
Gli Advanced Persistent Threat (APT) sono attori malevoli che operano nell’ombra della rete, conducendo attacchi altamente sofisticati e mirati. Questi gruppi, spesso associati a stati-nazione, rappresentano una minaccia significativa per la sicurezza informatica a livello globale.
Questo articolo si propone di gettare luce sul complesso mondo delle minacce APT, analizzando in dettaglio chi sono, cosa li spinge e come operano. Attraverso diversi capitoli, esploreremo le fondamenta degli APT, passando dalle motivazioni che li guidano alla comprensione delle loro tattiche avanzate e al modo in cui le organizzazioni possono difendersi da queste minacce pervasive. Il nostro viaggio ci porterà dall’identificazione degli APT fino alle implicazioni legali e diplomatiche legate a questa categoria di attacchi cibernetici sofisticati.
Nel prossimo capitolo esamineremo l’essenza degli APT, definendo chi sono e cosa li rende una minaccia così formidabile. Attraverso questa panoramica iniziale, gettiamo le basi per una comprensione più approfondita di questo mondo in continua evoluzione.
Gli Advanced Persistent Threat (abbreviati in APT) costituiscono una delle forme più insidiose di minacce cibernetiche nel panorama della sicurezza informatica. Questi attori malevoli, noti per la loro capacità di operare in modo silente, persistente e mirato, rappresentano una seria preoccupazione per organizzazioni di tutto il mondo.
Per comprendere meglio chi sono gli APT e quale sia la loro rilevanza, è essenziale iniziare con una solida introduzione a questa temibile categoria di minacce.
Gli Advanced Persistent Threat, traducibile in italiano come “Minaccia Persistente Avanzata”, sono gruppi di hacker altamente sofisticati, spesso associati a entità statali o gruppi criminali altamente organizzati. La caratteristica distintiva degli APT è la loro capacità di operare in modo persistente all’interno delle reti informatiche, con l’obiettivo di ottenere accesso non autorizzato, raccogliere informazioni sensibili o condurre attacchi mirati. La “persistenza” si riferisce al fatto che gli APT lavorano a lungo termine, spesso rimanendo all’interno di una rete per periodi prolungati, sfuggendo così alla rilevazione.
Per comprendere appieno la minaccia rappresentata dagli APT, è fondamentale conoscere alcune delle loro caratteristiche chiave:
La storia degli APT risale agli anni ’90, ma è negli ultimi due decenni che hanno iniziato a destare preoccupazioni significative. Alcuni degli attacchi APT più noti includono Stuxnet, un malware che colpì le centrifughe di arricchimento dell’uranio, all’interno della centrale nucleare iraniana di Natanz e NotPetya, un attacco che ha causato danni su vasta scala a livello globale.

Gli Advanced Persistent Threat (APT) sono noti per la loro mira precisa e i loro obiettivi ben definiti. La comprensione delle motivazioni dietro gli attacchi APT è fondamentale per riconoscere la portata delle minacce che rappresentano e per sviluppare strategie di difesa efficaci. In questo capitolo, esploreremo gli obiettivi comuni degli attacchi APT e le motivazioni che li guidano.
Gli APT selezionano obiettivi specifici che spaziano dalle organizzazioni governative alle aziende private di settori chiave. Ecco alcuni degli obiettivi più comuni degli attacchi APT:

Le motivazioni che guidano gli APT variano a seconda degli attori coinvolti. Alcune delle motivazioni più comuni includono:
La comprensione delle motivazioni dietro gli attacchi APT è cruciale per sviluppare strategie di difesa adeguate. Nel capitolo successivo, esamineremo le interconnessioni tra Stati nazione e gruppi di criminalità informatica.
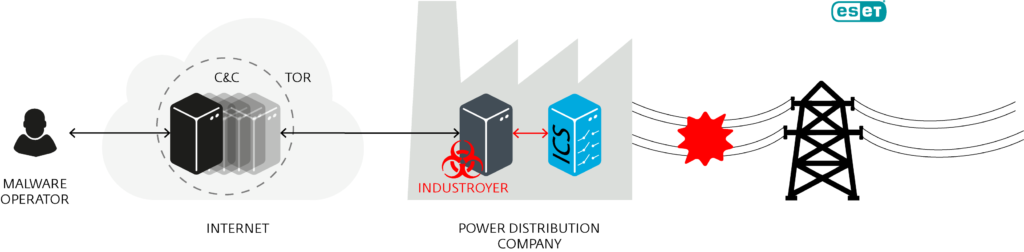
La comprensione delle dinamiche tra stati-nazione e gruppi di criminali informatici è essenziale per valutare la portata e la complessità degli Advanced Persistent Threat (APT). In questo capitolo, esamineremo le differenze fondamentali tra queste due categorie di attori e come interagiscono nel mondo della cibersicurezza.
Gli stati-nazione rappresentano uno dei principali attori dietro gli APT. Questi attacchi sono spesso condotti o sponsorizzati da governi e agenzie governative. Ecco alcune delle caratteristiche chiave degli stati-nazione come attori di APT:
I gruppi di criminali informatici, al contrario, sono spesso mossi da motivazioni di lucro. Questi gruppi cercano di ottenere guadagni finanziari attraverso attività illegali online. Alcune delle loro caratteristiche includono:
È importante notare che, in alcuni casi, gli stati-nazione possono sfruttare o collaborare con gruppi di criminali informatici per raggiungere i propri obiettivi. Questo rende il panorama della cibersicurezza ancora più complesso, poiché le linee tra attori statali e criminali possono sfumare.
La comprensione delle dinamiche tra stati-nazione e gruppi di criminali informatici è cruciale per sviluppare strategie di difesa efficaci contro gli APT. Nel prossimo capitolo, esamineremo i gruppi APT più noti.

Gli Advanced Persistent Threat (APT) sono spesso associati a gruppi specifici che si distinguono per le loro tecniche tattiche e procedure (TTP), le risorse e la persistenza nelle loro operazioni. In questo capitolo, esamineremo alcuni dei gruppi APT più noti e i loro notevoli attacchi nel corso degli anni.
Questi sono solo alcuni degli APT noti nel panorama della sicurezza informatica. Gli attacchi condotti da questi gruppi hanno avuto un impatto significativo su organizzazioni governative, aziende e individui in tutto il mondo e come avete modo di vedere, tutti gli stati altamente industrializzati hanno delle fazioni interconnesse. Nel capitolo successivo, esamineremo le fasi di attacco di un Advanced Persistent Threat.
Gli Advanced Persistent Threat (APT) sono noti per la loro capacità di condurre attacchi sofisticati che si sviluppano attraverso diverse fasi, ognuna delle quali contribuisce al successo dell’operazione APT. In questo capitolo, esamineremo le fasi chiave di un attacco APT: l’infiltrazione, l’espansione e la persistenza.
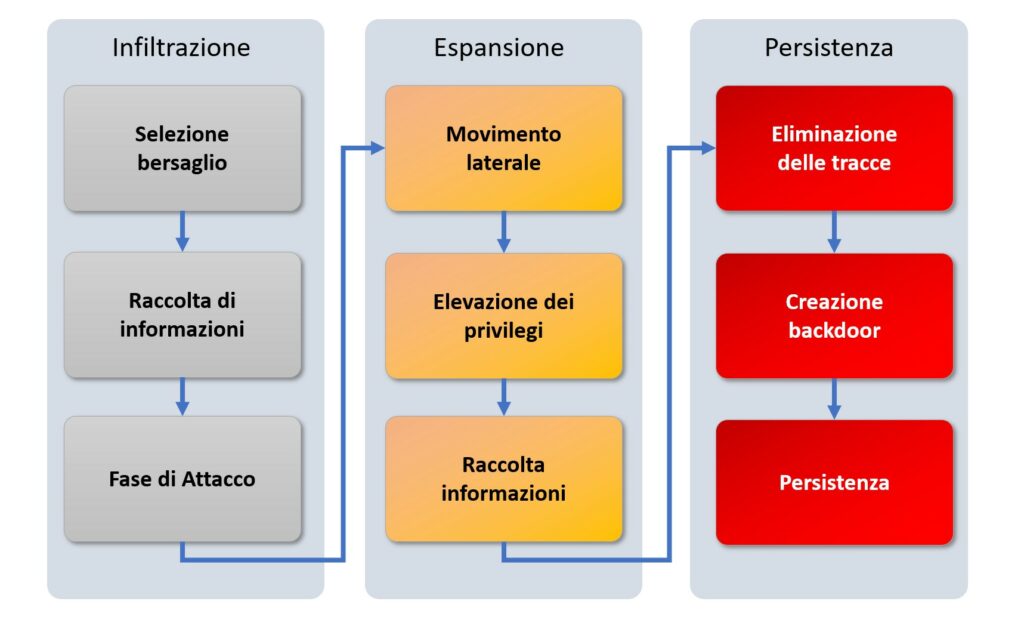
La fase di infiltrazione rappresenta l’inizio dell’attacco APT, in cui gli aggressori cercano di ottenere accesso non autorizzato a una rete o a un sistema obiettivo. Questa fase include:
Una volta all’interno della rete obiettivo, gli aggressori passano alla fase di espansione. Durante questa fase, cercano di ottenere un maggiore controllo e accesso alla rete per raggiungere i loro obiettivi. Questa fase include:
La fase di persistenza è la fase finale in cui gli aggressori cercano di mantenere l’accesso e il controllo sulla rete a lungo termine. Questo è ciò che rende gli APT “persistenti”. Questa fase include:
Comprendere queste fasi di un attacco APT è cruciale per sviluppare strategie di difesa efficaci. Nel prossimo capitolo, esamineremo le migliori pratiche di difesa contro gli APT e come le organizzazioni possono proteggersi da queste minacce sofisticate.

Gli Advanced Persistent Threat (APT) rappresentano una minaccia grave e costante per la sicurezza informatica. Per proteggersi da queste minacce altamente sofisticate, le organizzazioni devono adottare un’ampia gamma di metodi di difesa. In questo capitolo, esamineremo alcuni dei principali metodi di difesa contro gli APT e valuteremo l’efficacia degli strumenti di rilevamento e risposta degli endpoint (EDR) in questa lotta.
Gli strumenti di rilevamento e risposta degli endpoint (EDR) svolgono un ruolo cruciale nella protezione contro gli APT. Questi strumenti sono progettati per monitorare e proteggere i dispositivi endpoint all’interno di una rete, come computer e dispositivi mobili. Ecco come gli EDR contribuiscono alla difesa contro gli APT:
Per proteggersi da APT, le organizzazioni devono adottare una strategia di sicurezza multistrato che includa:
L’educazione degli utenti è un aspetto critico della difesa contro gli APT. Gli utenti devono essere formati per riconoscere segnali di potenziali minacce, come e-mail di phishing o collegamenti sospetti. La consapevolezza degli utenti è un elemento chiave nella prevenzione di attacchi.
Il monitoraggio continuo delle reti e degli endpoint è essenziale. L’analisi dei dati in tempo reale e la rilevazione delle minacce consentono di intervenire prontamente contro gli attacchi APT prima che causino danni gravi.
Limitare l’accesso alle risorse solo agli utenti autorizzati e basato sul ruolo riduce le opportunità per gli aggressori di muoversi lateralmente all’interno della rete.
In sintesi, gli strumenti EDR giocano un ruolo cruciale nella difesa contro gli APT, ma devono essere parte di una strategia di sicurezza complessa che comprenda diverse misure preventive e reattive. Il monitoraggio costante, l’educazione degli utenti e la risposta rapida sono fondamentali per ridurre al minimo il rischio di successo di un attacco APT.

Gli Advanced Persistent Threat (APT) rappresentano una minaccia che va ben oltre il mondo della tecnologia e della sicurezza informatica. Le operazioni APT possono avere gravi implicazioni legali e diplomatiche, in quanto spesso coinvolgono stati-nazione, organizzazioni governative o entità internazionali. In questo capitolo, esamineremo le complesse implicazioni legali e diplomatiche degli APT.
Uno dei principali ostacoli legali nella gestione degli APT è l’attribuzione, ovvero la capacità di identificare con certezza gli autori di un attacco APT. Gli aggressori APT spesso cercano di nascondere la loro identità attraverso tecniche di occultamento avanzate. Questo può rendere difficile stabilire la responsabilità di un attacco.
Quando gli APT sono attribuiti a uno stato-nazione o a una specifica entità, le vittime possono cercare di intraprendere azioni legali contro i responsabili. Queste azioni possono includere denunce a livello nazionale o denunce presso organizzazioni internazionali anche se spesso l’accusato riporta sempre la non veridicità delle affermazioni.
Anche se non esiste ancora un trattato internazionale vincolante, esistono delle convenzioni internazionali (come il Manuale di Tallinn 2.0 o la Convenzione di Budapest sulla criminalità informatica) che regolano il comportamento degli stati-nazione in materia di cyber-attacchi. Ad esempio, il diritto internazionale stabilisce che gli stati dovrebbero astenersi dal condurre attacchi che danneggiano infrastrutture critiche di altri stati o interferiscono con le loro operazioni politiche.
Nel contesto degli APT, ci sono norme di condotta internazionali che delineano comportamenti accettabili e inaccettabili nello spazio cibernetico, anche se non c’è nulla di condiviso unilateralmente. Queste norme sono ancora in evoluzione e sono oggetto di discussioni diplomatiche, anche se sono stati fatti degli sforzi verso una regolamentazione del cyberspazio.
Le vittime di attacchi APT possono cercare di prendere misure di difesa attiva, ad esempio attraverso la ricerca di vulnerabilità nel sistema dell’attaccante o la neutralizzazione delle minacce. Queste azioni possono innescare ritorsioni e complicare ulteriormente le implicazioni diplomatiche.
Le azioni di rappresaglia possono sfociare in un ciclo di escalation, con rappresaglie da parte dell’aggressore e ulteriori misure di difesa attiva. Questo può avere gravi conseguenze diplomatiche.
Le vittime di attacchi APT possono intraprendere azioni diplomatiche, come denunciare l’attacco alle autorità competenti o cercare di risolvere la questione attraverso trattative bilaterali o multilaterali.
La diplomazia è spesso la via preferita per affrontare le implicazioni degli attacchi APT, in quanto mira a risolvere le controversie in modo pacifico e negoziato.
Ricordiamo però sempre che Il quinto dominio dopo terra, mare, cielo e spazio, è l’estensione di quest’ultimo, noto a tutti come cyberspace, è stato dichiarato nel 2016 dalla NATO come “Operational Domain”. Si tratta quindi di un motivo di una possibile richiamo alla clausola di difesa collettiva presente nell’articolo 5. Tale articolo afferma che un “attacco armato” contro uno o più alleati si considera come un attacco contro ogni componente della Nato e quindi ognuno di essi può, secondo il diritto all’autodifesa sancito dall’articolo 51 della carta dell’Onu, decidere le azioni che ritiene necessarie a “ristabilire e mantenere la sicurezza”, compreso “l’uso delle forze armate”.
Gli APT possono minare le relazioni internazionali tra gli stati, causando tensioni e sfiducia reciproca. Gli attacchi APT possono portare a una crescente sospetto tra gli stati e complicare le relazioni diplomatiche. Le implicazioni delle operazioni APT possono avere ripercussioni a lungo termine sulle relazioni tra gli stati e le organizzazioni internazionali.
In sintesi, gli APT non sono solo una minaccia tecnologica, ma anche una questione complessa con implicazioni legali e diplomatiche. La gestione degli APT richiede una combinazione di misure di sicurezza informatica, cooperazione internazionale e diplomazia per affrontare le sfide che queste minacce rappresentano.

Gli Advanced Persistent Threat (APT) sono una minaccia in continua evoluzione e, di conseguenza, le tendenze nei loro attacchi sono in costante mutamento. Per affrontare questa sfida in continua evoluzione, è importante riconoscere le tendenze emergenti nei cyber-attacchi APT. In questo capitolo, esamineremo alcune delle tendenze più rilevanti e all’avanguardia in questo campo.
Gli aggressori APT stanno sfruttando sempre più l’intelligenza artificiale (AI) e il machine learning (ML) per rendere i loro attacchi più sofisticati e difficili da rilevare. L’IA può essere utilizzata per automatizzare il processo di infiltrazione, scoprire nuove vulnerabilità e adattarsi alle contromisure di sicurezza.
L’Internet delle Cose è diventato un bersaglio sempre più allettante per gli APT. Dispositivi IoT spesso meno sicuri, come telecamere di sorveglianza e dispositivi di rete, possono essere compromessi e utilizzati come punti di accesso per le reti aziendali.
Gli APT stanno combinando più tecniche di attacco in una serie di azioni coordinate, creando così attacchi a catena più complessi. Questi attacchi possono iniziare con una campagna di phishing, passare a un exploit di una vulnerabilità e culminare con l’infiltrazione e il furto di dati.
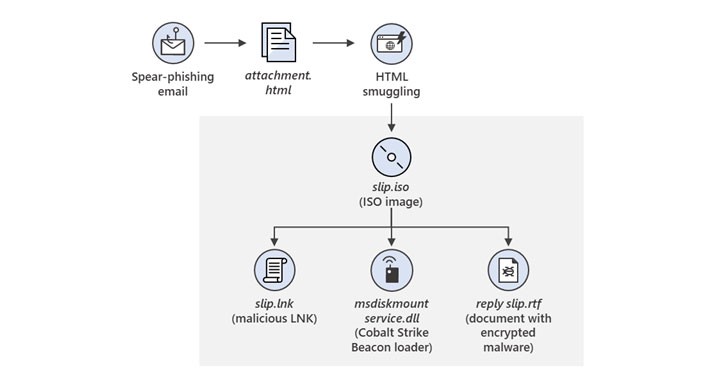
L’ingegneria sociale continua a essere un vettore di attacco efficace per gli APT. Gli aggressori si affidano sempre più a messaggi di phishing sofisticati e inganni mirati per indurre gli utenti a rivelare informazioni sensibili o fare clic su link dannosi.
Gli APT stanno sviluppando malware sempre più evasivi, in grado di evitare la rilevazione da parte dei software antivirus tradizionali. Questo può comportare l’uso di tecniche di evasione, come la firma dinamica, per rimanere nascosti.
Gli APT continuano a sfruttare le vulnerabilità Zero-Day, ovvero vulnerabilità software precedentemente sconosciute, per condurre attacchi. Questi attacchi sono particolarmente difficili da difendere poiché non esistono patch o contromisure conosciute.
Gli APT continuano a concentrarsi su settori chiave, come quelli legati all’energia, alla difesa e alla sanità. Questi settori sono spesso obiettivi appetibili a causa delle informazioni sensibili che contengono.
Nella nostra esplorazione delle Advanced Persistent Threat (APT), emergono alcune conclusioni chiave che sottolineano l’importanza di affrontare queste minacce con grande attenzione e consapevolezza.
Gli APT sono chiamate “persistenti” per una ragione. La loro determinazione a raggiungere i loro obiettivi è notevole, e possono continuare a operare all’interno di una rete per lunghi periodi senza essere scoperti. Possono provenire da diverse fonti, compresi stati-nazione, gruppi criminali informatici e attori con motivazioni ideologiche. Questa diversità di attori rende gli APT una minaccia ancora più complessa da affrontare.
Questi aggressori utilizzano tecniche avanzate, tra cui il phishing mirato, l’ingegneria sociale, il malware evasivo e l’uso di vulnerabilità Zero-Day. Queste tattiche richiedono misure di sicurezza altamente sofisticate per essere rilevate ed affrontate con immediatezza. Inoltre, vanno oltre il mondo della tecnologia e della sicurezza informatica, avendo implicazioni legali e diplomatiche significative. L’attribuzione degli attacchi e le risposte a livello internazionale sono sfide complesse.
In conclusione, affrontare le minacce APT richiede una combinazione di tecnologia avanzata, strategie di sicurezza multistrato, educazione degli utenti, cooperazione internazionale e alte skill tecniche. Rimanere vigili e pronti ad affrontare le sfide in continua evoluzione delle APT è essenziale per proteggere le organizzazioni. Pertanto Collaborazione e Condivisione rappresentano come al solito il modello vincente anche per questa sfida altamente tecnologica del mondo di oggi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…