
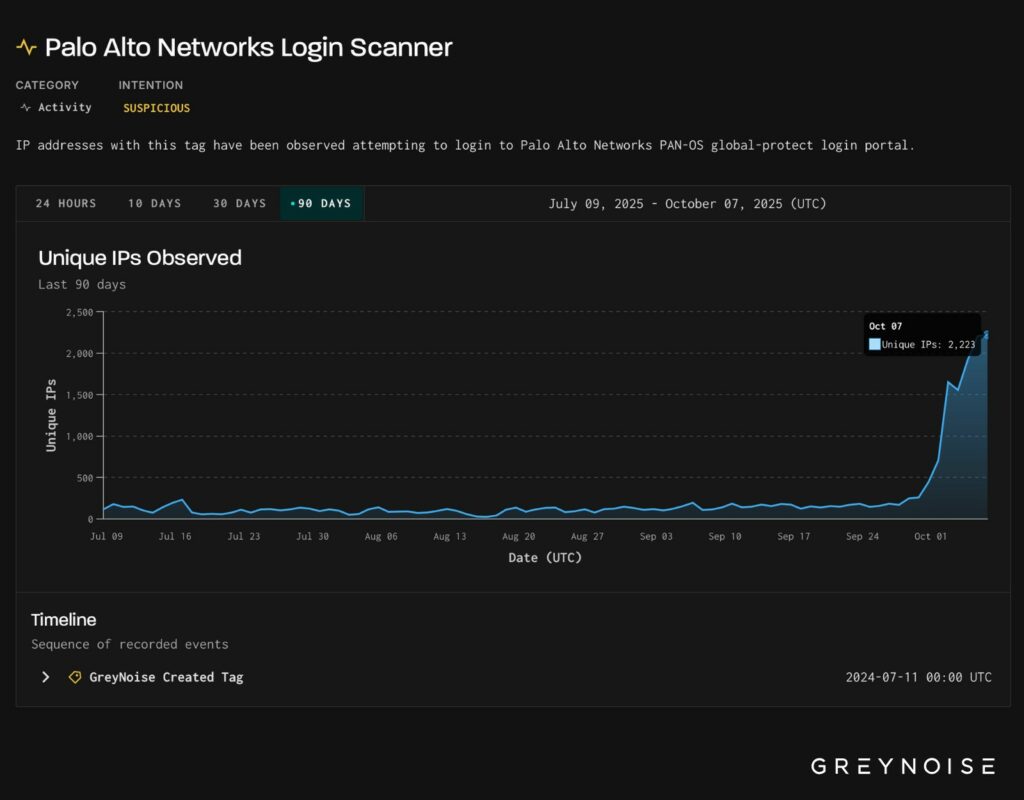
A partire dal 7 ottobre 2025, si è verificata un’intensificazione su larga scala di attacchi specifici contro i portali di accesso GlobalProtect di Palo Alto Networks, PAN-OS. Oltre 2.200 indirizzi IP unici sono stati coinvolti in attività di ricognizione.
Un notevole incremento è stato rilevato rispetto ai 1.300 indirizzi IP iniziali rilevati solo pochi giorni prima. Secondo il monitoraggio di GreyNoise Intelligence, questo rappresenta l’attività di scansione più intensa degli ultimi 90 giorni.
Il 3 ottobre 2025, un’impennata significativa dell’attività di scansione, pari al 500%, ha contrassegnato l’inizio della campagna di ricognizione. In quel giorno, sono stati rilevati circa 1.300 indirizzi IP unici che stavano esplorando i portali di accesso di Palo Alto. Rispetto ai tre mesi precedenti, questo picco iniziale di attività ha costituito il più alto livello di scansioni registrate.
Nei 90 giorni che hanno preceduto tale evento, i volumi giornalieri di scansioni non avevano quasi mai raggiunto la soglia dei 200 IP.
L’analisi condotta da GreyNoise ha messo in luce che una quota preponderante degli indirizzi IP nocivi, ben il 91%, risulta essere ubicata negli Stati Uniti. Si rilevano inoltre altri nuclei concentrati di tali indirizzi rispettivamente nel Regno Unito, nei Paesi Bassi, in Canada e nella Russia.
Un sostanziale investimento infrastrutturale per tale operazione è evidenziato dal fatto che gli specialisti della sicurezza hanno individuato intorno al 12% delle subnet ASN11878 complessivamente dedicate alla scansione dei gate di accesso Palo. E’ probabile che gli artefici della minaccia stiano esaminando in modo sistematico ampi database di credenziali, visti i pattern di autenticazione falliti che fanno supporre l’utilizzo di operazioni automatizzate brute-force nei confronti dei portali GlobalProtect SSL VPN.
GreyNoise ha reso pubblico un dataset esaustivo che include nomi utente e password univoci ricavati dai tentativi di login a Palo monitorati, in modo da permettere ai team per la sicurezza di stimare l’eventuale esposizione delle credenziali. Dall’analisi tecnica emerge che il 93% degli indirizzi IP coinvolti è stato etichettato come sospetto, mentre un 7% è stato giudicato dannoso.
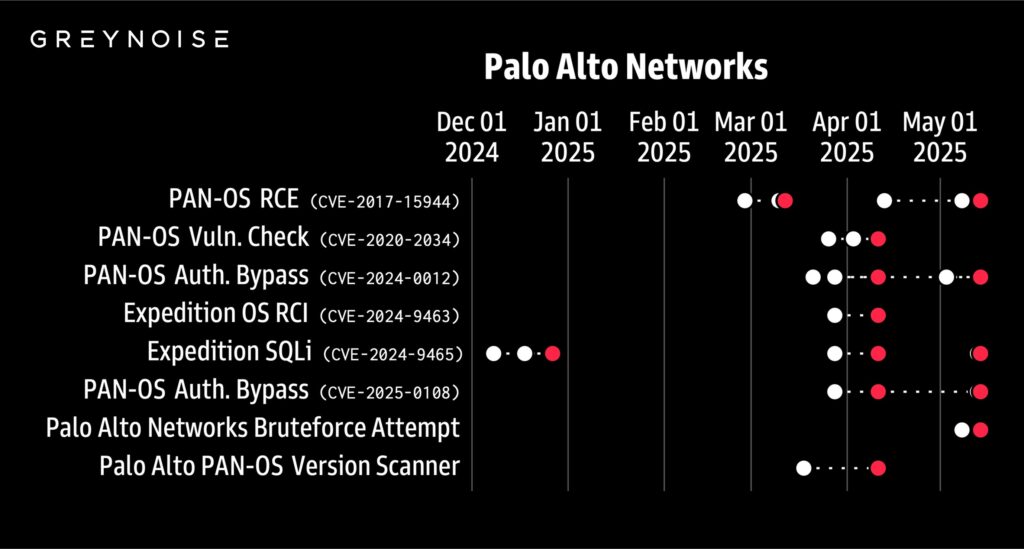
L’esame delle attività di scansione rivela la presenza di diversi pattern di aggregazione a livello regionale contraddistinti da impronte TCP uniche, il che fa supporre l’esistenza di vari gruppi di minacce organizzate che agiscono in concomitanza. Gli studiosi nel campo della sicurezza hanno rilevato possibili legami tra la serie di scansioni registrata a Palo Alto e le operazioni di esplorazione condotte simultaneamente contro dispositivi Cisco ASA.
Entrambe le campagne di attacco condividono impronte TCP dominanti legate all’infrastruttura nei Paesi Bassi, insieme a comportamenti di clustering regionale e caratteristiche degli strumenti simili. L’attacco multitecnologico suggerisce una campagna di ricognizione più ampia contro le soluzioni di accesso remoto aziendale.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…