
In the world of cybersecurity, firewalls are the first line of defense against cyber threats and attacks. Every day, businesses and home users are exposed to risks such as malware, ransomware, and unauthorized intrusions . A firewall acts as a true “digital gatekeeper,” filtering network traffic and blocking suspicious activity before it can cause damage.
But what exactly is a firewall and how does it work?
This security tool can be either hardware or software and operates according to predefined rules to allow or deny data transmission over a network. Without a firewall, any device connected to the internet would be vulnerable to external attacks, increasing the risk of data theft and system compromise.
In this article, we’ll explore the importance of firewalls in protecting businesses, analyzing the different types available and their role in countering cyber threats. We’ll understand why every business, regardless of size, should adopt an effective firewall solution to ensure the security of their digital infrastructure.
A firewall is a computer security system designed to monitor, filter, and control network traffic , preventing unauthorized access and protecting sensitive devices and data. Its name derives from the idea of a wall or “firewall,” a barrier that prevents the spread of cyber threats between different networks.
A firewall works based on a set of predefined rules that establish which connections can be accepted and which should be blocked. This process occurs by analyzing data packets traveling on the network and deciding whether to allow or deny their transmission based on specific criteria.
Firewalls are essential for preventing malicious intrusions, protecting confidential information, and ensuring the security of business and home networks. Without a firewall, an internet-connected device would be exposed to numerous threats, including malware, DDoS attacks, and hacking attempts . In a business setting, their importance is even greater: they protect financial data, digital archives, and critical IT infrastructure. Learn more about how firewalls fit into corporate cybersecurity strategies.
The evolution of cyber threats has led to the development of increasingly sophisticated firewalls, capable of recognizing and blocking advanced attacks. Today, solutions exist that combine traditional firewalls with artificial intelligence and machine learning , improving the ability to detect suspicious behavior and respond to attacks in real time.
In short, a firewall is not only a recommended option, but an absolute necessity for anyone who wants to browse safely and avoid intrusions into their computer systems.
To better understand how firewalls work, it is essential to know the OSI (Open Systems Interconnection) Stack, a reference model that describes the functioning of network communications by dividing it into seven layers .
Each layer has a specific purpose and helps transfer data between devices connected to a network. The OSI stack is composed of the following layers, starting from the lowest:
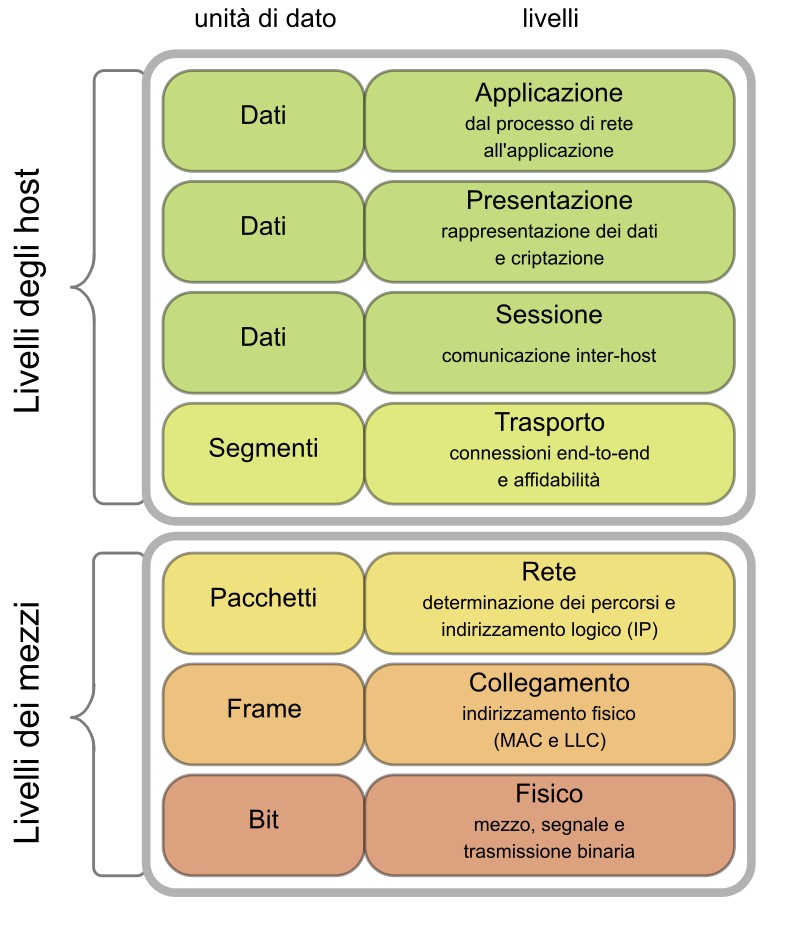
Firewalls operate primarily at the Network, Transport, and Application layers , filtering data packets according to predefined security rules. A packet-filtering firewall , for example, works at the Network layer (Layer 3) , while a stateful inspection firewall also operates at the Transport layer (Layer 4) , analyzing the state of connections.
Next-generation firewalls (NGFWs or WAFs) are even more advanced, extending protection up to the Application Layer (Layer 7) , where they can recognize and block application-specific threats and sophisticated attacks such as SQL injection or zero-day exploits .
Understanding the OSI model is essential to identifying network vulnerabilities and better understanding firewalls, thus implementing more effective security strategies . A cyber attack can occur at different layers of the OSI stack, and a well-configured firewall can block threats before they reach sensitive data. For example, a DDoS attack can be mitigated at the Transport layer, while a phishing attack can be blocked at the Application layer.
Integrating firewalls with other security tools, such as intrusion prevention systems (IPS) and Zero Trust security solutions , allows you to protect your entire network infrastructure and ensure business continuity .
There are different types of firewalls, each designed to meet specific protection needs. Among the main ones are standard firewalls , next-generation firewalls (NGFWs) , and Web Application Firewalls (WAFs) . Each of these solutions offers a different level of protection within the OSI stack and can be chosen based on the complexity of the network and the nature of the threats faced.
Standard, or traditional, firewalls are the most common and are used to filter traffic based on predefined rules. They typically operate at the network (Layer 3) and transport (Layer 4) layers of the OSI model, analyzing incoming and outgoing data packets and deciding whether to allow or block the connection. These firewalls are particularly useful for protecting simple networks and small businesses, where network traffic is not complex and advanced features are not required.
However, traditional firewalls have some limitations, such as their inability to detect more sophisticated attacks, such as application-layer attacks or more targeted threats. Furthermore, they cannot analyze the contents of packets, limiting themselves to verifying the source and destination addresses.
Next-generation firewalls (NGFWs) are designed to address modern and more sophisticated threats. These firewalls integrate advanced features compared to traditional firewalls, such as deep packet inspection (DPI) and traffic analysis at the Application layer (Layer 7) . NGFWs don’t just filter traffic based on static rules, but use advanced artificial intelligence and machine learning algorithms to identify and block complex attacks such as malware, ransomware , and zero-day exploits .
Additionally, NGFWs also support user identity management , allowing you to monitor and control traffic based on users, not just IP addresses. These firewalls can also integrate with VPNs and Zero Trust solutions, making them ideal for protecting modern enterprise networks, where borders are more fluid and attacks can come from multiple sources.
Web Application Firewalls ( WAFs ) are a type of firewall designed to protect web applications from common attacks targeting this layer, such as SQL injection , cross-site scripting (XSS) , and file inclusion . Unlike traditional firewalls that operate primarily on networks and devices, WAFs focus on protecting websites and online applications by filtering incoming HTTP/HTTPS traffic.
WAFs analyze web traffic in real time to detect and block suspicious requests that could compromise application security. These firewalls are particularly useful for companies that run online platforms, e-commerce, or SaaS applications, as they protect against specific vulnerabilities that traditional firewalls cannot block. WAFs are also critical for protecting against application-based DDoS attacks , which aim to overload a web platform and render it unusable.
The growing sophistication of cyber attacks makes network protection crucial for every business, regardless of size. Deploying a firewall is no longer just a recommended choice, but a necessity to ensure the security of corporate data , protect internal resources, and maintain operational reliability. But why should every company invest in a firewall? Here are some key reasons.
In an increasingly connected world, cyber threats are commonplace. From unauthorized access to corporate systems to the theft of sensitive data , including attacks like malware, ransomware, and phishing , companies are constantly under attack. A well-configured firewall is the first line of defense against these threats, blocking suspicious connections and preventing malicious actors from entering the corporate network. Thanks to real-time monitoring, a firewall can identify anomalous behavior and block access to systems before the damage becomes irreparable.
Every business, large or small, handles sensitive data that needs to be protected. This data may include financial information, personal customer data, or confidential company documents. Firewalls are designed to prevent unauthorized access and data theft . By securing the gateways to the corporate network, a firewall ensures that only authorized users or devices can access critical information, preventing privacy breaches and reducing the risk of data protection-related legal penalties.
A firewall not only protects against external threats, but also provides granular control over network traffic. Companies can define custom rules to allow or block specific types of traffic based on their needs. For example, they can restrict access to certain websites, prevent communication with certain networks or applications, and monitor employee online activity to prevent access to malicious or irrelevant content. The firewall therefore helps optimize and control the use of network resources, improving efficiency and reducing the risk of security incidents.
Many corporate regulations, including the GDPR (General Data Protection Regulation) in Europe and the CCPA (California Consumer Privacy Act) in the United States, require companies to protect customer data and implement adequate security measures. A well-configured firewall is one of the tools that helps companies meet these requirements, avoiding fines and reputational damage resulting from data security breaches. Investing in a firewall also ensures that the company remains compliant with data protection laws.
In a business environment, any service disruption can have a significant impact on productivity and profits. Distributed Denial of Service ( DDoS ) attacks, for example, are designed to overwhelm corporate servers with a massive flow of traffic, causing service disruptions and downtime . Firewalls, especially next-generation firewalls (NGFWs) , can filter traffic in real time, preventing these threats from paralyzing business systems. Protection against DDoS attacks is one example of how a firewall can ensure business continuity and reduce the risk of financial loss.
While firewalls are among the most effective security tools for protecting corporate networks, even these devices are not immune to vulnerabilities that can be exploited by malicious attackers. Vulnerabilities in firewalls can pose significant threats to the security of the entire corporate IT infrastructure, compromise data confidentiality, and, in some cases, allow hackers to take complete control of the network. One of the most serious vulnerabilities is Remote Code Execution (RCE) , a vulnerability that allows attackers to remotely execute malicious code on devices protected by the firewall. This type of vulnerability is particularly dangerous because it offers attackers the opportunity to compromise the firewall itself and, consequently, evade network defenses.
RCE vulnerabilities in firewalls allow hackers to access the device’s internal functions and manipulate configuration parameters, disabling or bypassing default security policies. In some cases, this can allow them to open unauthorized ports , execute remote commands, collect sensitive data, or, worse yet, completely compromise the entire network defense system. Therefore, companies must be aware that the protection offered by a firewall is only valid as long as the device is properly configured and free of exploitable vulnerabilities.
Another crucial aspect concerns access to firewall management consoles. These consoles are the primary control point for configuring and managing network security, and allow those with access to modify firewall settings. If these consoles are accessible over the Internet , exposure to potential attacks increases significantly. Attackers can exploit open access ports to attempt to obtain administrator credentials or exploit known vulnerabilities in management software. It is therefore essential to disable Internet access to management consoles and restrict it to local IP addresses or a virtual private network (VPN), thus drastically reducing the risk of compromise by external attacks.
In addition to access management, it is vital that firewalls are constantly monitored . Security bugs , both new and existing, can emerge even on seemingly secure devices. Firewall vendors frequently release security updates to fix newly discovered vulnerabilities. The importance of monitoring and applying updates promptly cannot be underestimated. The patch management process must be a regular and automated activity to apply necessary fixes without delay. Ignoring security updates leaves the system vulnerable to attack, putting the corporate network at risk.
Firewalls remain one of the fundamental tools for ensuring corporate network security. Their ability to monitor, filter, and protect network traffic makes them crucial for defending IT infrastructures from unauthorized access, malware, and hacker attacks. However, it’s essential to understand that a firewall, while powerful, is not a foolproof solution. Vulnerabilities that can affect firewalls themselves, such as Remote Code Execution vulnerabilities, and improper management of console access can seriously compromise corporate security.
To adequately protect your business, it’s essential to properly configure firewalls, disable unnecessary remote access, and constantly monitor the network for threats. Furthermore, the patch management process must be integrated into your company’s security strategy, ensuring that vulnerabilities are patched promptly.
In short, while a firewall is an essential element of cybersecurity, its effectiveness depends on the attention given to it. Companies must be aware that network protection requires a combination of technologies, management strategies, and daily practices to ensure firewalls remain effective and don’t become a weak point in their security defenses. Deploying a firewall without constant attention to its management and updates is not enough. Security, in fact, is an ongoing process that requires constant attention.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
