signature-based antivirus software.
After installing the driver, the virus sets Windows registry entries (HKLMSystemCurrentControlSetServicesMRXCLS and MRXNET) so that the two drivers are started as system services.
Stuxnet then starts its own Remote Procedure Call (RPC) server and listens for incoming connections from other infected computers on the same local network. The RPC server has a fixed GUID that allows Stuxnet peers to identify, communicate with, and update each other, allowing it to propagate updates even if they can’t reach the external command and control server due to a firewall or lack of Internet connectivity.
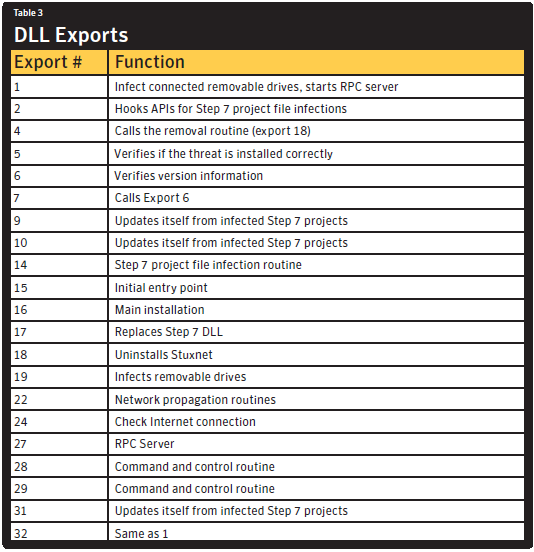
Stuxnet’s Manifest DLL. Source Symantec
A notable aspect of the rootkit is that when it needs to load a DLL that includes itself, it uses a special mechanism designed to bypass typical behavior blocking and intrusion detection technologies that actively monitor calls to the Windows LoadLibrary method.
Stuxnet calls LoadLibrary with specific file names that do not exist on disk and are instead mapped to areas of memory where the DLL code has already been decrypted and stored by the rootkit previously. Stuxnet achieves this by attaching itself to the Windows kernel’s NTDLL.DLL, intercepting commands, and injecting code into already running trusted operating system processes such as lsass.exe, svchosts.exe, and services.exe, as well as security programs such as avp.exe (Kaspersky), mcshield.exe (McAfee), rtvscan.exe (Symantec), and others.
Once installed as a service on your computer, Stuxnet searches your local computer for Siemens SIMATIC Step7 software by looking in the Windows system folder for the file S7OTBXDX.DLL. Once found, it renames the file to S7OTBXSX.DLL and then replaces it with a modified version that has the same DLL calls as the original but with code changes for more than a dozen critical functions related to accessing, reading, writing, and deleting blocks of code on the PLC.
Stuxnet will execute additional instructions before calling the actual functions contained in the original S7OTBXSX.DLL and, by modifying data sent or received by the PLC, can also act as a Man-in-the-Middle attack. Note that if Siemens Step7 is not found, Stuxnet does not perform any further malicious actions on the computer host.
Stuxnet attempts to contact a remote web server to test Internet connectivity using the following benign URLs (windowsupdate.com or msn.com). If successful, it connects to the following URLs to send and receive commands from a remote user (mypremierfutbol.com, todaysfutbol.com).
It then generates the following URL and sends a message to the server: http://www.mypremierfutbol.com/index.php?data={data } where data is an XOR-encrypted hexadecimal value containing the IP address, computer name, domain, operating system version, and whether WinCC Step7 is installed. The server may respond to the infected machine by sending arbitrary code to execute (possibly an updated version of the malware payload or some data exfiltration commands).
Finally, once all the installation and configuration operations have been performed, if the Siemens software has been installed on the local machine, Stuxnet accesses the available PLCs connected to the Windows machine using S7OTBXDX.DLL and the default WinCC MSSQL database credentials (userid=WinCCConnect and password =2WSXcder, 0-day exploit CVE-2010–2772) and checks the type of CPU they have.
If the CPU is of the 6ES7–315–2 or 6ES7–417 type, the malware checks the type of devices connected to them by reading the PLC’s system data blocks (SDB). Finally, it checks whether the found devices are Vacon or Fararo Paya frequency converters and whether they operate in the 807–1210 Hz range.
If all these specific conditions are met, Stuxnet records the frequency configuration data in the PLC and begins intercepting commands, altering their operation. Approximately every 30 days, Stuxnet then changes the output frequency of the converters for short periods of 15–50 minutes to 1410 Hz or 2 Hz, respectively, and then returns to 1064 Hz (a normal frequency). The periodic change in output frequency sabotages the automation system, introducing mechanical stress to the centrifuges, thus increasing the likelihood of failure and reducing the quality of the uranium processed.
Many members of the media have speculated who designed the Stuxnet worm and who was responsible for using it to attack the Iranian nuclear facility. It is now widely accepted that it was designed as a cyberweapon to attack the development of the Iranian nuclear program. It was given the code name “Operation Olympic Games,” which was initiated under President George W. Bush and continued under President Obama. While neither government has ever officially acknowledged the development of Stuxnet, a 2011 video created to celebrate the retirement of Israel Defense Forces chief Gabi Ashkenazi listed Stuxnet as one of the successes under his watch.
Edward Snowden, the NSA whistleblower, also claimed this in the 2013 Datagate scandal. But despite this speculation, there is still no concrete evidence as to who designed the original cyberweapon.
While the individual engineers behind Stuxnet have not been identified, we know that they were very skilled and that there were many of them. Kaspersky Lab’s Roel Schouwenberg estimated that it took a team of ten programmers two to three years to create the worm in its final form.
Several other worms with similar infection capabilities to Stuxnet, including those nicknamed Duqu and Flame, were identified in subsequent active attacks, although their goals were very different from Stuxnet’s. Their similarity to Stuxnet leads experts to believe that they are products of the same “development workshop,” which is apparently still active. Headquarters of the United States National Security Agency (NSA)
Although Stuxnet’s makers scheduled its expiration in June 2012, and Siemens issued fixes for its PLC software, Stuxnet’s legacy lives on in other malware attacks based on its original code. These “children of Stuxnet” include:
While ordinary computer users have no reason to worry about these Stuxnet-like malware-based attacks, they are clearly a serious threat to a number of critical industries, including energy production, power grids, and defense.
Although extortion is a common goal of malware writers, the Stuxnet family of worms appears to be more interested in attacking infrastructure.
The sophistication of the Stuxnet code (multiple zero-day vulnerabilities, code obfuscation, code injection, modular design, remote command and control and peer-to-peer updating, all-in-1 payload), its fraudulent digital certificates, and the dogged patience of the cyberattack (which unfolded over months rather than minutes) suggested that the author of Stuxnet was a nation-state with comprehensive knowledge of cybersecurity and nuclear power plants.
According to Symantec’s analysis of the first 38,000 infected IP addresses, 22,000 were located in Iran, 6,700 in Indonesia, 3,700 in India, and only 400 in the United States. Of those machines, 217 in Iran were reported to host Siemens Step7 and 16 in the United States, which were the highest counts worldwide.
Stuxnet redefined what computer malware could do in terms of the methods used and the damage inflicted. It opened the digital door to further cyberwarfare attacks on physical infrastructure.
According to sources such as the Institute for Science and International Security and the International Atomic Energy Agency, Stuxnet damaged approximately 1,000 IR-1 centrifuges at the Natanz uranium fuel enrichment plant and set back Iran’s nuclear program by a year.
Malware authors also learn from each other. Stuxnet has had several offspring inspired by its engineering. Duqu logged keystrokes and extracted data from industrial facilities in 2011. Flame also traveled via USB sticks in 2012 and was a complete spyware that logged keystrokes and recorded Skype conversations.
In short, all this led us in a very short time to understand that malware can cause significant damage to an industrial plant, introducing the world to a new era of warfare. Cyber warfare.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
