
Con l’aumentare degli attacchi ransomware – spesso avviati attraverso e-mail di phishing – è davvero importante, cruciale, agire in modo proattivo per proteggere se stessi nonché la sicurezza dell’organizzazione in cui si lavora.
Certamente, avere a disposizione computers e servers che siano aggiornati per quanto riguarda patch di sistema e di sicurezza, antivirus ed altri endpoint tools aiuta molto nel ridurre il rischio di insieme d’infezione, ma l’essere preparati al sapere riconoscere le e-mail di phishing ed anche educare gli impiegati della propria organizzazione a comportarsi in modo proattivo è un nodo cruciale.
Per capire come ragiona un attore malevolo che ci minaccia con e-mail di phishing, si può vedere l’interessante video di Veronica Patron per Red Hot Cyber su Psicologia e Social engineering:
Per una introduzione generale invece a cosa sia il phishing ed ai tipi di questo vettore di attacco, rimando all’articolo di Massimiliano Brolli: https://www.redhotcyber.com/post/il-phishing-cosa-%C3%A8
Per mantenere le cose semplice, elencherò dodici regole d’oro non troppo tecniche:
Molti moderni client di posta o provider di web email (come GMail, Microsoft e molti altri) POTREBBERO NON MOSTRARE / NON INDICARE l’indirizzo effettivo del mittente della email ma un nome alternativo. Per questo motive potreste vedere un nome o una scritta che vi ricorda un indirizzo noto/affidabile, ma l’indirizzo sottostante/nascosto è diverso.
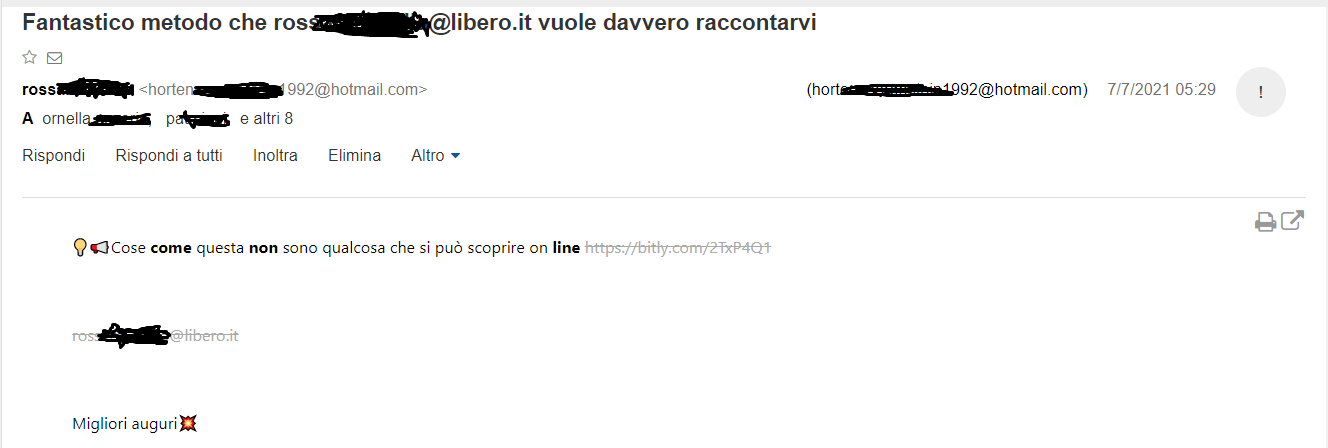
Figura 1
In figura 1 potete vedere una fake email inviata da ros…..…@libero.it, ma in realtà inviata da un vero indirizzo email “nascosto” horten……[email protected] (la figura mostra come ad oggi appare il web mail client del sito www.libero.it e come siano mostrate le informazioni all’utente finale).
Sfortunatamente, I protocolli usati per la posta elettronica sono vecchi (email standard, protocollo SMTP) e basati su standards che non garantiscono la affidabilità/trustability del mittente.I lettori interessati al dettaglio possono leggere RFC 5321https://datatracker.ietf.org/doc/html/rfc5321 paragraph 7.1 Mail Security and Spoofing
SMTP mail is inherently insecure in that it is feasible for even
fairly casual users to negotiate directly with receiving and relaying
SMTP servers and create messages that will trick a naive recipient
into believing that they came from somewhere else.
Quindi l’indirizzo sottostante potrebbe essere un indirizzo noto/valido, ma usato da terzi malintenzionati, poiché come indicato in RFC 5231 p. 7.1 il protocollo non verifica che un “mittente” sia in effetti “chi dice di essere”.
Passate il mouse su tutte le parti dell’e-mail senza fare clic: se il testo che appare sopra elementi cliccabili/links sembra strano o non corrisponde a ciò che è indicato nel testo associato al collegamento, NON fate clic e segnalate l’evento al dipartimento IT/Security. Si veda figura 2.
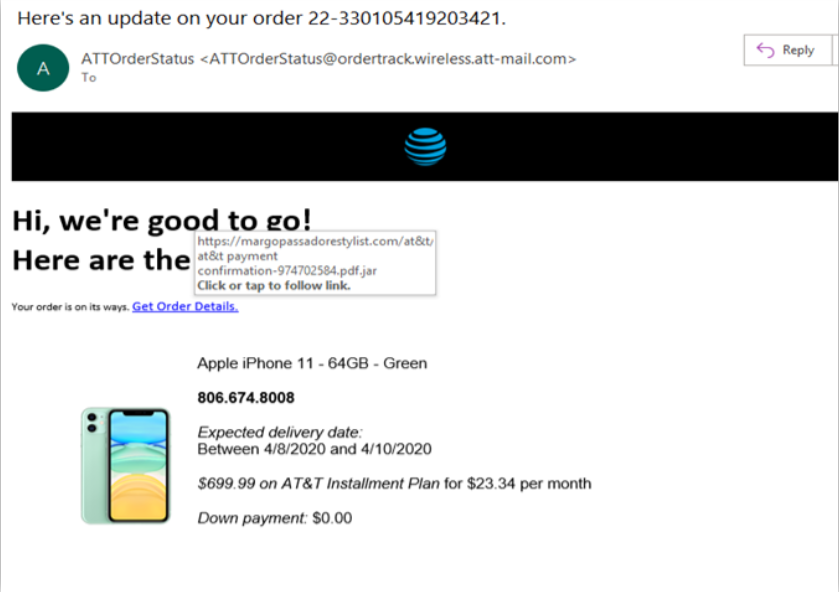
Figura 2
Gli attaccanti spesso si preoccupano poco di errata ortografica ed errori grammaticali. Questo elemento può far distinguere un attore malevolo da un mittente legittimo. Si veda figura 3.

Figura 3
We’re have been hold your account …”: la frase non è corretta in lingua inglese. Come in figura 2 anche in figura 3 il link associato al testo rosso in basso è un segno di e-mail malevola.
Gli hacker malevoli spesso si affrettano a creare siti di phishing e a preparare e-mail truffa, quindi alcuni di questi siti/e-mail possono avere un aspetto significativamente (ma purtroppo a volte anche leggermente) diverso da quello in uso nelle aziende originali “simulate”. Questi elementi, come anche lievi differenze nei loghi/marchi/icone, possono essere utilizzati per poter distinguere un’e-mail dannosa da una legittima nella propria casella di posta.
Avete ricevuto una e-mail con un incipit vago/generale, tipo “Caro cliente” o “Pregiato cliente”?
Di solito le aziende che vi conoscono, con cui avete rapporti, vi chiameranno per nome.
Si veda figura 3a. Come in figura 2 e figura 3, anche in figure 3a il link che appare al passaggio del mouse è un chiaro segno di e-mail truffa.
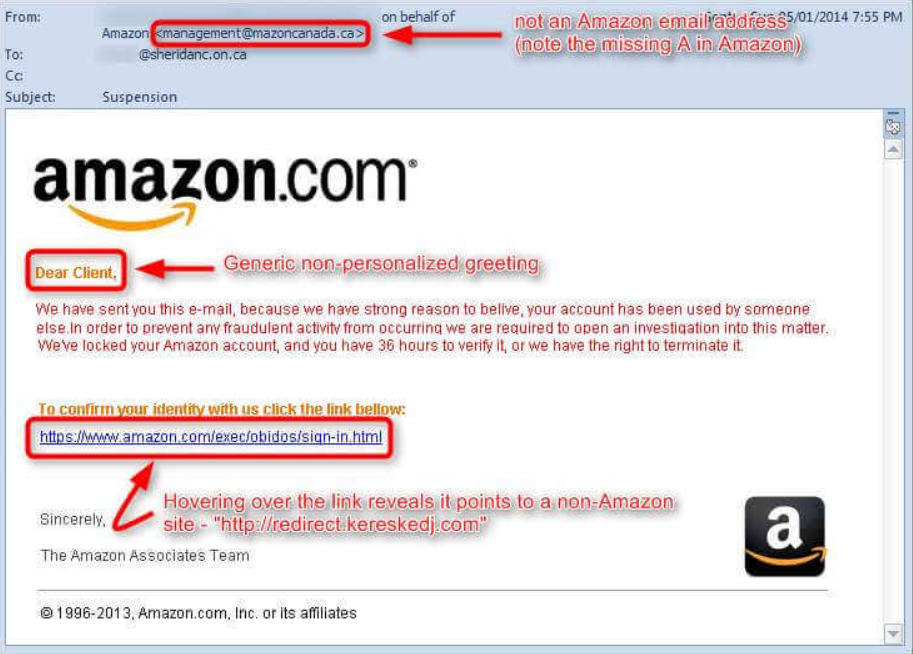
Figura 3a
Le società legittime a cui sei collegato, non ti chiedono MAI o è improbabile che ti chiedano informazioni personali via e-mail o telefonata (ricordate il Vishing ed i libri di Kevin Mitnick sull’ingegneria sociale). Si veda figura 4.
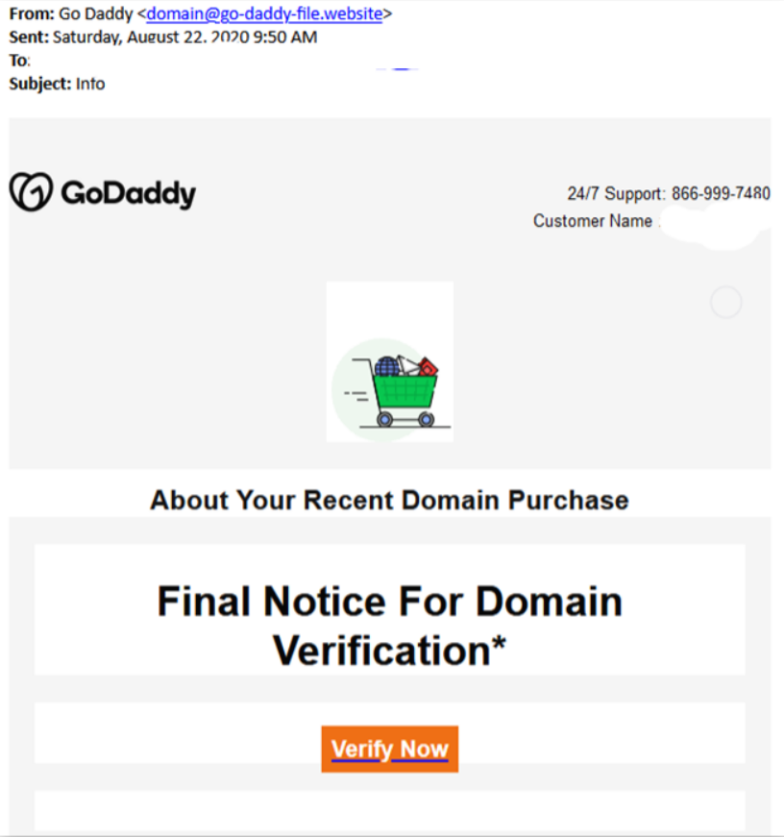
Figura 4
Queste e-mail dannose potrebbero tentare di farti pensare a qualcosa di veramente urgente da fare: inviare del denaro (anche pochi soldi) per reclamare una grossa ricompensa o vincita oppure, come in attacchi BEC/whaling/CEO Fraud, fingere di essere un manager della tua organizzazione affermando che il tuo Chief Finantial Officer ha bisogno di un bonifico urgente di una grande quantità di denaro.
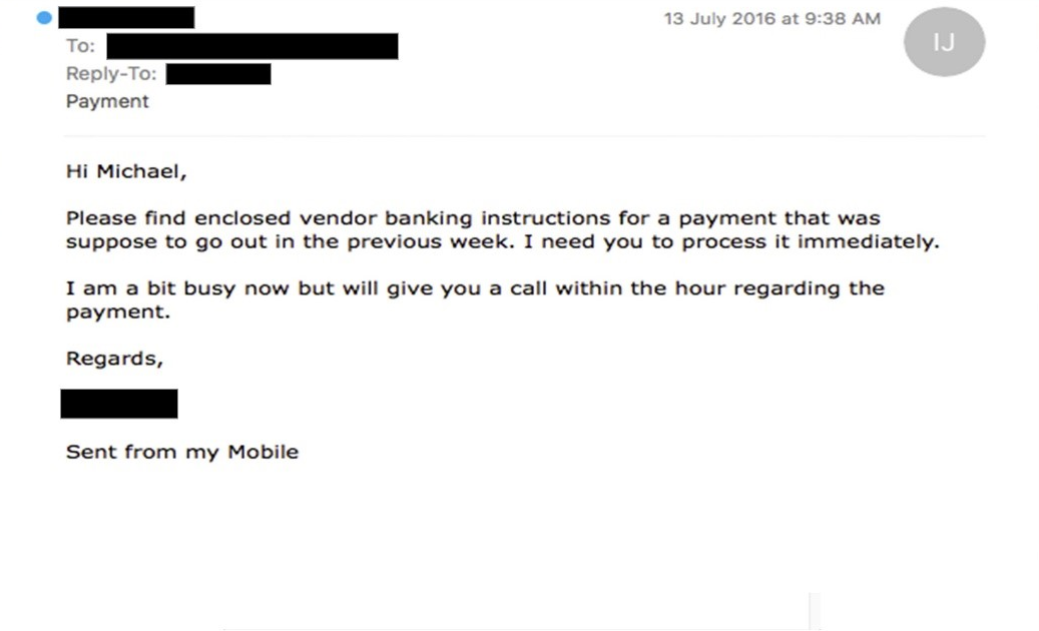
Figura 5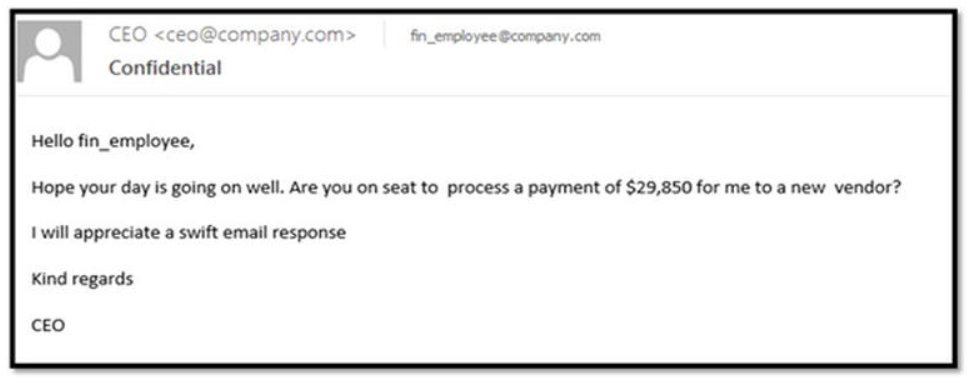
Figura 6
La maggior parte dei mittenti legittimi invierà un’e-mail includendo un blocco completo della firma nella parte inferiore dell’e-mail. Inoltre, le informazioni su quel blocco devono corrispondere al testo in altre parti dell’e-mail. Si vedano le figure 4 e 5, non è presente alcun blocco di firma.
In figura 7, si può notare una mancata corrispondenza tra il riferimento del mittente e i dettagli sul blocco della firma.
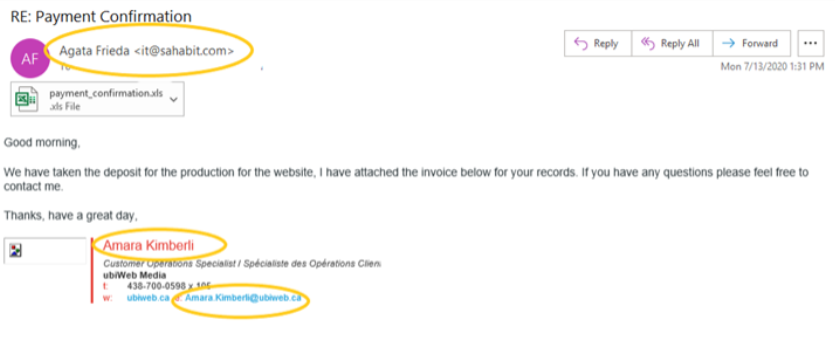
Figura 7
Un rapporto F-Secure sui tipi di allegati e-mail più pericolosi afferma che ci sono l’85% di possibilità che le e-mail dannose contengano allegati .DOC, .XLS, .PDF, .ZIP o .7Z. Questi sono i file che gli utenti aprono spesso senza alcuna esitazione perché sono così comunemente usati nelle aziende: gli hacker lo sanno e lo usano a loro vantaggio. Questo potrebbe essere il punto di ingresso per un software/dropper per l’avvio di un attacco ransomware e/o APT.
Se qualcosa non torna, o sembra anche leggermente fuori dalla norma, chiamate un collega o telefonate a persone di aziende terze che possano confermare che l’e-mail sia legittima oppure una truffa. Come controllo finale chiamate sempre e segnalate l’evento ai vostri esperti di sicurezza IT.
Nuove truffe di phishing vengono sviluppate continuamente. Senza stare al passo con queste nuove tecniche, potreste inavvertitamente cadere in una di esse. Tenete gli occhi aperti sulle novità: venendo a conoscenza di loro il prima possibile, correrete un rischio molto minore di essere fregati ed di abboccare.
Per gli amministratori IT, si consiglia di seguire una formazione continua sulla consapevolezza della sicurezza e di simulare il phishing per tutti gli utenti dell’organizzazione per tenere in primo piano la sicurezza.
In caso di dubbio, contattate sempre gli esperti di sicurezza informatica della vostra organizzazione.
Gli allegati e gli URL dannosi possono essere analizzati utilizzando il sito di VirusTotal:
Punti di estensione per evitare lo spoofing:
Sebbene il phishing possa essere un tema difficile da affrontare a volte, seguendo i semplici suggerimenti e consigli delineati in questo articolo (e adottando strumenti software di prevenzione del phishing adeguati come detto nell’introduzione) si potrà ridurre notevolmente il rischio di cadere vittima di truffatori digitali.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…