
BazarLoader (a volte indicato come BazaLoader) è un “malware precursore“, che fornisce l’accesso backdoor iniziale ad un host Windows infetto. Dopo che un client è stato infettato, i criminali utilizzano questo accesso per inviare ulteriore malware, scansionare l’ambiente, sfruttare altri host vulnerabili sulla rete e lanciare il ransomware.
L’attore delle minacce dietro BazarLoader utilizza metodi diversi per distribuire questo malware alle potenziali vittime.
All’inizio di febbraio 2021, i ricercatori hanno iniziato a segnalare un metodo basato su call center per la distribuzione di BazarLoader. Questo metodo utilizza delle e-mail con un tema basato su abbonamento di prova che incoraggia le potenziali vittime a chiamare un determinato numero di telefono.
Un operatore di call center risponde e indirizza le vittime a un sito Web per annullare l’iscrizione del servizio. Gli operatori del call center si offrono di guidare personalmente le vittime attraverso un processo progettato per infettare i computer vulnerabili con BazarLoader.
Questo processo basato sul call center per infettare i computer con BazarLoader è stato soprannominato il metodo “BazarCall” (a volte indicato come metodo “BazaCall”).
Le infezioni BazarCall seguono uno schema ben preciso. Nella Figura 1 viene riportato un diagramma di flusso che mostra con precisione la catena di questi eventi.
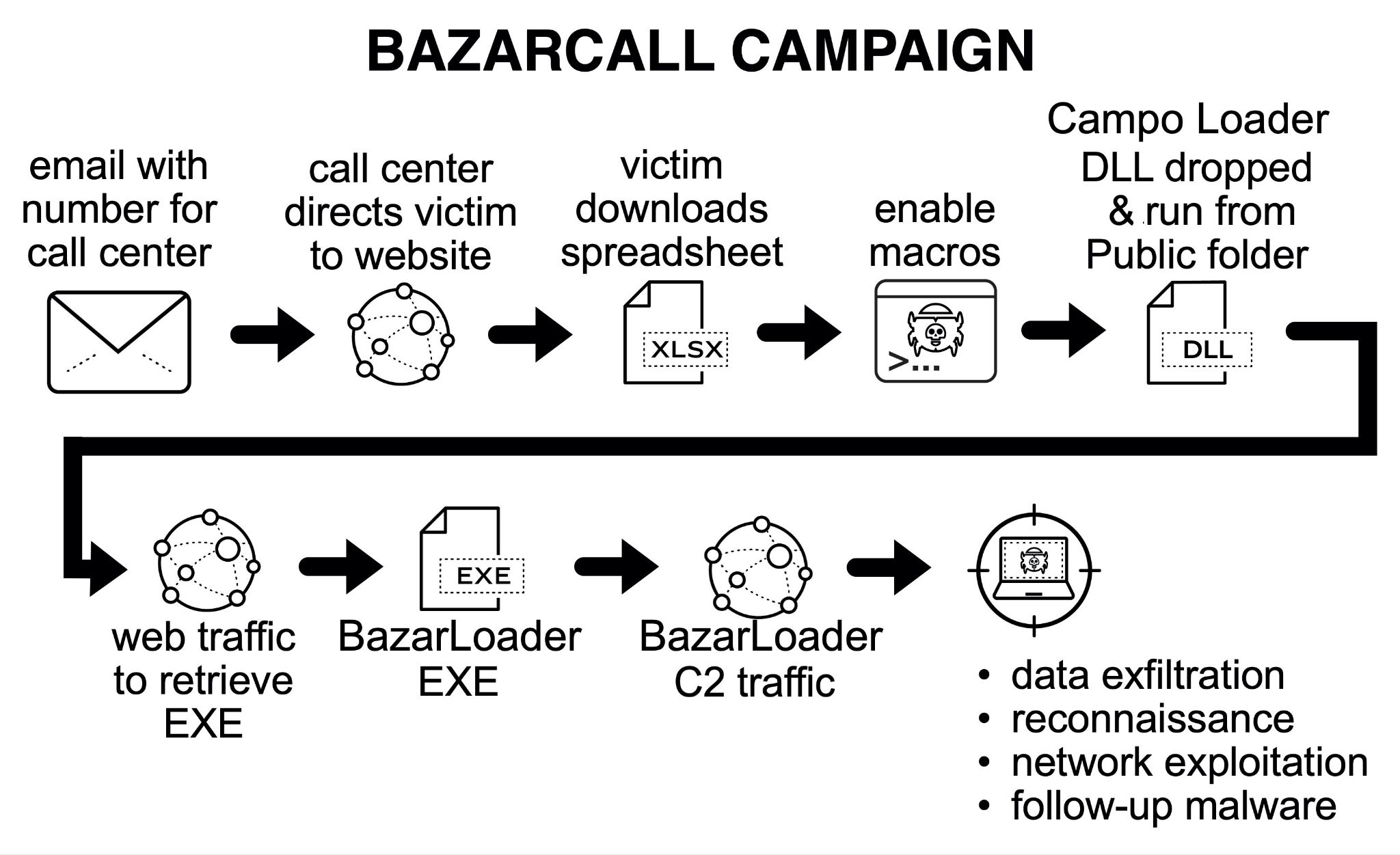
Tali eventi possono essere sintetizzati in queste fasi:
Il call center, contattato da Palo Alto Network (UNIT42), è apparentemente composto da persone di madrelingua inglese. Due degli operatori erano donne e tre erano uomini. Ogni operatore ha seguito lo stesso script di base, ma c’erano delle variazioni.
La seguente conversazione, riportata tramite un video YouTube riportato in calce, si è svolta mercoledì 14 aprile 2021 utilizzando un numero di telefono dall’e-mail mostrata di seguito nella Figura 2.
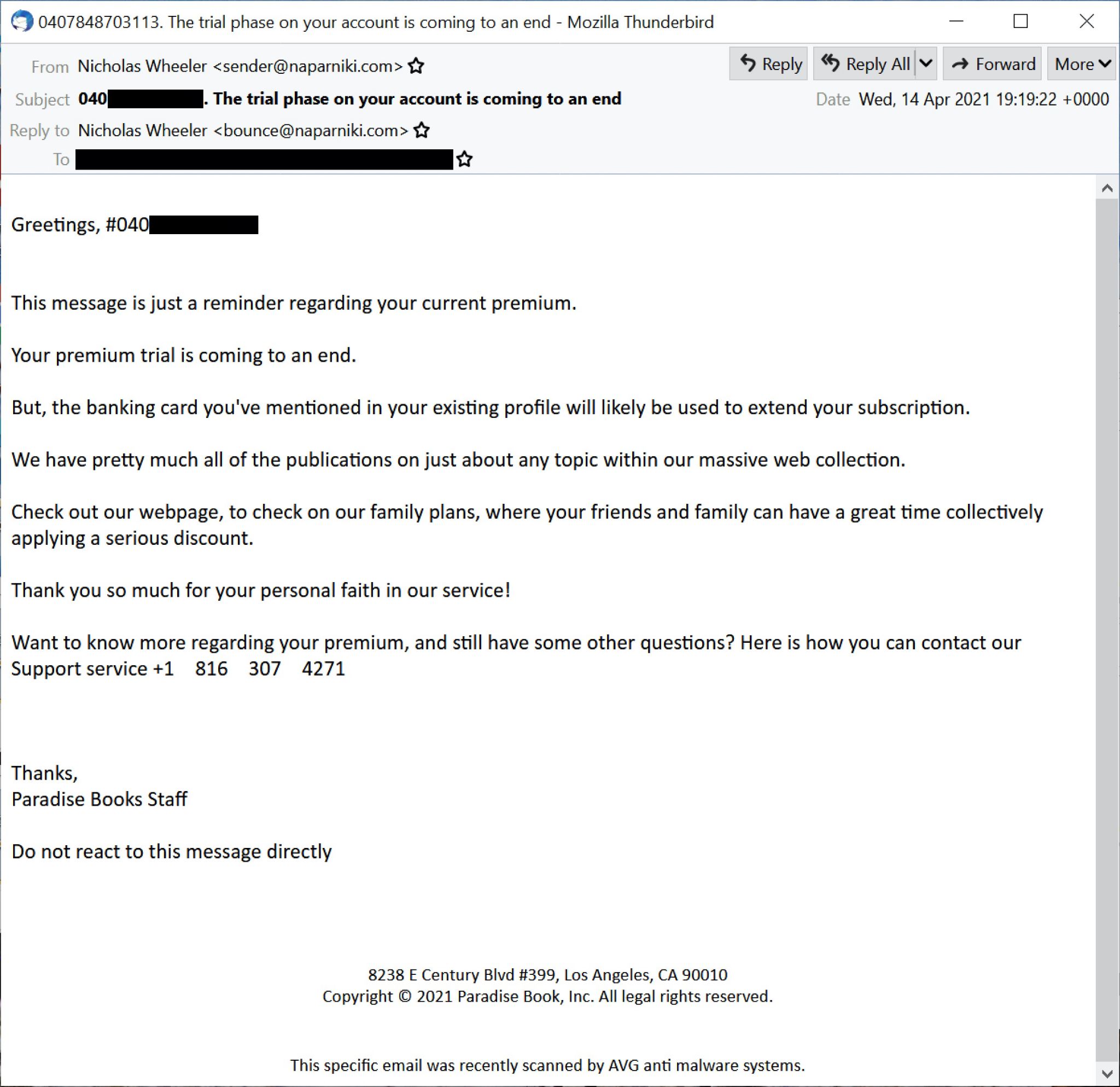
Operatore: servizio clienti. Come posso aiutarti?
Vittima: Salve. Oggi ho ricevuto un’e-mail da una società chiamata Paradise Books. Dice che ho un abbonamento e che verrà addebitato sulla mia carta di credito. Ma non ho mai avuto a che fare con Paradise Books. Non ricordo di aver fatto nulla o di essere andato su un sito Web per Paradise Books o qualcosa del genere.
Operatore: Va bene, signore. Hai un numero di abbonamento?
Vittima: Sì, aspetta. 040*********. [Nota: le ultime 9 cifre di questo numero non vengono visualizzate di proposito in quanto il numero identifica l’indirizzo e-mail del destinatario.]
Operatore: Ok, posso ripetertelo. 040*********.
Vittima: Sì.
Operatore: Aspetti un momento, mi faccia controllare sul nostro sistema.
Vittima: Va bene.
[musica di sottofondo]
Operatore: Pronto?
Vittima: Sì.
Operatore: Va bene. Sembra che questo account sia stato aperto da John Edwards, ma la tua email inizia con [nome della vittima] .
Vittima: Sì, sono [nome della vittima]. Non conosco nessun John Edwards.
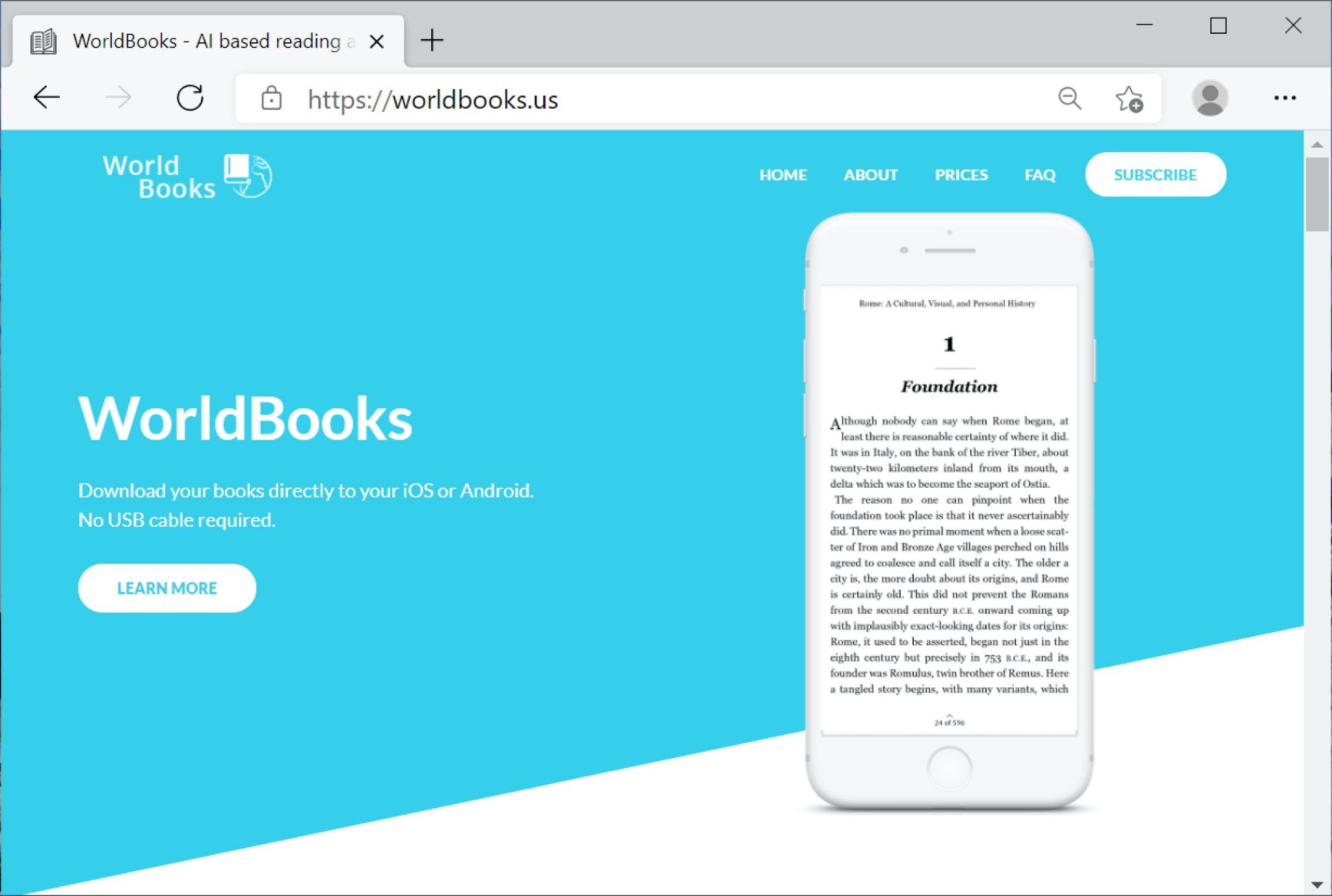
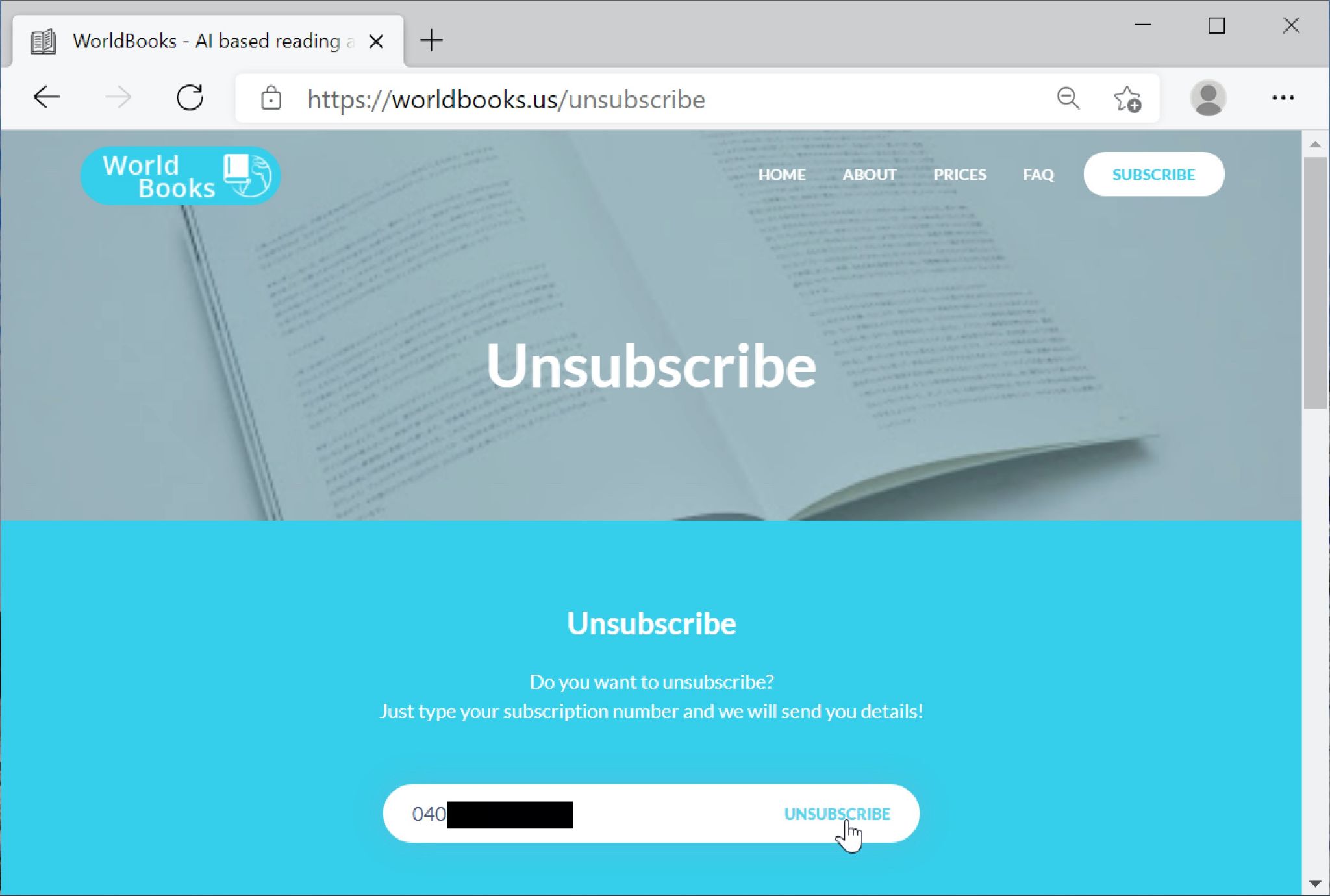
Operatore: Va bene, signore. Dobbiamo annullare l’abbonamento. Quindi quello che deve fare è andare su worldbooks.us.
Operatore: Worldbooks [indica ogni lettera foneticamente] punto US.
Vittima: Aspetta un secondo. Mi faccia accedere al sito web.
Operatore: Sì? Posso rileggerlo?
Vittima: No grazie. Ci sono. [suoni di battitura sulla tastiera]
Operatore: Pronto?
Vittima: Sì, aspetta. Sembra che stia caricando.
Operatore: Hai già visto il sito web?
Vittima: Va bene, ci sono. Non ho mai visto questo sito prima.
Operatore: Nessun problema. Possiamo semplicemente annullare l’abbonamento. Quello che ci serve è il tuo numero di abbonato che mi ha detto prima.
Vittima: Va bene.
Operatore: Riesce a vedere il pulsante di iscrizione?
Vittima: Sì.
Operatore: Quando fa clic su quello, dovrebbe essere in grado di vedere l’annullamento dell’iscrizione.
Vittima: Ok, sto facendo clic sul pulsante di iscrizione.
Operatore: Riesce a vedere l’annullamento dell’iscrizione?
Vittima: vedo una riga che dice “Vuoi annullare l’iscrizione?”
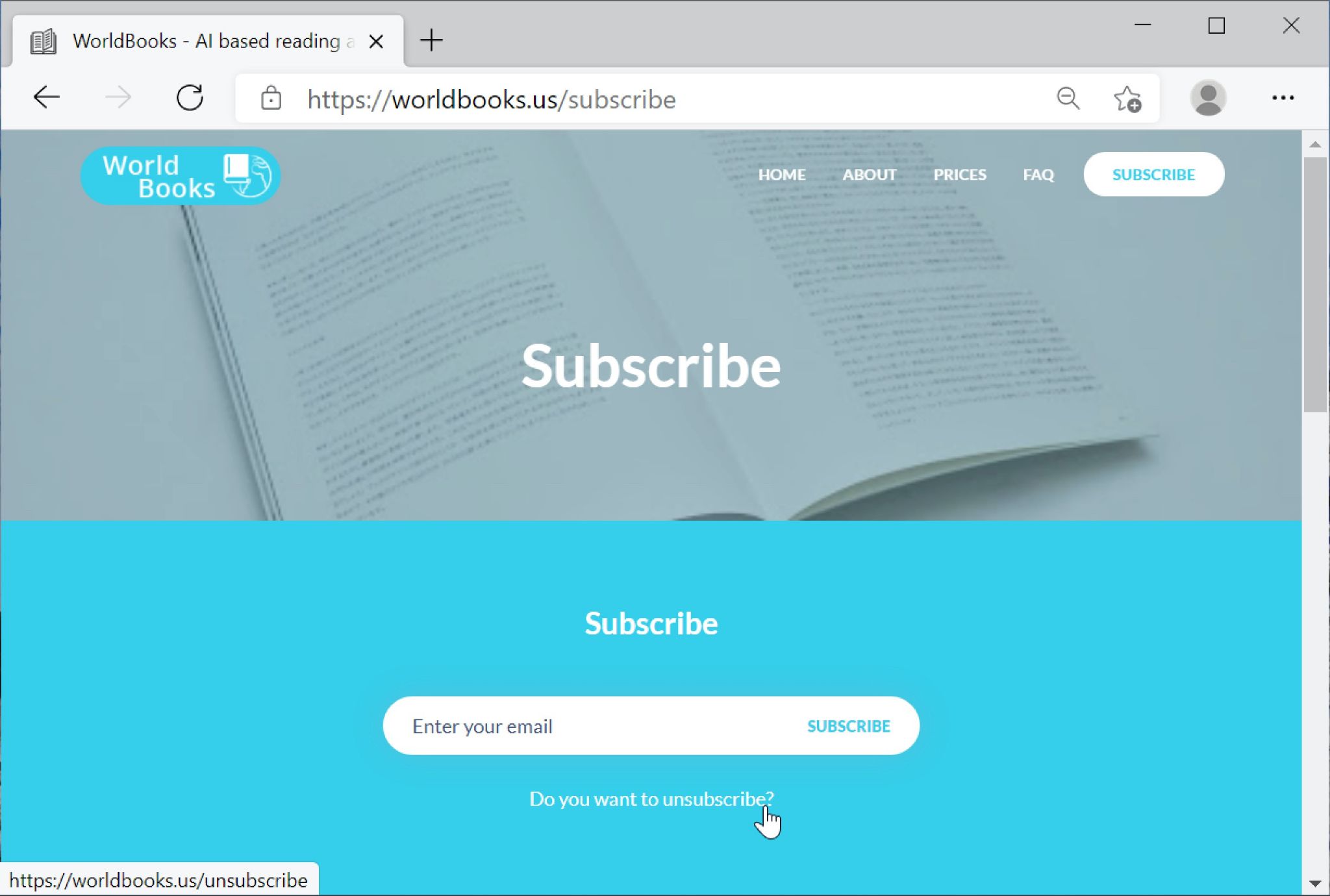
Operatore: È lì che deve andare. Ci deve cliccare sopra.
Vittima: Va bene.
Operatore: E poi inserisca il numero dell’abbonamento.
Vittima: Capito. [suoni di battitura sulla tastiera]
Operatore: Una volta fatto, riceverai un documento di conferma.
Vittima: Ok, mi sta chiedendo cosa voglio fare con l’abbonamento 16184. Mi dice di scaricare un file XLSB?

Operatore: Questo è il documento di conferma. È lì che ha il codice di conferma.
Vittima: Devo aprirlo? Devo salvarlo? Cosa devo fare?
Operatore: Puoi aprirlo, se hai bisogno del codice di conferma. Il codice di conferma è importante. In caso ci siano problemi, può chiamarci e darci il codice di conferma.
Vittima: Va bene.
Operatore: Quindi se vuole possiamo noi risolvere il problema.
Vittima: Capito. Bene.
Operatore: Hai capito?
Vittima: Va bene. Lo sto aprendo proprio ora. Vedo Excel Office 365. Mi dice che questo documento è protetto. L’anteprima non è disponibile per i documenti protetti. Devo premere abilita.
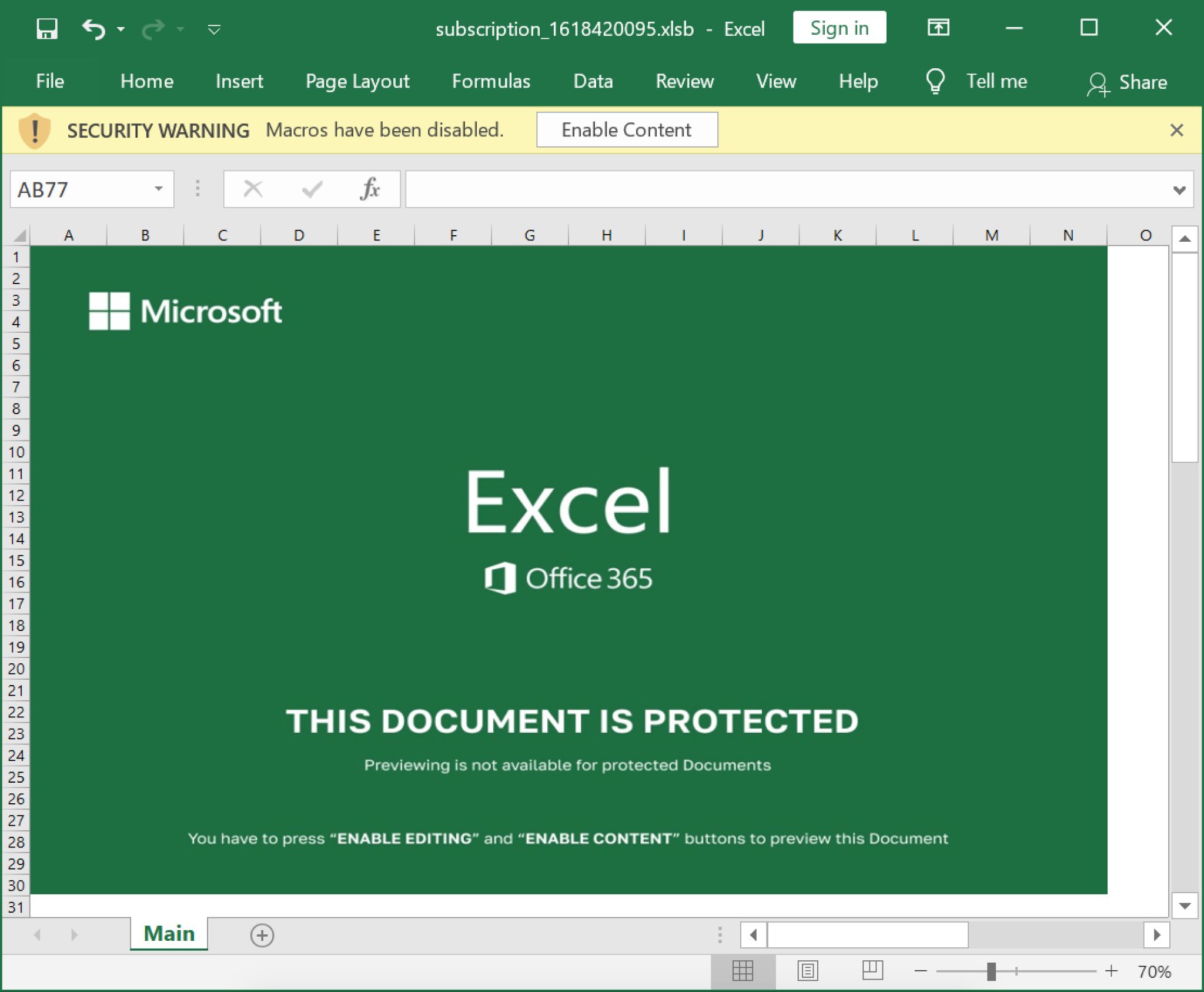
Operatore: faccia clic su modifica e abilitare il contenuto.
Vittima: Va bene. Va bene. Il foglio di calcolo è cambiato. Ora mostra un modulo con il nome dell’azienda, il nome, il cognome, la data di nascita e tutto il resto.
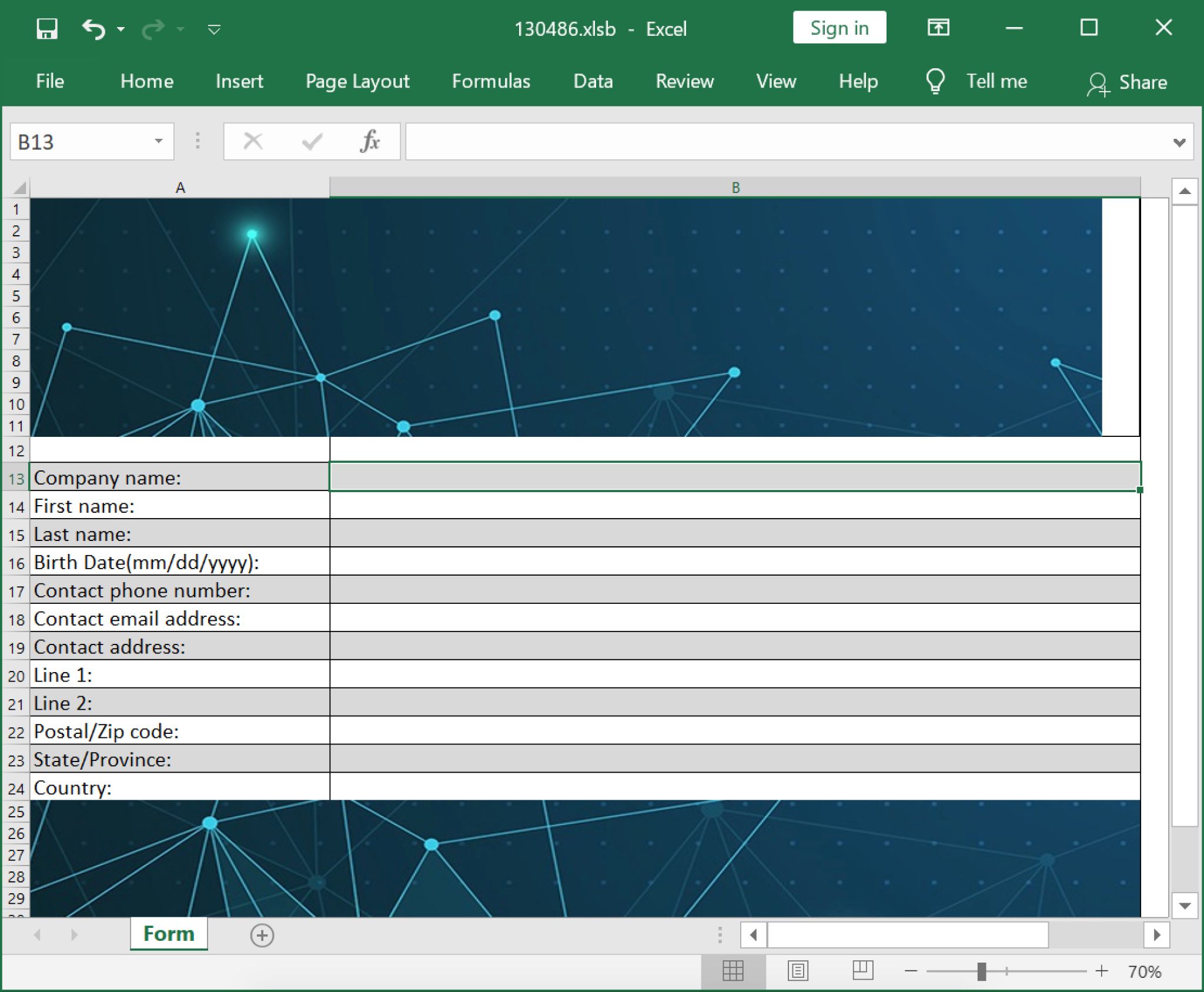
Operatore: Ok, riesce a vedere il codice? Il codice è quello importante.
Vittima: Non vedo un codice, no.
Operatore: Va bene. Ci sono diverse pagine. Riesce a vedere la prossima pagina?
Vittima: Dove dovrebbe essere questo codice?
Operatore: c’è un codice di conferma nel caso in cui non desideri ricevere un addebito, ma nel caso in cui ti venga addebitato, questo è ciò con cui ci chiami per annullare l’addebito.
Vittima: Ok, ancora non so dove dovrei trovare questo codice.
Operatore: Aspetta e fammi controllare con il dipartimento IT.
Vittima: Va bene.
[tieni la musica per circa 1 minuto]
Operatore: Salve signore.
Vittima: Sì.
Operatore: Ho verificato con il reparto IT e dicono che l’annullamento è andato a buon fine. Abbiamo solo un problema con i nostri server, ma la cancellazione è andata a buon fine.
Vittima: Va bene.
Operatore: Quindi nulla verrà addebitato sul suo account. E mi hanno dato un codice da parte loro. Posso leggerlo?
Vittima: Sì.
Operatore: il codice è [complica sette caratteri di un codice alfanumerico] .
Vittima: Va bene.
Operatore: In caso di problemi, puoi semplicemente richiamare e darci quel codice. Saremo in grado di risolvere qualsiasi problema.
Vittima: Va bene. Grazie.
Operatore: Prego, signore. E se richiama, può chiedere di [nome dell’operatore], perché ci sono molti miei colleghi.
[La vittima ripete il nome dell’operatore]
Operatore: Sì, è il mio nome.
Vittima: Va bene, grazie.
Operatore: Buona giornata.
Vittima: Arrivederci.
Operatore: Arrivederci signore.
Dopo che le macro sono state abilitate sul file Excel scaricato, la DLL BazarLoader viene eliminata e genera un URL contenente la stringa campo. Questo tipo di URL è chiamato Campo Loader , che funge da gateway che reindirizza il traffico al malware.
Alcuni esempi di URL generati da una DLL BazarLoader sono mostrati nella tabella successiva.
| Date | URL |
| 2021-03-25 | hxxp://whynt[.]xyz/campo/w/w |
| 2021-03-29 | hxxp://veso2[.]xyz/campo/r/r1 |
| 2021-03-31 | hxxp://about2[.]xyz/campo/a/a1 |
| 2021-04-07 | hxxp://basket2[.]xyz/campo/u/u1 |
| 2021-04-08 | hxxp://dance4[.]xyz/campo/d8/d9 |
| 2021-04-14 | hxxp://glass3[.]xyz/campo/gl/gl3 |
| 2021-04-15 | hxxp://idea5[.]xyz/campo/id/id8 |
| 2021-04-16 | hxxp://keep2[.]xyz/campo/jl/jl7 |
La figura 9 mostra una URL che reindirizza a un URL per BazarLoader.
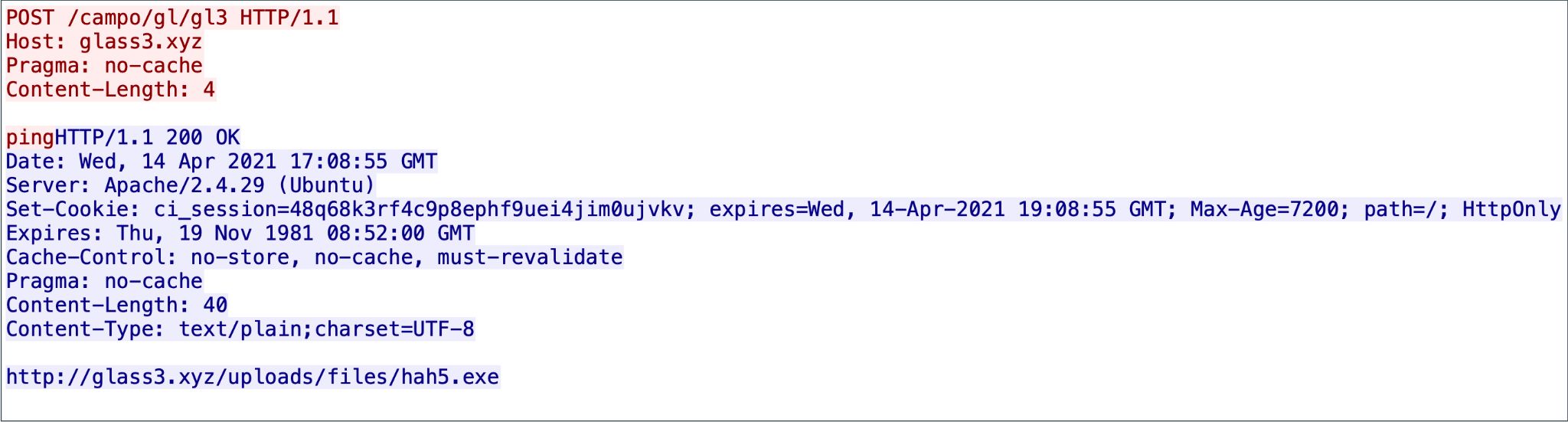
Esempi di URL recenti con eseguibili BazarLoader.
| Date | URL |
| 2021-03-25 | hxxp://whynt[.]xyz/uploads/files/dl8x64.exe |
| 2021-03-29 | hxxp://admin.yougleeindia[.]in/theme/js/plugins/o1e.exe |
| 2021-03-29 | hxxp://admin.yougleeindia[.]in/theme/js/plugins/rt3ret3.exe |
| 2021-03-31 | hxxp://about2[.]xyz/uploads/files/ret5er.exe |
| 2021-04-07 | hxxp://www.carsidecor[.]com/wp-content/uploads/2021/04/cv76.exe |
| 2021-04-08 | hxxp://dance4[.]xyz/uploads/files/10r3.exe |
| 2021-04-14 | hxxp://glass3[.]xyz/uploads/files/hah5.exe |
| 2021-04-15 | hxxp://idea5[.]xyz/uploads/files/ratan.exe |
| 2021-04-15 | hxxp://idea5[.]xyz/uploads/files/rets.exe |
| 2021-04-16 | hxxp://keep2[.]xyz/uploads/files/suka.exe |
L’eseguibile BazarLoader genera il traffico HTTPS C2 indicato di seguito nella Figura 10.
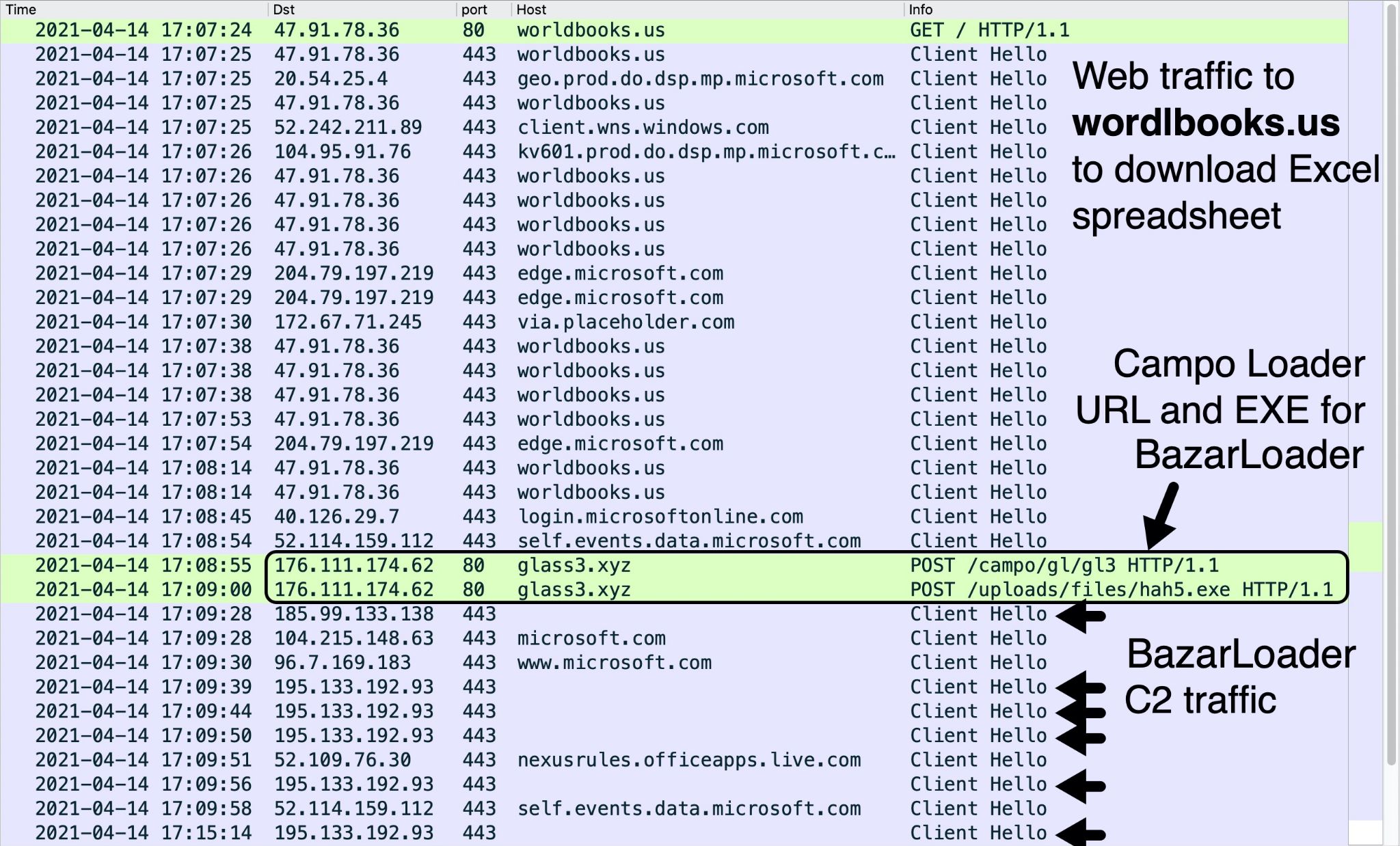
L’hash SHA256 per il foglio di calcolo Excel scaricato è:
db53f42e13d2685bd34dbc5c79fad637c9344e72e210ca05504420874e98c2a6
Le macro del file Excel scaricato crea artefatti nella directory C:\Users\Public del computer Windows, come mostrato nella Figura 11.
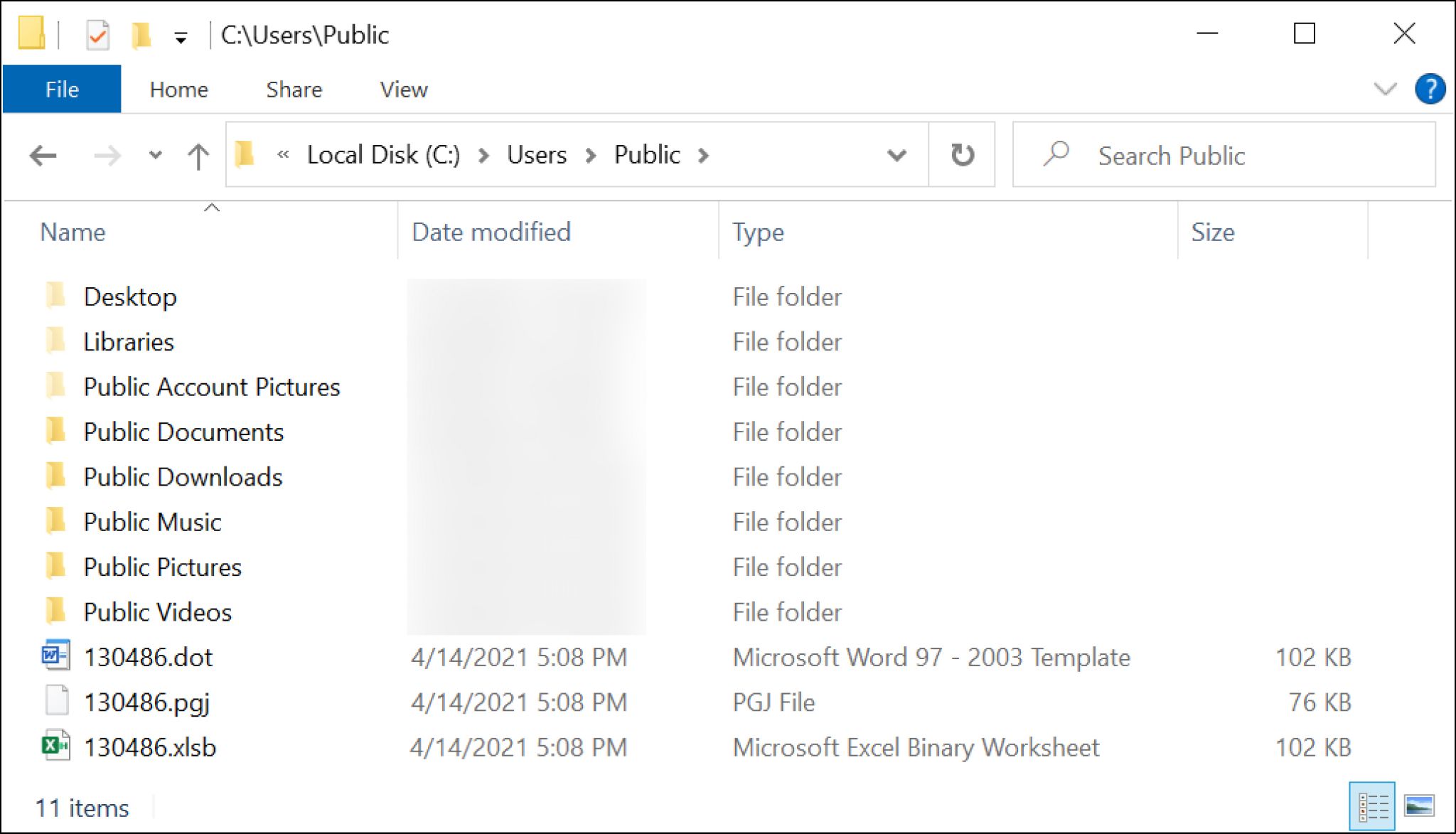
Le informazioni sui file sono mostrate di seguito nella Tabella 3. I primi due sono file di testo con lo stesso hash SHA256. L’altro file è una DLL BazarLoader.
| Nome del file | Tipo di file | hash SHA256 |
| 130486.xlsb | testo ASCII | 2632c0cc222a6d436b50a418605a7bd4fa8f363ab8d93d10b831cdb28a2ac1bc |
| 130486.punto | testo ASCII | 2632c0cc222a6d436b50a418605a7bd4fa8f363ab8d93d10b831cdb28a2ac1bc |
| 130486.pgj | DLL | f3b5cf1e40aed4567a8996cf107285907d432b4bc8cc3d0b46aae628813d82d4 |
Tabella 3. Artefatti da un foglio di calcolo BazarCall
130486.xlsb e 130486.dot sono costituiti da una stringa ASCII (American Standard Code For Information Interchange) con testo base64.
Questo testo rappresenta il file della libreria di collegamento dinamico (DLL) BazarLoader. Il codice macro dal file Excel scaricato converte il testo base64 in una DLL denominata 130486.pgj ed esegue questa DLL utilizzando i seguenti comandi di script:
Da tenere presente che questi file provengono da un esempio specifico. Gli artefatti generati da altri fogli di calcolo hanno nomi e estensioni ovviamente diversi. Le caratteristiche comuni includono:
La DLL è progettata per recuperare un EXE BazarLoader. Nell’esempio del 14 aprile 2021, BazarLoader EXE è stato salvato in una cartella nella directory C:\ProgramData, come mostrato di seguito nella Figura 12.
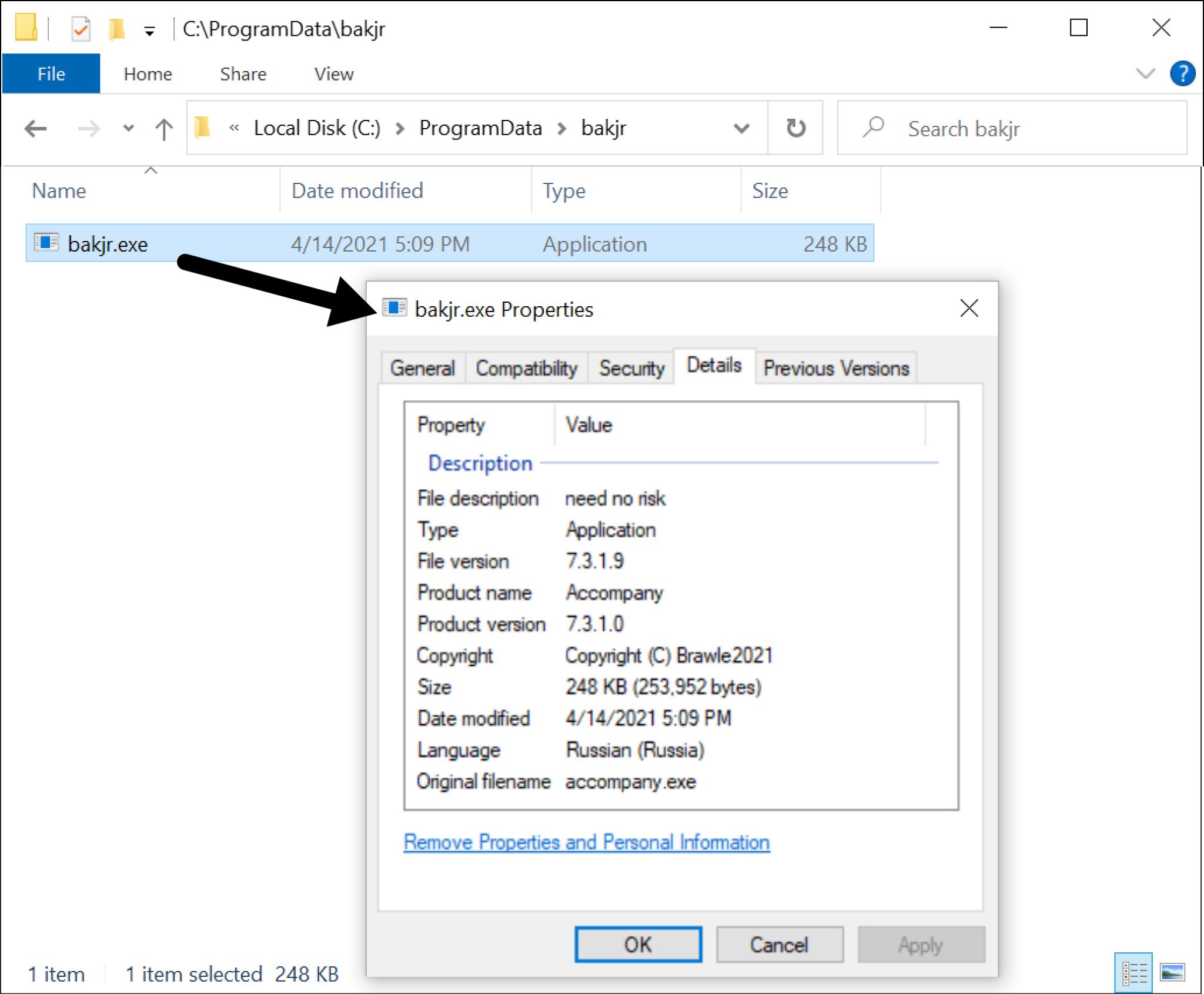
BazarLoader fornisce l’accesso backdoor a un host Windows infetto. In alcuni casi, Cobalt Strike è visto come un malware di follow-up, che porta ad altri malware come Anchor. Almeno due casi sono stati documentati pubblicamente in cui il malware BazarLoader ha distribuito Cobalt Strike e poi Anchor. Un caso si è verificato nel febbraio 2021 e l’altro nel marzo 2021.
Tuttavia, BazarLoader non si limita solo a Cobalt Strike e Anchor come malware di follow-up. Nel 2020 si sono viste segnalazioni di BazarLoader che hanno portato ad inoculare il ransomware Ryuk. L’accesso backdoor a un host Windows infetto potrebbe portare a qualsiasi famiglia di malware.
Già da febbraio 2021, si sono visti diversi rapporti sul metodo BazarCall che distribuisce nella sua fase finale il malware BazarLoader utilizzando il personale del call center. Queste infezioni seguono schemi evidenti e possono portare ad altri malware come Cobalt Strike, Anchor e Ryuk ransomware.
Le organizzazioni con filtri antispam decenti, una corretta amministrazione di sistema e host Windows aggiornati hanno un rischio molto inferiore di essere infettati dal malware BazarLoader e dalla sua attività post-infezione.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…