
Ransomware gang data leak sites (DLSs) pose an increasingly widespread threat to businesses and individuals using the internet. These sites were created by cyber gangs to publish data stolen during a ransomware attack, when the data owner refuses to pay the ransom.
In this article, we will explore what ransomware is, how it works and what the consequences of data leak sites are for victims, how they are used by cyber gangs, what the protected section is, the automations, who develops them and their exposure.
Ransomware is a type of malware that represents an increasingly widespread threat to businesses and individuals. individuals using the Internet. This type of malware works by encrypting data on the victim’s computer or system, making it inaccessible. In exchange for data decryption, the malware owner demands a ransom from the compromised organization.
In recent years, a new form of ransomware extortion has emerged, known as “double” extortion. In this ransomware variant, cybercriminals not only encrypt the victim’s data, but also threaten to publish the stolen data on a public website unless the victim pays the demanded ransom.
In practice, double extortion increases the pressure on ransomware victims, since the publication of data can cause damage to reputation and privacy, as well as potential violations of the law and therefore sanctions. Furthermore, publishing stolen data on a public website can have long-term consequences, as sensitive information can remain online for years, exposing the victim to future risks.
Ransomware spreads through a variety of techniques, including phishing emails, infected file downloads, and system vulnerability exploits. Once the system is infected, ransomware encrypts the owner’s data and demands a ransom in exchange for decryption.
Data leak sites are websites created by cybercriminals with the purpose of hosting and publishing sensitive and confidential information stolen during a ransomware attack. These sites are often created to exploit “double” extortion: cybercriminals threaten to publish the stolen data on these websites unless the victim pays the demanded ransom.
Data leak sites can contain information on a wide range of entities, including individuals, companies, governments and non-governmental organizations. The stolen information can include personal data, such as names, addresses, phone numbers, and financial information, but also highly confidential information, such as trade secrets, intellectual property, and information about government activities.
Cybercriminals use data leak sites as a form of pressure on the ransomware victim, making the stolen information public and causing reputational damage to the affected individual or organization. Furthermore, publishing the information on the website can also lead to potential legal violations.
Data leak sites are generally hidden and not accessible via common search engines. Cybercriminals make them accessible only via direct links or via the dark web, a part of the internet not accessible via standard browsers. To access data leak sites, you need to use specialized tools such as Tor Browser.
Once the data leak site is created, cyber gangs use various techniques to maximize the stolen information and obtain the ransom payment.
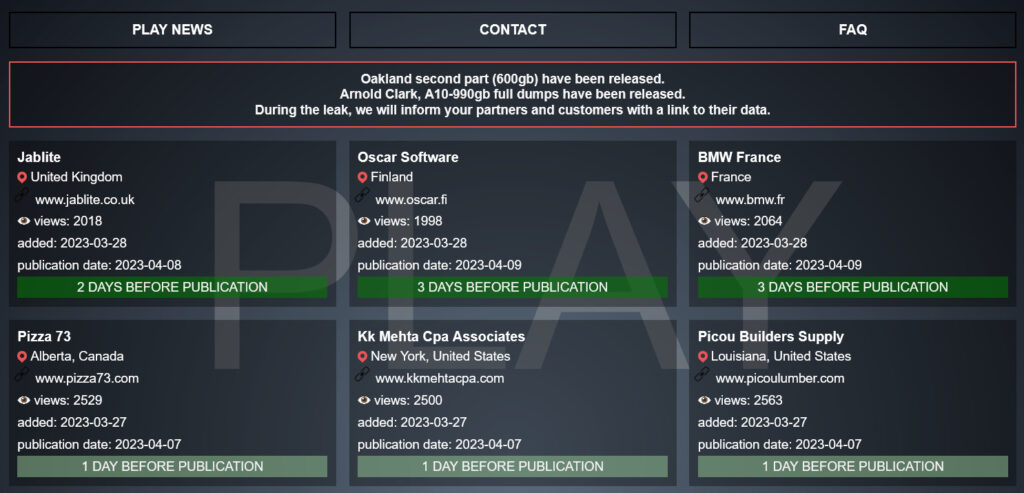
One of the most commonly used techniques is the countdown. Cybercriminals post a countdown on the website, indicating the time remaining before the stolen sensitive information is published. This technique creates a sense of urgency in the ransomware victim, forcing them to make a quick decision and pay the demanded ransom.
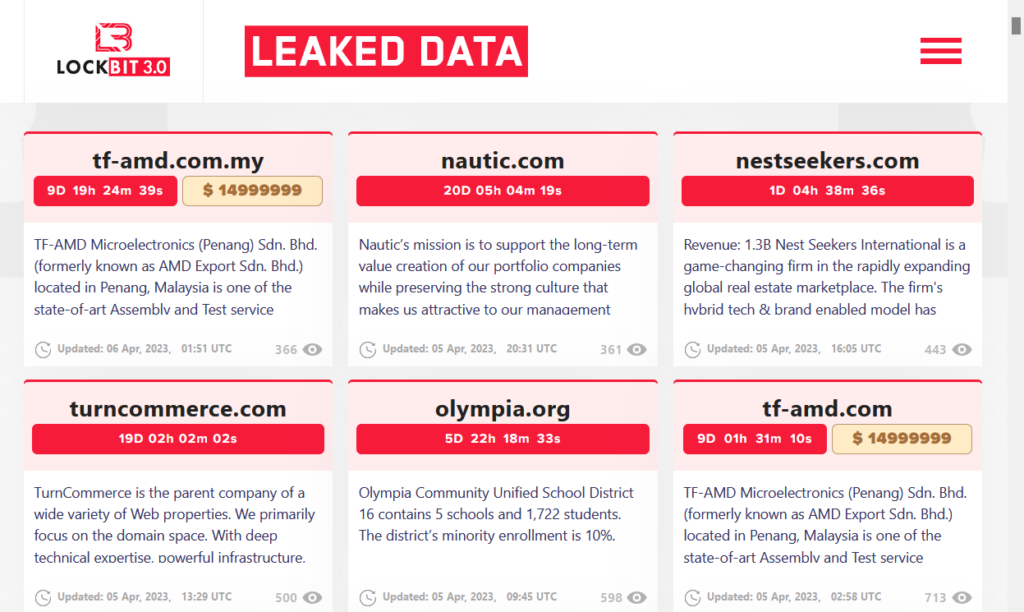
Another technique used A common practice used by cyber gangs is to publish samples of stolen information. Cybercriminals publish a small portion of the data exfiltrated from the company’s IT infrastructure, thus demonstrating the veracity of the attack and their ability to disclose the stolen sensitive information. This technique also serves to increase the pressure on ransomware victims, showing them that cybercriminals have indeed gained access to sensitive information and that the threat of data publication is worthy of attention.
Furthermore, some cyber gangs also organize private auctions for stolen information in the event of non-payment of the ransom. In these auctions, cybercriminals offer the stolen information to interested buyers, with the aim of monetizing their efforts. Very often, cyber gangs have been seen selling stolen sensitive information on underground forums in order to offer useful information to conduct phishing attacks and cyber fraud.
The data leak sites of ransomware cyber gangs are usually composed of two sections: the frontend section, which is viewed by website visitors, and the backend section, which is accessible only to the cyber criminals who manage the site.
The backend section is the reserved area where cyber criminals manage the stolen information and coordinate activities to obtain the requested ransom payment. In this section, cybercriminals also manage communications with the ransomware victim, offering the possibility of negotiating the ransom payment.
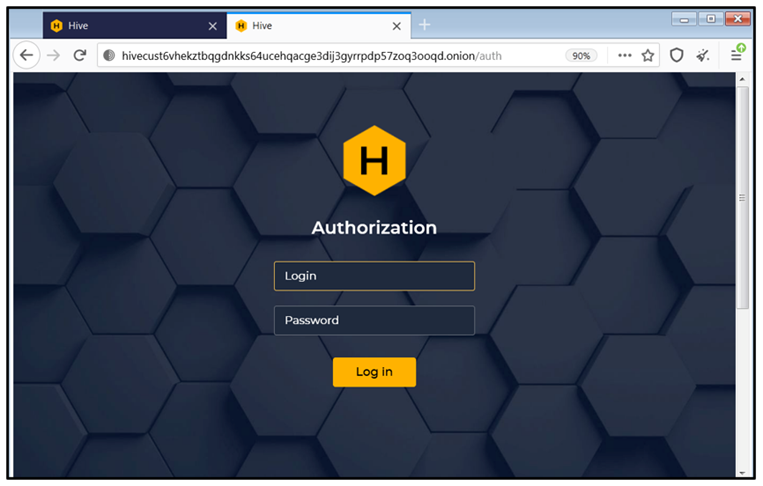
In fact, ransom notes left on computers often contain information about the victim’s identity. encrypted,a credential is present to access the backend of the data leak site and speak directly with the criminals to arrange the ransom payment.
In some cases, cybercriminals can use the backend of the data leak site to exchange messages with the ransomware victim and negotiate the ransom payment. In this way, cybercriminals try to convince the victim to pay the ransom by offering guarantees of data release or threatening to publish the stolen information.
However, it is important to remember that negotiating with cybercriminals is not always advisable, as there is no guarantee that the data will actually be released after the ransom is paid.
Furthermore, access to the backend of the data leak site is crucial for the activities of ransomware cyber gangs, as it allows them to manage the stolen information, control communications with the ransomware victim, and plan the publication of the stolen information in case of failure to pay the ransom.
Ransomware cyber gangs often operate with a hierarchical organizational structure and a vast network of affiliates, who are individuals or groups who collaborate with criminals to carry out cybercriminal activities. Affiliates can be involved in several phases of the ransomware attack, including scouting for potential victims, distributing the malware, and exfiltrating stolen data.
Data exfiltration from victims’ IT infrastructures occurs through various mechanisms, including the use of advanced hacking tools, manipulation of backup systems, or direct attacks on servers containing sensitive information. Once the data has been exfiltrated, it is transferred to the data leak sites managed by the cyber gang.
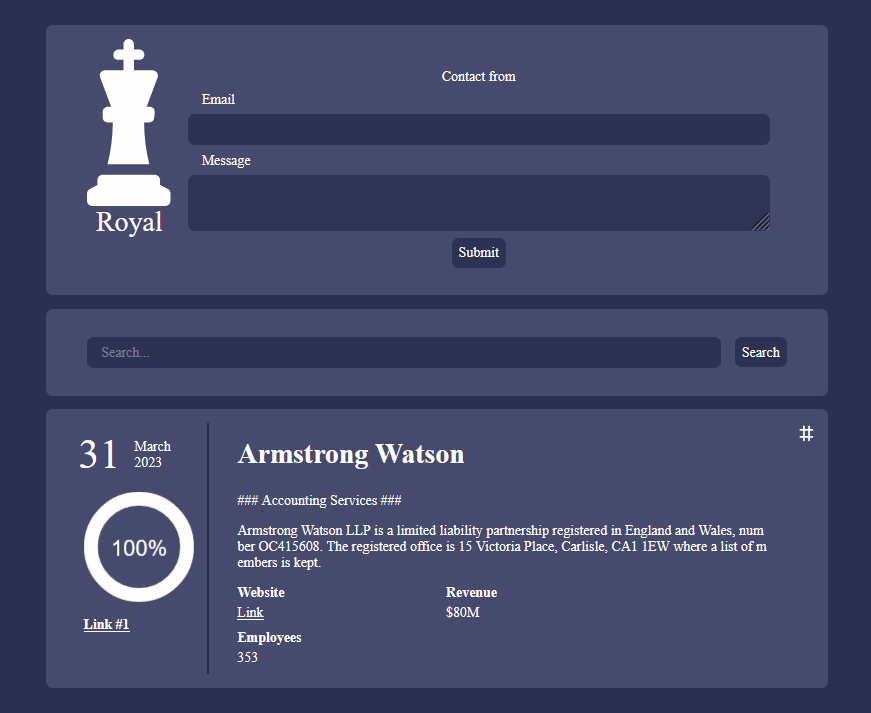
To simplify the process of managing data leak sites, ransomware cyber gangs often use automations that allow affiliates to upload stolen data directly to the website. These automations are usually integrated into the backend section of data leak sites, allowing affiliates to upload files quickly and securely.
In this way, ransomware cyber gangs are able to handle large amounts of stolen data efficiently and automatically. However, publishing stolen information on data leak sites poses a serious risk to the privacy and security of victims, who can suffer serious personal and business consequences.
The world of cybercrime is characterized by a great diversity of specializations, and not all criminals have the skills to carry out all aspects of their attack. In this context, the creation of a data leak site can be entrusted to specialized figures in the sector.
In fact, the developers of the malware that allowed the attack and the subsequent data exfiltration are not always the same ones who create the data leak site infrastructure. Sometimes, ransomware authors commission the site from other criminals, who specialize in creating these tools.
Creating a data leak site requires specific skills in various areas, such as designing web servers, implementing databases to manage stolen data, and creating intuitive web interfaces for users who want to purchase the data.
Furthermore, the site must be able to withstand possible DDoS attacks and must guarantee anonymity to the criminals who use it to sell the exfiltrated data. All of this requires advanced knowledge of cybersecurity and encryption technologies.
In conclusion, data leak sites are often developed by specialized cybercriminals, who work closely with malware authors to ensure the success of the entire criminal operation. The great variety of skills required for the creation of a data leak site means that this activity can only be performed by a few experts capable of managing all phases of creating such an infrastructure.

Data leak sites are usually exposed on the so-called onion network, a part of the Internet accessible only via the Tor browser. This choice is due to the need to guarantee the anonymity of the site’s authors and their customers, who can thus purchase the exfiltrated data discreetly and protected from possible attacks by law enforcement.
However, data leak sites are not always exclusively accessible via the onion network. Sometimes, in fact, the site’s authors also create a domain on the clearweb, the part of the Internet accessible via common browsers like Chrome or Firefox. This often happens when the site needs to be made more accessible and advertised to attract more buyers.
The exposure of a data leak site can pose significant risks to the site’s authors, who risk being detected by law enforcement or cybersecurity experts. In fact, data leak sites are often identified thanks to the domain and server analysis techniques used by cybersecurity researchers.
Furthermore, the exposure of a data leak site can also lead to the risk of being attacked by other cybercriminals, who may attempt to steal the data contained on the site or take control of it for illicit purposes.
In conclusion, data leak sites represent an increasingly widespread threat to companies and ordinary users. Organized cybercrime uses these platforms to extort money from the victims of their attacks, exploiting double extortion to jeopardize the privacy and reputation of companies.
The complexity of these attacks demonstrates the need to invest in a solid cybersecurity strategy, which includes user training, the adoption of advanced defense technologies, and active risk management. Furthermore, it is essential that authorities and international organizations unite to combat this phenomenon, through international cooperation and the exchange of information.
Finally, it is important to underline that cybercrime is made up of a multitude of specialized actors, who work together to obtain maximum profit. Malware developers, affiliates, data leak site creators, and other cybercriminals collaborate with each other, often without ever meeting in person, to carry out their attacks.
This complexity requires an equally complex response, based on cooperation between law enforcement, companies, and international organizations.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
