
The cybersecurity landscape was recently rocked by the discovery of a critical Remote Code Execution (RCE) vulnerability in Microsoft’s Windows Server Update Services (WSUS) .
Identified as CVE-2025-59287 and with a CVSS score of 9.8 (Critical) , this flaw poses a high and immediate risk to organizations using WSUS for centralized update management.
The vulnerability is particularly dangerous because it allows a remote, unauthenticated attacker to execute arbitrary code with system privileges on the affected WSUS servers.
After Microsoft released an emergency out-of-band patch on October 23, 2025, which was necessary because the initial October patch had not fully addressed the issue, active exploitation activity was immediately observed on the network .
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) quickly added this vulnerability to its Catalog of Known Exploited Vulnerabilities (KEV), emphasizing the urgency of an immediate response from system administrators.
WSUS is a critical tool in corporate networks, serving as a trusted source for distributing software patches.
Its nature as a key infrastructure service makes it a high-value target, as its compromise can provide a beachhead for lateral movement and widespread network compromise.
The root of the problem lies in a case of “unsafe deserialization of untrusted data” and is one of the causes of RCE (Remote Code Execution) as a final effect.
This technical flaw can be exploited in several known attack routes:
In both scenarios, the attacker can trick the system into executing malicious code with the highest level of privilege: System
The vulnerability is specific to systems with the WSUS Server role enabled and Microsoft Windows Server 2012, 2012 R2, 2016, 2019, 2022 (including version 23H2), and 2025 are vulnerable.
Following the recent public disclosure of a Proof-of-Concept (PoC) for the exploit , we conducted a lab test to analyze its functionality and potential impact.
The PoC, available at the link: https://gist.github.com/hawktrace/76b3ea4275a5e2191e6582bdc5a0dc8b
This is specifically designed to target publicly exposed Windows Server Update Services (WSUS) instances on the default TCP ports 8530 (HTTP) and 8531 (HTTPS) .
Running the PoC is simple, you just need to run the script specifying the vulnerable http/https target as an argument.
This triggers the launch of malicious PowerShell commands via child processes and uses the second exploit mode explained above (ReportingWebService), in this specific case the calc.exe (system calculator) process is opened.
The malicious commands are present in Base64 encoded format and are executed during a deserialization phase within the WSUS service.
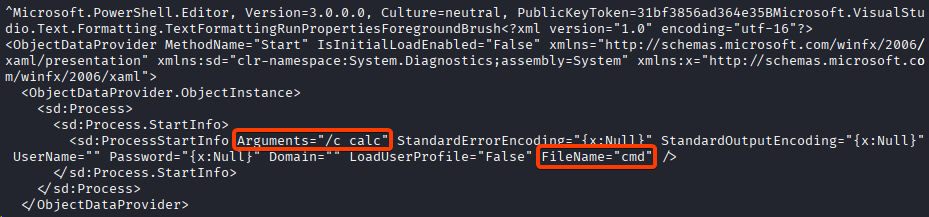
This deserialization mechanism represents the crucial point where an attacker can inject any other commands to conduct reconnaissance or post-exploitation activities.
The sequence of processes in the laboratory test was as follows:
WsusService.exe -> Cmd.exe -> Calc.exe -> win32calc.exe
Here are the child processes spawned by the legitimate WSUS processes (wsusservice.exe).
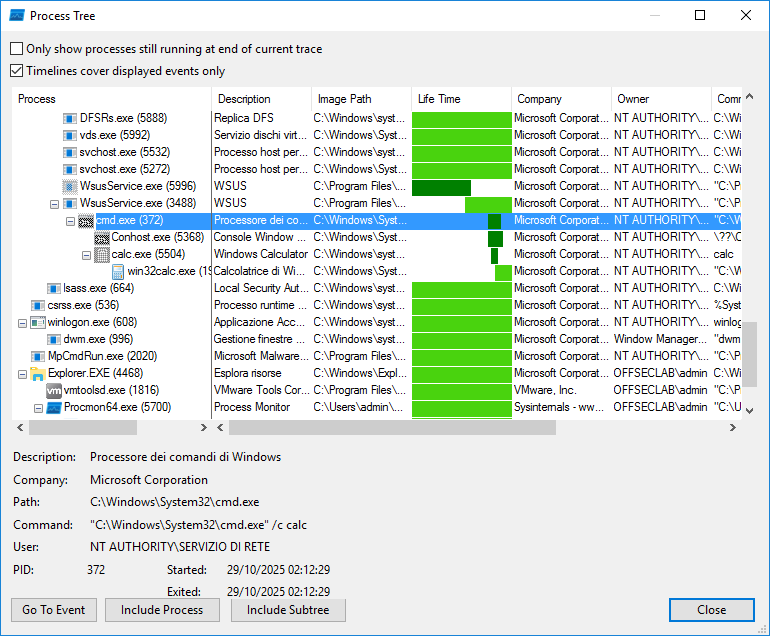
(Note: In this specific PoC, running calc.exe (System Calculator) serves as non-destructive proof of successful remote code execution.)
Furthermore, the command remains persistent: when the server or service is restarted, the previously injected RCE is executed. The same happens when you start the MMC (Microsoft Management Console) with the WSUS snap-in, used to configure and monitor the service.
Demo Video: The full operation of this PoC can be seen in the video available at this link: https://www.youtube.com/watch?v=CH4Ped59SLY
The following table summarizes the critical artifacts to examine and their detection criteria to identify a possible compromise from this CVE:
| Artifact | Description | Focus on Detection |
| C:inetpublogsLogFilesW3SVC*u_ex*.log | HTTP Service Log | Look for anomalous POST requests to WSUS endpoints such as /ClientWebService/Client.asmx . Pay particular attention to requests with large payloads or repeated login attempts . |
| Process creation log | Windows event log / EDR (Endpoint Detection and Response) | Monitor running child processes (e.g., cmd.exe , powershell.exe ) spawned by legitimate WSUS processes such as wsusservice.exe or w3wp.exe (specifically, the WSUS application pool). This behavior is highly suspicious. |
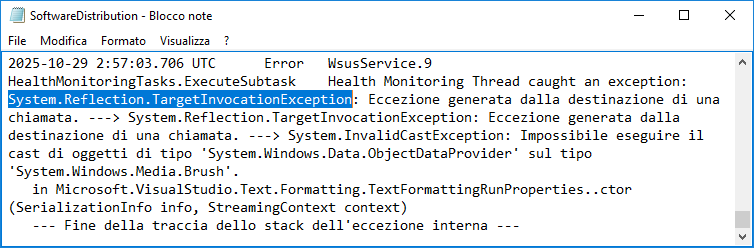
| WSUS log files | C:Program FilesUpdate ServicesLogfilesSoftwareDistribution.log | Check for deserialization errors that may indicate an exploitation attempt, especially messages like System.Reflection.TargetInvocationException . |
Here is an example of the log during testing.
The contents of SoftwareDistribution.log
And finally, the IIS log also contains an anomalous useragent.
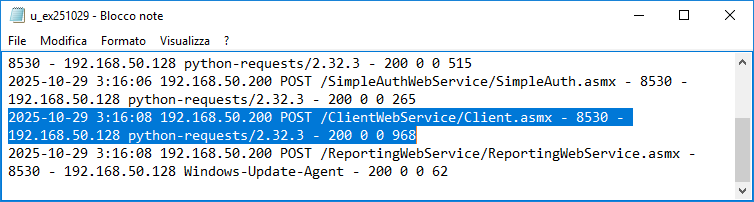
(This log is accessible only if the “HTTP Logging” feature is installed in the “Web server/Server Health and Diagnostics” subcategory.)
The attack surface associated with this vulnerability is extremely significant.
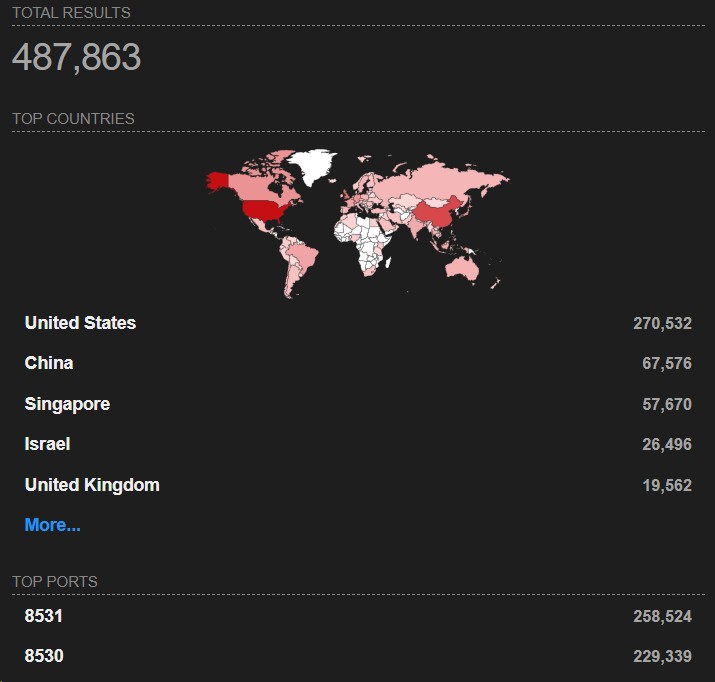
Currently, thousands of WSUS instances remain exposed to the Internet globally and are potentially vulnerable. A search on Shodan reveals over 480,000 results worldwide, including more than 500 in Italy alone , classified as open services in the two default ports associated with WSUS .
The main recommendation is to immediately implement the emergency security patches released by Microsoft.
For organizations that are unable to immediately deploy updates, Microsoft has suggested the following temporary measures to mitigate the risk, which are intended as stopgap solutions:
It is critical that organizations follow these guidelines and engage in threat hunting to detect any signs of compromise or past exploitation attempts.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
