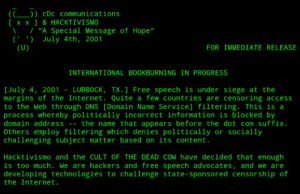
“If you’re looking for computer security, then the Internet is not the place to be.” Said Mudge, then 27, with the look of a biblical prophet wi...
03/07/2025
The Red Hot Cyber community is made up of a collection of people who actively collaborate, with different roles, to create targeted content focused on information security and technology, with the aim of spreading awareness and culture, and generating a mentality of widespread attention to IT risk and technology in general. All free of any political contamination.
|
(12314 articoli, 10918 italiano, 1396 inglese)12314 articoli
10918 italiano, 1396 inglese The editorial staff of Red Hot Cyber is composed of IT and cybersecurity professionals, supported by a network of qualified sources who also operate confidentially. The team works daily to analyze, verify, and publish news, insights, and reports on cybersecurity, technology, and digital threats, with a particular focus on the accuracy of information and the protection of sources. The information published is derived from direct research, field experience, and exclusive contributions from national and international operational contexts. |