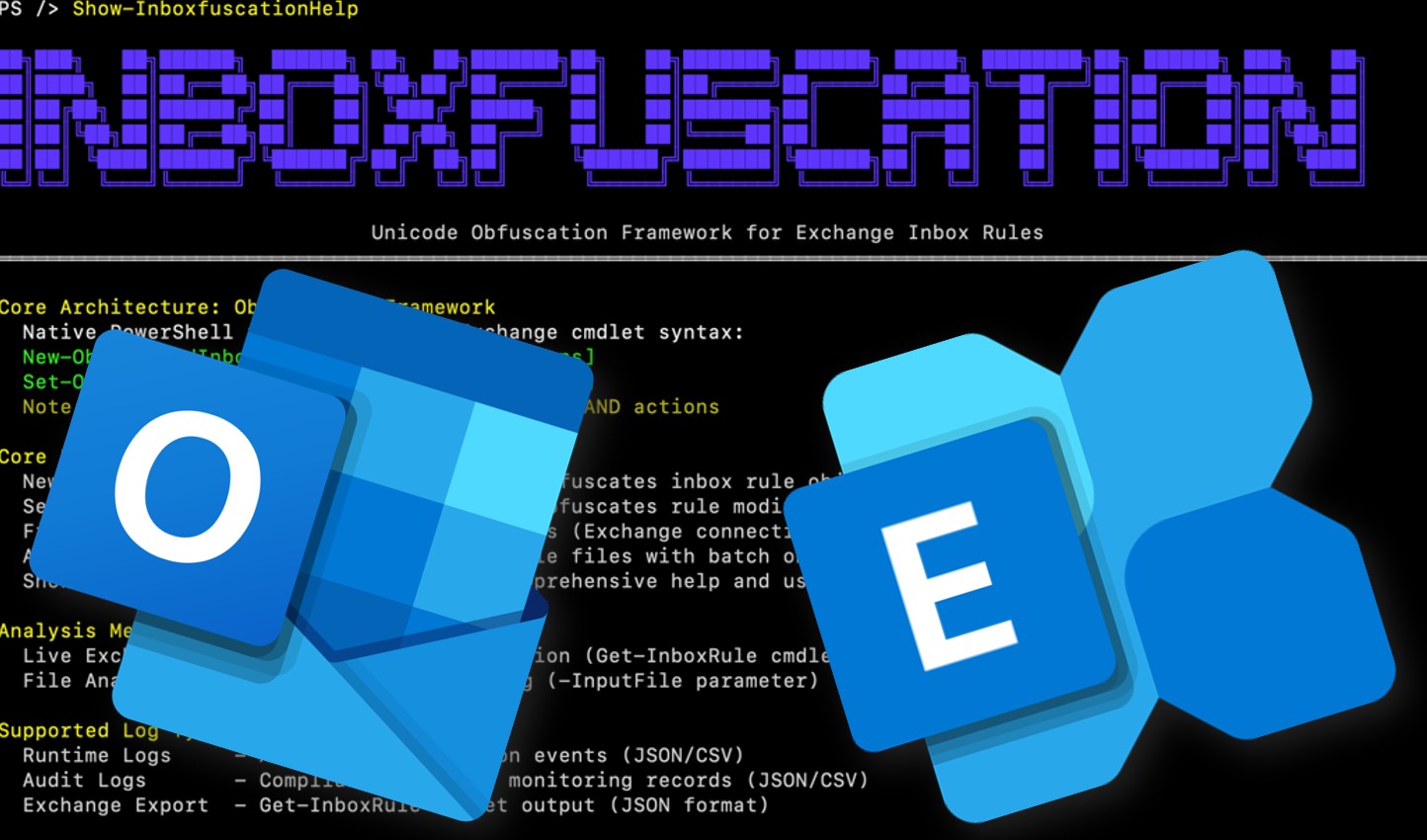
I malintenzionati stanno sempre più utilizzando le funzionalità della casella di posta in arrivo di Microsoft Exchange per garantirsi la persistenza e rubare informazioni sensibili all’interno dei network aziendali.
Inboxfuscation, sviluppato da Permiso, è un framework che dimostra come gli aggressori possano sfruttare il motore delle regole di Exchange come arma, creando meccanismi di persistenza furtivi che eludono sia la revisione umana sia il rilevamento basato sul codice.
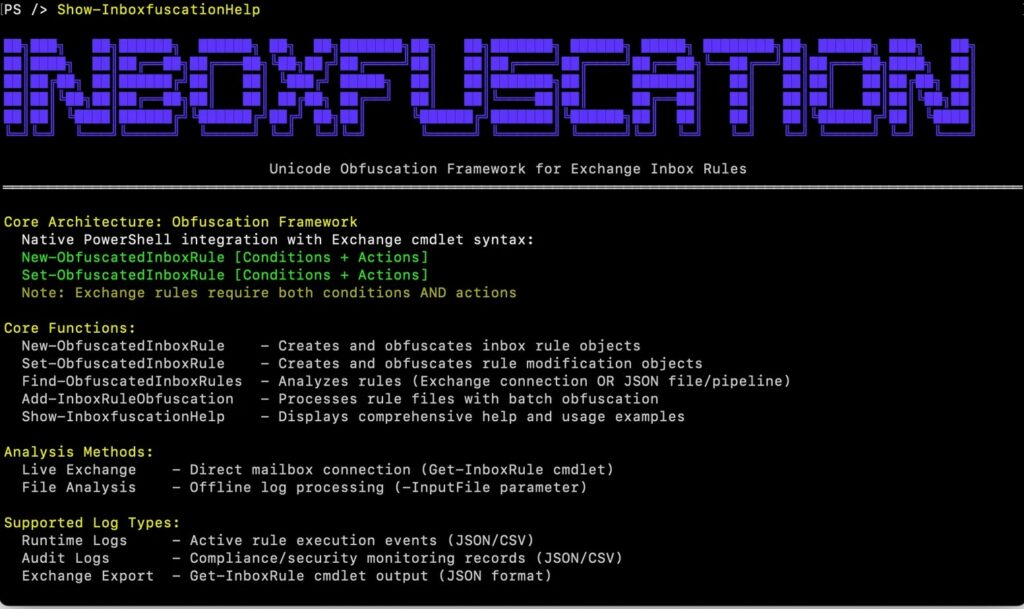
Inboxfuscation sfrutta tecniche di offuscamento basate su Unicode per generare regole di posta in arrivo dannose, che riescono a bypassare i sistemi di sicurezza tradizionali.
Nel passato le regole dannose per la posta in arrivo erano spesso semplici da individuare: parole chiave evidenti abbinate ad azioni come eliminare o inoltrare messaggi verso caselle controllate dagli aggressori. I tradizionali strumenti di sicurezza facevano affidamento su rilevamenti basati su parole chiave e su espressioni regolari, strategie che risultavano efficaci contro regole visivamente ovvie.
La disponibilità di un vasto repertorio di caratteri Unicode ha però aperto nuove vie di elusione. Sostituendo caratteri ASCII con varianti visivamente simili o sfruttando processi di normalizzazione eseguiti dal sistema, è possibile creare regole che sembrano innocue alla lettura ma che funzionano in modo differente sul piano logico, sfuggendo così ai meccanismi di rilevamento che si basano esclusivamente su corrispondenza testuale semplice. Pur non essendo state ancora osservate campagne che usino massicciamente queste tecniche, la fattibilità tecnica rappresenta un punto cieco che richiede attenzione.
Alcune categorie di caratteri rendono l’offuscamento particolarmente insidioso. Varianti dei caratteri permettono di replicare l’aspetto di lettere comuni; caratteri a larghezza zero possono essere inseriti tra lettere per interrompere la corrispondenza dei modelli senza alterare l’aspetto visivo; controlli bidirezionali possono ribaltare o riordinare il rendering del testo; varianti cerchiate o racchiuse alterano ulteriormente la percezione visiva. L’ampiezza dell’insieme Unicode offre molte opportunità di inganno visivo e funzionale.
Le tecniche di offuscamento si organizzano in approcci diversi che possono essere usati singolarmente o combinati. La sostituzione dei caratteri sostituisce simboli riconoscibili con equivalenti Unicode; l’iniezione a larghezza zero interrompe pattern con caratteri invisibili; la manipolazione bidirezionale sfrutta controlli di direzionalità per confondere il rendering; combinazioni ibride mixano questi metodi per massimizzare l’evasione. Queste strategie permettono a regole apparentemente innocue di eludere sia il giudizio umano sia il rilevamento automatizzato.
Oltre ai trucchi di offuscamento testuale, esistono tecniche funzionali che alterano il comportamento delle regole di posta. È possibile deviare automaticamente messaggi verso cartelle non convenzionali rendendoli non visibili nelle viste normali, inserire caratteri nulli o spazi che fanno sì che una condizione si applichi a tutti i messaggi, o sfruttare la normalizzazione di parametri di dimensione per creare filtri che si attivano su ogni email. Tali manipolazioni possono trasformare regole apparentemente innocue in meccanismi di persistenza o di occultamento.
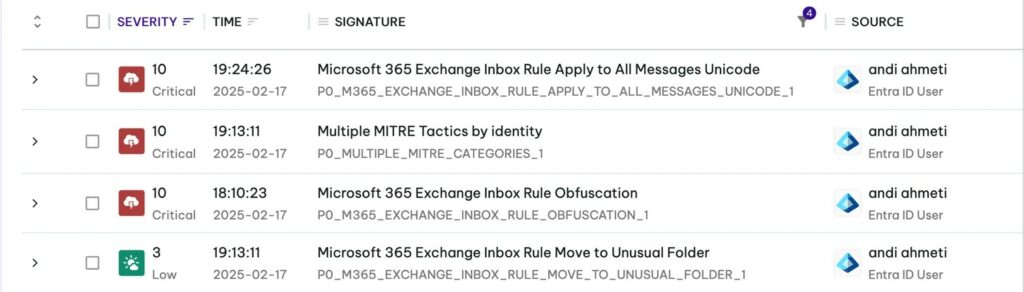
Per rispondere a queste minacce il quadro di rilevamento presentato adotta un approccio multistrato e compatibile con diversi formati di log di Exchange. Il sistema individua categorie Unicode sospette, analizza registri in diversi formati e produce output strutturati per l’integrazione con sistemi di security operations. Le azioni raccomandate includono la scansione delle caselle di posta per rilevare offuscamenti, l’analisi storica dei registri di controllo per individuare compromissioni passate e l’integrazione dei risultati nei processi SIEM e di risposta agli incidenti. La ricerca evidenzia lacune nelle difese attuali, rischi di compliance e difficoltà forensi legate alla complessità Unicode, invitando a sviluppare capacità proattive.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…