
A new version of the Android malware called Konfety has become even more sophisticated: specialists at Zimperium zLabs have discovered an improved variant that uses non-standard ZIP archives and loads encrypted code during execution. These techniques allow the malware to effectively bypass automated analysis tools and remain undetected.
The main feature of the updated version is an ingenious modification of the ZIP archive: the APK file has a flag enabled that causes many tools to mistakenly perceive it as encrypted. Some utilities require a password to unzip it, while others fail to analyze the file structure at all.
Further confusion is caused by the incorrect compression method: AndroidManifest.xml claims to use BZIP, but in reality, no compression is performed with this method. This causes partial unpacking or malfunctions in analysis tools, significantly complicating work with infected files.
Despite the non-standard nature of the ZIP file, the Android operating system handles these cases without any issues and correctly installs the malicious app without displaying any warnings. Conversely, specialized tools like APKTool and JADX may prompt for a nonexistent password or simply display an error. This allows the malware to hide in seemingly normal apps.
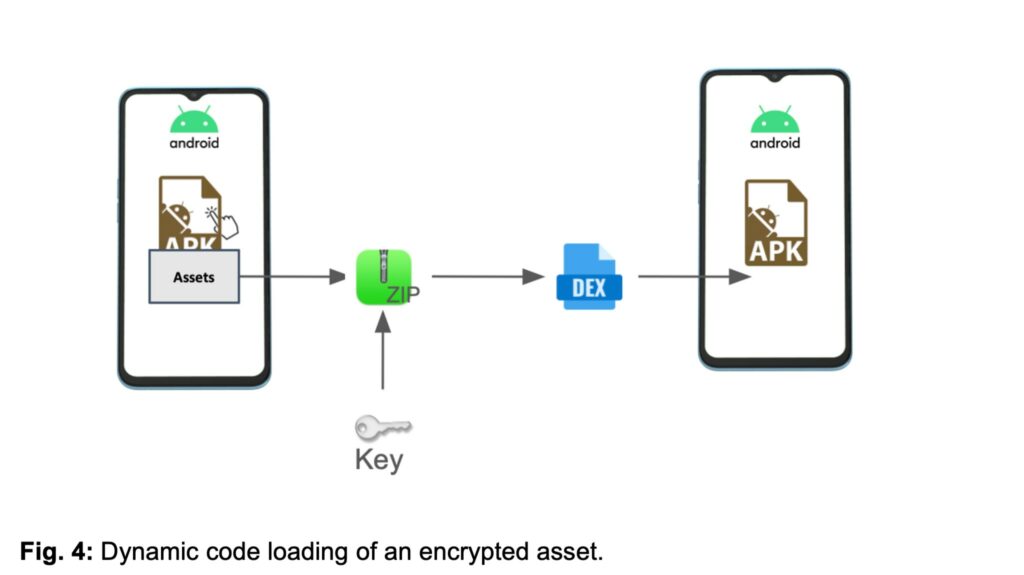
Furthermore, the new version of Konfety uses dynamic loading of encrypted executable code during operation. This is not visible in advance during the standard APK scan. Inside the malicious application is a secondary DEX file, encrypted and hidden in the resources. It is loaded only after the application is launched, replacing the missing components declared in the manifest, thus raising the suspicions of attentive analysts.
Furthermore, the malware reuses mechanisms already known from previous attacks. In particular, the CaramelAds SDK component is involved again, known for its ad fraud scheme. This allows the stealth display of advertisements, the installation of additional modules, and communication with remote servers without the user’s knowledge. Experts also point out the coincidence of regular expressions and a pop-up window related to a user agreement, all of which indicate a continuity with previous attacks.
To disguise itself, Konfety imitates real Google Play apps by copying their package names. However, it has no functionality within it, and the app itself often hides its name and icon. Upon launch, the user is asked to accept a specific agreement, after which the browser opens and is redirected to various sites. The ultimate goal is to convince the victim to install unwanted apps or accept annoying notifications.
The report lists infection signs, as well as the MITRE classification tactics and techniques used in this campaign. The new version of Konfety clearly demonstrates how seemingly simple ZIP manipulation and delayed code loading techniques can successfully bypass even the most advanced threat detection systems.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
