Red Hot Cyber – News and insights on cybercrime and cybersecurity
A blow to the heart of cybercrime: RAMP taken offline. The “temple” of ransomware falls!
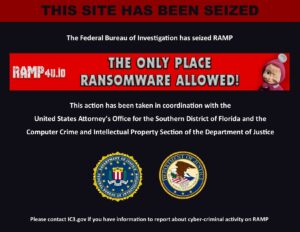
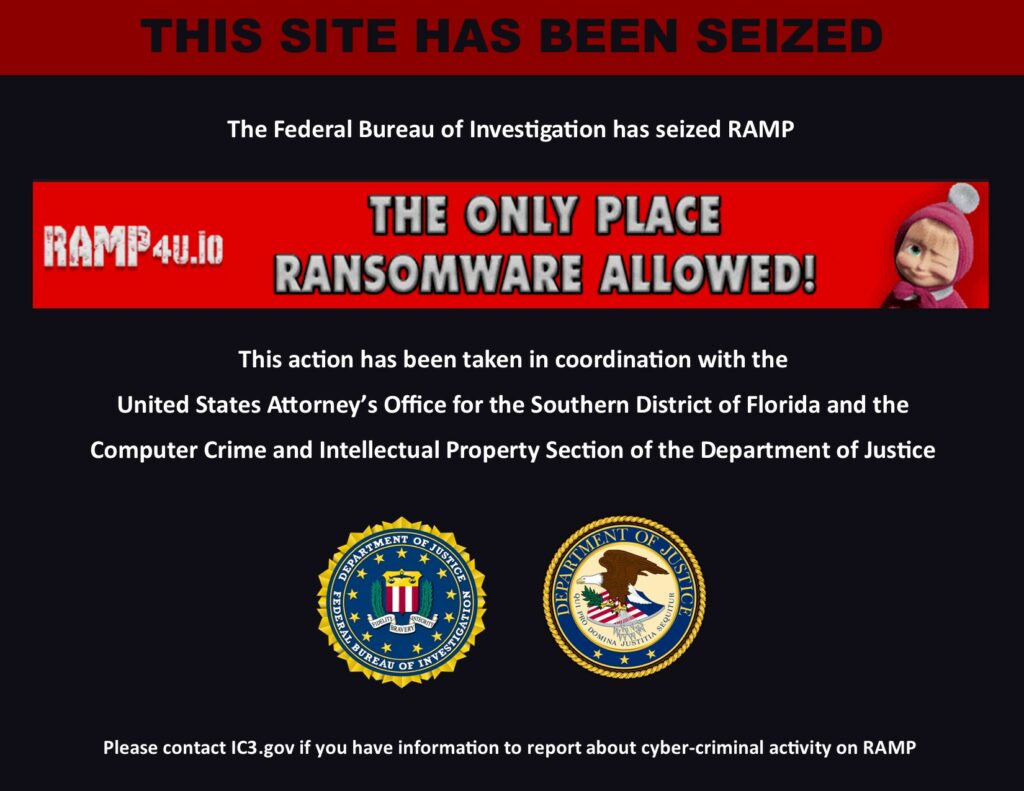
The RAMP (Russian Anonymous Marketplace) forum, one of the main hubs of the international cybercrime underground, has been officially shut down and seized by US law enforcement . The news emerged afte...
Digital Autonomy: France Says Goodbye to Teams and Zoom by 2027
This isn’t the first initiative to emerge on this front recently. Indeed, we’ve heard several of them, one after the other. And it’s almost inevitable: technological autonomy and national security are...
And let the phishing begin! Microsoft is taking action against a zero-day exploit already exploited in Office
Once again, Microsoft was forced to quickly fix some flaws. The company has released unscheduled patches for Microsoft Office, addressing a dangerous zero-day vulnerability that has already been explo...
When Malware Hides in Videos! The PixelCode Technique Breaks the Rules
PixelCode began as a research project exploring a hidden technique for storing binary data within images or videos . Instead of leaving a plaintext executable, the file is converted into pixel data, t...
CISA alert: Exploit underway against VMware vCenter. Risk of RCE without authentication.
The critical vulnerability recently added to the Cybersecurity and Infrastructure Security Agency (CISA) catalog of known exploited vulnerabilities (KEVs) affects the Broadcom VMware vCenter Server an...
“I Stole 120,000 Bitcoins”: The Confession of the Bitfinex Hacker Who Now Wants to Defend Cyberspace
The story ofIlya Lichtenstein, the hacker responsible for one of the largest cyber attacks ever carried out against cryptocurrencies, reads like an episode of a TV series, yet it is absolutely real. A...
NoName057(16) hits Italy 487 times in the last 3 months: the DDoS wave does not stop
Italy has confirmed itself as one of the main targets of the DDoS attack campaign carried out by the hacktivist group NoName057(16) . According to what was declared directly by the collective, our cou...
BlueNoroff: The Hacker Group Revolutionizing Cybercrime
The BlueNoroff hacker group has long since transformed cybercrime into a high-tech business, with tens of millions of dollars, cryptocurrency assets, and entire financial ecosystems at stake. A report...
Nearly 2,000 bugs in 100 dating apps: How your data can be stolen
A study of 100 dating apps revealed a disturbing picture: nearly 2,000 vulnerabilities were detected, 17% of which were classified as critical. The analysis was conducted by AppSec Solutions. The stud...
MacSync: The macOS malware that empties your wallet… after weeks
A new malware campaign has emerged in the macOS world, one that relies not on sophisticated exploits, but on good old-fashioned social engineering. It’s powered by the MacSync malware, distributed usi...
Ultime news
A blow to the heart of cybercrime: RAMP taken offline. The “temple” of ransomware falls!
Is privacy dead? No, but it’s in a coma! What are we really celebrating today, January 28th?
n8n Alert: Two critical RCE vulnerabilities discovered (CVE-2026-1470). Update now!
Telnet, the return of a ghost. A 2015 bug exploited in 2026: 800,000 devices at risk.
OpenSSL: 12 security bugs found, including a critical vulnerability
Digital Autonomy: France Says Goodbye to Teams and Zoom by 2027
A blow to the heart of cybercrime: RAMP taken offline. The “temple” of ransomware falls!
Bajram Zeqiri - January 28th, 2026
Is privacy dead? No, but it’s in a coma! What are we really celebrating today, January 28th?
Silvia Felici - January 28th, 2026
n8n Alert: Two critical RCE vulnerabilities discovered (CVE-2026-1470). Update now!
Redazione RHC - January 28th, 2026
Telnet, the return of a ghost. A 2015 bug exploited in 2026: 800,000 devices at risk.
Pietro Melillo - January 28th, 2026
OpenSSL: 12 security bugs found, including a critical vulnerability
Bajram Zeqiri - January 28th, 2026
Digital Autonomy: France Says Goodbye to Teams and Zoom by 2027
Silvia Felici - January 28th, 2026
Fortinet Vulnerability CVE-2026-24858: Hackers Inside Networks with Legitimate Credentials
Bajram Zeqiri - January 28th, 2026
NSA publishes first operational guidelines on Zero Trust
Silvia Felici - January 28th, 2026
Beware of WhatsApp groups: An image can compromise your smartphone.
Redazione RHC - January 27th, 2026
Linux: A “ghost” kernel bug discovered that had been lurking since 2020!
Agostino Pellegrino - January 27th, 2026
Discover the latest critical CVEs issued and stay updated on the most recent vulnerabilities. Or search for a specific CVE
Featured Articles
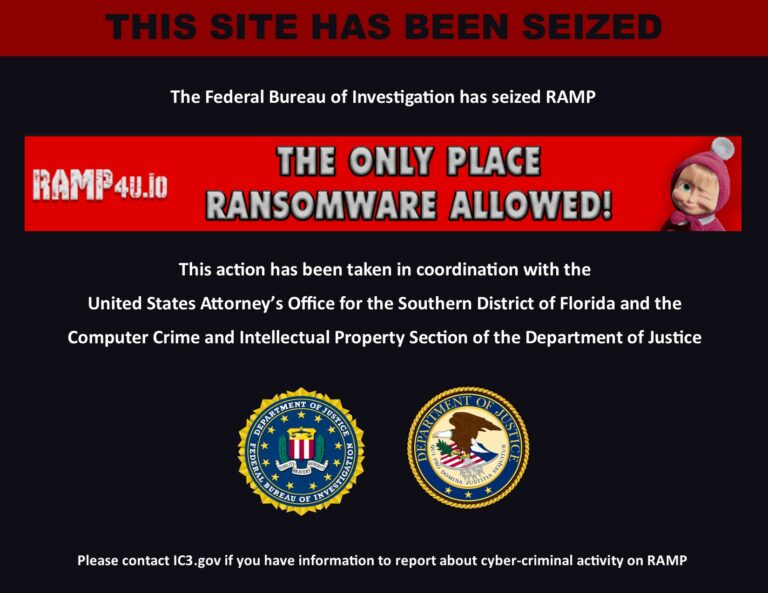 Cybercrime
CybercrimeThe RAMP (Russian Anonymous Marketplace) forum, one of the main hubs of the international cybercrime underground, has been officially shut down and seized by US law enforcement . The news emerged after the domain associated…
 Cyberpolitics
CyberpoliticsThis isn’t the first initiative to emerge on this front recently. Indeed, we’ve heard several of them, one after the other. And it’s almost inevitable: technological autonomy and national security are becoming an increasingly popular…
 Cyber News
Cyber NewsOnce again, Microsoft was forced to quickly fix some flaws. The company has released unscheduled patches for Microsoft Office, addressing a dangerous zero-day vulnerability that has already been exploited in cyberattacks. The issue, identified as…
 Cyber News
Cyber NewsThe recent discovery of a vulnerability in ServiceNow’s AI platform has shaken the cybersecurity industry. This flaw, characterized by an extremely high severity score, allowed unauthenticated attackers to impersonate any corporate user. To launch the…
 Cybercrime
CybercrimeA recent leak revealed 149 million logins and passwords exposed online , including accounts for financial services, social media, gaming, and dating sites. The discovery was made by researcher Jeremiah Fowler and shared with ExpressVPN.…