
In a digital landscape increasingly characterized by mass surveillance and indiscriminate data collection, the pursuit of online anonymity has become a primary necessity for journalists, activists, and researchers. It is in this context that TOR Anonymizer v3.0 emerges, a tool that represents a significant leap forward in digital privacy protection.
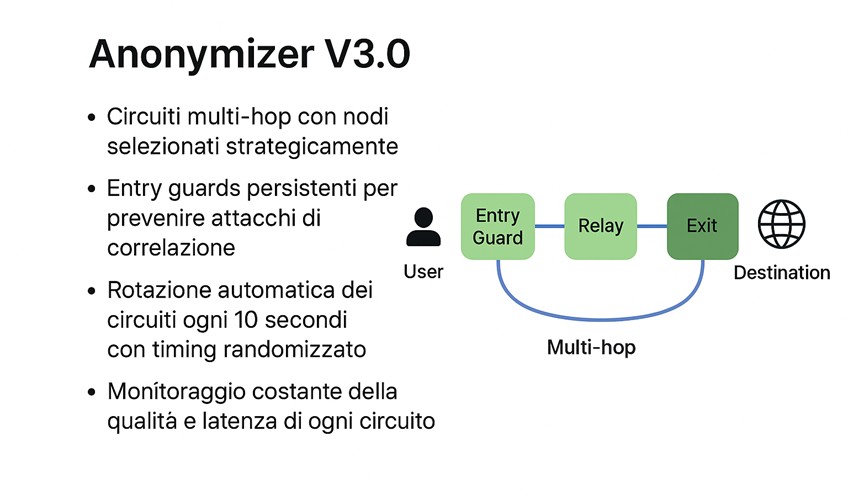
The real strength of TOR Anonymizer v3.0 lies in its advanced route management within the Tor network . Unlike a traditional client, which simply creates basic connections, this tool introduces an advanced system capable of building multi-hop connections with strategically chosen nodes, thus strengthening anonymity.
Entry guards are kept stable to reduce correlation risks, while circuits are automatically renewed every ten seconds with variable timing, making network activity unpredictable.
In parallel, a continuous monitoring mechanism analyzes the quality and latency of each path, thus ensuring constant efficiency and stability.
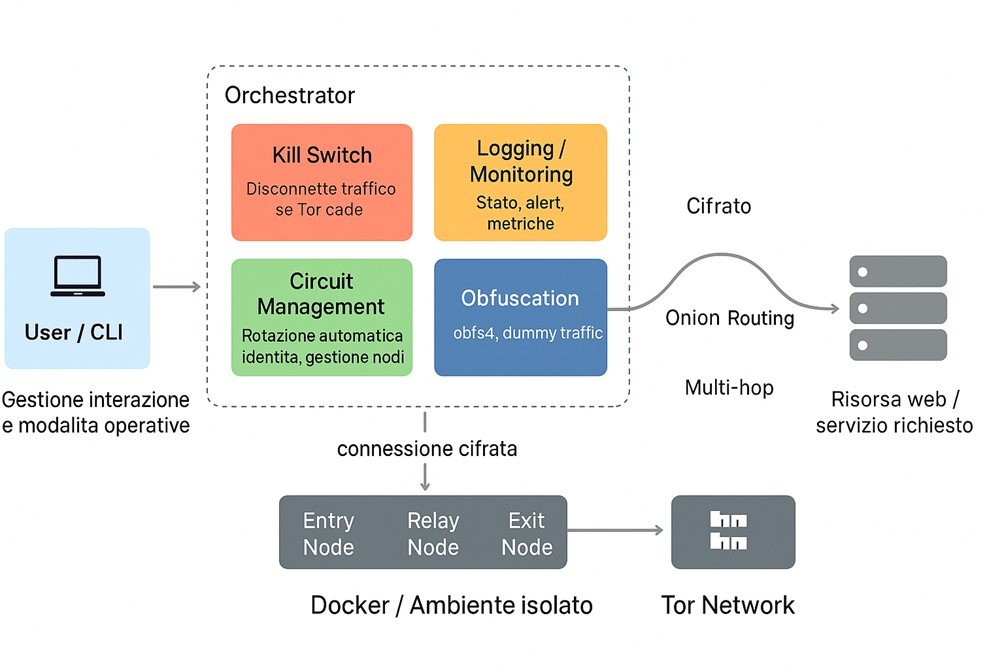
Among the most sophisticated components is the advanced kill switch system, which goes far beyond the classic emergency switch. It is a continuous monitoring mechanism capable of analyzing up to fifteen connection parameters in real time, identifying latency anomalies, packet loss, or suspicious traffic patterns.
In the event of any irregularities, the tool immediately activates a multi-level emergency shutdown protocol, accompanied by a cleanup procedure that eliminates all digital traces from the system’s memory. Essentially, even the slightest network anomaly is handled with instant and targeted countermeasures, making any attempt at de-anonymization extremely difficult.
One of the most sophisticated aspects is the fake traffic generation system, which does not simply send random packets but is based on an intelligent algorithm capable of reproducing credible human browsing patterns.
The engine simulates visits to legitimate sites in a random yet realistic manner, dynamically balancing the ratio of real traffic to obfuscation and modulating the volume of artificial communications based on user activity. This blurs genuine traffic within a much larger background, making traffic correlation extremely challenging.
The tool employs sophisticated countermeasures against browser fingerprinting: it automatically modulates user agents according to unpredictable patterns to prevent direct association with a single client, dynamically alters HTTP headers to mimic different browsers and devices, and intelligently manages cookies and sessions to reduce persistent traces. Additionally, settings such as time zone and location are spoofed, making the signals collected from sites appear inconsistent and making it much more difficult to reconstruct a unique identity from the set of fingerprints.
In independent tests conducted on laboratory infrastructures, TOR Anonymizer v3.0 showed satisfactory results: it preserved anonymity 99.8% of the time against basic correlation attacks and achieved 97.3% effectiveness even against advanced timing attack techniques. A complete digital identity rotation takes less than two seconds, while the computational overhead is kept low, around 15-20% compared to a vanilla Tor distribution. These data indicate that the tool offers an effective balance between robust protection and performance impact.
The system was designed to withstand real-world attacks: first, it carefully selects entry nodes to prevent malicious nodes from infiltrating the network. When necessary, it rapidly switches communication paths and adds “fake” traffic that mimics normal use, thus confusing anyone trying to connect two points in the same session.
For those attempting to analyze the packets, useful information is fragmented and masked across multiple layers, making the attackers’ job much more difficult. Finally, every DNS request passes exclusively through the Tor network, so there are no “leaks” that could reveal which sites are being visited. Essentially, the system combines multiple complementary barriers to protect anonymity in complex scenarios.
TOR Anonymizer v3.0 is not just an operational tool, but also a full-fledged research platform. Thanks to its modular architecture, it offers the ability to experiment with new anonymization techniques in controlled environments, rigorously test the effectiveness of countermeasures against digital surveillance, and develop anti-fingerprinting algorithms for field validation. This makes it not only a privacy protection tool, but also a flexible laboratory for security innovation.
As with any Tor-based solution, the overall effectiveness of TOR Anonymizer v3.0 depends directly on the stability and resilience of the Tor network itself. During periods of heightened surveillance or coordinated attacks on the network, even the most sophisticated tools may be impaired in their ability to provide complete anonymity. It is therefore essential to consider the health of the network as a critical factor in maintaining privacy.
For cybersecurity professionals, TOR Anonymizer v3.0 represents a strategic tool for protecting anonymity and testing advanced privacy defense techniques. While we recognize that no system can guarantee complete anonymity, adopting tools like this significantly reduces the attack surface, tests countermeasures against surveillance and fingerprinting, and integrates traffic obfuscation practices into real-world scenarios. The tool’s modularity and transparency also make it a useful platform for assessing network vulnerabilities and strengthening internal security protocols, providing a tangible operational advantage in managing digital risk.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
