
Navigare nel dark web può rivelare annunci inquietanti e allarmanti per chi si occupa di sicurezza informatica. Recentemente, abbiamo notato un post che offre in vendita un exploit 0-day, un tipo di strumento estremamente pericoloso. L’annuncio, proveniente da un utente con il nickname “admc21”, mette in mostra un attacco di Remote Code Execution (RCE) che colpisce le versioni più recenti di Windows, tra cui Windows 10, Windows 11 e Windows Server 2022. Il prezzo richiesto è di $125.000, una cifra che sottolinea il valore di questi strumenti sul mercato nero.
Ma cosa rende questi exploit così letali?
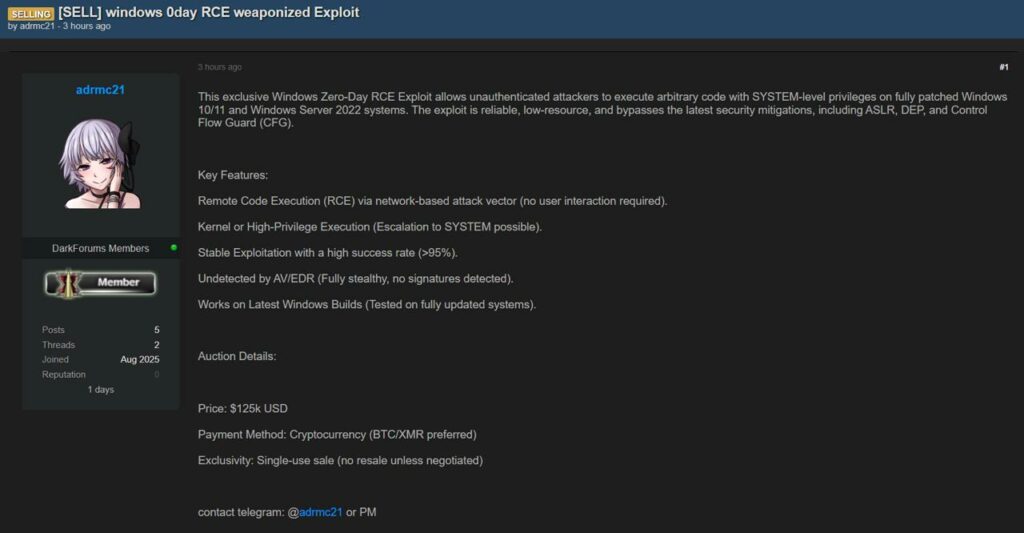
Il termine “0-day” (o zero-day) si riferisce a una vulnerabilità del software che è sconosciuta allo sviluppatore del prodotto. Questo significa che non esiste ancora una patch o un aggiornamento di sicurezza per correggerla. L’attaccante che scopre o acquista un exploit 0-day ha un vantaggio enorme: può sfruttare la falla per attaccare i sistemi senza che le vittime possano difendersi. Una volta che la vulnerabilità viene resa pubblica o scoperta, gli sviluppatori hanno zero giorni per preparare una contromisura.
Il post fa riferimento a un RCE, un tipo di attacco che consente a un cyber-criminale di eseguire codice malevolo sul computer della vittima da remoto, senza che questa se ne accorga. Nel caso specifico, l’exploit fornisce i privilegi di “SYSTEM”, il massimo livello di controllo su un sistema Windows.
È come dare le chiavi di casa all’aggressore: può rubare dati, installare malware o prendere il controllo totale del dispositivo.
L’annuncio specifica che l’exploit è in grado di aggirare le moderne difese di Windows come ASLR (Address Space Layout Randomization), DEP (Data Execution Prevention) e CFG (Control Flow Guard). Queste misure di sicurezza sono state create proprio per rendere più difficile lo sfruttamento delle vulnerabilità, ma un exploit 0-day ben progettato può riuscire a eluderle.
Il prezzo di $125.000 in criptovaluta ci offre uno sguardo sull’economia sommersa del cyber-crime. La richiesta di una “single-use sale” (vendita singola) indica che l’acquirente avrà l’uso esclusivo di questo strumento, almeno per un certo periodo, il che ne aumenta il valore e la segretezza.
Questa tipologia di transazioni alimenta un ecosistema in cui le vulnerabilità dei nostri sistemi vengono trasformate in armi digitali.
Allora, come possiamo proteggerci da una minaccia che non conosciamo? La risposta è complessa, ma si basa su alcuni principi fondamentali di cybersecurity:
La vendita di exploit 0-day ci ricorda che il mondo della sicurezza informatica è una battaglia continua.
Solo rimanendo informati, vigilanti e adottando le giuste contromisure possiamo sperare di rimanere un passo avanti rispetto alle minacce.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…