
The WinRAR security flaw, which emerged last summer, has become more widespread than expected. Several organizations, both common criminals and nationally funded APT groups, are actively exploiting this vulnerability, as reported by the Google Threat Intelligence Group (GTIG).
The vulnerability was initially discovered by ESET researchers. In early August 2025, they reported similar cyberattacks by the RomCom group. However, a recent Google report shows that exploitation began as early as July 18, 2025, and is still ongoing, with multiple attackers simultaneously.
This is a severe path traversal vulnerability ( CVE-2025-8088 ) related to the Alternate Data Streams (ADS) mechanism in Windows.
Using this tool, attackers can secretly write malicious files to arbitrary system directories, such as the startup folder, ensuring their stability after a computer reboot.
The attack pattern typically looks like this: a harmless decoy file, such as a PDF document, is hidden in a WinRAR archive. Additional data, including a malicious payload, is then hidden within the same archive via ADS.
The user opens a “document,” and WinRAR extracts the hidden file in the background, exploring paths, and saves it to the attacker’s desired location. These are often LNK, HTA, BAT, CMD, or scripts that run on login. Among the government cyber groups Google has identified as exploiting the CVE-2025-8088 vulnerability is a star-studded cast: UNC4895 (RomCom/CIGAR) sent phishing emails to Ukrainian military personnel and delivered the NESTPACKER (Snipbot) downloader. APT44 (FROZENBARENTS) used malicious shortcuts and Ukrainian-language callbacks to download add-ons. TEMP.Armageddon (CARPATHIAN) still uses HTA loaders that remain in the startup folder. Turla (SUMMIT) distributed its STOCKSTAY toolset, disguising the attacks as materials intended for the Ukrainian Armed Forces.
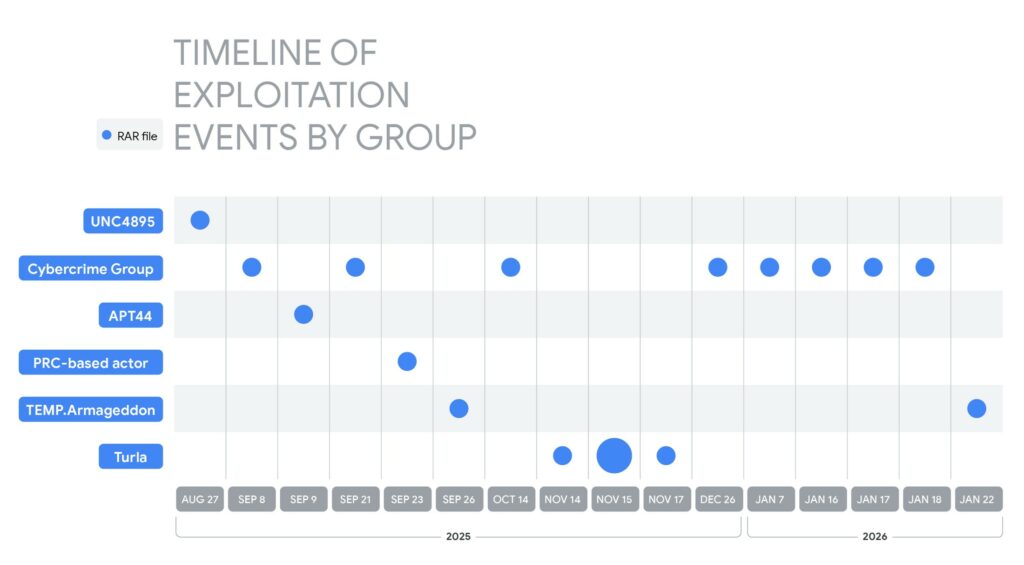
Chinese groups have also been identified using the exploit to spread POISONIVY via BAT files. But that’s not all. GTIG emphasizes that the vulnerability is also being actively exploited by financially motivated attackers . They use WinRAR to distribute popular Trojans and stealers, such as XWorm and AsyncRAT , backdoors controlled by Telegram bots, and malicious Chrome browser extensions that target banking data.
According to Google, most attackers didn’t create custom exploits, but simply purchased ready-made solutions from specialized vendors. One such vendor, known under the pseudonym ” zeroplayer ,” advertised a working exploit for WinRAR last summer.
Moreover, this is hardly its only “ product ”: it previously offered zero-days for Microsoft Office, remote code execution over corporate VPNs, local privilege escalation in Windows, and even security tool bypasses, at prices ranging from $80,000 to $300,000.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
