
Negli ultimi mesi, il gruppo di hacker cinese conosciuto come Salt Typhoon ha continuato a far parlare di sé grazie alle sue tattiche aggressive e persistenti nel settore della cybersicurezza.
Nonostante le sanzioni imposte dagli Stati Uniti e un’attenta sorveglianza governativa, Salt Typhoon ha dimostrato di non rallentare le proprie attività, continuando a lanciare attacchi coordinati contro istituzioni educative e infrastrutture critiche a livello globale.
Recenti rapporti indicano che il gruppo ha mirato a diversi fornitori di telecomunicazioni e università in vari paesi, principalmente Stati Uniti, Regno Unito, Sudafrica. Queste incursioni hanno permesso agli hacker di compromettere dispositivi cruciali, estraendo informazioni sensibili come dati scientifici e tecnologia proprietaria.
Da quanto viene riportato dalle dashboard della piattaforma di intelligence di Recorded Future (Partner strategico di Red Hot Cyber), gli attacchi hanno iniziato ad aumentare in modo sensibile da febbraio di questo anni con dei picchi nelle date del 13 e del 21 di questo mese.
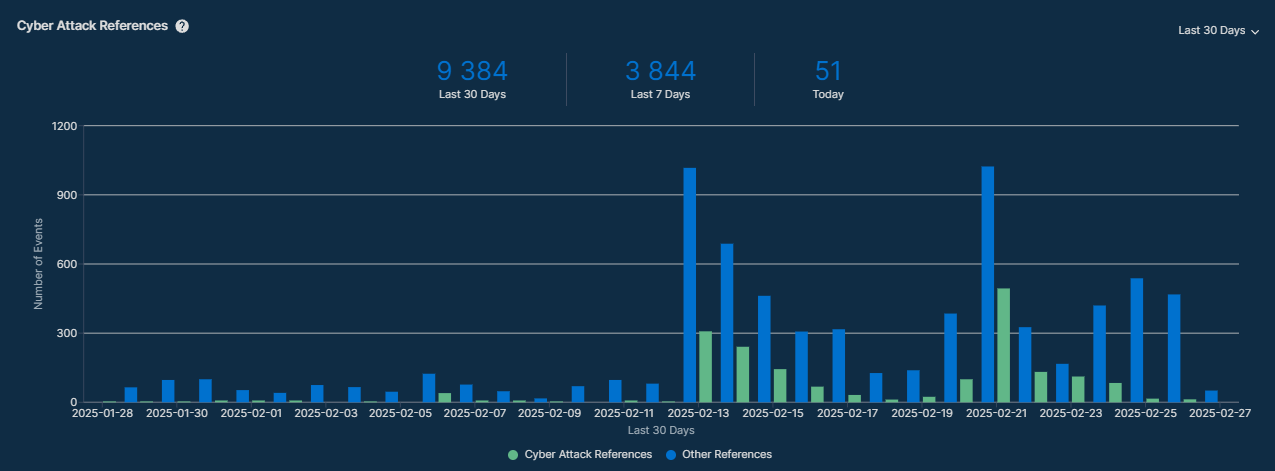
Dall’inizio di dicembre 2024, Salt Typhoon (RedMike) ha tentato di sfruttare oltre 1.000 dispositivi di rete Cisco esposti su Internet in tutto il mondo, principalmente quelli associati ai provider di telecomunicazioni, utilizzando una combinazione di due vulnerabilità di escalation dei privilegi: CVE-2023-20198 e CVE-2023-20273. Una volta compromesso con successo, il gruppo utilizza il nuovo account utente privilegiato per modificare la configurazione del dispositivo e aggiunge un tunnel GRE per l’accesso persistente e l’esfiltrazione dei dati.
La vulnerabilità di escalation dei privilegi CVE-2023-20198 è stata trovata nella funzionalità Web UI del software Cisco IOS XE, versione 16 e precedenti, e pubblicata da Cisco nell’ottobre 2023. Gli aggressori sfruttano questa vulnerabilità per ottenere l’accesso iniziale al dispositivo ed emettono un comando privilege 15 per creare un utente locale e una password. In seguito, l’aggressore utilizza il nuovo account locale per accedere al dispositivo e sfrutta una vulnerabilità di escalation dei privilegi associata, CVE-2023-20273, per ottenere i privilegi di utente root.
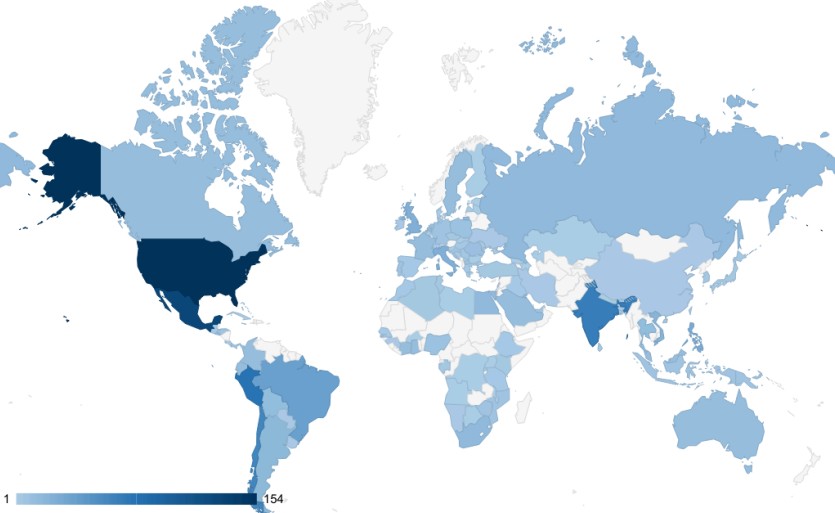
Oltre la metà dei dispositivi Cisco presi di mira da RedMike si trovavano negli Stati Uniti, in Sud America e in India. I dispositivi rimanenti si estendevano su oltre 100 altri paesi. Sebbene i dispositivi selezionati siano principalmente associati a provider di telecomunicazioni, tredici erano collegati a università in Argentina, Bangladesh, Indonesia, Malesia, Messico, Paesi Bassi, Thailandia, Stati Uniti e Vietnam.
Tale comportamento mette in evidenza la minaccia continua rappresentata dagli attori sponsorizzati dagli stati e la loro capacità di compromettere la sicurezza nazionale. Particolarmente preoccupante è la strategia di Salt Typhoon di sfruttare vulnerabilità nei dispositivi Cisco.
La Cina ha sviluppato un’ampia rete di operazioni di spionaggio informatico mirate a istituzioni accademiche, aziende e governi stranieri, con l’obiettivo di ottenere vantaggi strategici in settori chiave come l’intelligenza artificiale, la crittografia e la tecnologia quantistica. Gruppi di hacker sponsorizzati dallo Stato, come Brass Typhoon APT41 e Violet Typhoon APT31, sono stati collegati a campagne di attacco sofisticate che sfruttano vulnerabilità nei sistemi informatici di università e centri di ricerca per esfiltrare dati sensibili. Queste operazioni non si limitano al cyberspazio, ma coinvolgono anche il reclutamento di ricercatori e studenti stranieri attraverso programmi di scambio accademico e collaborazioni scientifiche, che spesso fungono da copertura per il trasferimento illecito di conoscenze.
Parallelamente, il governo cinese utilizza società di copertura e joint venture con istituzioni occidentali per acquisire tecnologie emergenti senza destare sospetti. Attraverso iniziative come il programma “Thousand Talents”, Pechino ha incentivato il rientro di scienziati e ingegneri cinesi dall’estero, spesso con informazioni e brevetti ottenuti illegalmente.
Inoltre, le cyber-operazioni cinesi hanno preso di mira fornitori di infrastrutture critiche, tra cui aziende di telecomunicazioni e contractor della difesa, con l’intento di compromettere la sicurezza delle comunicazioni e raccogliere dati di intelligence strategici. Queste attività, sempre più sofisticate, come quelle di Salt Typhoon (RedMike), hanno portato a crescenti tensioni tra la Cina e le potenze occidentali, con sanzioni e misure di ritorsione da parte di Stati Uniti ed Europa per contrastare l’aggressiva espansione dello spionaggio informatico cinese.
Il 15 febbraio 2025, Salt Typhoon ha sferrato moltissimi attacchi che hanno colpito 13 università e cinque fornitori di servizi Internet, inclusi quelli in Italia. Queste aggressioni segnano un notevole incremento della campagna di Salt Typhoon, considerata una delle più grandi operazioni di cyber-spionaggio condotte dalla Cina contro gli Stati Uniti. Le conseguenze di questi attacchi non si limitano a violazioni immediate dei dati, ma pongono interrogativi sugli impatti a lungo termine sulla ricerca accademica e sull’innovazione tecnologica.
E’ stata violata con successo un’affiliata statunitense di una società di telecomunicazioni del Regno Unito, vari provider di servizi Internet (ISP) e 13 università, tra cui importanti istituzioni come l’UCLA. Nel corso del mese di febbraio, Cisco ha confermato che questa falla è stata utilizzata per colpire le reti di telecomunicazione statunitensi, dimostrando la persistenza del gruppo nell’utilizzare sia le vulnerabilità consolidate che quelle più recenti per mantenere l’accesso ai sistemi compromessi.
Gli attacchi non si sono limitati agli Stati Uniti, ma si sono estesi anche a entità internazionali, tra cui ISP in Italia, Sudafrica e Thailandia. L’ampiezza di questi attacchi ha destato notevoli preoccupazioni per quanto riguarda la sicurezza dei dati sensibili e l’integrità delle infrastrutture di telecomunicazione su scala globale.
In generale le attività malevole di Salt Typhoon (Red Mike) hanno sfruttato le vulnerabilità identificate come CVE-2023-20198 e CVE-2023-20273, che hanno facilitato l’accesso non autorizzato ai router Cisco IOS XE. Ciò ha permesso agli aggressori di manipolare i dispositivi di rete e potenzialmente di esfiltrare dati sensibili.
Salt Typhoon (RedMike) dopo aver avuto accesso e compromesso i router CISCO, impiega una serie di sofisticati malware per infiltrarsi e compromettere le reti in vari settori.
Uno degli strumenti principali del loro arsenale è una versione personalizzata del MASOL RAT (Remote Access Trojan), che consente agli aggressori di ottenere il controllo remoto dei sistemi infetti.
Questo malware è particolarmente efficace nell’esfiltrazione di dati sensibili, nel monitoraggio delle attività degli utenti e nell’esecuzione di comandi sulle macchine compromesse. L’uso del MASOL RAT evidenzia l’attenzione strategica di Salt Typhoon per la furtività e la persistenza, che gli consentono di mantenere l’accesso a lungo termine alle reti mirate senza essere individuati.
MASOL RAT, tracciato da TrendMicro dal 2020 può essere utilizzato per prendere di mira entità governative del sud-est asiatico. In base alla stringa PDB della backdoor (E:\Masol_https190228\x64\Release\Masol.pdb), si ritiene che il Remote Access Trojan possa essere stata sviluppato già nel 2019. E’ stata osservata anche una nuova variante Linux in circolazione dopo il 2021.
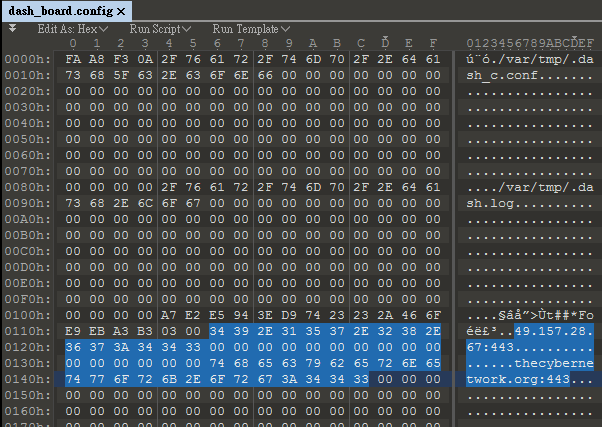
In un rapporto pubblicato da Cisco Talos il 20 febbraio, i ricercatori hanno confermato che Salt Typhoon ha ottenuto l’accesso all’infrastruttura di rete principale tramite dispositivi Cisco e ha poi utilizzato tale infrastruttura per raccogliere una serie di informazioni.
L’approccio di Salt Typhoon per ottenere l’accesso iniziale ai dispositivi Cisco è quello di ottenere le credenziali di accesso legittime della vittima utilizzando tecniche LOTL (Living-off-the-Land) sui dispositivi di rete.
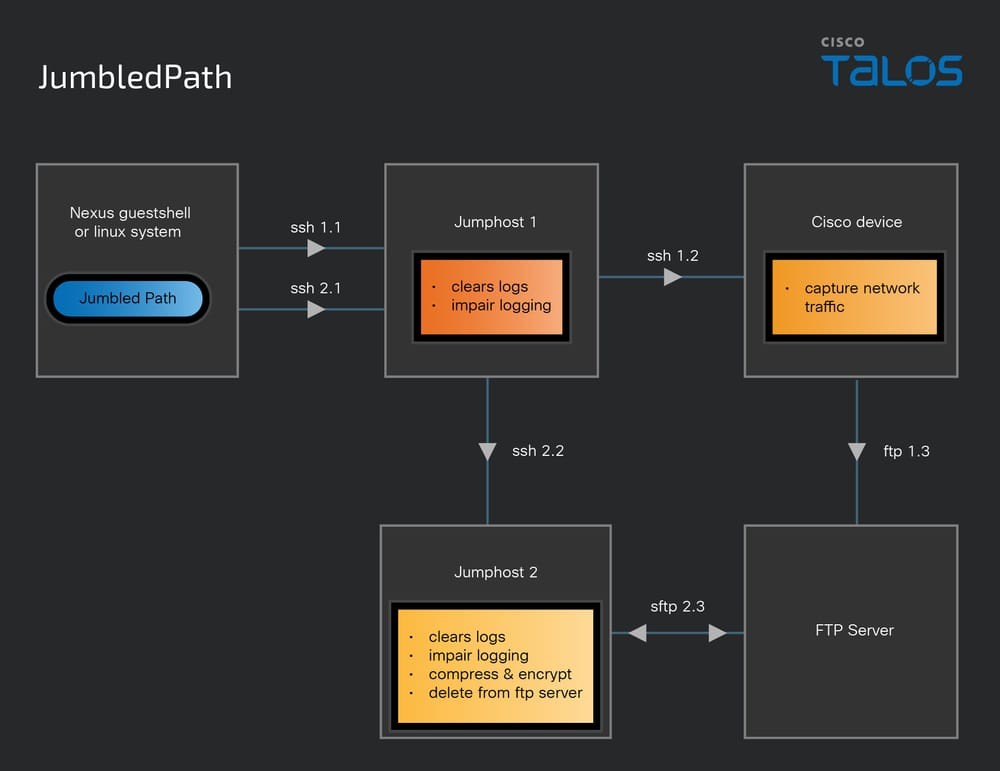
Salt Typhoon (RedMike) ha utilizzato un’utilità personalizzata, denominata JumbledPath, che gli ha consentito di eseguire un’acquisizione di pacchetti su un dispositivo Cisco remoto tramite un jump-host definito dall’attore. Questo strumento ha anche tentato di cancellare i log e compromettere la registrazione lungo il jump-path e restituire l’acquisizione compressa e crittografata risultante tramite un’altra serie unica di connessioni o jump definiti dall’attore.
Ciò ha consentito all’attore della minaccia di creare una catena di connessioni ed eseguire l’acquisizione su un dispositivo remoto. L’utilizzo di questa utilità contribuirebbe a offuscare la fonte originale e la destinazione finale della richiesta e consentirebbe inoltre al suo operatore di muoversi attraverso dispositivi o infrastrutture potenzialmente altrimenti non raggiungibili pubblicamente (o instradabili).
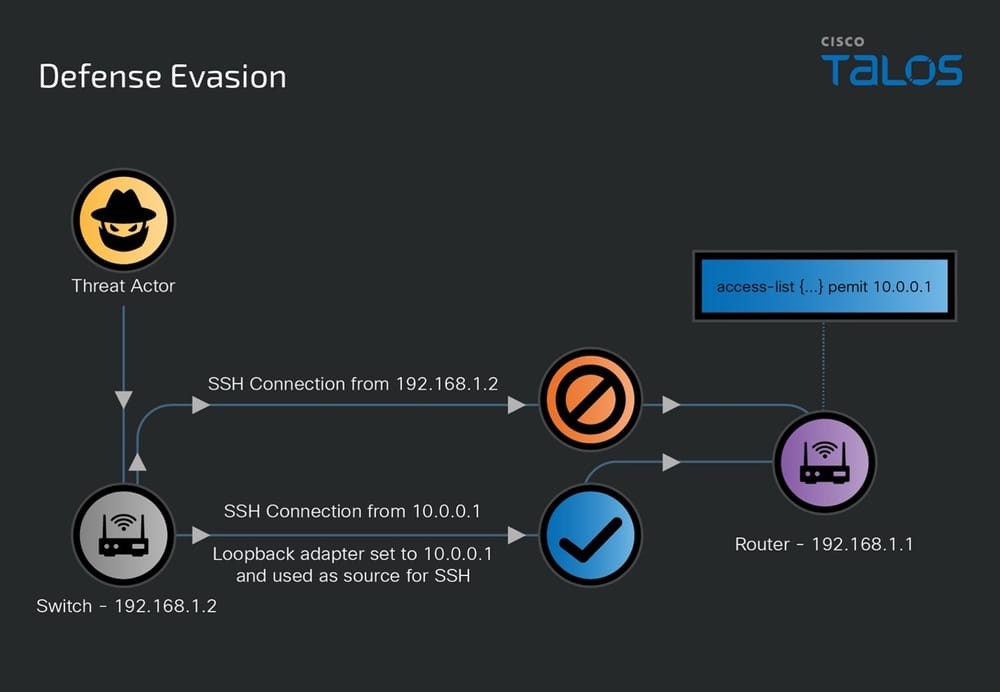
Questa utility è stata scritta in GO e compilata come binario ELF usando un’architettura x86-64. La compilazione dell’utility usando questa architettura la rende ampiamente utilizzabile su sistemi operativi Linux, che includono anche una varietà di dispositivi di rete multi-vendor. Questa utility è stata trovata in istanze Guestshell configurate dall’attore su dispositivi Cisco Nexus.
L’autore della minaccia ha modificato ripetutamente l’indirizzo dell’interfaccia loopback su uno switch compromesso e ha utilizzato tale interfaccia come origine di connessioni SSH ad altri dispositivi all’interno dell’ambiente di destinazione, il che gli ha consentito di aggirare di fatto gli elenchi di controllo di accesso (ACL) in vigore su tali dispositivi.
Salt Typhoon (RedMike), spesso prevede un approccio multiforme che sfrutta vulnerabilità note in dispositivi di rete ampiamente utilizzati, in particolare quelli di Cisco.
Un altro comportamento degno di nota mostrato da Salt Typhoon consiste nello sfruttare le tecniche LOTL (Living-off-the-Land) sui dispositivi di rete, abusando dell’infrastruttura affidabile come punto di snodo per passare da una società di telecomunicazioni all’altra. Di seguito viene riportata l’infrastruttura di sfruttamento di Salt Typhoon:
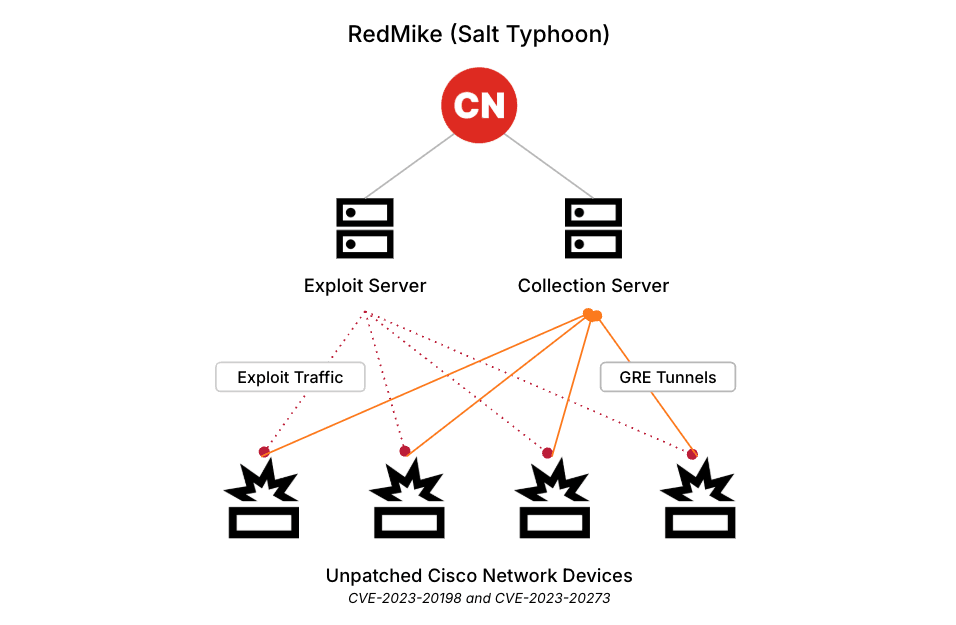
Salt Typhoon inizia con un’ampia ricognizione per identificare i potenziali obiettivi all’interno delle infrastrutture critiche, come i fornitori di telecomunicazioni e le istituzioni scolastiche. Questa fase può comportare la scansione dei dispositivi vulnerabili, la raccolta di informazioni sulle configurazioni di rete e l’identificazione del personale chiave.
Il gruppo sfrutta spesso specifiche vulnerabilità nei dispositivi Cisco. Ad esempio, è noto che sfrutta vulnerabilità come CVE-2018-0171 e CVE-2023-20198. Queste vulnerabilità consentono agli aggressori di ottenere l’accesso non autorizzato ai dispositivi di rete inviando messaggi o comandi artigianali, provocando condizioni di denial-of-service o l’esecuzione di codice arbitrario.
Una volta ottenuto l’accesso iniziale attraverso lo sfruttamento delle vulnerabilità, Salt Typhoon utilizza spesso malware come il MASOL RAT (come visto in precedenza) o kit di exploit personalizzati. Questi strumenti consentono agli aggressori di stabilire un punto d’appoggio all’interno della rete, di esfiltrare dati sensibili e di raccogliere credenziali legittime per ulteriori accessi. Il furto di credenziali è cruciale perché consente di aumentare il livello di accesso.
Salt Typhoon (RedMike) ha tentato di sfruttare più di 1.000 dispositivi Cisco a livello globale. Il gruppo ha probabilmente compilato un elenco di dispositivi target in base alla loro associazione con le reti dei provider di telecomunicazioni. Insikt Group di Recorded Future ha anche osservato che RedMike stava prendendo di mira dispositivi associati a università in Argentina, Bangladesh, Indonesia, Malesia, Messico, Paesi Bassi, Thailandia, Stati Uniti (USA) e Vietnam.
Per proteggersi dagli attacchi di Salt Typhoon (RedMike), le organizzazioni devono implementare una strategia di cybersecurity completa che enfatizzi la gestione delle vulnerabilità, la sicurezza della rete e la formazione dei dipendenti. Ecco alcune misure chiave da considerare:
Salt Typhoon è salito alla ribalta a causa della sua recente infiltrazione nell’infrastruttura delle telecomunicazioni commerciali. I senatori statunitensi hanno definito l’attacco “strabiliante”, affermando che dovrebbe fungere da “campanello d’allarme” per le aziende che si ritiene siano state violate, tra cui AT&T, Verizon e Lumen.
RedMike ha probabilmente preso di mira queste università per accedere alla ricerca in aree correlate a telecomunicazioni, ingegneria e tecnologia, in particolare presso istituzioni come UCLA e TU Delft. Oltre a questa attività, a metà dicembre 2024, RedMike ha anche eseguito una ricognizione di più indirizzi IP di proprietà di un provider di telecomunicazioni con sede in Myanmar, Mytel.
La continua esposizione di vulnerabilità nei dispositivi Cisco ha portato a una crescente preoccupazione tra i fornitori di servizi e le istituzioni, costringendoli a rivedere le loro strategie di sicurezza. È diventato evidente che la protezione delle reti e dei dati è di fondamentale importanza per preservare non solo la sicurezza nazionale, ma anche la fiducia del pubblico nei sistemi digitali.
Di fronte a queste minacce in evoluzione, esperti del settore e professionisti della cybersicurezza sottolineano l’importanza di misure di sicurezza robuste e difese proattive. È necessario che le organizzazioni conducano approfondite valutazioni delle loro reti, focalizzandosi in particolare sulle vulnerabilità all’interno dei dispositivi Cisco. La situazione attuale serve da monito sulla necessità di una vigilanza continua contro avversari sofisticati come Salt Typhoon e i suoi affiliati.
Mentre il gruppo continua a lanciare attacchi mirati contro infrastrutture critiche e istituzioni educative, è fondamentale che le organizzazioni di tutto il mondo migliorino le loro posture di sicurezza e collaborino per condividere informazioni, riducendo i rischi posti da tali minacce informatiche. La battaglia contro il cyber spionaggio è tutt’altro che finita, e solo attraverso uno sforzo collettivo la comunità internazionale può sperare di salvaguardare le proprie frontiere digitali.
Questo articolo è stato redatto attraverso l’utilizzo della piattaforma di Recorded Future, partner strategico di Red Hot Cyber e Leader Mondiale nell’intelligence sulle minacce informatiche, che fornisce analisi avanzate per identificare e contrastare le attività malevole nel cyberspazio.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…