
The ransomware threat landscape is constantly evolving, with increasingly structured groups adopting sophisticated strategies to maximize profits. VanHelsing is a new player positioning itself in the Ransomware-as-a-Service (RaaS) market, a model that enables even cybercriminals with limited expertise to conduct advanced attacks using an automated platform.
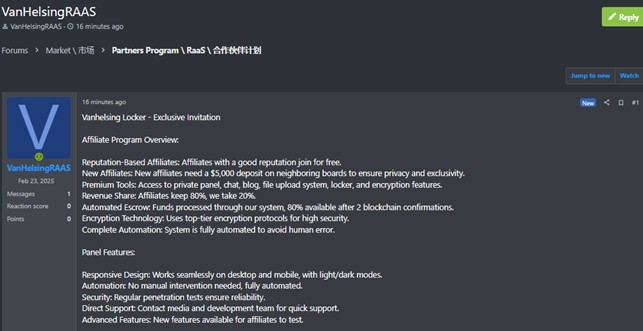
Following the February 23, 2025 announcement on an underground forum regarding the VanHelsing RaaS affiliate program, the ransomware group has officially published its first possible victim on its Data Leak Site (DLS).
Less than a month after its launch, the appearance of the first compromised organization confirms that VanHelsing is now actively operating. Although the DLS remains sparse, the emergence of a victim suggests that affiliates are already distributing the ransomware and that the number of attacks could escalate quickly.
The February 23 announcement revealed significant details about how the VanHelsing RaaS program operates. It stands out for its selective recruitment strategy and advanced tools.
The first potential victim of VanHelsing RaaS operates in the public sector, with administrative functions. This suggests that the group may be targeting government entities, municipalities, or public services, sectors often vulnerable to ransomware.
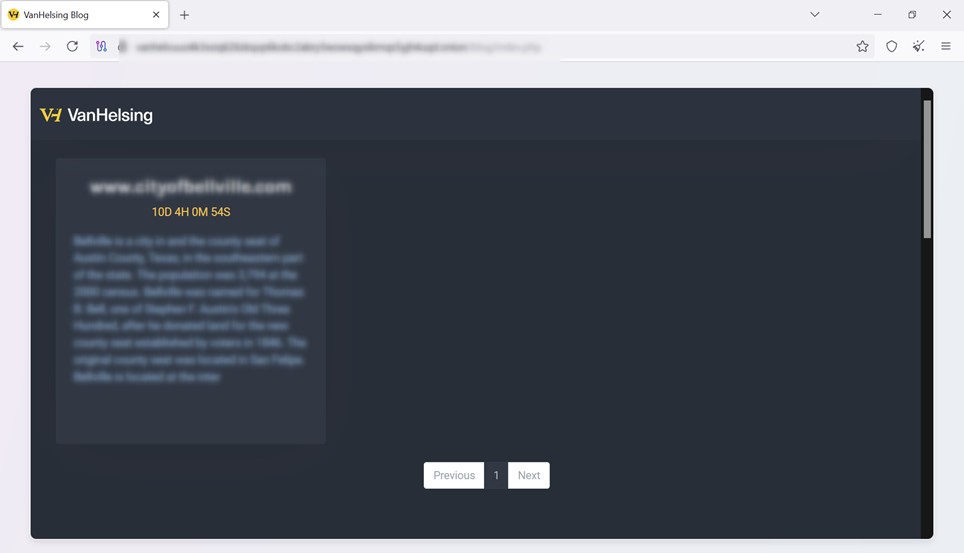
The attack appears to follow a double extortion strategy, featuring a 10-day countdown before exfiltrated data is published. This implies that VanHelsing is likely negotiating a ransom with the affected entity, attempting to maximize profits before making any sensitive information public.
At present, VanHelsing’s DLS contains only one possible victim, which could indicate several scenarios:
Experience with other RaaS groups shows that the number of victims tends to grow rapidly as more cybercriminals start using the service.
Another key element of VanHelsing is its private chat portal, accessible only via a Session ID. This suggests that the group manages ransom negotiations directly with victims and communicates with affiliates without relying on public platforms like Telegram or underground forums.
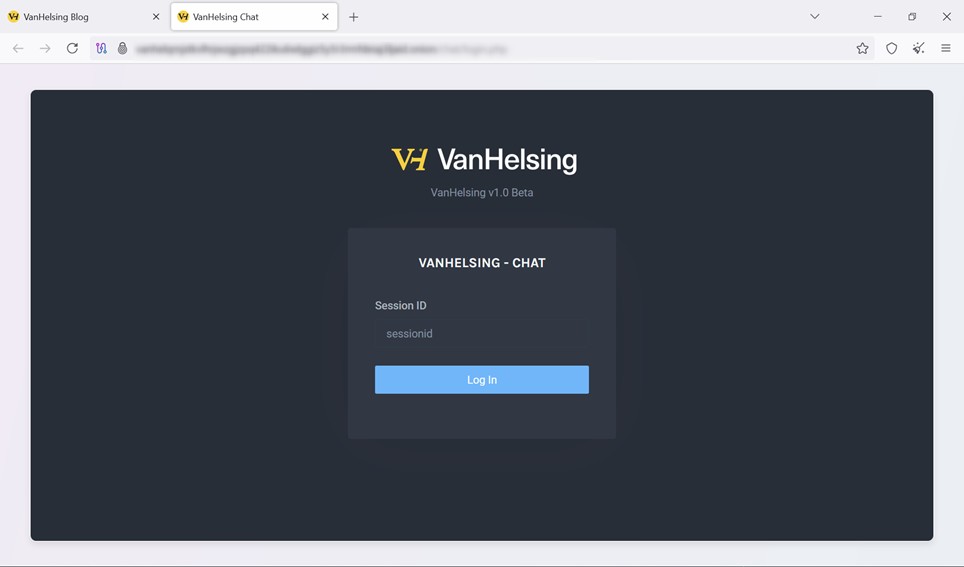
This infrastructure indicates that VanHelsing operates as a centralized and professional ransomware group, distinguishing itself from less organized actors.
The emergence of VanHelsing RaaS represents another evolution in the ransomware model, with a highly scalable infrastructure and advanced tools for affiliates. Their focus on automation and operational security suggests that we may see an increase in attacks in the coming months, with significant impacts on businesses and critical infrastructure.
Although the DLS remains minimal for now, the appearance of the first victim in less than a month confirms that the group is already executing real-world attacks. If VanHelsing’s RaaS model gains traction among cybercriminals, the number of attacks could rise rapidly, making it a serious emerging threat in the ransomware ecosystem.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
