
Il gruppo Warlock, noto anche come Storm-2603 e GOLD SALEM, è passato dall’essere un nuovo arrivato a un attore di spicco nel mercato dei ransomware in pochi mesi. I ricercatori di Sophos riferiscono che l’attività del gruppo è iniziata a marzo 2025 e che a settembre aveva già creato un proprio portale di fuga di dati, “Warlock Client Data Leak Show”, dove sono state pubblicate 60 vittime. Gli aggressori operano in tutto il mondo, colpendo piccole agenzie governative e aziende commerciali a multinazionali in Nord e Sud America ed Europa.
Warlock ricevette particolare attenzione dopo gli incidenti di agosto: i criminali si vantarono di aver compromesso le società francese Orange e britannica Colt. In quest’ultimo caso, affermarono di aver rubato un milione di documenti e annunciarono persino un’asta per l’archivio.
Successivamente, la stessa risorsa ha elencato la Star Alliance tra le sue vittime, sebbene non sia arrivata alcuna conferma ufficiale da parte dell’organizzazione, e il post stesso era accompagnato da una nota sulla vendita del set di dati rubato. A differenza di altri gruppi ransomware, Warlock non pubblica le date degli attacchi e raramente mostra esempi di materiale rubato, limitandosi a laconiche note sullo stato del riscatto o a un collegamento a un archivio.
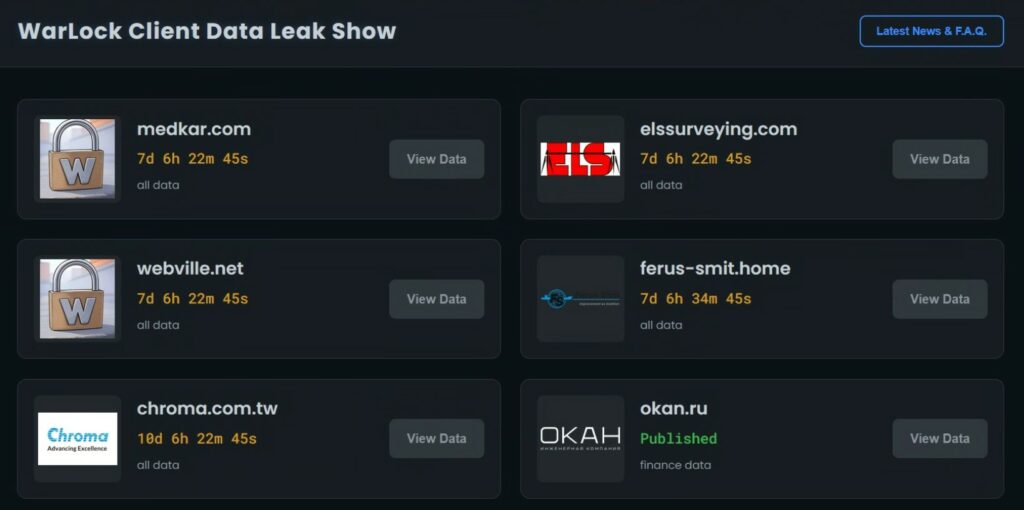
Lo stile negoziale di Warlock è palesemente duro: sul loro sito web, accusano le organizzazioni di irresponsabilità e promettono di divulgare i dati se si rifiutano di contattarle. Allo stesso tempo, per le grandi aziende che detengono informazioni estremamente sensibili, dichiarano che l’intera portata dei dati rubati non sarà resa pubblica. Questo approccio consente al gruppo di minare contemporaneamente la reputazione della vittima e di mantenere vivo l’interesse degli acquirenti del mercato nero.
Il rapporto di Sophos pone particolare enfasi sulle tecniche di attacco. Warlock è apparso pubblicamente per la prima volta a giugno su un forum di hacker, dove un rappresentante del gruppo era alla ricerca di exploit per applicazioni aziendali come Veeam, ESXi e SharePoint, nonché di strumenti per bypassare i sistemi EDR.
A luglio, Microsoft aveva già rilevato che il gruppo stava utilizzando una nuova vulnerabilità zero-day sui server SharePoint locali.
L’exploit è stato inizialmente distribuito dal gruppo cinese Salt Typhoon il 18 luglio, ma un aggiornamento problematico ha lasciato vulnerabili decine di migliaia di sistemi, inclusi server governativi. Warlock ha approfittato della situazione e ha implementato la propria catena ToolShell per installare web shell e ottenere persistenza di rete tramite un server Golang personalizzato basato su WebSocket.
Inoltre, gli aggressori combinano attivamente metodi collaudati: utilizzano Mimikatz per rubare le credenziali, PsExec e Impacket per gli spostamenti laterali e distribuiscono il ransomware sulla rete tramite policy di gruppo. Per il traffico nascosto, utilizzano strumenti legittimi, in particolare Velociraptor. Questa combinazione rende i loro attacchi flessibili e difficili da rilevare. Sophos sottolinea che questo mix di tecniche standard e innovazioni mirate dimostra l’elevato livello di preparazione e coraggio degli autori.
In breve tempo, Warlock è entrato nella lista delle 20 operazioni ransomware più attive dell’ultimo anno. Gli esperti stimano che sia improbabile che un’ulteriore pressione sulle infrastrutture aziendali possa essere fermata senza misure aggressive da parte degli operatori di sicurezza.
Per mitigare i rischi, gli esperti consigliano alle organizzazioni di prestare maggiore attenzione al monitoraggio della superficie di attacco, all’applicazione tempestiva di patch ai servizi pubblici e al mantenimento della prontezza per una risposta rapida agli incidenti. Sophos sottolinea che comprendere le tattiche dei Warlock è essenziale per rafforzare le difese prima che il gruppo selezioni un nuovo obiettivo.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…