
In today’s cybersecurity landscape, one of the most worrying trends is the abuse of legitimate messaging platforms for malicious purposes. Telegram in particular is increasingly being exploited by criminal groups as a Command & Control (C2) infrastructure, a centralized system for managing cyber attacks, receiving stolen data, and coordinating illicit operations. This phenomenon poses a significant challenge for companies, as the use of legitimate services makes it more difficult to detect and block such activities.
Attackers exploit Telegram’s public APIs to create automated bots capable of receiving commands and transmitting stolen data. The typical process involves an initial compromise phase, often through phishing or malware campaigns, followed by the installation of a malicious agent on the victims’ devices. Once they gain access, hackers use Telegram bots to maintain remote control, avoiding the need for dedicated servers and drastically reducing the risk of detection.
The ease with which these bots can be configured, combined with the platform’s built-in encryption, makes Telegram particularly attractive to cybercriminals. Furthermore, because it is a service widely used for legitimate purposes, the traffic generated by malicious bots goes unnoticed among normal communications, further complicating the work of security teams.
The North Korean-linked Lazarus cybercriminal group is known for its ability to constantly evolve, adopting increasingly sophisticated tactics to make its attacks as invisible and effective as possible. One of its strategies involves the use of Telegram, for the reasons mentioned above. In the “Operation Blacksmith” campaign, Lazarus exploited the Log4Shell vulnerability to spread the NineRAT Trojan. This malware allows hackers to remotely control compromised systems by using Telegram as a command-and-control channel.
This tactic demonstrates the growing sophistication of cybercriminals, who not only exploit known vulnerabilities but also adapt common tools for criminal purposes. For businesses, the risk is clear. Defending against such advanced groups requires not only constant updates but also threat intelligence specialists capable of identifying anomalous behavior even within seemingly secure services.
The lesson learned is clear: in an increasingly complex cyber landscape, even the apps we use every day can become vehicles for intrusion. It is up to the cybersecurity manager to adopt appropriate strategies to try to mitigate increasingly ingenious threats. The attack flow can be summarized with the following diagram, in which cybercriminals apply (but are not limited to) the techniques described in MITRE T1102.002 (Web Service: Bidirectional Communication) and T1567 (Exfiltration Over Web Service).
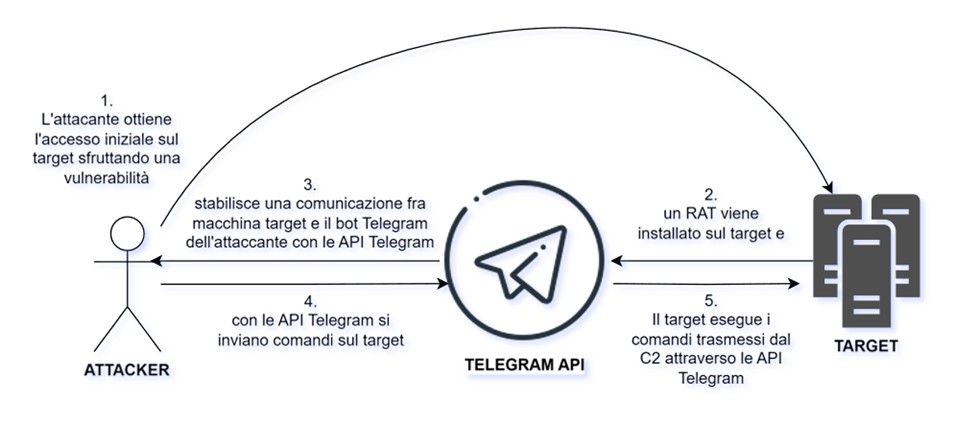
A company specializing in Cybersecurity and Threat Intelligence like Olympos Consulting plays a fundamental role in helping organizations protect themselves from these advanced threats. Through a proactive, data-driven approach, Olympos is able to intercept the actions of these criminal infrastructures and intervene before they cause significant damage.
Collaborating with a specialized partner like Olympos Consulting offers organizations several advantages in the fight against these hybrid threats.
First, the team of experts can implement advanced detection systems capable of identifying suspicious communications to Telegram bots, even when they are disguised as legitimate traffic. By analyzing network traffic and detecting requests from a host to the api.telegram.org API, it’s a clear indication that the host is using the Telegram API for command-and-control (C2) operations or data exfiltration.
Secondly, through appropriate assessments, the team is able to evaluate the resilience of the corporate infrastructure and identify any vulnerabilities that could be exploited by threat actors.
Furthermore, it issues threat intelligence bulletins that enable companies to anticipate advanced threats, take targeted countermeasures, and strengthen their security posture in line with industry compliance standards. Relying on their expert analysis not only reduces cyber risks but also brings organizations closer to regulatory obligations, transforming cybersecurity from compliance to competitive advantage.
Another crucial aspect is staff training, as many of these attacks begin with social engineering techniques. Educating employees to recognize phishing attempts and other threats can significantly reduce the risk of compromise. The use of messaging platforms as C2 infrastructures by threat actors poses a complex cybersecurity challenge, but with the right tools and skills, the risks can be mitigated.
Companies like Olympos Consulting demonstrate how a threat intelligence-based approach can make a difference in protecting corporate data and systems. As attackers continue to innovate their techniques, it’s crucial that defenses evolve accordingly. Investing in proactive solutions and strategic partnerships with cybersecurity experts is no longer an option, but a necessity for any organization that wants to ensure its security in an increasingly hostile digital landscape.
If you want to verify that your defenses are truly effective against these threats, contact Olympos Consulting for a personalized consultation here: [email protected]
Make your company a more difficult target for cybercriminals with the support of experts who speak the language of business!
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
