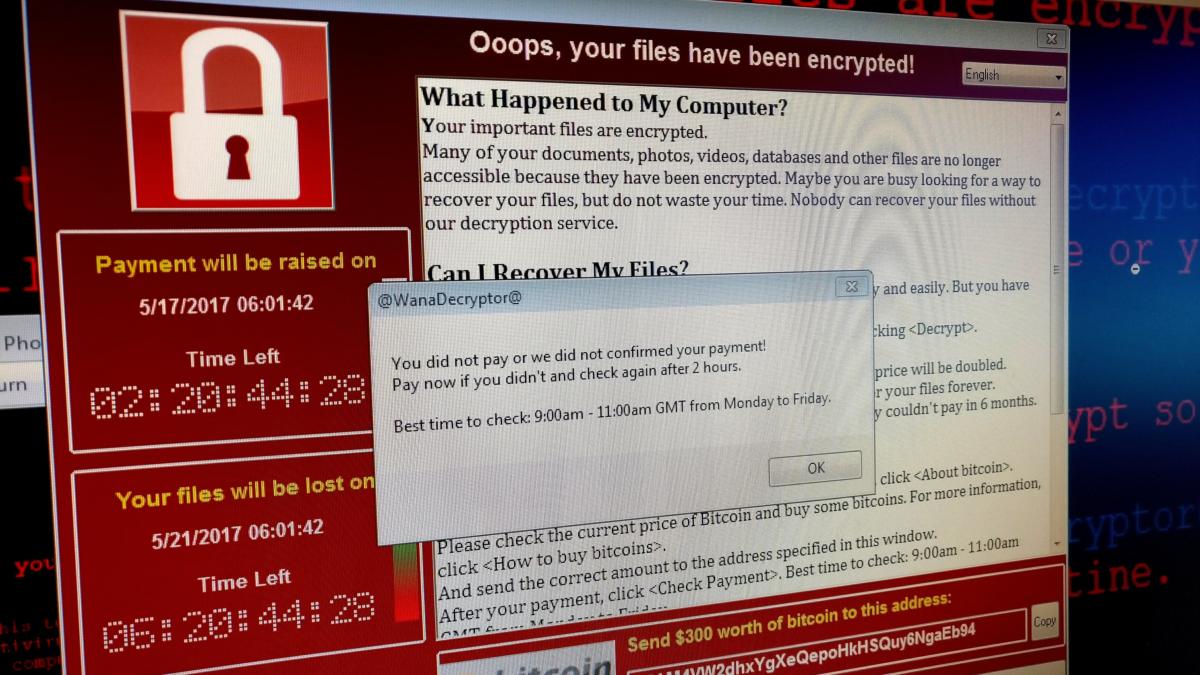
Il 12 di maggio del 2017, è stata una giornata particolare.
Per molti non significherà nulla, ma altri la ricorderanno bene, perché è stata una giornata convulsa e movimentata in quanto il mondo venne catapultato nella prima infezione globale da ransomware della storia.
Infatti il 12 maggio viene ricordato come il giorno 0 di WannaCry, il malware che crittografava i contenuti all’interno di un computer chiedendone un riscatto.
Tutto comincia nella mattinata del 12 di maggio del 2017, quando Telefonica (il noto ISP spagnolo) dirama un comunicato che raccomanda ai propri clienti di spegnere i computer per via di un attacco informatico in corso.
In poche ore WannaCry inizia a mietere vittime in tutto il mondo, infatti il New York Times pubblica una mappa interattiva che mostra l’andamento dei focolari d’infezione in realtime e tutto il mondo è in allerta, inserendo nel vocabolario e nel gergo comune la parola “ransomware”, ovvero un malware che chiede un riscatto per decifrare i dati presi in ostaggio all’interno di un pc.
Ma a parte la weaponization, l’exploit Eternalblue, The Shadow Broker e Lost in Translation (cose delle quali abbiamo parlato a lungo), oggi ci concentreremo sugli aspetti più storici della massiccia infezione mondiale che causò il collasso di 230.000 computer in 150 paesi, inclusa Russia, Cina, Usa, Regno unito ed ovviamente l’Italia.
WannaCry colpì i sistemi Windows e a dicembre 2017, il governo degli Stati Uniti dopo una serie di indagini, considerò pubblicamente responsabile la Corea del Nord dell’attacco WannaCry, anche se la Corea ha sempre negato l’origine dell’attacco.
Tra le organizzazioni maggiormente colpite, ci furono molti ospedali del Servizio sanitario nazionale della Gran Bretagna e della Scozia con 70.000 dispositivi in ostaggio dei criminali informatici oltre a risonanze magnetiche, frigoriferi per la conservazione del sangue e attrezzature di diverso tipo.
Venne identificato come artefice di WannaCry, con un documento di 179 pagine prodotto dal dipartimento della giustizia degli Stati Uniti d America, l’allora trentaquattrenne Park Jin Hyok, responsabile anche di una serie di attacchi contro le reti di Sony Pictures Entertainment e ad altre banche in tutto il mondo, oltre ad essere stato correlato al gruppo APT Lazarus.

A Park si associa la scrittura del malware WannaCry, ma in questa storia molto ingarbugliata, dal 12 di maggio del 2107 altri eroi si sono fatti avanti per difendere il pianeta da questa grandissima pandemia informatica di massa.
Parlo di Marcus Hutchins chiamato MalwareTech, che durante la fase acuta dell’infezione da WannaCry, stava analizzando i primi campioni del malware, quando scoprì che al suo interno, era stato creato quello che in gergo tecnico si chiama “kill switch”, una sorta di “interruttore” capace di bloccare l’infezione.
Infatti WannaCry richiamava costantemente un dominio. Se il dominio risultava non attivo, l’infezione andava avanti, ma se invece il dominio rispondeva, il ransomware bloccava la sua attività.
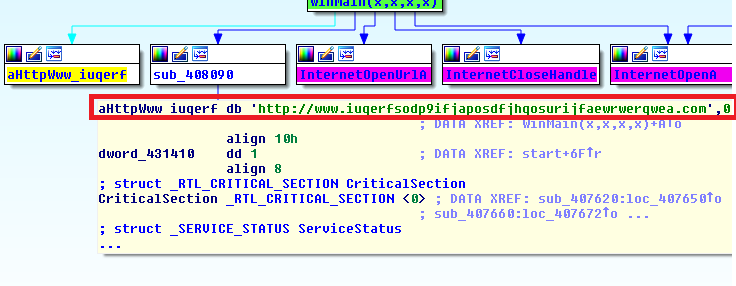
Kill switch presente all’interno del ransowmare WannaCry
MalwareTech non fece altro che registrare questo dominio con un investimento pari a 10 dollari dell’epoca, inizialmente pensando che in questo modo potesse capire meglio la diffusione del contagio. Ma capi presto ben presto che l’algoritmo interno di WannaCry verificava la sua presenza e in caso positivo bloccava l’infezione.

Marcus Hutchins chiamato MalwareTech
WannaCry verrà ricordato da tutti come un avvenimento “biblico” nella letteratura della sicurezza informatica, un caso mondiale, riconosciuto da tutti, una sorta ILOVEYOU più grande e tecnologicamente più avanzato e soprattutto più pervasivo.
I ransomware oggi sono una grande minaccia per ogni organizzazione piccola o grande che sia, e i nuovi ransomware non perdonano, in quanto se non paghi il riscatto, pubblicano i contenuti trafugati illegalmente con danni inimmaginabili per le organizzazioni.
Si tratta del fenomeno della RaaS (Ransomware As a Service), composto da criminali che sviluppano il software e affiliati che lo utilizzano per sferrare gli attacchi. Una sorta di meccanismo virtuoso che fa guadagnare molti soldi a tutti e sta creando sempre più problemi alle organizzazioni, con incidenti di rilievo e taglie mostruosamente elevate.
Quando finirà il fenomeno del Ransomware?
Fino ad oggi risulta in costante ascesa.
Sono passati 4 anni da WannaCry, ma e Il ransomware è maturato e il suo livello di minaccia è ora alla pari degli APT, poiché gli attaccanti usano strumenti migliori e imparano dagli errori del passato per mantenere persistenza all’interno delle organizzazioni.
Quindi prestiamo la massima attenzione ad un allegato presente all’interno di una mail di dubbia provenienza prima di aprirlo.
Siete tutti avvertiti!
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…