
RHC analysis of the “BHS Links” network and global Black Hat automated SEO infrastructure
An internal Red Hot Cyber analysis of its domain has uncovered a global Black Hat SEO network called “BHS Links,” capable of manipulating Google algorithms through automated backlinks and synthetic content.
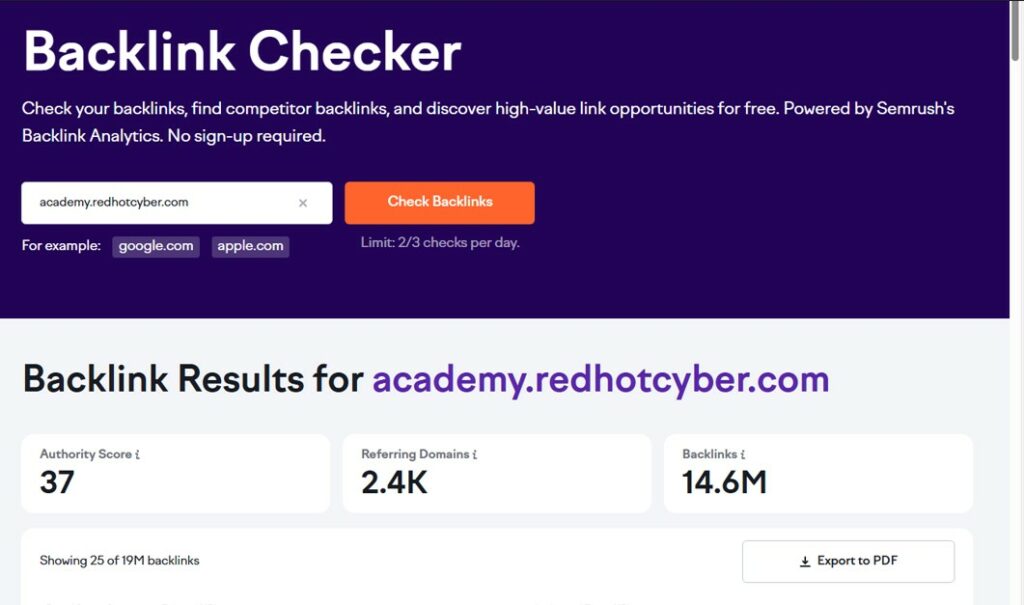
Many of these sites, hosted on distributed proxy networks in Asia, generated automated backlinks and synthetic content with the aim of manipulating search engine ranking algorithms .
These infrastructures combined rotating IPs, residential proxies, and publishing bots to simulate traffic and authority signals, a strategy designed to make the attack indistinguishable from organic activity and to bypass search engine automatic controls.
During the investigation, however, among the various clusters observed, one in particular attracted attention due to its size, coherence, and operational persistence: the non-Asian network called “BHS Links,” active since at least May 2025.
Unlike fragmented Asian groups, BHS Links presents itself as a structured “Black Hat SEO as a Service” ecosystem, which uses automation, anti-forensics techniques, and compromised domains to sell temporary rankings to anonymous clients in various sectors, often with high reputational risk (gambling, pharma, trading, adult).
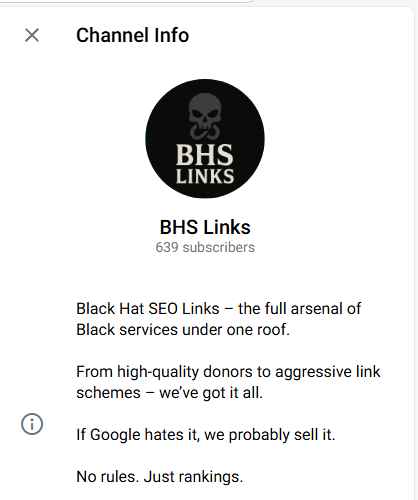
The BHS Links infrastructure comprises dozens of coordinated domains, including:
Each domain acts as a redistribution node: it aggregates backlinks , generates new pages, replicates HTML code from legitimate sites, and links to the official Telegram channel t.me/bhs_links.
Many domains are protected by Cloudflare and hosted on offshore servers , making traceability difficult. Forensic logs also indicate selective Googlebot filtering and deliberate cloaking patterns.
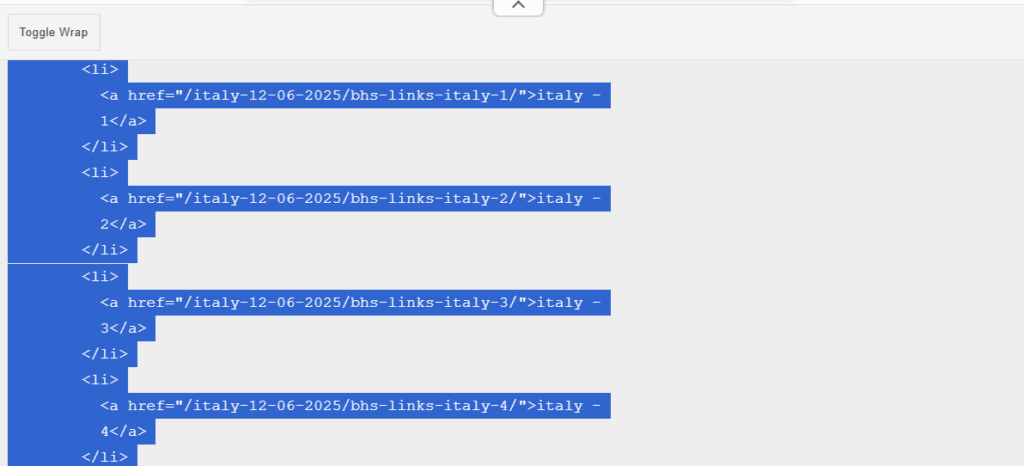
A test conducted by RHC using curl with different User-Agents highlighted selective cloaking behavior, a practice prohibited by Google Search Essentials.
C:UsersOSINT>curl -I -A "Googlebot/2.1 (+http://www.google.com/bot.html)" https://bhs-links-blaze.online
HTTP/1.1 403 Forbidden
Server: cloudflare
C:UsersOSINT>curl -I -A "Mozilla/5.0 (Windows NT 10.0; Win64; x64)" https://bhs-links-blaze.online
HTTP/1.1 200 OK
Server: cloudflare
The site deliberately blocks Google crawlers, making its promotional content invisible to avoid penalties. The Cloudflare rule is similar to:
Rule: Block Googlebot
Condition: (http.user_agent contains “Googlebot”)
Action: Block
From a forensics perspective, this is a deliberate anti-forensics technique , useful for evading Google’s automatic checks, hiding the network of artificially generated clients and backlinks, and disrupting crawl-based OSINT analysis.
While analyzing the source code of multiple BHS domains, RHC detected hundreds of links to legitimate Italian sites, including:
Ansa, repubblica.it, gazzetta.it, fanpage.it, legaseriea.it, adm.gov.it, gdf.gov.it, liceoissel.edu.it, meteofinanza.com, aranzulla.it, superscudetto.sky.it.
All domains cited are passive victims of algorithmic citation and are not involved in any illicit activity.
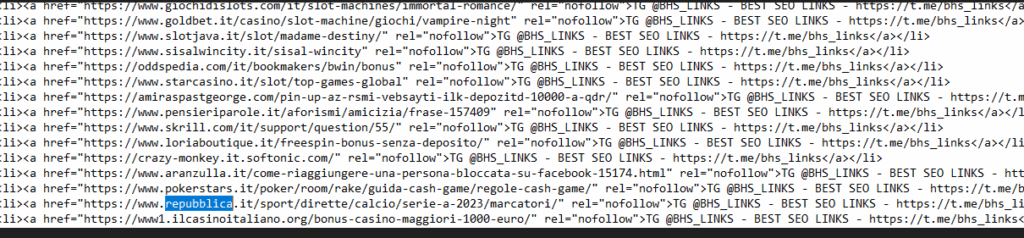
These websites aren’t compromised: they’re passively cited to exploit their reputation. This strategy is based on so-called semantic trust , where the mere co-occurrence of a reliable site and a malicious domain causes the algorithm to interpret the latter as credible. In other words, BHS Links doesn’t hack the sites, but uses them as reputational spotlights. This tactic allows clients to obtain temporary ranking boosts, especially in the gambling, forex, and adult content sectors.
A recurring element appears in the source code of the analyzed pages: a list enclosed in a
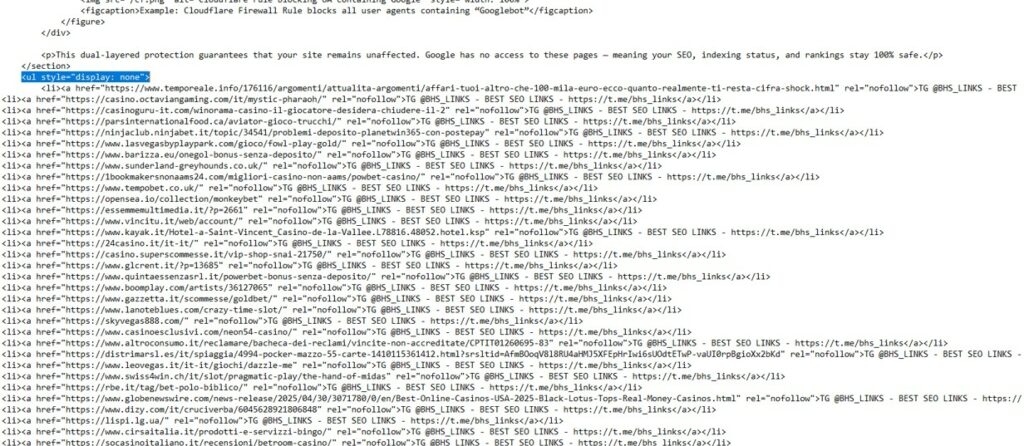
At first glance it may seem harmless, but in reality it represents one of the most insidious tactics of semantic cloaking : the links are made invisible to human visitors, but remain present in the source and therefore readable by search engine crawlers.
In this way, the BHS Links network injects dozens of hidden links to external domains, forums, online casinos, and affiliate sites, all branded with the “TG @BHS_LINKS – BEST SEO LINKS – https://t.me/bhs_links” tag. The server can serve two versions of the same page, one public and “clean” for users and one intended for bots, or it can leave the same HTML which, despite being hidden via CSS, is still indexed as shadow content : ghost content that lives in the code but not on the visible page.
Googlebot and other crawlers analyze source code and links even when they’re hidden via CSS. As a result, invisible references are interpreted as signals of co-occurrence and authority, giving the malicious domain a false sense of credibility. In practice, BHS Links thus creates an artificial reputational bridge between its domains and real portals (newspapers, regulated sites, authoritative blogs). To the user, everything appears normal; to the algorithm, however, it’s a rich network of thematic and authoritative links. It’s precisely this discrepancy between what humans see and what the algorithm interprets that makes semantic poisoning so effective and difficult to detect.
In all the cases analyzed, after the code injection already described, the technical evidence converges on two other recurring clues that complete the semantic deception triad:
These elements, taken together, constitute the recurring technical signature of the BHS Links operation.
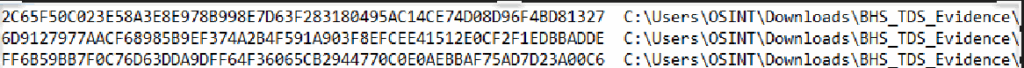
The SHA-256 hashes calculated for each file accurately confirm the semantic manipulation.
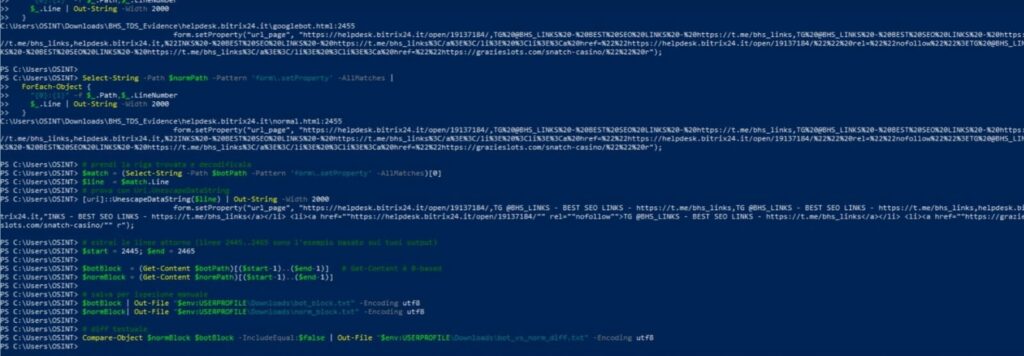
In the example case, the detected values show two distinct versions of the same page:
2C65F50C023E58A3E8E978B998E7D63F283180495AC14CE74D08D96F4BD81327 → normal.html , version served to the real user6D9127977AACF68985B9EF374A2B4F591A903F8EFCEE41512E0CF2F1EDBBADDE → googlebot.html , version intended for the Google crawler The discrepancy between the two hashes is the most direct evidence of active cloaking : the server returns two different HTML codes depending on who makes the request.
The file diff.txt , hashed FF6B59BB7F0C76D63DDA9DFF64F36065CB2944770C0E0AEBBAF75AD7D23A00C6 , documents the lines that are actually different between the two versions, constituting the forensic trace of the manipulation.
Here’s what one of the sites mentioned looks like, left intact and unaltered by cloaking.
After verifying the hashes, code analysis reveals a further manipulation strategy: semantic rotation of the contents.
In this scheme, the Bitrix24 CMS generates dynamic blocks with different IDs depending on the user agent. The normal.html and googlebot.html files display the same content but in reverse order, a semantic rotation that changes the logical priority of internal links. To Googlebot, the site appears semantically rewritten: some sections, often those containing hidden references to the BHS Links trademark, gain greater weight in the semantic graph, influencing the authoritativeness rating. This is an invisible but precise manipulation that affects the algorithm’s cognitive hierarchy.
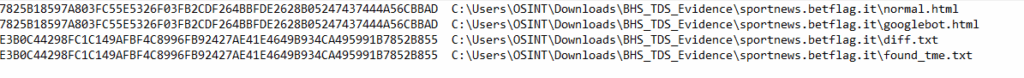
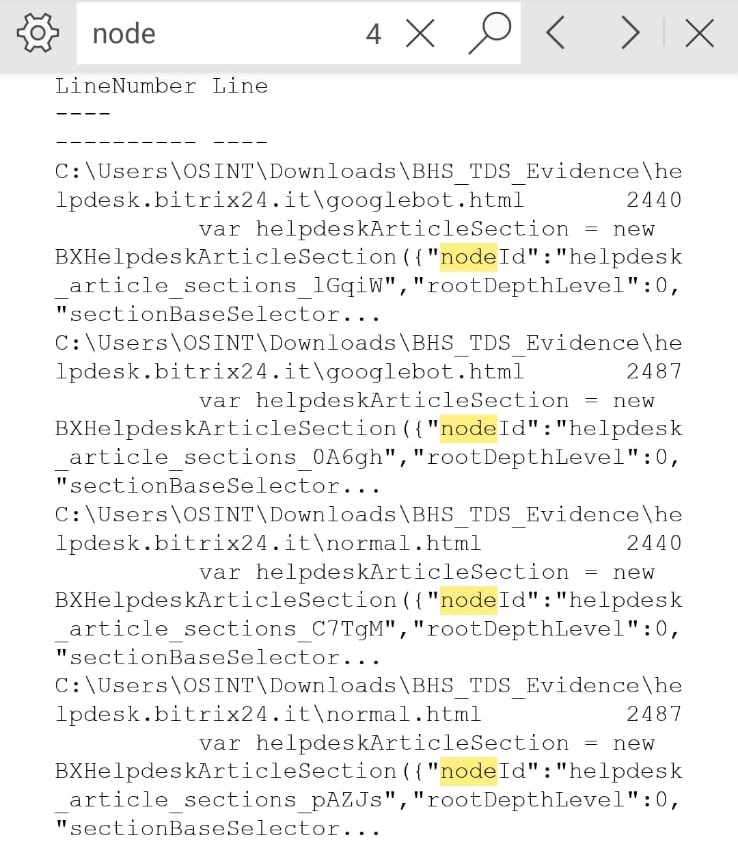
To verify the anomaly, RHC compared two locally acquired versions of some sites: normal.html (real user) and googlebot.html (Google crawler).
The code served to Googlebot has different section IDs generated by the CMS, such as helpdesk_article_sections_lGqiW and helpdesk_article_sections_0A6gh , while in the normal version the same blocks have different IDs, such as C7TgM and pAZJs .
This change doesn’t change the visual appearance of the page, but it does alter the logical structure interpreted by the search engine: Googlebot interprets the content with a different hierarchy, assigning greater importance to certain internal links. This is the mechanism of semantic rotation : an invisible rewriting that guides the algorithmic understanding of the page.
In the bot version’s code, there is also a line that doesn’t exist in the normal file:
form.setProperty("url_page","https://helpdesk.bitrix24.it/open/19137184/,TG @BHS_LINKS - BEST SEO LINKS - https://t.me/bhs_links")
The same semantic manipulation techniques employed by the BHS Links network, when directed against legitimate domains, transform into Negative SEO : a reputational weapon capable of contaminating search results, duplicating content, and inducing Google’s algorithm to devalue the original source.
During the analysis, RHC documented duplication of the institutional headline
“Cybersecurity is about sharing. Recognize the risk, combat it, share your experiences, and encourage others to do better than you.”
This phrase, belonging to the official Red Hot Cyber portal, has appeared on spam portals and compromised domains of various origins, combined with pornographic or clickbait titles.
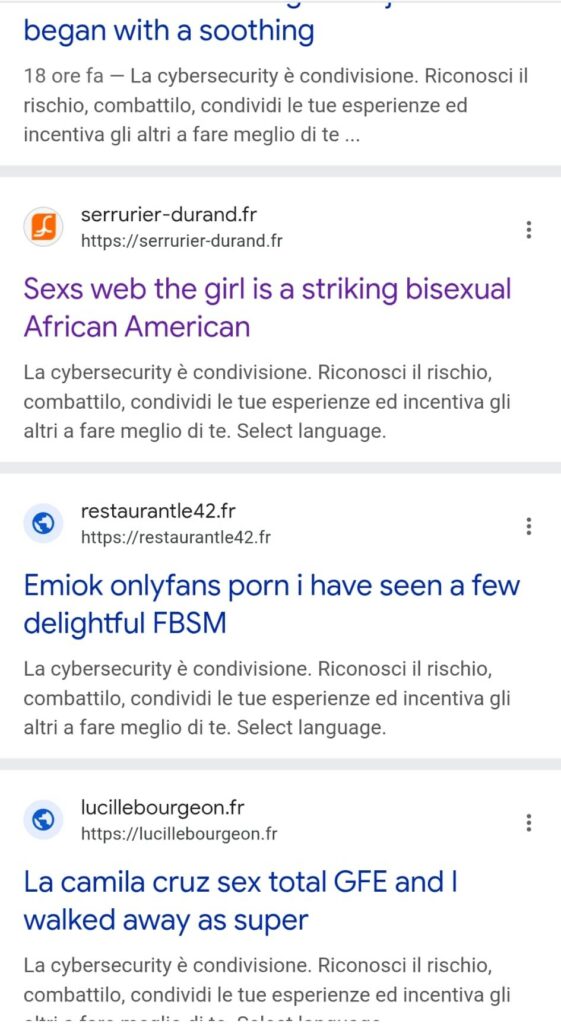

The evidence collected shows results on Google such as:
peluqueriasabai.es — Woman seeking man Avezzano contacted the booker and set uprestaurantele42.fr — Emiok OnlyFans porn I have seen a few delightful FBSMlucillebourgeon.fr — La Camila Cruz sex total GFE and I walked away as superbenedettosullivan.fr — Baad girl Sandra her images caught my eye and I had timeserrurier-durand.fr — Sexs web the girl is a striking bisexual African American In all cases, the description under the title featured the lyrics of Red Hot Cyber, creating a paradoxical effect:
pornographic or spam content presented in the tone of a reputable cybersecurity news outlet.
This mechanism is at the heart of semantic theft : Google’s algorithm automatically merges title and description based on semantic clues, generating hybrid and seemingly credible results.
Thus, real brands and authoritative phrases become involuntary reputational bait to push malicious networks to the top.
In the Red Hot Cyber case, the original phrase was extracted from the main domain, cached, and reused to construct fake authority snippets , which reinforce the trustworthiness of the compromised sites.
It is a form of third-generation negative SEO : it does not directly destroy the target site, but reuses its identity to deceive ranking algorithms and, with them, the very perception of digital reputation.
Behind the semantic theft lies a deeper and more functional structure: the Traffic Direction System (TDS) of the BHS Links network.
Analysis of HTML dumps and decoded Base64 strings revealed this infrastructure, designed to route and monetize manipulated traffic through SEO.
The identified redirects point to a stable group of domains that constitute the heart of the network’s dating-affiliate circuit, active for months and already observed in international contexts.
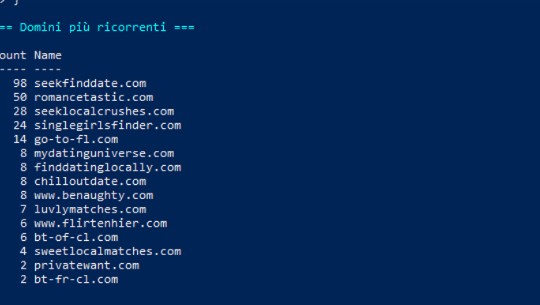
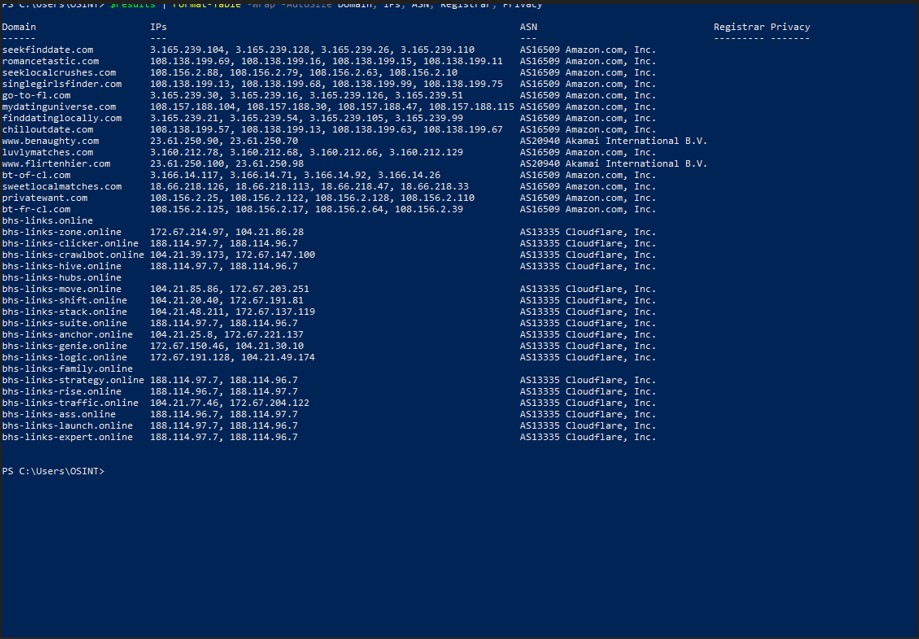
Among the main ones, seekfinddate.com acts as a central sorting hub, present in almost all of the dumps analyzed.
From there, traffic is directed to romancetastic.com , singlegirlsfinder.com , finddatinglocally.com , sweetlocalmatches.com , and luvlymatches.com , which operate as landing pages for affiliate networks like Traffic Company , AdOperator , and ClickDealer .
Connecting these layers are bridge domains such as go-to-fl.com , bt-of-cl.com , and bt-fr-cl.com , which mask redirects and often rely on Cloudflare to hide the origin of the traffic.
The chain is completed by alternative front ends such as mydatinguniverse.com , chilloutdate.com , privatewant.com , and flirtherher.com , which dynamically redirect based on the user’s IP address, language, or device.
In practice, compromised or synthetic pages on the BHS network include encrypted redirects that lead first to TDS nodes and then to affiliate landing pages or dating scams.
The analysis of the parameters (tdsid, click_id, utm_source, __c) confirms the typical affiliate tracking pattern: a BHS page, a TDS domain (e.g. seekfinddate.com), and finally a commercial or fraudulent landing page.
Hosted on proxy networks distributed across Asia and protected by Cloudflare, these sites generate backlinks and synthetic content to deceive search engines by feigning popularity and authority.
Cross-analysis of IP addresses and autonomous system addresses (ASNs) confirms the infrastructural overlap between the two network layers.
Domains in the “dating-affiliate” network, such as seekfinddate.com, romancetastic.com, singlegirlsfinder.com, and mydatinguniverse.com, are hosted on Amazon AWS (AS16509), while domains in the BHS Links network, such as bhs-links-zone.online, bhs-links-anchor.online, and bhs-links-suite.online, are served by Cloudflare (AS13335).
This dual architecture suggests a clear division of roles: Amazon hosts the sorting and monetization nodes, while Cloudflare ensures obfuscation and persistence of SEO domains.
The repetition of the same IP blocks and the coincidence between ASNs demonstrate that this is a coordinated infrastructure, in which reputation is manipulated on one front and monetized on the other.
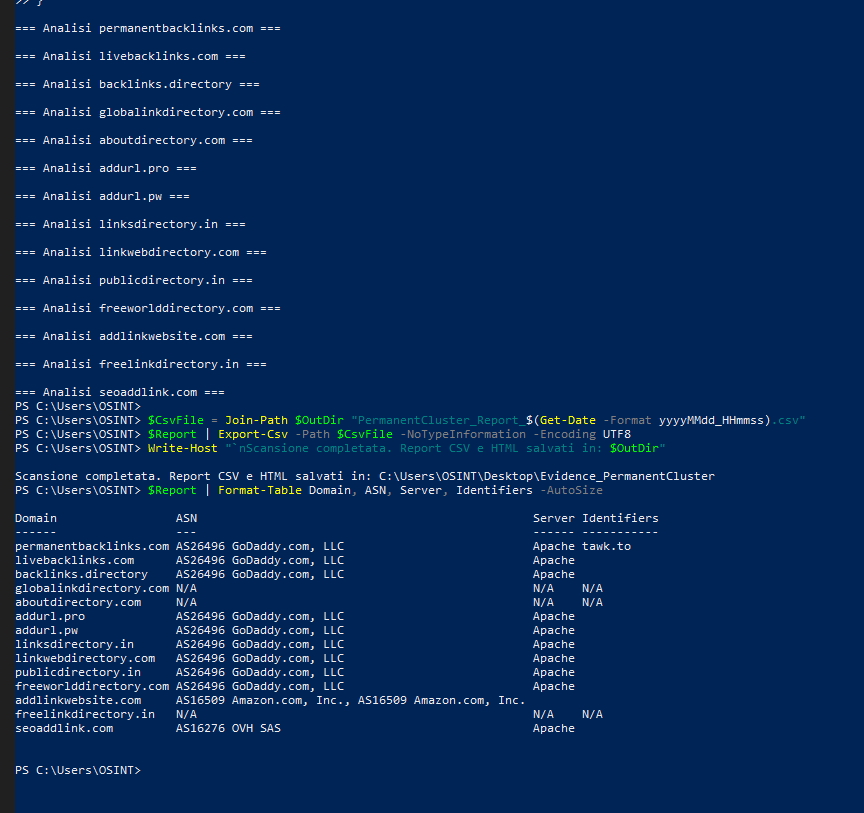
During the investigation of the BHS Links network, Red Hot Cyber identified a second group of portals linked to the permanentbacklinks.com domain, which shows structural and operational similarities with the previously analyzed networks.
The site is configured as an architectural platform dedicated to the automated management of backlinks, with logic compatible with the link building clusters already observed.
Unlike BHS domains, which focus on directly manipulating ranking signals and selective cloaking, the Permanent Backlinks cluster acts as an infrastructure backend—a domain list collection, replication, and distribution hub designed to power multiple instances with identical datasets.
It doesn’t host actual “SEO directories,” but builds coherent, self-referencing ecosystems to resist penalties and ensure customer continuity.
The permanentbacklinks.com domain is the hub of this synchronized replication network, which includes, among others, livebacklinks.com, backlinks.directory, addurl.pro, addurl.pw, linkwebdirectory.com, and publicdirectory.in.
The latter act as a sending satellite : the “Add Your Link” module allows you to insert a domain or a link, showing the “Rules & Regulations” section on the same page, with a limit of 255 characters, exclusion of expired domains, disabled guest submission and the promise of “delivery reports” visible only within the account.
Immediately below the form, a second button appears, “Proceed to permanentbacklinks.com” , which explicitly links to the parent site .
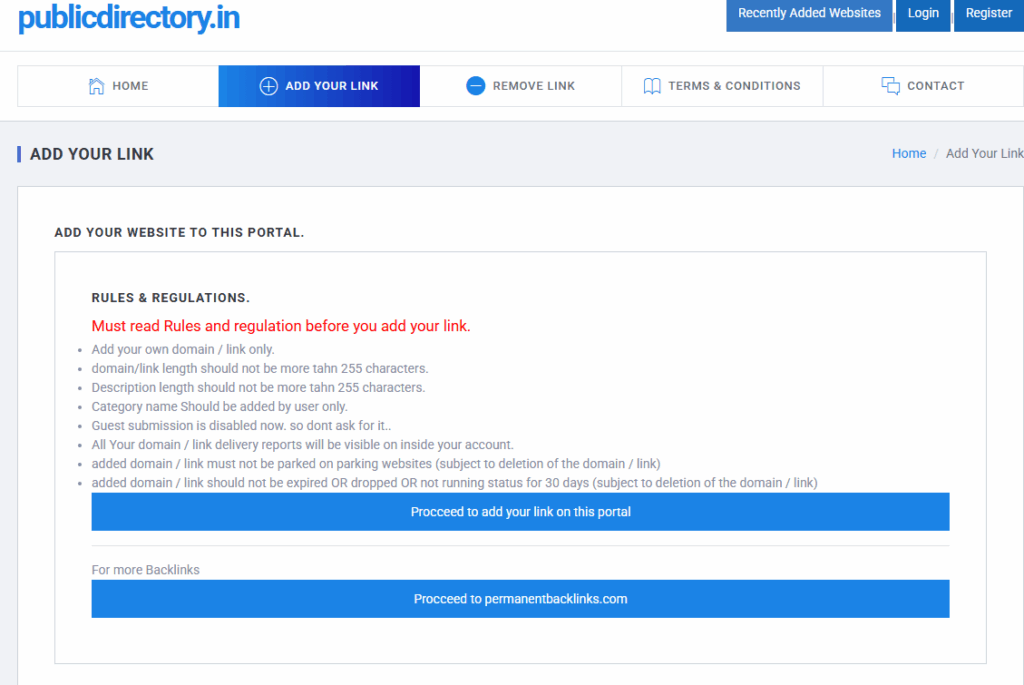
The way it works is straightforward: users fill out the form on the satellite portal, but for multiple links, they’re directed to the central hub to complete or purchase the service. It’s therefore not a standalone directory, but rather a functional promotional frontend connected to the main hub , responsible for collecting traffic and referrals.
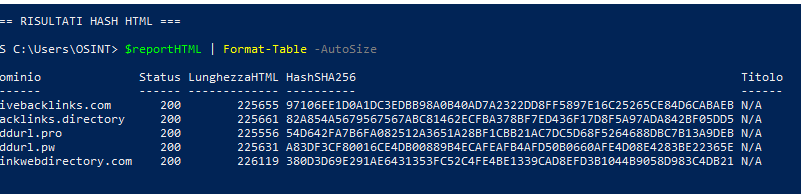
Analysis conducted by RHC with PowerShell environment on eight portals of the cluster, including addurl.pro , addurl.pw , livebacklinks.com , backlinks.directory , linkwebdirectory.com , publicdirectory.in , onlinelinkdirectory.com and permanentbacklinks.com , highlighted a uniformly generated infrastructure.
The HTML pages have similar dimensions and a nearly identical structure, with minimal variations in the markup that can be traced back to the same builder.
Only permanentbacklinks.com displays an active form ( action="/search/websites.php?" , q field), confirming its role as the main operational node, while the other sites, although without visible forms, share the same dataset and functional layout.
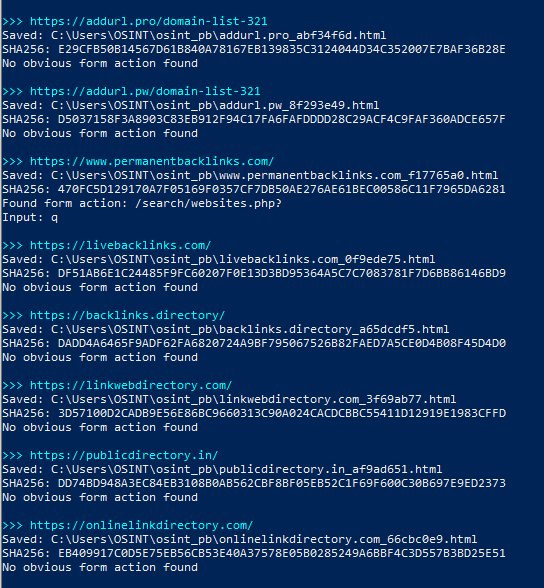
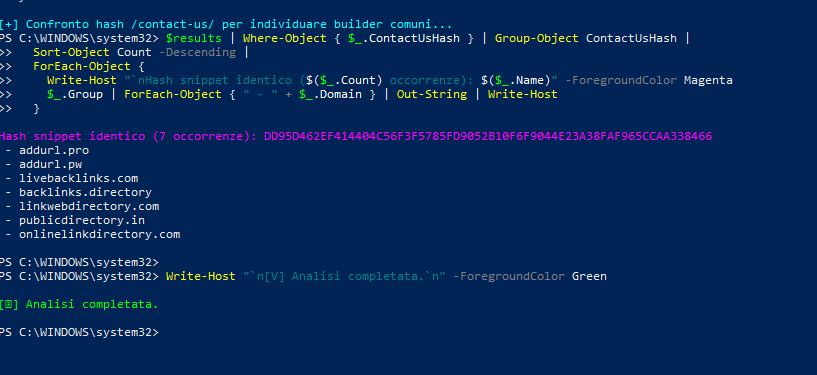
Seven portals, including addurl.pro, addurl.pw, livebacklinks.com, backlinks.directory, linkwebdirectory.com, publicdirectory.in, and onlinelinkdirectory.com, share the same “Contact Us” HTML block, with an identical hash and a unified path (/contact-us/).
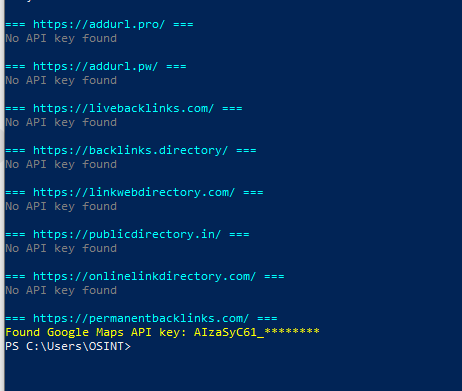
This seemingly minor element is a clear architectural indicator of the use of a common builder or publishing engine, consistent with a multi-instance system managed by a central node. Code analysis also highlights the presence of a Google Maps API key exposed on permanentbacklinks.com, while the other domains return no key, suggesting the reuse of assets and configurations within the same ecosystem.
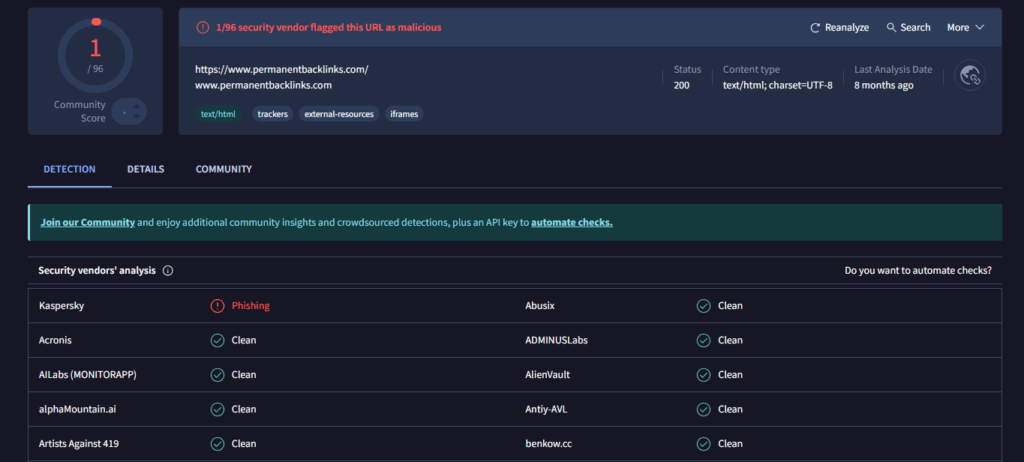
The discrepancy in VirusTotal’s results is significant:
permanentbacklinks.com is detected by Kaspersky as “phishing”, while the others are “clean” for all engines.
The difference reflects the different roles of the two domains in the network: the first acts as a central interactive hub , with active forms and redirects, while the second operates as a passive mirror , without forms or POST calls.
In this context, detection does not imply fraudulent behavior in the strict sense, but rather a heuristic matching with patterns typical of data collection or SEO automation platforms.
This is a technical signal consistent with a multi-tiered infrastructure, where only the central node actually manages the flow of requests.
With a high degree of technical confidence, the set of all the evidence discussed describes a synchronized replication system, where satellite portals operate as collection interfaces and service storefronts, while the central hub manages content propagation and synchronization.
No automatic data forwarding was detected; verification would require analyzing POST packets and HTTP headers, but the consistent structure, rules, and links suggest centralized dataset management, typical of a distributed link automation platform.
Furthermore, automated analysis conducted in PowerShell returned output consistent with this interpretation, highlighting matches between domains and the presence of active mirrors on the same root IP or on contiguous subnets.
The WHOIS information shows synchronized registration and renewal dates, while the output sections for hashes and “partial HTML fingerprints” indicate the presence of a common builder.
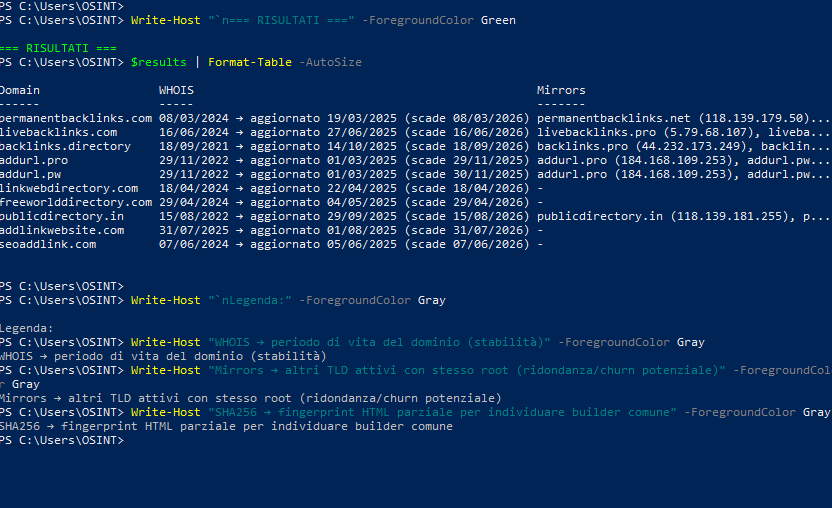
The point is not how many sites make up the network, but how they are replicated.
The differences between the SHA-256 hashes demonstrate that they are not static copies, but versions generated by the same engine with small markup variations, a behavior consistent with a synchronized multi-instance system designed to evade direct correlation.
Analysis by RHC shows that the /domain-list-321 pages of various domains list the same record sequences, with the same IDs and the same structure.
In particular, the #320166 record associated with redhotcyber.com appears in identical locations and with an “Active” status on all instances, representing the signature of a centralized dataset powering multiple nodes.
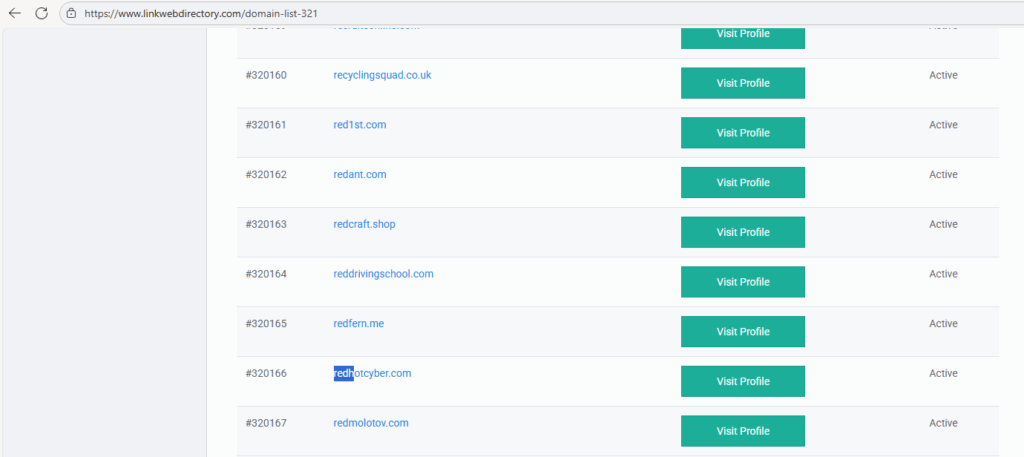
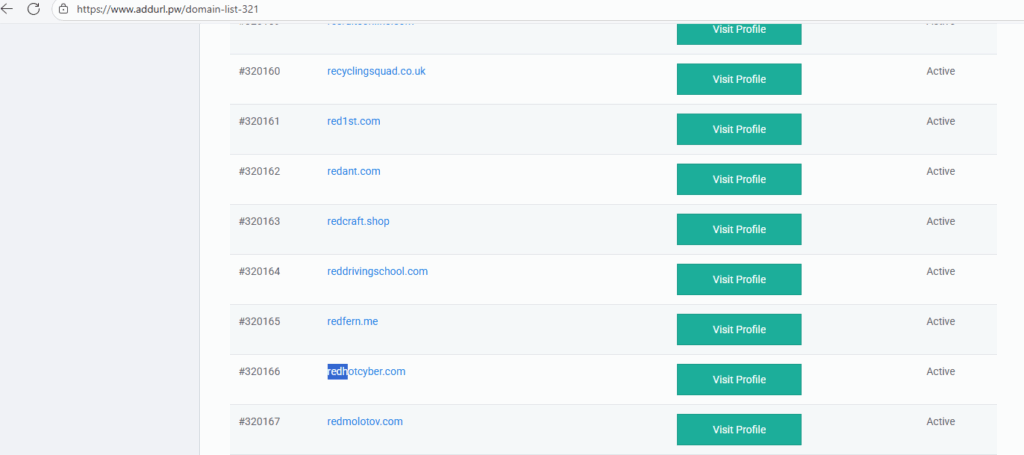
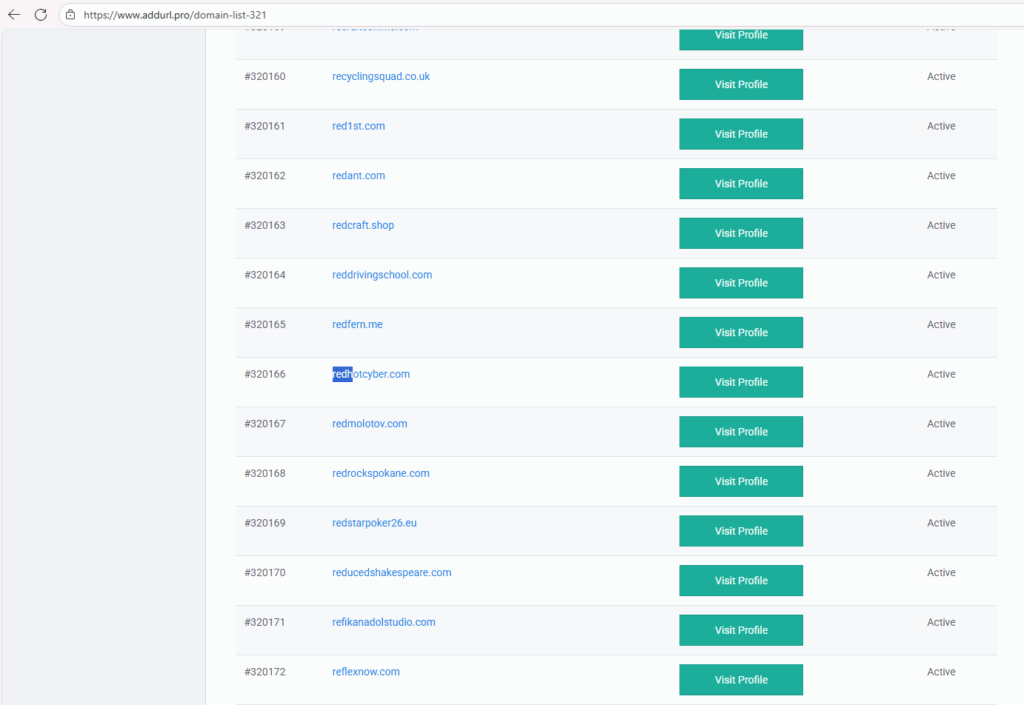
From an OSINT perspective, the logic is clear: same dataset, different renderers.
The network reduces the possibility of algorithmic tracking but retains recurring patterns, such as structure, record IDs, and trust elements, which make it recognizable to forensic analysis.
The occurrence of redhotcyber.com in the dataset does not generate editorial backlinks or real SEO value: it serves to disguise the semantic context.
It’s trust spoofing : among random domains, inserting references to well-known and legitimate portals, such as newspapers, public bodies or tech sites, artificially raises the perception of authority (“if A cites B, then A must be trustworthy”).
In this scheme, Red Hot Cyber is not a real recipient but an element of simulated reputation , used as a decoration of trust.
It is therefore not a network that sells links , but an infrastructure that sells apparent trust , by synchronously replicating the same datasets across multiple domains.
In short, the web does not create authority: it imitates it.
And in doing so, it uses legitimate brands to mask a fictitious industry ranking structure, designed to survive even after its discovery.
Technical evidence confirms the existence of a unified builder : meta tags, JavaScript libraries (jQuery, Popper, Bootstrap), and the window._trfd variable with the identifier dcenter:"sg2" are identical across all instances. The footer, with the words “© aboutdirectory.com 2025,” is also unchanged.
All main domains resolve to IPs in the same region (Singapore, AS26496 – GoDaddy.com LLC), organized into two segments: 184.168.xx for the stable core and 118–119.139.xx for elastic capacity and backup replicas.
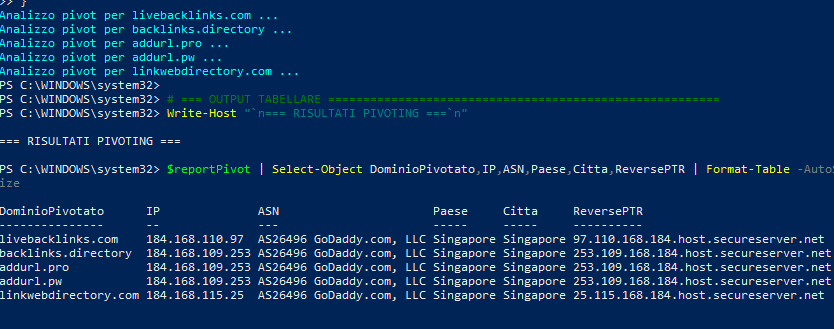
This design suggests a “ churn and replace ” system: a selective rotation logic that allows a compromised domain to be quickly replaced without disrupting the dataset distribution.
Permanent Backlinks thus acts as a persistence node of the larger BHS Links ecosystem, ensuring signal continuity and replicating content across multiple synchronized hosts.
Black Hat SEO encompasses tactics that violate Google’s terms of service to manipulate search engine rankings. The most well-known of these is manipulative link building, the mass creation of artificial backlinks to simulate authority.
In the early years of the web, directories were a legitimate tool for visibility. With the evolution of aggressive SEO, the logic changed: quality gave way to quantity, generating automated link networks like those analyzed in the BHS Links cluster by Red Hot Cyber.
With the Panda and Penguin updates, Google introduced filters to penalize unnatural linking patterns. Services like permanentbacklinks.com, based on thousands of uncurated links, are now considered cases of unnatural linking, exposed to algorithmic or manual penalties. Algorithms now easily recognize geometric patterns and structural repetitions (known as algorithmic fingerprints), which reveal the artificial nature of the web.
If Black Hat SEO aims to build fictitious authority, Negative SEO represents its flipside: the same techniques transformed into a reputational weapon. They no longer serve to boost one site’s rankings, but to lower another, eroding the trust the algorithm places in the targeted domain.
In this offensive approach, tools such as link farms, PBNs (Private Blog Networks), cloaking, or deceptive redirects are used not to promote, but to contaminate. The target suddenly finds themselves surrounded by thousands of toxic backlinks or spurious copies of their content, to the point of being penalized either algorithmically or manually. The logic is reversed: what in Black Hat SEO is the artificial construction of authority, in Negative SEO becomes the demolition of another’s reputation.
The line separating the two phenomena is thin but substantial. The first serves to inflate the visibility of those who adopt it, the second to destroy that of a competitor. Both manipulate the algorithm, but in opposite directions: Black Hat builds trust, Negative SEO erodes it.
Making the phenomenon even more insidious is its operational ambiguity. Many services designed for promotional purposes, such as selling backlinks or guest post packages on compromised sites, end up producing negative SEO side effects even without direct intent. The automated dissemination of links on a large scale, without quality filters or control over domain origin, generates a web of digital contamination that affects both victims and attackers alike. In this distorted ecosystem, the line between promotion and sabotage blurs, and search engine positioning becomes a battlefield where reputation is the first casualty.
SEO forensic diagnostics often starts from signals visible directly in the Google Search Console (GSC) , which represents the first warning tool in case of pollution or attack.
Among the most frequent symptoms are:
Taken together, these clues suggest that the domain may have been exposed to toxic link campaigns or manipulation schemes typical of negative SEO. From there, we proceed with a technical analysis of the backlinks, a check for suspicious referrals, and possible remediation using disavow tools.
Backlink auditing is one of the most important steps in diagnosing SEO issues.
Through the systematic analysis of incoming links, it is possible to distinguish organic and progressive links, generated over time by authentic content or spontaneous citations, from artificial or toxic ones, produced en masse by automated networks such as BHS Links.
This type of analysis doesn’t just count links, but also evaluates the semantic quality, thematic coherence, and geographical distribution of sources. When numerous backlinks come from newly registered domains, with similar HTML structures, or repetitive anchors, the signal becomes clear: you’re dealing with an ecosystem designed to distort rankings.
In the specific case of BHS Links, link tracking revealed recurring patterns: sudden spikes in outbound links, anchors manipulated with commercial keywords, and cross-references to hidden directories. These are all typical signs of an artificial SEO operation, aimed not only at boosting their own domains but also semantically polluting the legitimate linked ones.
When a domain shows signs of compromise or receives toxic backlinks , the first step is to map and isolate the suspicious domains. Malicious links can be collected in a simple text file (.txt, UTF-8 encoded) in the following format:
domain:bhs-links-hive.online
domain:bhs-links-anchor.online
domain:bhs-links-blaze.online
domain:backlinks.directory
The file should then be uploaded to Google Search Console , under the Disavow Tool section, to tell the search engine to ignore links from those domains . It’s important to monitor the effects of this process over time: removing the negative impact can take weeks, depending on how frequently Googlebot crawls your site.
In case of a manual penalty , you can submit a request for reconsideration , providing clear documentation of the actions taken:
A truly effective defense strategy requires ongoing prevention and constant monitoring of the digital ecosystem. The most recommended practices include:
A negative SEO campaign can begin with a series of malicious actions aimed at compromising a site’s reputation in the eyes of search engines. Attackers can, as in this case, generate thousands of low-quality backlinks from spam or penalized sites, making it appear as if the site is attempting to artificially manipulate its rankings. This type of attack can cause Google to reduce trust in the domain, resulting in a drastic drop in organic rankings and a significant loss of traffic.
A typical case is content duplication, which can occur when distinctive elements of the portal, such as original headlines or slogans , are copied and reused by third-party sites in a malicious manner. For example, the headline “Cybersecurity is sharing. Recognize the risk, fight it, share your experiences, and encourage others to do better than you,” originally conceived to promote the Red Hot Cyber philosophy, was detected in several posts published on unknown or low-quality portals, as seen previously, used for black SEO practices.
The damage resulting from a black SEO operation can be profound and long-lasting, going far beyond a simple loss of search engine rankings. In addition to the drop in organic traffic and reduced visibility, the portal can suffer a deterioration in trust among both users and ranking algorithms. When a site is associated, even indirectly, with spam, link farming, or duplicate content, Google and Bing filters can apply algorithmic or manual penalties that take months to remove.
In essence, in the digital world, trust is a capital that is lost in a day and rebuilt in months: once compromised, no technical optimization can restore it immediately.
This article is not intended to tell the unknown, but to explain.
Automated backlink networks and Black Hat SEO techniques are well known to industry insiders, but they are rarely described in detail in how they actually work.
Red Hot Cyber analyzed them using OSINT methods and verifiable technical tests, rigorously documenting how they manipulate algorithmic trust and the perception of authority.
It’s not about pointing fingers, but about understanding a mechanism that alters the transparency of the web, to restore to the community knowledge of what operates in the shadows of the SERP.
When trust is the only algorithm that cannot be corrupted, defending transparency is no longer a technical choice, but an act of digital resistance.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
