
Il “phishing as a service” (PaaS) è un tipo di servizio offerto da cyber criminali o fornitori di servizi illeciti che semplifica e automatizza l’intero processo di creazione e distribuzione di attacchi di phishing e quindi di campagne malevole.
Funziona in modo simile a molti altri servizi basati su abbonamento o modelli di affiliazione, rendendo più facile per gli attaccanti eseguire campagne di phishing senza la necessità di conoscenze tecniche approfondite.
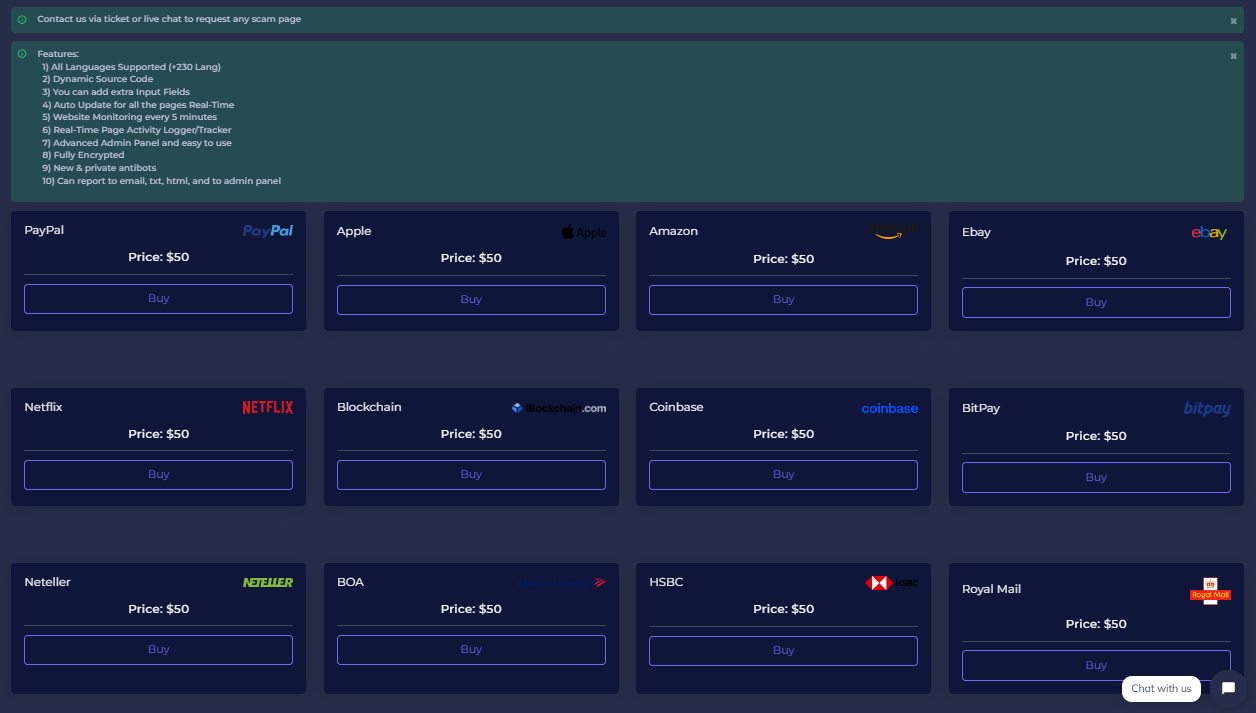
Ecco come funziona il phishing as a service:
Oltre ai modelli di PaaS che abbiamo visto, sono presenti molti criminali informatici che offrono servizi per la realizzazione di siti fake altamente simili ai siti originali. Tali servizi vengono pubblicati nei forum underground come riportato nel post di seguito.
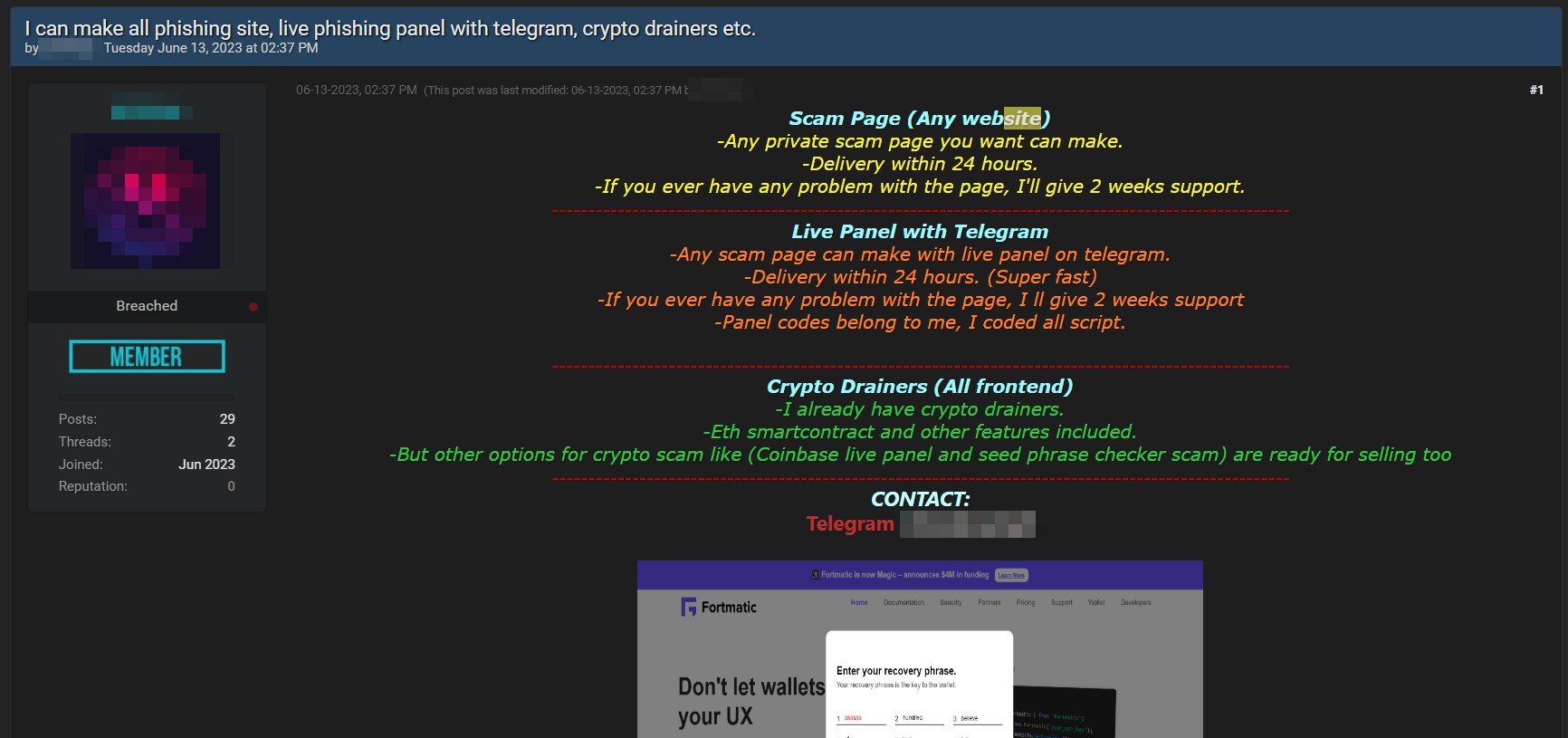
Il phishing as a service rende più accessibili gli attacchi di phishing, poiché non richiede una conoscenza tecnica avanzata da parte degli attaccanti.
Questi servizi rappresentano una minaccia significativa per individui e organizzazioni, e la difesa contro di essi richiede una grande sensibilizzazione, l’istruzione degli utenti e l’utilizzo di soluzioni di sicurezza informatica avanzate per rilevare e mitigare gli attacchi di phishing.
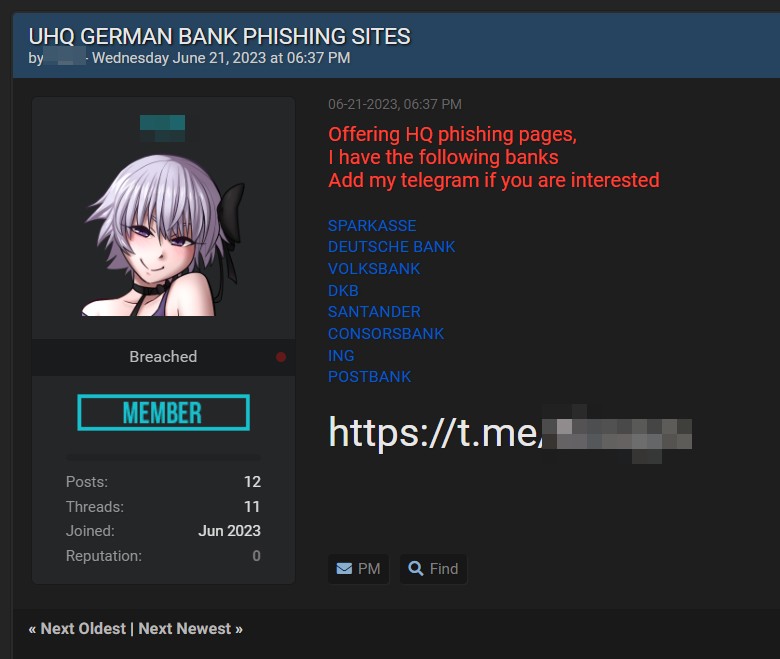
L’acronimo “Phishing as a Service” (PaaS) è stato adottato in modo simile a “Software as a Service” (SaaS) e altri servizi basati su cloud sono abbreviati per comodità. Tuttavia, è importante notare che il termine “PaaS” può anche essere associato a “Platform as a Service” in un contesto di cloud computing.
Pertanto, quando si utilizza l’acronimo “PaaS” per riferirsi a “Phishing as a Service”, è consigliabile specificare chiaramente il contesto per evitare confusioni.
L’importanza della consapevolezza del rischio relativo agli attacchi di phishing è fondamentale nella difesa contro questa minaccia sempre crescente. La diffusione degli attacchi di phishing è in costante aumento, rappresentando una delle principali minacce alla sicurezza informatica. Ecco alcune informazioni chiave sull’importanza di essere consapevoli dei rischi legati al phishing:
Le e-mail rimangono uno dei vettori più comuni per gli attacchi di phishing. Si stima che oltre il 90% degli attacchi di malware inizia con un’e-mail di phishing. La consapevolezza dell’utente è fondamentale per prevenire gli attacchi di phishing. Formare gli utenti aziendali a riconoscere e segnalare e-mail sospette può ridurre significativamente il rischio.
Pertanto la formazione sulla sicurezza informatica dovrebbe essere un processo continuo. Gli attaccanti si evolvono costantemente, creando e-mail e siti web di phishing sempre più convincenti. Mantenere gli utenti informati sulle ultime minacce e tattiche di phishing è essenziale per una difesa efficace.
Sia le aziende che gli utenti devono essere consapevoli dei rischi associati agli attacchi di phishing e adottare misure per proteggersi da questa minaccia sempre crescente. La prevenzione è spesso la difesa più efficace contro gli attacchi di phishing, e la consapevolezza del rischio è la chiave per una prevenzione di successo.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…