
In an article published on August 5, 2025, on the ISC SANS blog by Bojan Zdrnja, it is possible to steal “machine keys” from IIS servers. The author explores the mechanism of these keys and how they can be exploited, particularly in light of recent ToolShell exploits for Microsoft SharePoint. Machine Key theft poses a significant threat, allowing attackers to bypass data protection measures, such as VIEWSTATE validation, and potentially gain persistent access.
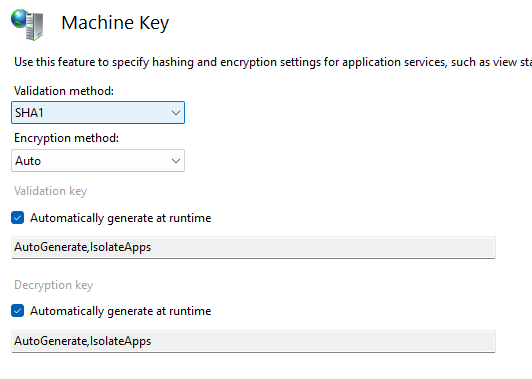
A Machine Key is a crucial configuration setting in IIS and ASP.NET, used to protect sensitive data such as VIEWSTATE, cookies, and session state. Its primary function is to validate and encrypt this data to prevent unauthorized tampering. The author explains how in ASP.NET Web Forms, the VIEWSTATE is a mechanism designed to maintain the state of page controls and data between postbacks to the server.
By default, IIS enables VIEWSTATE MAC (Message Authentication Code) validation, but encryption is often set to “Auto,” meaning it may not always be in use. The Machine Key is essential for this validation, which typically uses algorithms such as SHA1 or HMACSHA256. The author emphasizes that if an attacker gains control of a server’s machine key, they can alter the VIEWSTATE and cookie values at will.
Possession of a valid machine key can lead to very serious consequences, including remote code execution. The text illustrates two ways a machine key is commonly stored: either it is automatically generated by IIS and saved in the registry, or it is created by the administrator and stored in plain text in the web.config file. The author notes that attackers exploiting vulnerabilities such as file inclusion or XML external entities (XXE) can often retrieve the web.config file to steal the key.
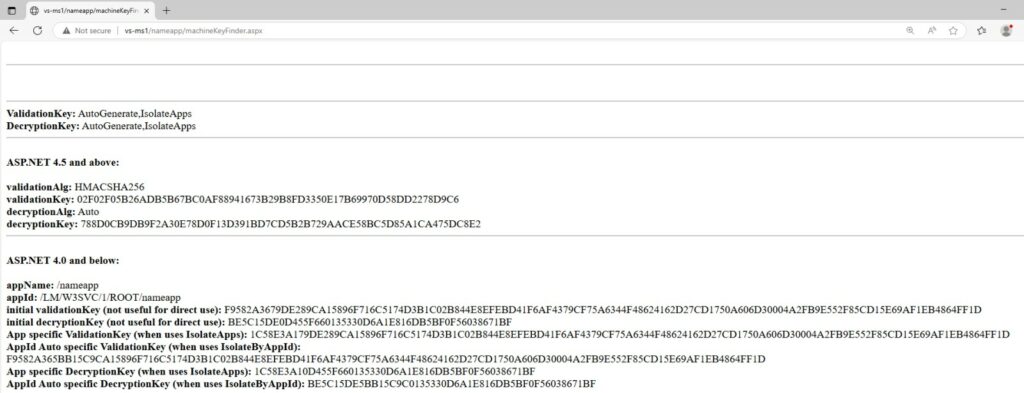
Even if the key is automatically generated and stored in the registry, an attacker who has already achieved code execution on the server can still read it. The article provides a practical example, a “proof-of-concept,” demonstrating how a stolen Machine Key can be exploited for remote code execution. Using a tool like ysoserial.net, an attacker can create a malicious VIEWSTATE object.
Since the attacker has a valid Machine Key, the server will successfully validate the object’s MAC and attempt to deserialize it, activating the malicious code. The author emphasizes that once an attacker has a valid Machine Key, they have effectively created a “persistent backdoor” to the server that will work on any ASPX page within the application.
Finally, the article offers a tip for administrators, explaining that they can detect such attacks by monitoring event code 4009 in the Windows Application log. This event is generated when VIEWSTATE deserialization fails, and the entire VIEWSTATE object is logged, allowing for deeper inspection.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
