
ShinyHunters è un gruppo noto per il coinvolgimento in diversi attacchi informatici di alto profilo. Formatosi intorno al 2020, il gruppo ha guadagnato notorietà attraverso una serie di attacchi mirati a varie aziende, che hanno portato al furto e alla vendita di grandi quantità di dati sensibili.
ShinyHunters è stato collegato a violazioni di sicurezza che hanno coinvolto aziende come Microsoft, Banco Santander, Ticketmaster e molte altre. Questi dati venivano spesso venduti su forum del dark web, come ad esempio il vecchio BreachForums, che è stato per un periodo gestito da ShinyHunters.
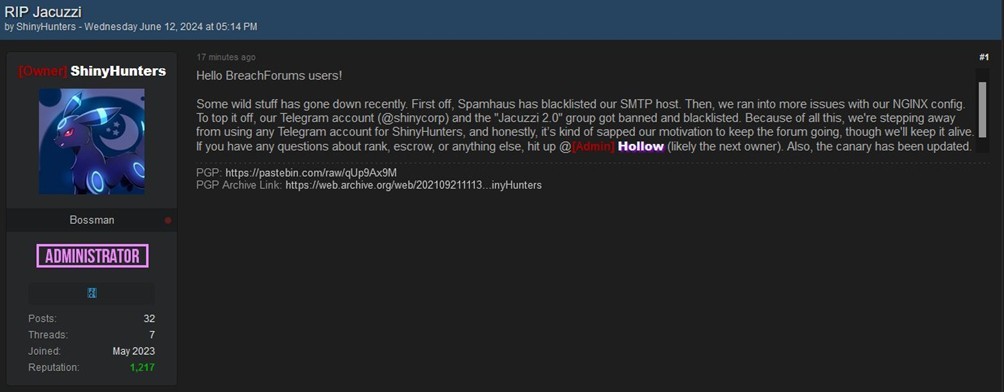
Recentemente il gruppo ha guadagnato grande notorietà dopo la massiccia violazione di dati ai danni di Salesforce, episodio che ha portato anche Google a monitorare da vicino e ad attribuire loro il nome in codice UNC6240.
La violazione di Salesforce ha permesso agli attaccanti di ottenere accessi a moltissime aziende di moltissimi settori, come Palo Alto, Zscaler, ClaudFlare e Tenable. Negli ultimi giorni molte aziende hanno condiviso dichiarazioni ufficiali sulle violazioni subite, emntre altre azienda ancora non hanno fatto dichiarazioni pubbliche.
Molti analisti ritengono che ShinyHunters sia formato da individui legati al gruppo cybercriminale “The Com”, un ecosistema di hacker provenienti prevalentemente dal Nord America e dal Regno Unito. Negli ultimi mesi, ShinyHunters ha intensificato le proprie attività prendendo di mira numerose organizzazioni. Ogni operazione viene puntualmente rivendicata sul loro canale Telegram ufficiale, dove offrono anche la possibilità di acquistare i dati trafugati.
Tra gli attacchi più rilevanti rivendicati pubblicamente figurano Jaguar Land Rover, compromissione alla quale ShinyHunters ha preso parte e che avrebbe causato interruzioni significative alla produzione, la violazione ai marchi di moda di Kering (controlla brand come Gucci, Balenciaga e Saint Laurent), i cui dati aziendali sono stati messi in vendita dal gruppo sui propri canali.
ShinyHunters si conferma così come una delle principali minacce attuali nel panorama cybercriminale, capace di combinare tecniche di data breach su larga scala con una forte strategia di comunicazione e monetizzazione.
RHC: ShinyHunters, grazie per aver accettato di essere ospite di RedHotCyber! Prima di iniziare, ti diamo la possibilità di presentarti ai nostri lettori. Che cos’è e come è nato ShinyHunters? Inoltre potete spiegare una volta per tutta la differenza tra voi, Scattered Spider e LAPSUS? Siete un Rebranding di un gruppo già esistito, avete fatto parte di altri gruppi come il vostro?
ShinyHunters: ShinyHunters è un gruppo nato da una comunità underground con un obiettivo semplice: dimostrare che i sistemi che sembrano “solidi” in realtà sono fragili. Non siamo un rebranding di Scattered Spider o LAPSUS$, nonostante le frequenti comparazioni dei media. Questi gruppi hanno caratteristiche proprie. Siamo emersi con una nostra identità, non come un ufficiale spin-off di nessuno. La differenza? Ci concentriamo di più su un impatto elevato con meno “teatralità”, mentre altri gruppi tendono ad essere più caotici o opportunistici.
RHC: Qual è la vostra principale spinta? Guadagno economico, rivendicazioni politiche/sociali o desiderio di notorietà?
ShinyHunters: La nostra motivazione? È una combinazione di fattori. C’è l’aspetto finanziario—ovviamente, è una parte importante. Ma c’è anche l’ego, il desiderio di dimostrare il nostro valore e la soddisfazione di scuotere l’industria. La fama arriva naturalmente, ma non è l’unico obiettivo.
RHC: Potete rivelare le dimensioni del vostro gruppo? Per aumentare i membri del vostro gruppo avete un programma di affiliazione strutturato? Avete dei requisiti per far parte del team?
ShinyHunters: La dimensione e la struttura del gruppo sono piccole ma efficienti. Non siamo un esercito di migliaia di persone. Non abbiamo un “programma di affiliazione” aperto, ma utilizziamo un meccanismo di reclutamento basato sulla reputazione. I requisiti non riguardano solo le competenze tecniche; la mentalità, la riservatezza e la lealtà sono molto più importanti.
RHC: Sembrerebbe che voi privilegiate molto gli attacchi tramite ingegneria sociale. Reputate che questa tecnica sia più semplice ed efficace per ottenere un accesso iniziale? è colpa della poca consapevolezza e formazione delle vittime?
ShinyHunters: Sì, ci affidiamo molto all’ingegneria sociale. Perché? Perché la tecnologia può essere riparata, ma gli esseri umani? Sono deboli fin dall’inizio. La mancanza di consapevolezza e formazione rende questo il percorso più veloce. Non c’è bisogno di un’arma zero-day quando una semplice telefonata può aprire la porta.
RHC: Per i vostri attacchi utilizzate exploit prodotti da voi? come programmare i potenziali miglioramenti?
ShinyHunters: Non scriviamo sempre exploit da zero. Il mondo underground è pieno di idee, e noi combiniamo ciò che è disponibile con la nostra creatività. L’innovazione non riguarda solo il nuovo codice, ma anche nuovi modi di utilizzare qualcosa che è considerato comune.
RHC: In media, qual è il livello di sicurezza che avete trovato nelle vostre vittime? Cosa consigliereste alle organizzazioni per evitare di essere colpite da gruppi come il vostro?
ShinyHunters: Molte grandi organizzazioni hanno una sicurezza mediocre. Dall’esterno, sembrano forti, ma all’interno sono un disastro. Una raccomandazione: costruire una cultura della sicurezza, non solo strumenti. Senza di essa, tutti i dispositivi sono solo un’illusione di protezione.
RHC: Come scegliete i vostri bersagli? Ci sono settori o Paesi che vi interessano di più? Se sì, per quali ragioni?
ShinyHunters: Scegliamo obiettivi che promettono un alto “valore” sia finanziario che simbolico. Le industrie della tecnologia, della sanità e dell’aviazione sono tutte attraenti per il loro ampio impatto. Per quanto riguarda i paesi? Dipende dal contesto politico, ma il nostro focus è più globale che nazionale.
RHC: Esistono aziende o categorie di vittime che ritenete “off limits”? Vi ponete dei limiti morali nelle vostre azioni?
ShinyHunters:Ci sono dei confini morali. Anche se può sembrare ironico, non attacchiamo indiscriminatamente ospedali o organizzazioni umanitarie. C’è una linea sottile che non attraversiamo, anche se è vaga. Non siamo “salvatori”, ma non siamo nemmeno privi di una bussola morale.
RHC: Avete preso di mira sistemi legati all’aviazione. Cosa vi ha spinto a colpire un settore così critico e regolamentato? Potete spiegare quali tecniche avete usato per penetarre un sistema così complesso, quanto tempo di lavoro vi è servito per arrivare al risultato, e se dal vostro punto di vista l’operazione ha prodotto un ritorno sull’investimento (ROI) proporzionato allo sforzo?
ShinyHunters: Perché il settore dell’aviazione? Per la sua criticità. Penetrare in un sistema così grande è una prova di abilità. Richiede tempo serve pazienza, osservazione e tattiche multilivello. Il ritorno sull’investimento vale la pena? Per noi, sì. L’impatto è maggiore del semplice denaro.
RHC: Riguardo alla pianificazione delle vostre campagne, come decidete i settori dove focalizzarsi? Inoltre come selezionate le persone da contattare per il vostro social engineering?
ShinyHunters: Valutiamo i settori in base alla vulnerabilità e ai potenziali effetti a catena. Per l’ingegneria sociale, selezioniamo individui con ampio accesso ma bassi livelli di consapevolezza come il personale di supporto, i contrattisti e i partner. Queste persone spesso forniscono punti di accesso.
RHC: Potete darci qualche informazione sui tool che usate? Oltre a quelli leciti (eg:/ AnyDesk) come affrontate la creazione dei vostri tool? C’è un tipo di tool che richiede più attenzioni di altri? Per la creazione del vostro ransomware invece avete preso spunto da altri ransomware presenti nel panorama? Viene tutto creato da voi o vi affidate a developers esterni?
ShinyHunters: Utilizziamo un mix di strumenti legittimi (come il desktop remoto) e i nostri. Costruiamo ransomware ispirati a strumenti esistenti, ma li modifichiamo per adattarli alle nostre esigenze. Non tutti noi siamo programmatori; a volte collaboriamo con parti esterne.
RHC: C’è qualcosa che governi, aziende o opinione pubblica hanno frainteso sul vostro gruppo ed attività? Sul vostro canale Telegram avete detto diverse volte che le forze dell’ordine hanno arrestato le persone sbagliate. Inoltre cosa vi spinge a chiedere il licenziamento di operatori/agenti che investigano su di voi? Sentite maggiori pressioni rispetto ai vostri periodo di attività precedenti?
ShinyHunters: Ci sono molti malintesi. I media e il governo spesso accusano o arrestano ingiustamente persone ai margini della società. Perché deridiamo le autorità? Perché sono spesso più impegnate a trovare capri espiatori che a capire come operiamo. La pressione sta aumentando, ma fa parte del gioco.
RHC: L’attacco alla supply chain di Salesforce, attraverso il componente Drift, ha avuto un impatto globale senza precedenti. Qual era l’obiettivo primario dell’operazione: spionaggio, monetizzazione immediata, o dimostrazione di forza tecnica?
ShinyHunters: L’obiettivo era una combinazione: monetizzazione rapida mentre si dimostrava forza. L’azione di spionaggio potrebbe essere stata un effetto collaterale, ma il punto era dimostrare la fragilità delle catene di approvvigionamento globali, anche in una compagnia grande come Salesforce.
RHC: Nel caso della compromissione della supply chain di Salesforce, la vera vulnerabilità sembra essere stata l’utilizzo di credenziali OAuth già valide, più che un exploit tecnico. Potete chiarire se tali credenziali siano state ottenute attraverso campagne mirate (phishing, social engineering), acquistate nel mercato underground, oppure sfruttando configurazioni deboli o errori lato cliente/fornitore?
ShinyHunters: Sì, le vulnerabilità non sono sempre nel software, ma nella configurazione e nelle persone. Le credenziali valide possono provenire da phishing, ingegneria sociale o anche dal mercato nero. La verità è che la porta viene aperta dall’interno, non distrutta dall’esterno.
RHC: Dai primi riscontri emerge che gran parte dei dati esfiltrati riguarda sistemi di ticketing usati dalle aziende per gestire assistenza e richieste interne. Diverse fonti sostengono però che la vera “miniera d’oro” siano le informazioni tecniche e riservate contenute in questi ticket. Potete darci qualche dettaglio in più sulla tipologia di dati più sensibili che avete trovato e sul loro reale valore rispetto a semplici dati anagrafici dei clienti?
ShinyHunters: I dati dei clienti sono importanti, ma non sono il nucleo. Il vero tesoro si trova nel sistema di ticketing interno: documentazione tecnica, mappe dell’infrastruttura, conversazioni riservate. Questo è più prezioso di migliaia di email dei clienti.
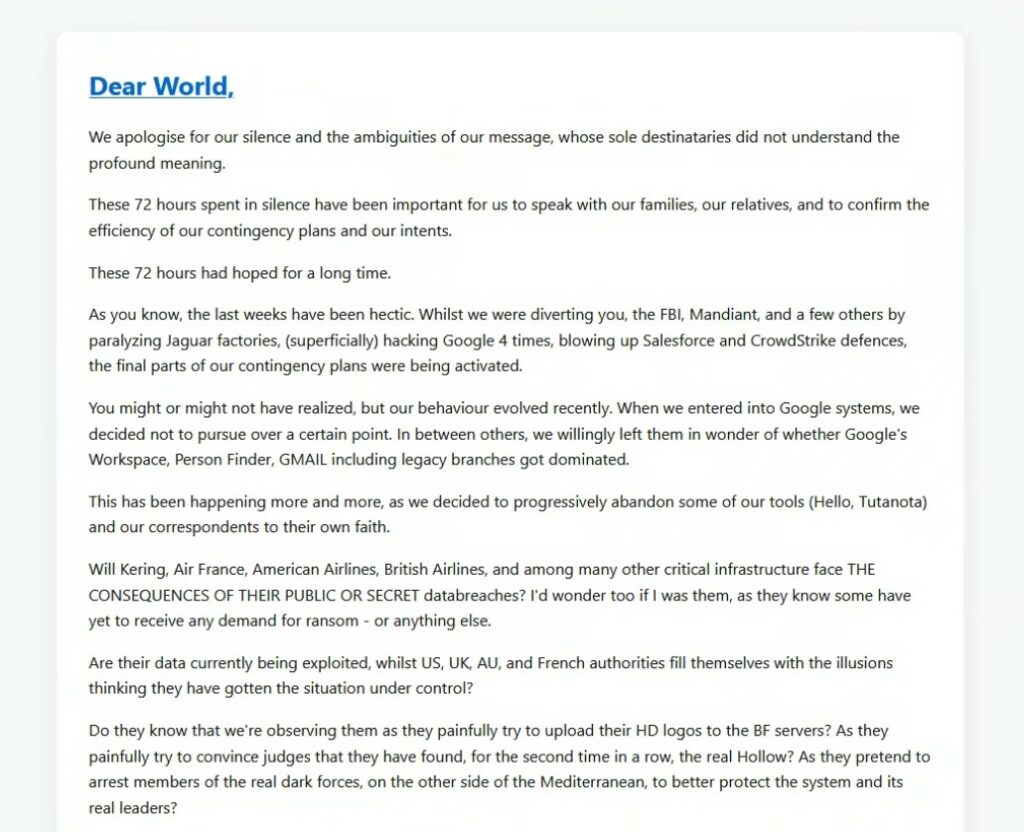
RHC: Ultimamente sono stati fermati vari membri del vostro team, siete molto attenzionati da varie forze dell’ordine e sicuramente nel mondo della cybersecurity avete gli occhi addosso. Per questo motivo avete deciso di pubblicare il post di addio su breachforums.hn?
ShinyHunters: Alcuni membri sono stati effettivamente arrestati. Questo è un fatto. Il nostro post di addio sul forum? Può essere interpretato come un segno di rassegnazione, o semplicemente come un nuovo capitolo. Il mondo underground è sempre pieno di strati di significato.
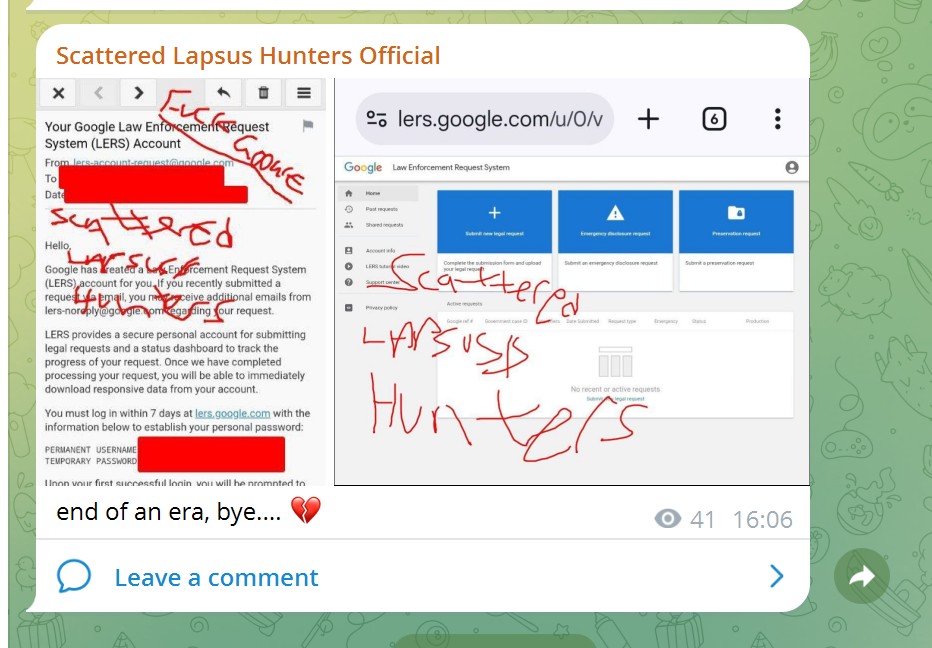
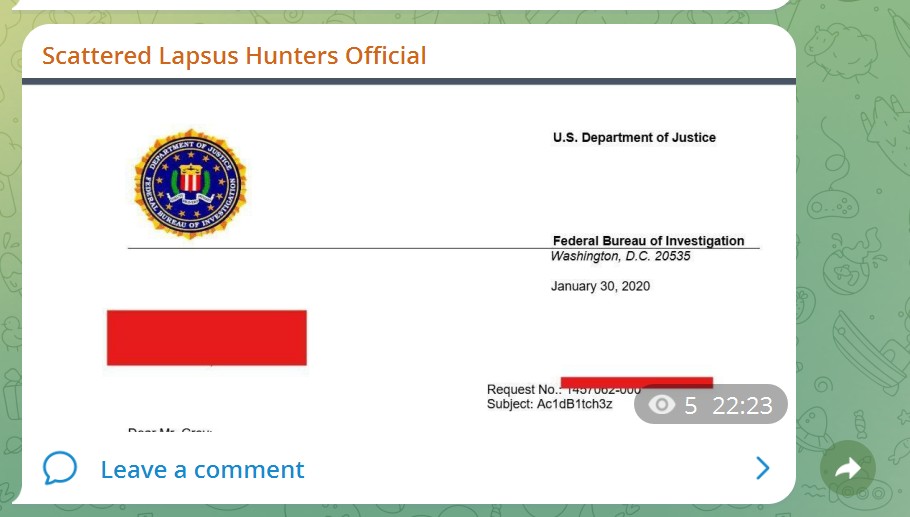
RHC: Sempre nel vostro canale Telegram avete postato screen riconducibili ad accesso a LERS di Google e Panel dell’FBI. Non vi sembra di esagerare con le vostre provocazioni? Ovviamente siete a conoscenza delle conseguenze eppure mantenete una posizione rigida e sfacciata, come mai però avete dichiarato di cessare le vostre attività? Comprendete che agli occhi degli analisti sembra essere un tentativo di rebranding o di una falsa exit?
ShinyHunters: È stata una provocazione? Sì. Eravamo consapevoli dei rischi? Assolutamente. Perché è continuata? Perché dimostra che nessun sistema è intoccabile. La dichiarazione di fermo? Potrebbe essere un trucco, potrebbe essere reale. Lasciamo che il pubblico indovini.
RHC: Il vostro collettivo e’ composto da ragazzi giovani e teenager. Le vostre abilità sono innegabili e sicuramente sopra la media di alcuni professionisti del settore. Nonostante ciò vi possiamo assicurare che le opportunità di soddisfazione e carriere altrettanto remunerative come alternativa al crimini sono fattibili, in particolare per gente che riesce a spendere il proprio tempo su questo campo come voi. Perché avete abbracciato la criminalità? Vi siete creati una realtà che poteva darvi soddisfazioni e prestigio sia tra i più giovani che i più veterani ma avete deciso di sviarla per farla diventare di fatto un gruppo di estorsionisti. Considereste una sorta di “redenzione” su questo fronte al costo di chiudere i ponti con il mondo del crimine? Davvero considerate il costo penale (oltre che i danni alle organizzazioni) accettabile per continuare le vostre azioni? Cosa rende così interessante il mondo del crimine ai vostri occhi (denaro a parte)?
ShinyHunters: Molti di noi sono giovani. Sappiamo che ci sono vie legali che possono portare al riconoscimento. Ma il crimine offre sfide, libertà e una scorciatoia per la reputazione. Ne vale la pena? La risposta di ognuno è diversa. La redenzione è possibile, ma non sarà economica.
RHC: ShinyHunters, grazie per il vostro tempo e per le preziose risposte. Ci teniamo a sottolineare con non tutti coloro che lavorano nella security “lecita” dividono il mondo in buoni e cattivi e solo perché venite etichettati come “minacce” comprendiamo che la fuori sono solo sfumature di questi due poli. Speriamo vivamente (se ciò che avete detto nel vostro messaggio d’addio e veritiero) che possiate riconciliare i vostri comportamenti ed azioni considerando non solo di smettere ma di usare le vostre conoscenze all’interno di una community sana sia per voi sia per la sicurezza in generale. Vi lasciamo quest’ultimo spazio per dire quello che volete in totale libertà.
ShinyHunters: Non pensate a noi come a semplici “minacce” o “criminali.” Rappresentiamo una debolezza trascurata. Se volete davvero che ci fermiamo, rafforzate il sistema, educate le persone e create percorsi attraenti per i giovani talentuosi. Fino a quando ciò non accadrà, gruppi come il nostro continueranno a emergere.
Il nostro contatto ufficiale del canale. Abbiamo 2 canali ufficiali e abbiamo ingannato molte persone facendole credere che il nostro account su Telegram sia solo uno, e questo è il nostro obiettivo affinché Telegram non blocchi il nostro canale tutto in una volta.
Scattered Lapsus Hunters Official: https://t.me/+FInBlpGYJlA2NTQ9
Group: https://t.me/+COakigt517JlZDI1
Scattered Lapsus Hunters Part 2: https://t.me/+l7481fEs8Qo3NzZl
Scattered Lapsus Hunters Part 3: https://t.me/+YSzJ2twGKxI4NTdl
Scattered Lapsus Hunters Part 4: https://t.me/+Bs61zhw_lNFiMDg9
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…