
A new report published by the Huntress Tactical Response Team documents a highly sophisticated intrusion detected in December 2025 , in which an advanced actor managed to compromise a VMware ESXi infrastructure by exploiting a VM escape – a breakout from a guest virtual machine into the underlying hypervisor.
According to analysts, the attack relies on a toolkit that was developed and operational long before the exploited vulnerabilities were publicly disclosed , highlighting how some critical flaws in the virtualization ecosystem have likely been exploited as zero-days for over a year .
Contrary to what one might expect from an operation of this scale, the initial access did not occur through a hypervisor vulnerability, but through the compromise of a SonicWall VPN account .
From here, the attackers gained access to an internal Windows environment and began a lateral movement phase that took them from a backup Domain Controller to the primary Domain Controller .
Only after consolidating control over the Windows infrastructure did the attackers deploy an advanced toolkit orchestrated by a binary named “MAESTRO” ( exploit.exe) , which was used as the coordinating component of the entire attack chain.
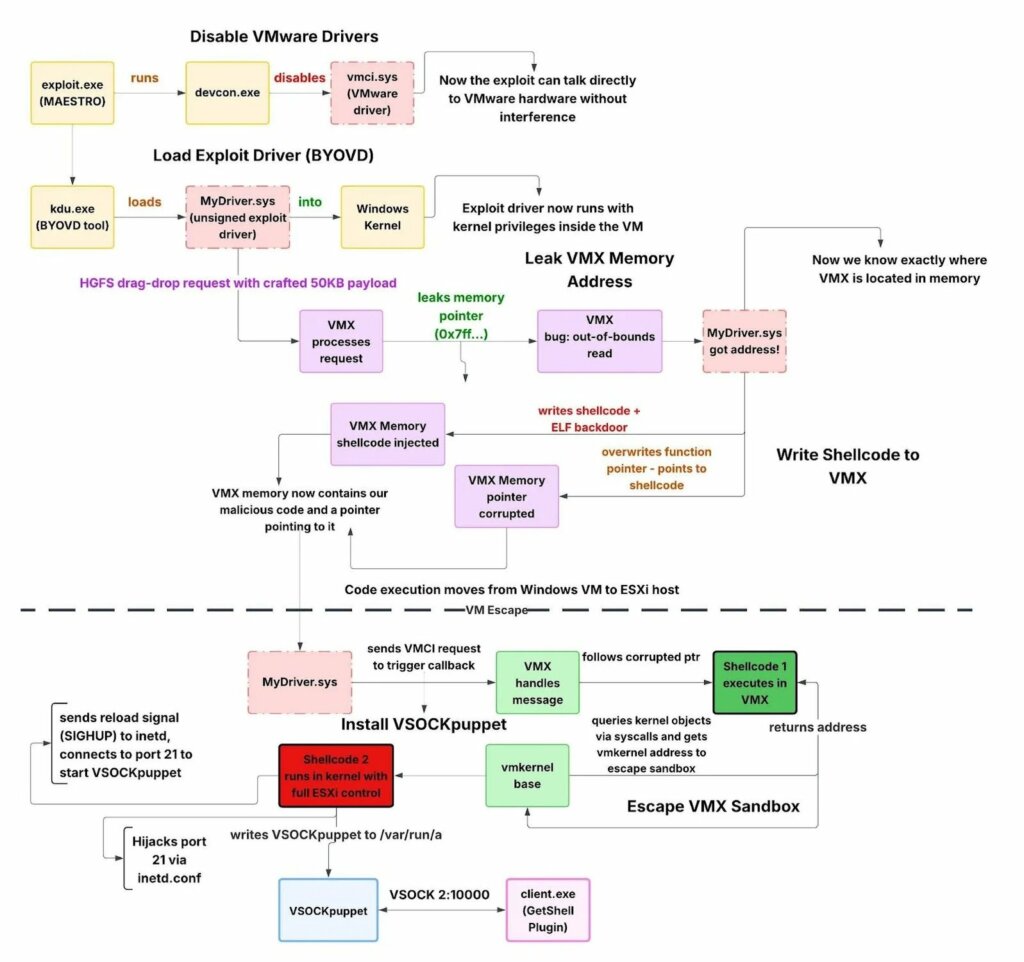
Within the compromised Windows systems, Huntress researchers report , the toolkit exploited the Bring Your Own Vulnerable Driver (BYOVD) technique to gain kernel-level privileges . This involves loading an unsigned malicious driver, MyDriver.sys , whose purpose is not to target the ESXi hypervisor, but rather:
It is important to note that ESXi does not run Windows code and that BYOVD represents only an escalation and consolidation phase within the Microsoft infrastructure, acting as a stepping stone towards the virtualization environment.
The most critical phase of the operation is represented by VM escape , achieved by exploiting one or more vulnerabilities in the interface between the guest and the hypervisor . This type of attack does not “disable VMware drivers from within the VM”, but rather affects bugs in hardware emulation or in guest-host communication mechanisms , such as VMX processes and virtual devices.
The report links the attack to the exploitation of vulnerabilities subsequently identified as:
At the time of the intrusion, these vulnerabilities were not yet publicly available , suggesting active use as zero-days prior to official disclosure by VMware.
As Huntress points out: “Virtual machine isolation is not absolute. Vulnerabilities in the hypervisor can allow attackers to escape from the guest VM and compromise all workloads on the host.”
Once they gained access to the ESXi host, the attackers deliberately avoided using traditional network communications, which would have been intercepted by firewalls, IDSs, or NDR systems. Instead, they implemented a backdoor called VSOCKpuppet .
This malware exploits VSOCK (Virtual Sockets) , a high-speed communication channel designed for host-guest traffic within VMware environments. VSOCK abuse allows attackers to:
Activity remains visible at the ESXi host level, but is opaque to network-centric security controls .
During forensic analysis, researchers located simplified Chinese strings within the development paths, including a directory named “全版本逃逸-交付” , which translates to “All versions escape – delivery” .
Timestamps and references in the PDB files indicate that the toolkit was already up and running in February 2024 , more than a year before the public disclosure of the exploited CVEs.
According to Huntress: “The development history suggests that this exploit existed as a zero-day for an extended period, highlighting the risk posed by well-funded actors with continued access to unpatched vulnerabilities.”
The toolkit is designed as a true universal key , with declared support for 155 builds of VMware ESXi , from versions 5.1 up to 8.0 , including numerous end-of-life releases still in widespread use in enterprise environments.
Huntress urges organizations to reconsider the assumption that virtualization is an inherent security barrier. Recommendations include:
The bottom line is clear: relying solely on VM isolation and network defenses is no longer enough.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
