
Redazione RHC : 29 July 2025 23:18
Across the UK, people are turning to location-blocking virtual private networks (VPNs) to circumvent new national rules on online age verification. Last week, new age verification rules came into force through the UK’s Online Safety Act, requiring people to present ID, facial scans to estimate their age, and financial documents such as credit card checks to access adult websites, such as pornography platforms.
However, age verification has a dark side: invasion of privacy. Given the requirement to share a government-issued ID to watch Pornhub, RedTube, and YouPorn in the UK, many people refuse to participate.
As we’ve seen, it seems Pornhub cares deeply about its UK audience because it has decided to comply with the law. If we consider the infamous Pornhub ban in South Carolina, we can see how it failed to comply with the law, which led to its unavailability in that state. People in the UK may consider themselves luckier, although this law can be circumvented very easily.
Immediately after the law went into effect, VPN company Proton posted on the social media platform Xthat it had seen subscriptions to its services increase by more than 1,400 percent in the UK. The company said this surge in interest was “sustainable,” unlike other recent spikes, such as when people in France temporarily lost access to adult sites like Pornhub and RedTube due to legislative changes.

Data from Google Trends, meanwhile, shows that searches for VPN companies like Surfshark increased 300 percent over the weekend across the UK, and in some regions, reached peak popularity. Searches for related topics, such as “internet age verification system proposed in the UK” and “age verification system,” increased by 2,450% and 1,950%, respectively.
A VPN (Virtual Private Network) establishes an encrypted digital connection between your computer or device and a remote server owned by a third party. provider.
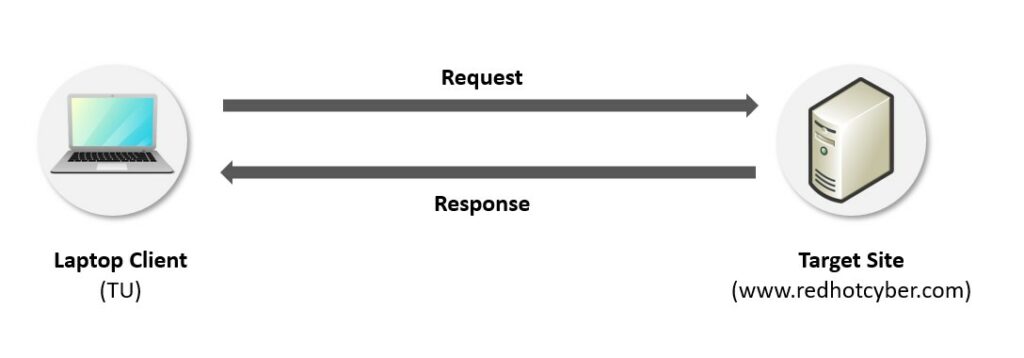
Normally, when a user visits a website, a direct connection is established with the web server, which precisely knows the client’s IP address and some information about the device used, such as the operating system, browser type, preferred language, and approximate geographic location. This information can be used to personalize the user experience, but also to track the user’s online activity, monitor behavior on the site, and, in some cases, for advertising or profiling purposes.
Using a VPN (Virtual Private Network) changes this scenario. When you connect to a site via a VPN, the IP address visible to the web server is that of the VPN server, not the client’s real IP address. In this way,the VPN hides the user’s true identity, offering a level of anonymity and privacy protection. Furthermore, the VPNencrypts the connection, protecting data from interception during transmission, especially on public or unsecured networks. This makes it much more difficult for third parties to monitor online activity or collect sensitive information.
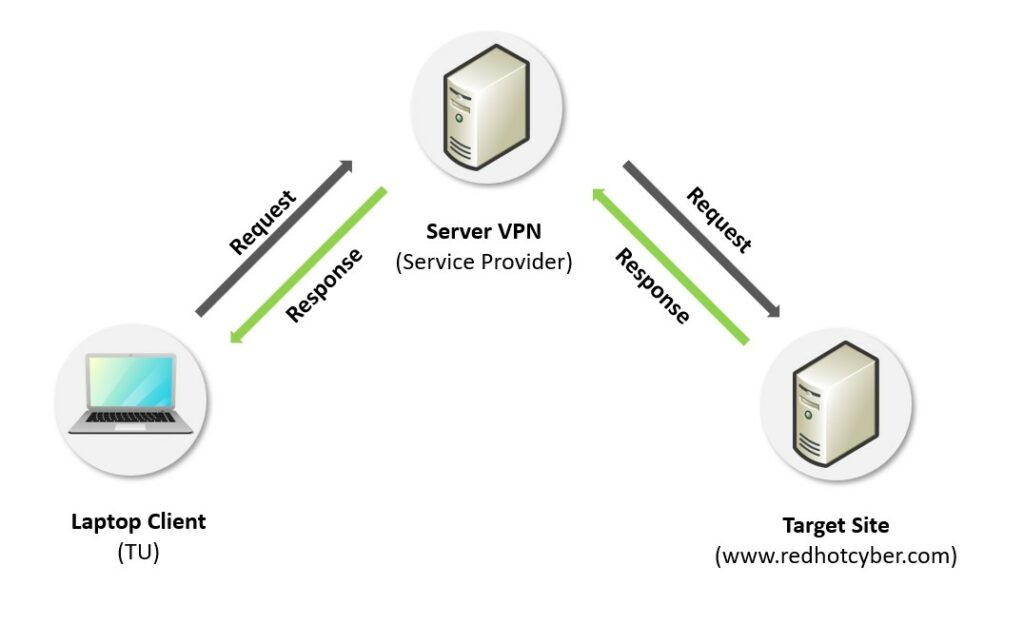
In the diagram above, when a request is sent over the internet, it is routed to the VPN server, which masks its origin and protects it with encryption. The VPN server then forwards the request to the destination site and, once it receives a response, redirects it back to the user. This process guarantees both the security and anonymity of the connection.
There are dozens of solutions in the VPN (Virtual Private Network) market, some completely paid and others that also offer a free version, often with limited features or traffic limits.
VPNs are primarily used to protect online privacy, browse anonymously, bypass geographic restrictions, and improve security on public networks.
Below you will find A table summarizing the most popular and reliable VPNs, indicating:
| VPN Name | Free / A payment | Official website |
|---|---|---|
| NordVPN | Paid only | https://nordvpn.com/ |
| ExpressVPN | Only at payment | https://www.expressvpn.com/ |
| Surfshark | Paid only | https://surfshark.com/ |
| CyberGhost | Paid only (period try) | https://www.cyberghostvpn.com/ |
| Private Internet Access (PIA) | Paid only | https://www.privateinternetaccess.com/ |
| ProtonVPN | Free version + version premium | https://protonvpn.com/ |
| Windscribe | Free version + premium version | https://windscribe.com/ |
| TunnelBear | Free version (data cap) + version premium | https://www.tunnelbear.com/ |
| Hotspot Shield | Free version (limited) + premium | https://www.hotspotshield.com/ |
| Atlas VPN | Free version + version premium | https://atlasvpn.com/ |
| Hide.me | Free version + premium version | https://hide.me/ |
VPNs are valuable tools for those who want to protect their online privacy, bypass geographic restrictions, and fight censorship. For this reason, they are also used by journalists, political dissidents, and activists who live or work in countries hostile to freedom of information, where protecting their digital identity can mean the difference between communicating freely or suffering repression.
However, the reliability of VPNs is not absolute: in recent years, several cyber incidents have highlighted the fragility of some of these platforms, demonstrating that tools designed to protect privacy have in some cases produced the opposite effect, exposing sensitive data or connection logs. Furthermore, in countries like the United Kingdom, using a VPN to bypass filters or blocks may be considered a violation of local regulations. Therefore, it’s important to remember that, while VPNs are legal in most parts of the world, they should be used wisely and always in compliance with regulations.
 Redazione
Redazione