
Check Point researchers have discovered a new Linux infection framework distinguished by its advanced modular architecture and wide range of features. The malware has been dubbed VoidLink .
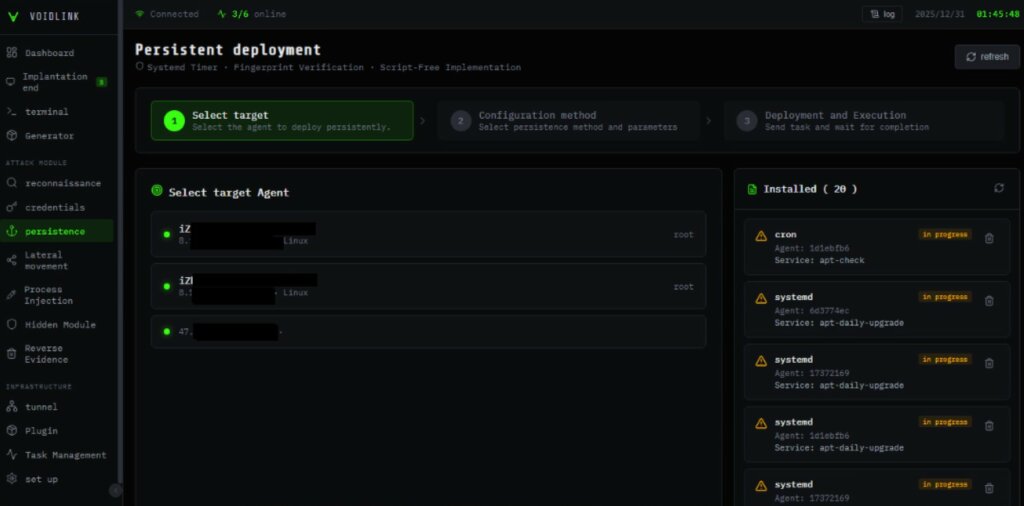
The framework is composed of over 30 modules that can be combined to meet specific attacker objectives on each infected machine. These modules add stealth capabilities, reconnaissance tools, privilege escalation, and lateral movement within the compromised network. The components are easily plugged in and out: the architecture allows for on-the-fly functionality changes as the campaign progresses.
Researchers report that VoidLink is written in Zig, Go, and C and can detect whether an infected computer is using popular cloud services: AWS, GCP, Azure, Alibaba, and Tencent. The code also includes patterns for detecting solutions from Huawei, DigitalOcean, and Vultr. The malware developers are believed to intend to add these in future versions. To determine the cloud provider, the malware accesses metadata via the corresponding provider’s API.
Similar frameworks for Windows servers have existed for some time, but similar solutions for Linux are less common. VoidLink’s capabilities are extensive and “significantly exceed those of typical Linux malware,” according to Check Point. The company believes the emergence of such a tool may signal a shift in attackers’ attention toward Linux systems, cloud infrastructure, and containerized environments, where organizations are increasingly migrating workloads.
“VoidLink is a comprehensive ecosystem for long-term stealth access to compromised Linux systems, particularly those running on public cloud platforms and containerized environments,” the researchers write in a separate publication . “The level of sophistication suggests significant resources and planning, typical of professional APT groups, rather than opportunistic attackers.”
The malware communicates with its operators using multiple protocols ( HTTP, WebSocket, DNS tunneling, ICMP ), which are wrapped in a special encryption layer called VoidStream , which masks the traffic as normal web or API activity.
Furthermore, VoidLink’s interface is localized for Chinese operators, indicating the malware’s Chinese origin . Comments in the code indicate that the framework is still under development. This is indirectly confirmed by another fact: Check Point specialists have found no evidence that VoidLink has been actively used in real-world attacks; the malware was discovered last month on VirusTotal.
A two-stage loader was found in the binary set. The final package contains integrated core modules that can be extended with plugins loaded and installed during operation. After analyzing the 37 discovered modules, researchers identified the following malware features.
Since no signs of active VoidLink exploitation have been detected, no immediate action is required from defenders. Indicators of compromise are available on the Check Point blog.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
