
Google researchers warn that hackers are exploiting a critical vulnerability in Gladinet Triofox to remotely execute code with SYSTEM privileges, bypassing authentication and gaining complete control of the system.
The vulnerability, identified as CVE-2025-12480 (CVSS score 9.1), is related to the access control logic: administrative privileges are granted if the request comes from localhost.
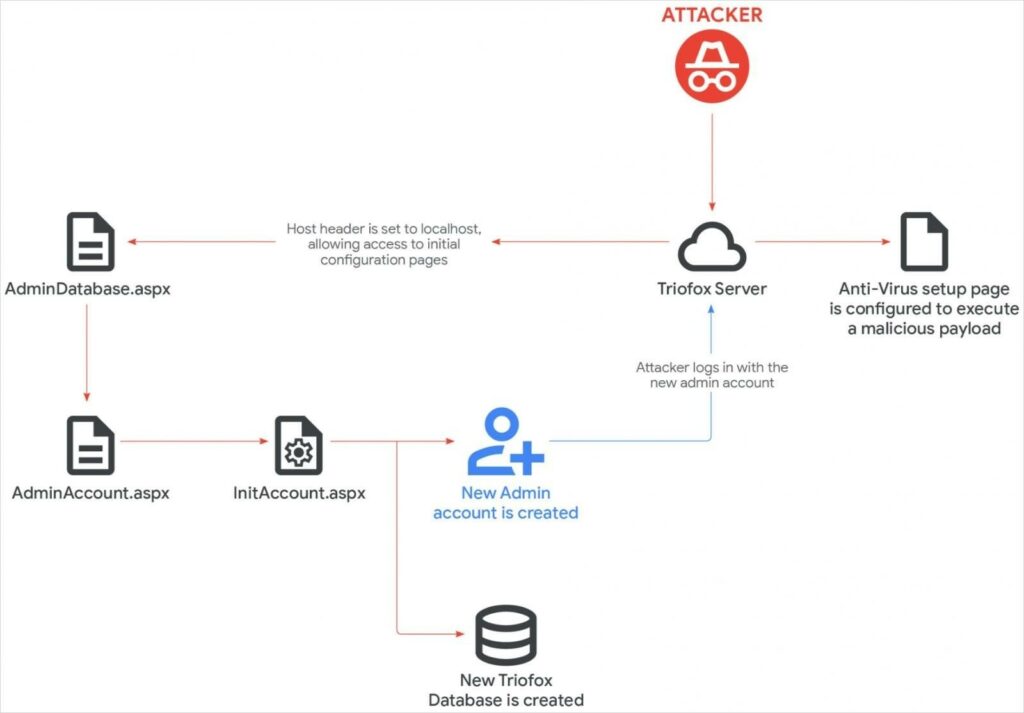
This allows attackers to forge the HTTP Host header and penetrate the system without a password, according to experts at the Google Threat Intelligence Group (GTIG).
Note that if the optional TrustedHostIp parameter is not configured in web.config , the localhost check becomes the only barrier, leaving installations with default settings vulnerable.
A patch for CVE-2025-12480 was included in version 16.7.10368.56560 , released on July 26, and Google experts confirmed to the manufacturer that the issue has been resolved.
However, experts report having already detected malicious activity related to this bug. For example, in August, a hacker group identified by the code UNC6485 attacked Triofox servers running the outdated version 16.4.10317.56372.
In this attack, attackers exploited Triofox’s built-in antivirus . By sending a GET request from localhost to the HTTP referrer, the hackers gained access to the AdminDatabase.aspx configuration page, which is launched to configure Triofox after installation. The attackers then created a new Cluster Admin account and uploaded a malicious script.
The hackers configured Triofox to use the path to this script as the location of its antivirus scanner. As a result, the file inherited the permissions of Triofox’s parent process and ran under the SYSTEM account.
The script then launched a PowerShell downloader, which downloaded the Zoho UEMS installer . Using Zoho UEMS, the attackers deployed Zoho Assist and AnyDesk for remote access and lateral movement, and used Plink and PuTTY to create SSH tunnels to the host’s RDP port (3389).
Experts advise users to update Triofox to the latest version 16.10.10408.56683 (released on October 14) as soon as possible, check administrator accounts, and ensure that the built-in antivirus does not run any unauthorized scripts.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
