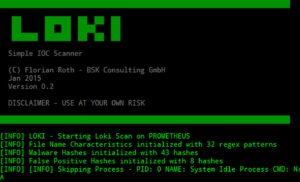
Loki, starting IOC discovering
Today is always more important and significant to be efficient in controlling our own infrastructures; actions to put in place for this verification process shall require both proactive and post-action approach: the last aspect is fundamental when an attack or in general any malicious behavior is conducted on a targeted system and we have to know all about this action, from its start to its finalization. The paradigm “it’s happened and I have to know all about it” is checked as well by Loki. Loki is an open source tool, developed in Python by Florian Roth (aka Neo23x0) and it is a



