
The ransomware landscape continues to be characterized by dynamics of adaptation and resilience. Even when an international operation seems to spell the end for a criminal group, experience shows us that the disappearance is often only temporary.
This is the case of LockBit, one of the most prolific and structured gangs of the last five years, whose saga seemed to have ended with Operation Cronos in February 2024. Today, however, new evidence from the dark web is fueling speculation that it’s returning under a new guise: LockBit 5.0.
Over the years, LockBit has represented a benchmark for the criminal ecosystem, thanks to its Ransomware-as-a-Service (RaaS) approach, its widespread affiliate network, and constant innovation in encryption and propagation techniques. The introduction of data leak sites (DLS) as a pressure tool has made LockBit a true cybercrime icon.
With Operation Cronos, which culminated in the seizure of numerous infrastructures and the compromise of affiliated panels, the group seemed destined for definitive decline. However, as already analyzed in the previous article, residual traces of activity and signals scattered across the dark web suggested a possible reorganization.
In the last few hours, an image has emerged that seems to confirm this hypothesis: an authentication screen for a new DLS linked to the LockBit brand. Unlike traditional portals, which are freely accessible to maximize the coercive effect on victims, this new infrastructure requires the insertion of a private key to access its contents.
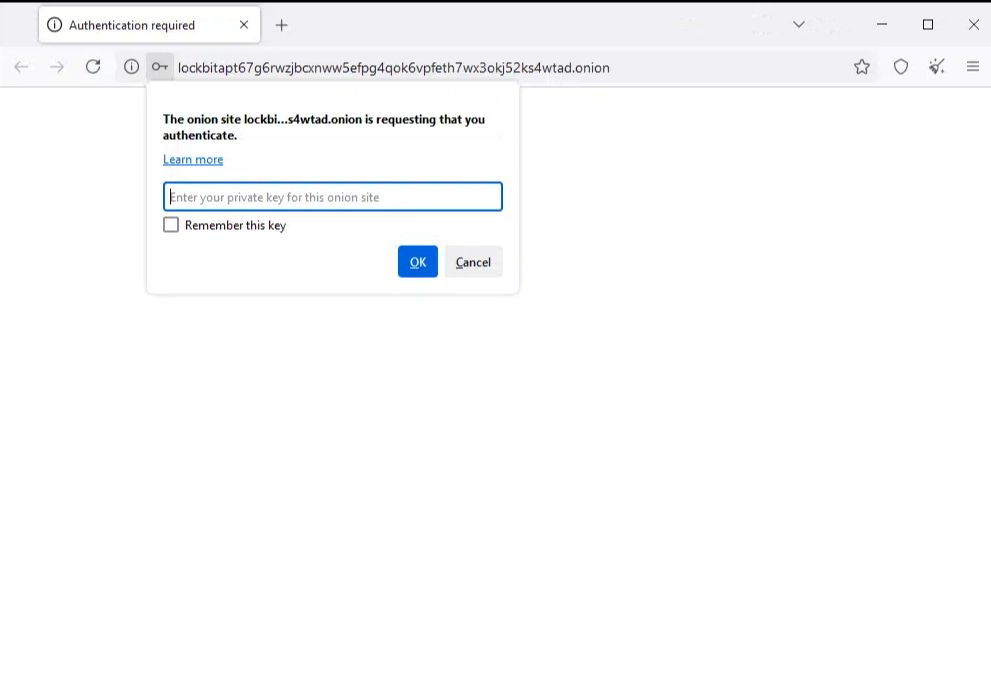
This choice introduces new elements and opens up different interpretative scenarios:
The resurgence of LockBit must be seen in the context of a broader evolution. Several ransomware groups are experimenting with new attack techniques, integrating automation, advanced evasion modules, and more aggressive double-extortion strategies.
In this context, the debate on the use of artificial intelligence as a disruptive factor is increasingly central. As also highlighted in the post by Anastasia Sentsova, the possibility of AI-orchestrated ransomware campaigns emerging in the future opens up scenarios in which targeting, lateral movement, and negotiation could be optimized in real time. In this sense, the potential rebirth of LockBit 5.0 could mark the beginning of a new experimental phase.
The leaked login screen from the new DLS, requesting a private key, isn’t just a technical detail, but a clue that raises a series of open questions:
At the moment, there are no definitive answers. However, one thing is certain: the void left by LockBit in the ransomware landscape is too large to remain so for long. If LockBit 5.0 were to prove itself, the industry could face a new turning point, with significant impacts on the tactics, techniques, and procedures of international cybercrime.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
